Chromium virus term exploited. 14 variants listed
Chromium virus Removal Guide
What is Chromium virus?
Chromium virus is a browser virus misusing the name of the legitimate Google open-source project
Chromium virus is a term used to describe a malicious browser application that is using the source code of a legitimate project presented by Google. The list of malicious apps is excessively long, such as WebDiscover, Chroomium, eFast,[1] Citrio, and many others.
These apps are engaging in malicious activities that can easily be classified as malicious: infiltrating systems WITHOUT users' approval, rerouting them to affiliated websites, displaying fake search results, harvesting and sharing sensitive information, changing settings without permission, etc. These browser hijackers are mostly prevalent in Spain, Italy, Portugal, and USA. Both operating systems, macOS and Windows, can be affected.
| Name | Chromium virus |
|---|---|
| Type | PUP/Browser hijacker/Browser malware/adware |
| Danger Level | From medium to high. Does not damage the system but can alter Windows Registry and browser's settings, redirect to malware-filled websites |
| Main file | Chromium.exe |
| Related files | QtWebEngineProcess.exe (not digitally signed)[2] |
| Symptoms | High CPU usage, replaced the browser's homepage, installation of suspicious toolbars |
| Types/versions | eFast, Chroomium, Tortuga, Olcinium Browser, Qword Browser, Chedot Browser, BrowserAir Browser, Fusion Browser, BeagleBrowser, MyBrowser, Super Browser, Citrio browser, WebDiscover, Yandex browser |
| Distribution method | Software bundling, freeware or shareware download websites and networks, ads |
| Main dangers | Redirects to malicious websites, infected ads, identity theft |
| How to uninstall | To uninstall use anti-virus software or a guide provided below |
| Recovery from virus damage | Perform a scan with FortectIntego to recover corrupted entries |
Note that Chromium virus is not related to Chrome and open-source web projects. The latter project[3] is entirely legitimate and doesn’t contain any malicious codes. It is open to anyone who wants to create a customized browser, however, just like any other open-source tool, it gets exploited by malevolent people. If you noticed that your browser acts suspicious, check if it isn't replaced by a bogus version.
Typically, users infected with this virus do not notice anything suspicious because the aim of this shady add-on is to persuade them into thinking they are using the genuine version of the browser. However, suspicious redirects[4] and also annoying pop-up ads shortly reveal that something is wrong with the browser, and users might start looking for suspicious programs or browser extensions on the system.
Sadly, there might be none because the virus disguises its processes well. On the other hand, if you check Task Manager processes, you might notice Chromium.exe process. It stands out by consuming large amounts of CPU memory energy resources. To recover after such a virus and fix system changes initiated by it, use FortectIntego. You can detect and remove browser viruses from a Mac or Windows operating system with the help of SpyHunter 5Combo Cleaner or Malwarebytes.
Main features of the article's culprit
It is dangerous to keep browser virus on the system as there are numerous unauthorized activities initiated by this unauthorized malware, including the following ones:
- tracking the user's online activity and collecting NPII and PII;
- redirecting traffic to sponsored sites;
- filling websites with the sponsored content;
- pushing fake updates, push notifications, etc.
Once you are tricked, it starts its activity by tracking your actions online the entire time you use it. Therefore, the virus observes what websites you visit, what ads you click on, and what entries you type. Such information might be collected by third parties and could reach someone you cannot trust. Besides, the collected data is typically used to deliver targeted advertisements, and it also means that it can be used to serve deceptive, but luring content for you.
Therefore, expect to see a lot of catchy ads offering hard-to-believe deals as well as ads suggesting you check out adult-only websites or install software updates you did not even know you “need.”
Be careful if you notice that your browser causes redirects to a particular website every time you launch it. Browser virus might attempt to force you to use a particular search engine just to provide you with a bunch of sponsored search results next to organic ones and then trick you into clicking them.
Furthermore, during its stay, the hijacker may bother you with constant redirects and similar issues. Due to this phenomenon, the browser may direct you to potentially insecure domains[5] or ask to disclose personal information[6]. Avoid staying too long on these websites, and, instead, focus on the virus removal.
A detailed list of malicious browsers. 14 versions listed.
BeagleBrowser virus
BeagleBrowser by Lollipop Network, S.L. is a potentially unwanted program (PUP) that takes over the victim's computer and starts displaying annoying ads to the victim. Although the developers of the software present it as a browsing tool that helps to “create a clean and safe environment for surfing the web,” it proved to be yet another adware-type web browser that seeks to push paid content to its users daily. There is no wonder why so many users try to remove BeagleBrowser shortly after installing it.

