BufferKey (Removal Instructions) - Free Guide
BufferKey Removal Guide
What is BufferKey?
BufferKey is a Mac virus variant that targets users' personal data
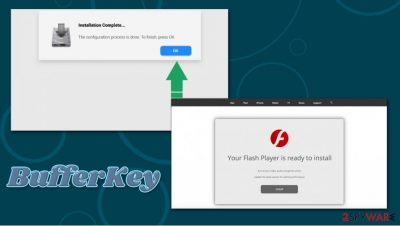
BufferKey is a potentially unwanted application that belongs to the Adload malware family, which mostly spreads via software bundle packages and fake Flash Player updates. As a result, Mac users allow the malicious app to access their devices after they type in their Apple login information into a warning prompt. Essentially, the BufferKey virus is a Trojan[1] when it comes to its distribution, as users never intend to install the app in the first place.
Once inside the system, BufferKey adware would establish a new profile and install a new browser extension on Safari, Google Chrome, or another web browser. Most of the users would also notice homepage and search engine changes that are most commonly set to Safe Finder or similar useless tools. All searches perfumed by such a hijacked browser would also cause several akamaihd.net redirects to unknown sites.
| Name | BufferKey |
| Type | Adware, Mac virus |
| Danger level | Medium. Can be associated with malware infection |
| Distribution | Cybercriminals use software bundle packages on pirated software websites or fake Flash Player updates to deliver malicious app to users |
| Symptoms |
|
| Termination | To completely get rid of malware/adware from your macOS, perform a full system scan with powerful anti-malware software – we recommend using SpyHunter 5Combo Cleaner or Malwarebytes |
| Optimization | After you eliminate the infection, we recommend using FortectIntego for best results |
BufferKey is just one of many Adload apps that attack Mac users regularly – ArchimedesLookup, SectionBrowser, AgileHelp, ProductEvent, and many others, are just a few clones that operate in the exact same way. All the apps can be recognized by a blue/green/red magnifying glass icon that is presented next to the browser extension and the installed program. However, similarities do not end there.
By using misleading and deceptive distribution tactics, the BufferKey virus manages to trick many users into downloading this malicious app. Once installed, the app can establish several persistence components within the macOS by abusing the built-in AppleScript. For example, while checking various locations on the computer, users might find new login items, profiles, or malicious .plist files. These changes can greatly diminish the chances of successful BufferKey removal.
There are more malicious traits of the BufferKey adware. Since the app is installed with elevated permissions, it can grant itself access to various information that is located on the computer. For example, the extension that is clipped to the browser is capable of reading all types of sensitive data that you type while using the internet – the description states:
Permissions for “BufferKey 1.0”
Webpage contents
Can read sensitive information from webpages, including passwords, phone numbers, and credit cards on: all webpagesBrowsing History
Can see when you visit: all webpages
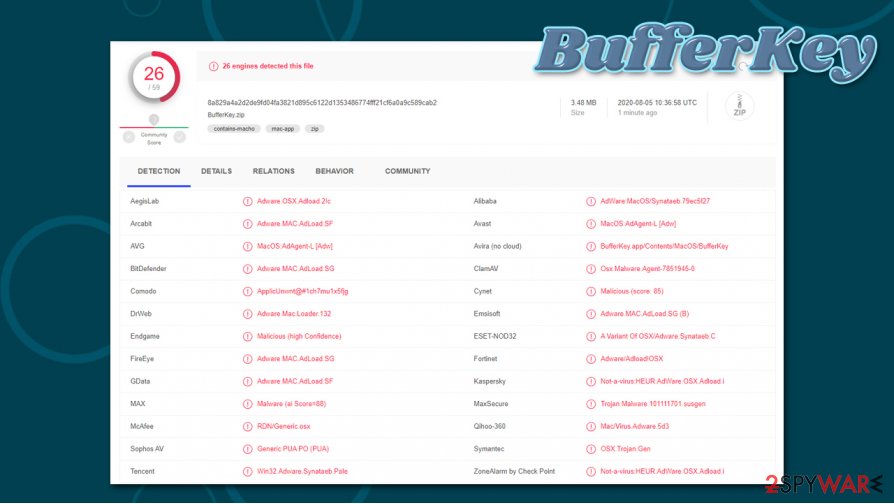
As you can see, BufferKey acts a lot like malware, and, according to research, can often be associated with more serious malware infections such as Shlayer Trojan (security experts from Kaspersky found[2] that the malware is present on 10% of Macs worldwide). Thus, it is not uncommon for infected individuals to find more malicious extensions and apps installed on their computers.

