CTB Locker virus (Improved Guide) - 2021 update
CTB Locker virus Removal Guide
What is CTB Locker virus?
CTB Locker virus – ransomware that has been targetting the USA, Germany, Italy, and the Netherlands mostly
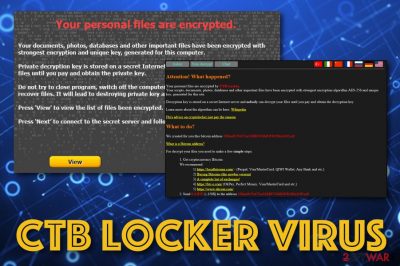
CTB Locker virus (also found under a title of CTB-Locker ransomware) is a crypto-type [1] malware, which started attacking PC users in the middle of July 2014. According to research, this malware strain has been found targetting users in USA, Germany, Italy, and the Netherlands. It is almost identical to Cryptowall virus, Cryptolocker, Cryptorbit, Critroni, etc., so if you have ever heard about any of these parasites, you will know what this ransomware is used for. Basically, it is designed for encrypting specific data files and then making people pay for their decryption. In most cases, people who want to recover access to their photos, videos, and other files are asked to pay $300. Besides, CTB-Locker ransomware loads AllFilesAreLocked.bmp, DecryptAllFiles.txt, [seven random letters].html, or similar messages/files to report about the data encryption process.
| Name | CTB Locker virus |
|---|---|
| Type | Ransomware |
| Danger level | Very high. Can cause important data losses |
| Targets | People who reside in Germany, USA, Italy, and the Netherlands |
| The start | This infection first took place in 2014 |
| Similar malware | Cryptowall virus, Cryptolocker, Cryptorbit, Critroni |
| Ransom notes | AllFilesAreLocked.bmp, DecryptAllFiles.txt, [seven random letters].html |
| Malware detection | Use anti-malware to scan the entire system and detect malicious objects |
| Repair | Rely on PC repair tools like FortectIntego and fix virus damage |
CTB Locker virus, of course, demands a ransom price that should be paid in a form of Bitcoins [2]. If you think that your PC has already infected by this ransomware virus, the first thing that you should notice is that you cannot reach your files anymore. Also, you may start seeing a warning message explaining the whole thing and asking to pay a fine.
In this case, you should immediately scan your computer with a reputable anti-spyware program because the sooner you do that, the larger amount of files you could save. Unfortunately, this CTB Locker virus can hardly be noticed before it starts showing its notification that reports about encrypted data and asks to pay a ransom.
That's why you should always have an updated anti-spyware installed on your computer that could easily help you to prevent infections like this one. For that, we highly recommend using SpyHunter 5Combo Cleaner or Malwarebytes. Also, this is a very beneficial program to search for malware traces when opting for automatic removal.
You need to remove the virus immediately after you spot files that are encrypted and do not load properly. This type of threat has been getting more and more advanced each year and targetting a bigger audience. Continue reading this article and find out all updates on this ransom-demanding threat.
Additionally, note that when infected with CTB Locker ransomware, you can lose files with such extensions:
3fr, accdb, ai, arw, bay, cdr, cer, cr2, crt, crw, dbf, dcr, der, dng, doc, docm, docx, dwg, dxf, dxg, eps, erf, indd, jpe, jpg, kdc, mdb, mdf, mef, mrw, nef, nrw, odb, odm, odp, ods, odt, orf, p12, p7b, p7c, pdd, pef, pem, pfx, ppt, pptm, pptx, psd, pst, ptx, r3d, raf, raw, rtf, rw2, rwl, srf, srw, wb2, wpd, wps, xlk, xls, xlsb, xlsm, xlsx, etc
The start of 2015: CTB-Locker starts urging for a ransom of 3 BTC
CTB-Locker was renewed at the beginning of 2015. After this, the virus started asking to pay 3 BTC or about $2774 for giving people an opportunity to recover the connection to their files. Also, it includes “free decryption” service, an extended deadline (96 hours) to pay the fine, and an option that allows changing the language of the ransom message.
At the moment of writing, victims can switch from English to Dutch, German and Italian [3]. An interesting thing is that this new version of CTB Locker allows people to select 5 different files for free decryption. This option is called “Test Decryption” and is presumably given to convince users that this service is not invented.