BrowserAir virus
BrowserAir is yet another potentially unwanted program posing as a version of Chrome. This web browser project is hardly useful and should not be used by computer users at all. Although it claims to be “free, fast and lightweight” web browser, it functions as a typical adware program that causes URL redirections to trigger pop-up ads and deteriorates the browsing experience. It is highly advisable to remove BrowserAir virus to improve computer performance and secure browsing sessions.

Chedot
Chedot virus is a highly deceptive web browser that loads the search.chedot.com page on startup. This page quickly redirects the victim to a modified version of Google. Such redirection is required to convince the victim that he/she is using the real version of Chrome (since the majority of Chrome users use Google as the homepage). However, further activities initiated by these browser hijackers aren't pleasant and should not be ignored.
The suspicious browser is ad-supported, which means that it will test all possible ways of serving sponsored offers and pushing ads to the victim. The user of Chedot Browser might run into ads in search results, see them in pop-up or pop-under ads, banners, or full-screen ads. These ads hardly ever provide useful offers and simply annoy the victim, so it is better to eliminate Chedot.
Chroomium virus
Chroomium browser is yet another malicious adaptation of the Google project. This highly annoying virus replaces the original Chrome browser and starts displaying commercial offers during each browsing session. The initial sign of Chroomium malware hijack is the slow performance of the browser. Besides, you will notice common browser hijacking signs such as unexpected redirections or an overload of ads in search results during browsing sessions.
Citrio
Citrio Browser. This version was developed by Epom Ltd. and is classified as a potentially unwanted application that spreads with the help of software bundling, so users rarely notice the entry point. Once installed, Citrio allocates itself as a primary browser with modified settings that are preset by the authors.
Citrio browser allows users to use it as a “powerful download manager” that has implemented the torrent feature. However, they will soon notice that there are several browser extensions or plugins that they never installed. This will lead to excessive ads in the forms of pop-ups, pop-unders, in-text links, flashing windows, banners, etc.