Since the main goal of BufferKey is to remain on the system for as long as possible and operate as adware, those infected can experience a variety of bothersome browser behavior while infected. Adware specializes in displaying users plenty of intrusive commercial content that the malicious actors monetize on. Thus, expect to see a lot of popups, redirects, hyperlinks, altered search results, and other ads during your browsing sessions.
You might not be able to uninstall BufferKey until you find and delete all the components that the malicious app placed on your system. However, this might be very time consuming and difficult, so you should instead trust security applications to do the job for you. If you experience lag or slowdowns after malware termination, you can delete junk and speed up your Mac with tools such as FortectIntego.
Macs are secure machines, as long as you don't let malware in
A myth that Macs don't get infected with malware has been around for years. While it is true that macOS is immune to some types of parasites (for example, worms), cybercriminals have been focusing on this platform much more and created malicious apps designed to exploit users. Macs offer a variety of built-in defenses, including Gatekeeper or XProtect. However, these built-in security options are not unbreakable, as users can be tricked into letting the infection in.
If you download an app from an unapproved source, macOS will ask you to enter your credentials. Of course, if it is a malicious app, you would never do it. However, if you believe that the app is legitimate (for example, you are installing a pirated version of MS Office suite, or you were told that your Flash Player is out of date),[3] you will allow it to gain access to your device.
Hence, you should not visit high-risk websites such as torrents, as they are often filled with malware-laden installs. Besides, Flash Player is an outdated plugin that is no longer required to play multimedia on websites. Another important point is keeping your macOS up to date, as cybercriminals might use exploits to break in.
Remove BufferKey and all its components at once
Changed browser settings typically do not indicate a serious security threat. Nonetheless, any unapproved action on your computer should be investigated, as it can be related to malicious applications that might download and install other malware and compromise the system further. That is why timely BufferKey removal is very important. However, many users found that the process can be much more difficult than anticipated.
As previously mentioned, the BufferKey virus might set persistence mechanisms on your Mac. Therefore, moving it to Trash as you do with legitimate apps might not be enough. If you want to get rid of all the threat's components manually, you should check the following locations and delete all the related items:
- System Preferences > Accounts> Login Items
- System Preferences > Users&Groups > Profiles
- ~/Library/LaunchAgents
- ~/Library/Application Support
- ~/Library/LaunchDaemons
If this process seems too complicated for you or you wish to remove BufferKey quickly, you should instead rely on powerful anti-malware instead. Besides, you can also reset your browsers if the extension is still present after a full computer scan.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of BufferKey. Follow these steps
Delete from macOS
To delete applications from macOS, follow these instructions:
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Remove from Mozilla Firefox (FF)
If you can't delete BufferKey extension from your Firefox browser, follow these steps:
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Remove from Google Chrome
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Delete from Safari
Reset Safari to ensure that no malicious components and settings are left on it:
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

After uninstalling this potentially unwanted program (PUP) and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti-spyware. This will help you to get rid of BufferKey registry traces and will also identify related parasites or possible malware infections on your computer. For that you can use our top-rated malware remover: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting adware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ What Is A Trojan Virus?. Vipre. Security solutions.
- ^ Anton V. Ivanov, Mikhail Kuzin, Ilya Mogilin. Shlayer Trojan attacks one in ten macOS users. Kaspersky. Security research blog.
- ^ Ben Lovejoy. PSA: There’s a new fake Flash Player installer for Macs, and it’s nastier than usual. 9To5Mac. Apple News & Mac Rumors Breaking All Day.