Nevertheless, you should NEVER pay this ransom and support scammers. Just scan your computer with reliable anti-spyware and remove the virus. Then, you should download one of these programs that are given down below to recover the connection to your files.
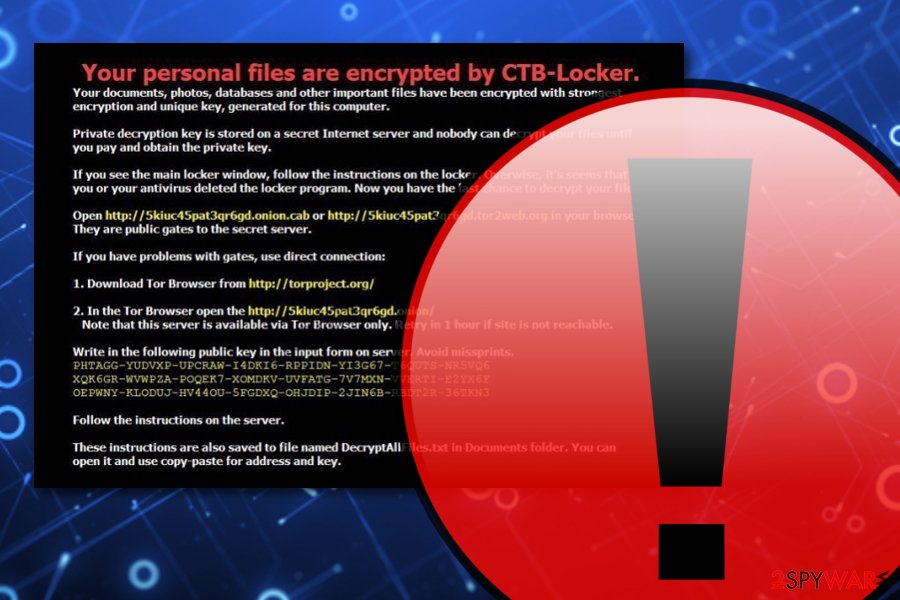
2016 update: CTB-Locker ransomware starts attacking websites
It seems that 2016 can be called the year of CTB Locker. According to the latest news, hackers have started using this virus to attack websites. Beware that “CTB Locker for websites” can easily replace your original index page to the affected webpage. Also, it can encrypt all scripts, documents, photos, databases, and other important files, and start displaying its warning on the main page of the affected website.
According to the latest reports, the CTB-Locker virus can hold the site for as long as it makes its owner pay a ransom. To unlock it and decrypt encrypted files, a victim of this ransomware has to pay a ransom of $150 or £100. Also, the virus lets its victim see how the decryption process works and provides 2 decryption keys to unlock two random files.
The latest victim is the British Association for Counseling & Psychotherapy website [4]. People can't reach this domain, which now shows a detailed guide explaining how the owner of this site has to pay the fine and get encrypted files back. Of course, money is what scammers are expecting to get. To avoid a need to pay a ransom for hackers, you should create A BACKUP for your OS and the most important data.
RAUM method helps to spread the virus
According to the latest news, CTB-Locker has started spreading with the help of a new system called RAUM. This newly presented strategy is used to infect the most popular torrent files with ransomware, an infamous Dridex, Pony, and similar malware that is launched right after the malicious torrent file is installed on the system.
If infected with CTB Locker, you will discover that your files with these extensions are encrypted: .ai, .cdr, .doc, .docx, .eps, .jpg, .xls, .ppt, .psd, .pdf, etc. RAUM [5] is believed to work as a pay-per-install system that tracks torrent users first to find out which torrent files are the most popular ones among them.
Next, it infects these files with malware and uses hacked accounts to upload malicious content on the system. Security researchers have already discovered that hackers have been using Pirate Bay and Extra Torrent sites. Make sure you stay away from these domains to protect yourself and your files.