eFast Browser virus
eFast virus is a deceptive web browser that silently replaces Google Chrome and starts generating never-ending pop-up ads, banners, and injecting links into websites that display ads as soon as the victim hovers the cursor over them. This web browser is hard to remove, so experts recommend using professional anti-malware programs for detection and removal of eFast components. If you suspect that Chrome acts suspiciously, it might be eFast virus. Do not ignore the issue and check your system for this browser-replacing malware ASAP.
Fusion Browser
Fusion Browser is merely an ad-supported program that tries to surpass the original Chrome browser. However, it strives too hard to monetize its services, therefore users do not consider it useful. It simply displays too many ads during the user's browsing sessions and even manages to cause URL redirects to generate pay-per-click revenue faster. Sadly, its questionable functionality has convinced cybersecurity experts to add it to the spyware category and rank it as a potentially unwanted program.
MyBrowser virus
MyBrowser virus is a questionable program that tries to convince computer users to use it instead of the original Google Chrome browser. Sadly, lack of useful functions and continuous URL redirection issues have earned this fake web browser a bad reputation over time. If you spotted this fake browsing tool on your computer, remove MyBrowser ASAP. 
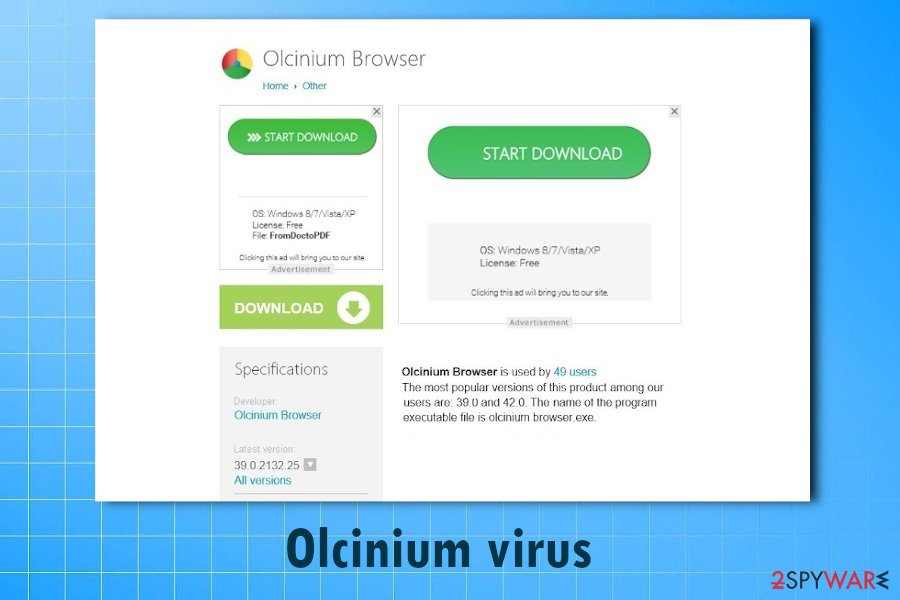
Olcinium virus
Olcinium Browser is a potentially unwanted program (PUP) that is also based on the Google project. It poses as a regular web browser that looks almost identical to Google Chrome. Once installed, it replaces original Chrome shortcuts and starts offering its web-browsing services for the victim. Sadly, these services aren't free – in order to use them, the victim has to encounter hundreds of third-party ads daily, which is really annoying, to say at least.
Besides, ads by Olcinium can hide links pointing to insecure web pages or even instantly install spyware or malware on your PC. If you want to keep your PC secured, remove Olcinium as fast as you can.
Qword Browser virus
Qword Browser gets installed on the system with the help of bundling. Once there, the victim starts experiencing adverse effects such as unexpected change of browser's homepage (the deceptive browser loads Qword.com on startup), continuous URL redirects, pop-up ads, and other inconveniences. These problems slow down the browser and prevent the victim from enjoying the browsing experience freely. 
Super Browser
Super Browser is probably the most annoying thing that a computer user can run into. Continuous redirects and pop-up ads during web browsing sessions is something that we all would like to avoid, however, computers infected with SuperBrowser simply cannot function differently. Therefore, security experts suggest removing this potentially unwanted software as soon as possible. The quickest way to catch all of its components is to run security software like FortectIntego.
Tortuga Browser virus
Tortuga virus is yet another creation based on Chromium. However, its suspicious activities have quickly convinced cybersecurity experts to add it to “potentially unwanted programs” and “spyware” lists. The web browser promotes itself as a secure, fast, and optimized web browser that offers an interruption-free browsing experience, it actually creates numerous interruptions (advertisements) and pushes them to the computer user on a daily basis. An immediate Tortuga Browser removal can help to get rid of these issues. 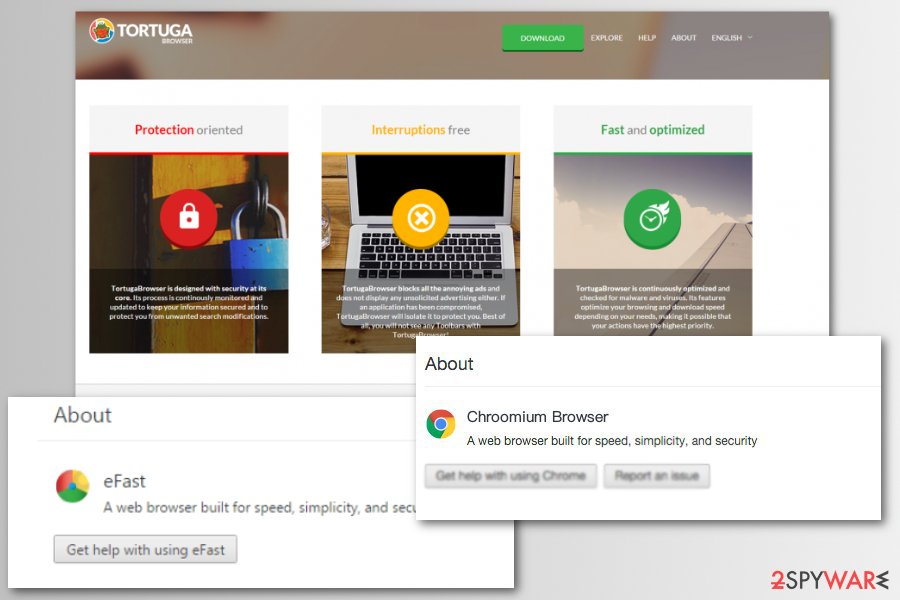
WebDiscover
WebDiscover is considered to be a potentially unwanted program that gets into systems with other applications from the internet. The developers, the US-based company WebDiscover Media, claim that the program will provide the “most convenient, clutter-free browsing experience.”
However, those who agree to set WebDiscover as their primary browser will soon realize that their searchers are littered with sponsored links and redirects lead them to sites like Safestsearches.com. As it is typical to PUP authors, what interests them is juicy ad revenue. Unfortunately, it can also direct users to unsafe domains where they could lose money, personal data, or get infected with malware. 
Yandex browser
Yandex browser is primarily used by Russian-speaking users and is basically an alternative to Google in the region. While the application is known to include several security features to protects its users (such as DNS encryption, file scanning, DNS spoofing protection, etc.), it also replaces Cortana with “Alice” and spawns pop-ups even when the browser is off.
The browser is also supported by often features from the company, such as Yandex toolbar, Yandex.ru redirect, etc. Without a doubt, users will not get accurate search results while the app tampered with various settings, and will end up on sponsored sites instead. Therefore, remove Yandex browser and use the original Chrome application instead.
Ways to install fake web browsers
You can accidentally enable the hijack virus if you tend to install new programs with “Standard” or “Default” mode on. It is of high importance to modify installation settings in order to prevent the infiltration of potentially unwanted programs.
All you need to do is to find and configure installation settings the right way – choose “Custom” or “Advanced” installation settings and look for suspicious checkboxes with shady statements next to them.
If you can find statements that grant your permission to install unknown programs, browser toolbars, and similar pieces of software, do not proceed with the installation until you configure them the right way. Deselect the ticks from these checkboxes and then continue. Finally, we must warn you that browser viruses can be distributed via “Urgent Chrome Update” ads.
However, some fake versions of web browsers can reach the victim's computer when installed alongside illegal software. We strongly recommend you to stay away from free licensed version packs you can download from torrent sites or other suspicious web sources. Placing them on your system can allow hazardous files to get in as well.
How to remove Browser Hijacker from Windows and MacOS
Remove Chromium virus windows 10 as soon as you notice that your Chrome browser behaves in a suspicious way. You may want to check the Chrome version via browser settings. However, remember that criminals can make the bogus browser display a fake Chrome version just to convince victims that they are using a legitimate version of the Internet browser, so you shouldn’t trust the information provided in Chrome’s “About” section.
To remove successfully, we advise you to perform a system check using anti-malware programs. It is likely that Norwegian users[7] might be more targeted by this PUP. Thus, they should be more cautious.
A video guide for more insight
To help you delete browser hijacker for good, we decided to prepare a video guide explaining every step that needs to be performed. Make sure you follow the details presented in this video. However, note that the virus keeps changing as it has already been three years of its operation. You may need to find the new malicious process of the virus. If this is a too complicated task for you, use the automatic removal method.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of Chromium virus. Follow these steps
Uninstall from Windows
Instructions for Windows 10/8 machines:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

