Bluelight-mc2.club ads (scam) - Free Guide
Bluelight-mc2.club ads Removal Guide
What is Bluelight-mc2.club ads?
Bluelight-mc2.club tries to sell you fake security software
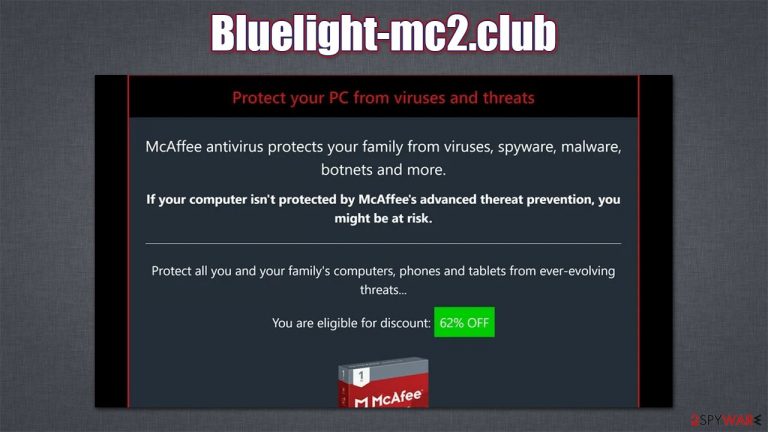
There are almost two billion websites on the internet, and, unfortunately, some of them are not created for legitimate purposes. While browsing the web, users might sometimes come across phishing, spoofing, misleading, and other types of malicious websites. Bluelight-mc2.club belongs to the category of scams that show misleading information about their computer security status in order to make users download or purchase some type of software. In some cases, this software might not be what it seems initially and might actually be malicious.
In this case, Bluelight-mc2.club might promote what it may seem like Norton, McAfee, Avast, and other prominent security applications. However, there is no guarantee that it is safe and legitimate – it is likely not to be the case considering the distribution methods. We strongly advise users to refrain from installing or even downloading these apps, as they might implement information tracking, infiltration of other malware, and other malicious activities behind your back.
| Name | Bluelight-mc2.club, Bluelight-mc1.club, etc. |
|---|---|
| Type | Scam, adware, redirect |
| Operation | Claims that the PC is infected with viruses and offers to download software to remove it |
| Distribution | Redirects from other websites, adware |
| Symptoms | Redirects to suspicious websites that hold plenty of commercial or scam content; fake messages offer to download malicious software; ads plague every visited website; unknown extension or program installed on the system |
| risks | Ads and links to sites displayed by the website might be dangerous: users might suffer from monetary losses, install malware or potentially unwanted programs on their systems, or disclose their sensitive data to cybercrooks |
| removal | You can remove potentially unwanted software or malware either by scanning your system with SpyHunter 5Combo Cleaner or performing manual elimination steps we provide below |
| Further steps | Cleaning web browsers is one of the secondary things you should do after PUP/malware removal to secure your privacy. You can use FortectIntego to do it quickly |
It is noteworthy that there are several versions of this malicious site, which uses different number within the same URL. Likewise, we have noticed that this scam is not unique, and there are plenty of websites under similar names that spread it – Redlight-mc2.club is being one of them.
While the name of the malicious site might differ, the looks of these scams remain the same: there is nothing much displayed on the page apart from a fake warning about a virus infection:
McAfee
Your PC is infected with 5 viruses!
ACTION REQUIRED!
Your Norton Subscription Has Expired!
Renew now to keep your pc protected.
If your PC is unprotected, it is at risk for viruses and other malware.
This scam is very typical and is trying to abuse basic human emotion – fear. The fake message is aimed at users who are not that familiar with how websites, the internet, and scams work, so it is much easier to trick them. In reality, there is no way that a website would know whether or not your system is infected with a virus
Likewise, keep in mind that crooks commonly fake the names of well-trusted tech companies and organizations. In this case, security software vendor names provide a fake sense of integrity. We have previously seen similar tactics being used in scams like “Pornographic virus alert from Microsoft” or “Google Chrome Critical Error.”
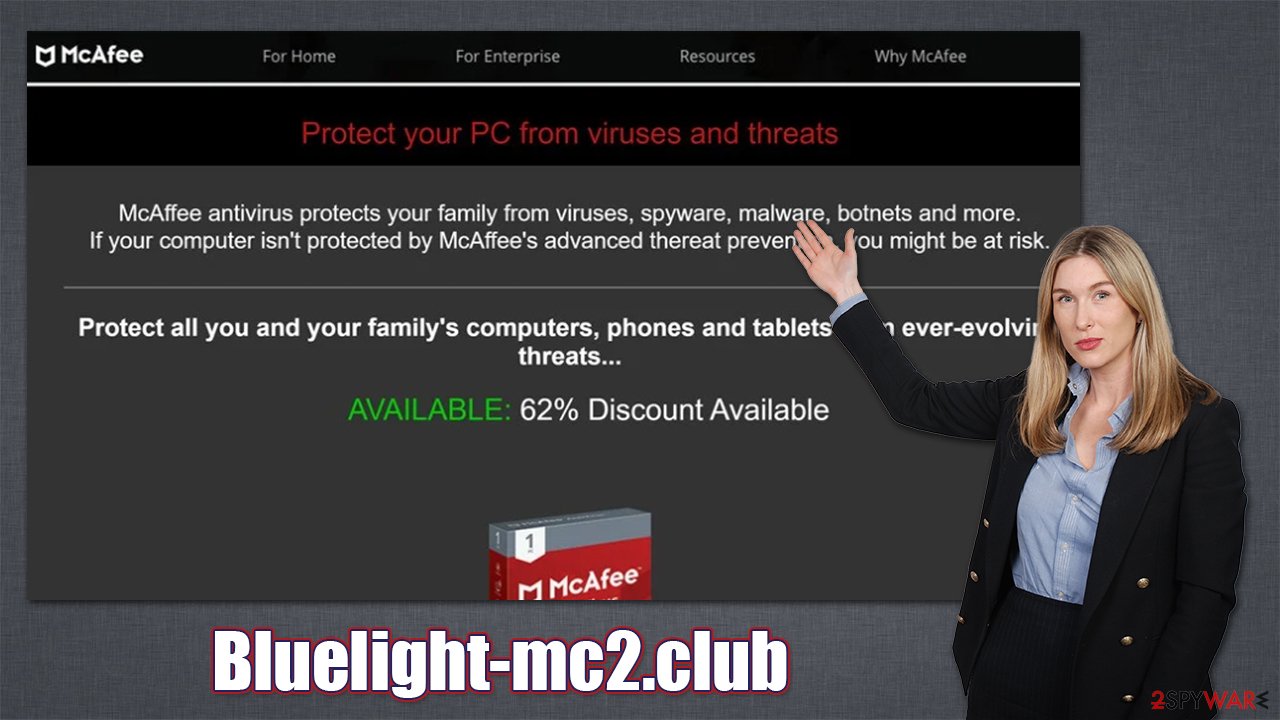
Remember, all the names, logos, wording, and similar attributes can be easily faked and impersonated, and the only giveaway in such situations might be the doubt, experience, and the web address in the URL bar. Speaking of which, it is one of the best indications that you have run into a scam – always check the URL, and visit the official websites instead if in doubt.
How the scams are spread