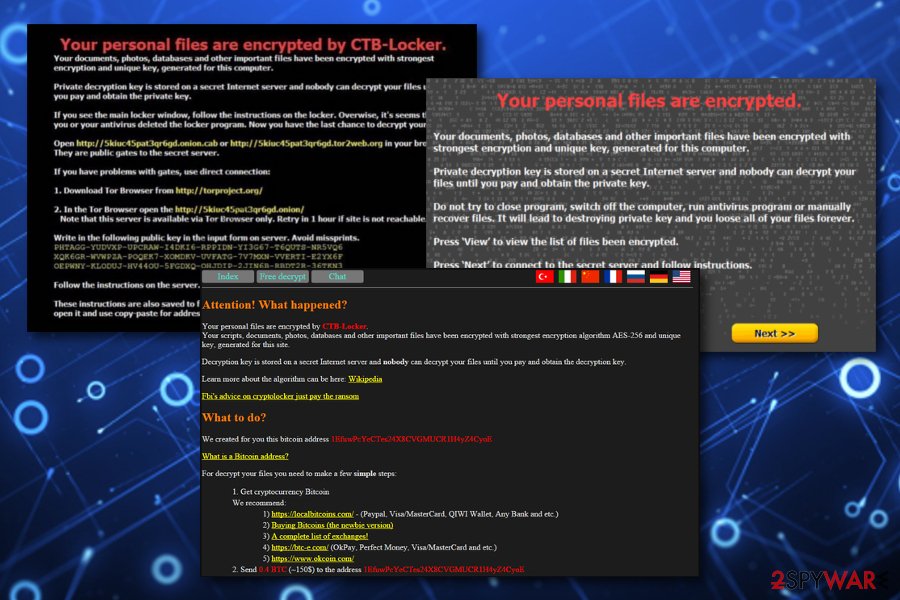
The year 2017: Crooks released a fake version of CTB-Locker named CTB-Faker
CTB-Locker has become a target of amateur hackers who have made a version of CTB-Faker — a program that looks like CTB-Locker but is not the actual infection [6].
A ransom note that this fake ransomware drops on the infected computers looks identical to the original virus version and notifies the victim that his/her computer has been infected with CTB-Locker and they have to pay 50 USD to recover their files.
However, for the data encryption CTB-Faker utilizes WinRAR functionalities, which is an easier and simpler way to achieve file encryption. The targeted files are simply compressed and stored in an archive protected with a password that hackers have selected.
Luckily, experts have already managed to dig up a vulnerability in this virus and disclosed this password — the virus-generated archives can be unlocked using the p4w1q3x5y8z code.
However, not all imposters can be decontaminated that easily. 2017 can bring programs that are equally dangerous to their malicious counterparts and may corrupt the system just as bad. So, we can only advise you to be careful out there!
Ransomware infections reach their target via email spam
According to experts from Virusai,[7] ransom-demanding threats are often injected into executables or Word documents that come attached to email messages. Email spam travels throughout the Internet sphere and reaches users frequently. The best way to protect yourself from malicious letters is NOT to open any questionable email received.
Additionally, if you are curious about opening an attachment, you should use an antivirus tool and scan the file/document before launching it. If something malicious is hiding there, you will be warned by your anti-malware and be able to delete the malware-laden content on time before anything bad occurs.
Nevertheless, you should always keep a distance from piracy networks, gambling, online dating, movie-streaming, game-playing, and adult-themed websites. Note that malicious payloads can come injected into hyperlinks, and suspicious-looking banner ads, pop-ups, pop-unders, and coupons.
CTB Locker removal guidelines on Windows system
If you are desperate, and you need a guide that could help you to remove virus from your computer, you are in the right place. If it has already hijacked your system, you should disconnect your computer from the Internet ASAP. Unfortunately, but we cannot give you a CTB Locker decrypter yet because it is just in the development stage. However, you should follow the step-by-step guide given below and finish the elimination of this ransomware.
Moreover, do not try to carry out the removal process on your own as even more damage might be caused! You might miss some malicious components and the infection might start running malicious processes right after the next computer boot. Note that anti-malware tools are more trustworthy at these tasks as they can complete multiple actions very fast: scan the system, detect malicious software, remove the threats.
Getting rid of CTB Locker virus. Follow these steps
Important steps to take before you begin malware removal
File encryption and ransomware infection are two independent processes (although the latter would not be possible without the former). However, it is important to understand that malware performs various changes within a Windows operating system, fundamentally changing the way it works.
IMPORTANT for those without backups! →
If you attempt to use security or recovery software immediately, you might permanently damage your files, and even a working decryptor then would not be able to save them.
Before you proceed with the removal instructions below, you should copy the encrypted files onto a separate medium, such as USB flash drive or SSD, and then disconnect them from your computer. Encrypted data does not hold any malicious code, so it is safe to transfer to other devices.