If you are Windows 7/XP user, proceed with the following instructions:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Delete from macOS
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Remove from Microsoft Edge
Delete unwanted extensions from MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Clear cookies and other browser data:
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Restore new tab and homepage settings:
- Click the menu icon and choose Settings.
- Then find On startup section.
- Click Disable if you found any suspicious domain.
Reset MS Edge if the above steps did not work:
- Press on Ctrl + Shift + Esc to open Task Manager.
- Click on More details arrow at the bottom of the window.
- Select Details tab.
- Now scroll down and locate every entry with Microsoft Edge name in it. Right-click on each of them and select End Task to stop MS Edge from running.

If this solution failed to help you, you need to use an advanced Edge reset method. Note that you need to backup your data before proceeding.
- Find the following folder on your computer: C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.
- Press Ctrl + A on your keyboard to select all folders.
- Right-click on them and pick Delete

- Now right-click on the Start button and pick Windows PowerShell (Admin).
- When the new window opens, copy and paste the following command, and then press Enter:
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” -Verbose

Instructions for Chromium-based Edge
Delete extensions from MS Edge (Chromium):
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Clear cache and site data:
- Click on Menu and go to Settings.
- Select Privacy, search and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Reset Chromium-based MS Edge:
- Click on Menu and select Settings.
- On the left side, pick Reset settings.
- Select Restore settings to their default values.
- Confirm with Reset.

Remove from Mozilla Firefox (FF)
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Remove from Google Chrome
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Delete from Safari
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

After uninstalling this potentially unwanted program (PUP) and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti-spyware. This will help you to get rid of Chromium registry traces and will also identify related parasites or possible malware infections on your computer. For that you can use our top-rated malware remover: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting browser hijacker
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Pieter Arntz. eFast browser hijacks file associations. Malwarebytes LABS. Security Blog.
- ^ Vangie Beal. Digital certificate. Webopedia. Online Tech Dictionary.
- ^ Official website. Chromium. Open-source web browser project.
- ^ Security researchers notice an increase in Trotux activity. VirusActivity. The latest news about computer viruses.
- ^ Olivia Morelli. Top 6 most dangerous computer viruses of 2016. NoVirus. Cybersecurity news and virus removal guides.
- ^ Personally identifiable information. Wikipedia. The Free Encyclopedia.
- ^ http://viruset.no/. IT Nyheter, Anmeldelser og Tutorials.