Users rarely access malicious websites on purpose – they are led there by various malicious links. For example, clicking on suspicious ads on various seemingly harmless websites can lead to unknown places. That being said, illegal sites, especially those that spread pirated applications and games, are the most dangerous ones and should be avoided. Otherwise, one might even get infected with treacherous malware, such as ransomware or a rootkit.[1]
Avoiding malicious websites can also be helped with security tools that have web and scam protection features. Likewise, employing ad-blockers could prevent malicious scripts from being executed automatically.
In some cases, however, users might be led to Bluelight-mc2.club, Bluelight-mc1.club, or similar sites with the help of adware or malware. Malicious software, suspicious websites, and untrustworthy advertisement networks are strongly intertwined.
To avoid adware infections, you should be cautious when downloading freeware[2] from the internet. Even third-party websites that are relatively popular and known were seen using software bundles.[3] In most cases, users rush through the installation steps by pressing the “Next” button several times until they are done with it, which is precisely what third parties are counting on – inattentiveness.
Thus, always pay close attention to the installation process: read the fine print, watch out for misleading button placements, decline all the offers, remove ticks from pre-ticked checkboxes and, most importantly, always pick Advanced/Custom installation settings instead of Recommended/Quick ones.
Removal steps
It is true that you could encounter the Bluelight-mc2.club scam by simply browsing the internet and clicking a malicious link. However, you should also ensure that your system is clear from adware and malware.
First of all, you should perform a full system scan with SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable security software to ensure that no malware is present on your device. For future reference, keep anti-malware running in the background at all times and never ignore its warnings. Likewise, make sure you have it set to be updated automatically. Next, you can check for potentially unwanted programs in various ways – check the details below.
1. Check for unwanted extensions
Many adware or browser hijackers are spread as browser extensions due to them being very versatile and easy to create in comparison to other methods. To find and eliminate unwanted extensions, access browser settings as follows:
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select the unwanted plugin and click Remove.

MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

2. Uninstall programs from the system
When installed on the system level, adware is capable of much more. It can create scheduled tasks, change the registry, and much more. In some rare cases, Mac adware was seen downloading and installing other PUAs on the system without users having a clue of what was happening. Thus, make sure you check your operating system properly.
Windows
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

Mac
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

3. Clean your browsers
Finally, you should clean your browsers accordingly. When you visit websites and enter your passwords or other login details, these preferences are saved in the form of cookies and other elements. While a lot of this data is encrypted and invisible, cookie hijacking is still possible in some cases. Additionally, third parties use them to track various user data, so removing them from time to time is recommended. If you would rather avoid doing so manually, we recommend employing FortectIntego repair and maintenance utility instead.
Google Chrome
- Click the Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

How to prevent from getting adware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Rootkit: What is a Rootkit?. Veracode. Security solutions.
- ^ Tim Fisher. What Is Freeware?. Lifewire. ech News, Reviews, Help & How-Tos.
- ^ Lowell Heddings. Yes, Every Freeware Download Site is Serving Crapware (Here’s the Proof). How-To Geek. Site that explains technology.