The instructions below might initially seem overwhelming and complicated, but they are not difficult to understand as long as you follow each step in the appropriate order. This comprehensive free guide will help you to handle the malware removal and data recovery process correctly.
If you have any questions, comments, or are having troubles with following the instructions, please do not hesitate to contact us via the Ask Us section.
IMPORTANT! →
It is vital to eliminate malware infection from the computer fully before starting the data recovery process, otherwise ransomware might re-encrypt retrieved files from backups repeatedly.
Isolate the infected computer
Some ransomware strains aim to infect not only one computer but hijack the entire network. As soon as one of the machines is infected, malware can spread via network and encrypt files everywhere else, including Network Attached Storage (NAS) devices. If your computer is connected to a network, it is important to isolate it to prevent re-infection after ransomware removal is complete.
The easiest way to disconnect a PC from everything is simply to plug out the ethernet cable. However, in the corporate environment, this might be extremely difficult to do (also would take a long time). The method below will disconnect from all the networks, including local and the internet, isolating each of the machines involved.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet

- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
If you are using some type of cloud storage you are connected to, you should disconnect from it immediately. It is also advisable to disconnect all the external devices, such as USB flash sticks, external HDDs, etc. Once the malware elimination process is finished, you can connect your computers to the network and internet, as explained above, but by pressing Enable instead.
Scan your system with anti-malware
If you are a victim of ransomware, you should employ anti-malware software for its removal. Some ransomware can self-destruct after the file encryption process is finished. Even in such cases, malware might leave various data-stealing modules or could operate in conjunction with other malicious programs on your device.
SpyHunter 5Combo Cleaner or Malwarebytes can detect and eliminate all ransomware-related files, additional modules, along with other viruses that could be hiding on your system. The security software is really easy to use and does not require any prior IT knowledge to succeed in the malware removal process.
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Find a working decryptor for your files
File encryption is a process that is similar to applying a password to a particular file or folder. However, from a technical point of view, encryption is fundamentally different due to its complexity. By using encryption, threat actors use a unique set of alphanumeric characters as a password that can not easily be deciphered if the process is performed correctly.
There are several algorithms that can be used to lock data (whether for good or bad reasons); for example, AES uses the symmetric method of encryption, meaning that the key used to lock and unlock files is the same. Unfortunately, it is only accessible to the attackers who hold it on a remote server – they ask for a payment in exchange for it. This simple principle is what allows ransomware authors to prosper in this illegal business.
While many high-profile ransomware strains such as Djvu or Dharma use immaculate encryption methods, there are plenty of failures that can be observed within the code of some novice malware developers. For example, the keys could be stored locally, which would allow users to regain access to their files without paying. In some cases, ransomware does not even encrypt files due to bugs, although victims might believe the opposite due to the ransom note that shows up right after the infection and data encryption is completed.
Therefore, regardless of which crypto-malware affects your files, you should try to find the relevant decryptor if such exists. Security researchers are in a constant battle against cybercriminals. In some cases, they manage to create a working decryption tool that would allow victims to recover files for free.
Once you have identified which ransomware you are affected by, you should check the following links for a decryptor:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

If you can't find a decryptor that works for you, you should try the alternative methods we list below. Additionally, it is worth mentioning that it sometimes takes years for a working decryption tool to be developed, so there are always hopes for the future.
Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from CTB Locker and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Crypto-ransomware attacks rise five-fold to hit over 700,000 users in one year. Kaspersky lab. Internet Security Protection Software news site.
- ^ Danny Palmer. In the Bitcoin era, ransomware attacks surge. Zdnet. Technology News, Analysis, Comments and Product Reviews for IT Professionals.
- ^ The current state of ransomware: CTB-Locker. Sophos blog. Security Made Simple for Business.
- ^ Chris Williams. This is what it looks like when your website is hit by nasty ransomware. The Register. Biting the hand that feeds IT.
- ^ Doug Olenick. RAUM weaponizes torrents to deliver malware. SC magazine. The cyber security source.
- ^ CTB-Locker ransomware impersonator uses WinRAR for encryption. SecurityWeek. Information Security News, IT Security News.
- ^ Virusai.lt. Virusai. Spyware and security news.






































