What is DECRYPT_INSTRUCTIONS.html? Should I remove it?
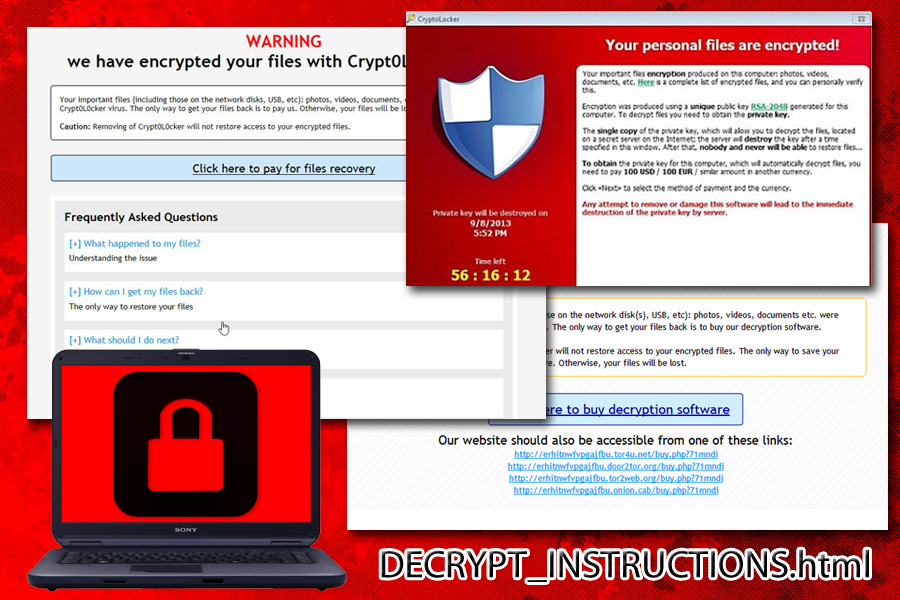
DECRYPT_INSTRUCTIONS.html is a file that users infected with CryptoLocker ransomware find on their computers
Encountering DECRYPT_INSTRUCTIONS.html file is certainly not good news. It signals that your computer and personal files have been victimized by CryptoWall, alternatively known as CryptoLocker, file-encrypting threat that started its infection spree in 2013.
Along with such threats as Locky and Cerber, emerging in later years, it has managed to spread terror globally. Due to the usage of elaborate asymmetric and symmetric, specifically, AES-256 and RSA-2048, encryption technology, it managed to encode personal files of natural and legal persons. Likewise, throughout its existence, it has made over $325 million profit.
Luckily, its activity declined over the years which triggered speculations that the authors decided to end the project. However, such naive thoughts should not persuade you into thinking that CryptoWall is no longer in the cyber space. Unfortunately, it gave inspiration for other hackers. So is it possible to terminate CryptoWall simply by deleting DECRYPT_INSTRUCTIONS.html file? The short answer is no, but there is much more than you should know about this.
The malware contains a complex source code and initiates commands which modify registry entries. While the malware is present on the system, it also launches the command to delete shadow volume copies which makes matters much worse.
Since there are multiple versions of CryptoWall, you might notice that your data contains different file extensions: if it is Crypt0L0cker, then it appends .enc file extension, while the original version attached .locked file extension. After completing the encryption process, it redirects users to DECRYPT_INSTRUCTIONS.html web page. In order to terrify victims even more, the analogous, DECRYPT_INSTRUCTIONS.txt, file is placed on the desktop to remind of the hopeless situation they are in. In these instructions, the authors provide a brief FAQ guide for users who have been struck with crypto-malware for the first time.
The guide also contains instructions how to purchase bitcoins and transfer them to a respective address controlled by racketeers. The file also contains an incorporated clock which counts expiration time. After the indicated time period ends, the files are said to be deleted. Since Cryptowall has shape-shifted into multiple versions throughout its existence, Crypt0L0cker and Torrentlocker have also been using the same file for instructing victims.
Distributing CryptoWall and DECRYPT_INSTRUCTIONS.html
All versions up to CryptoWall 5.1 have been using similar hijack techniques. Unfortunately, most profitable of them remains the transmission of the infection via spam emails. The malware is disguised as a .doc file in a .zip folder. Specifically, the virus asks a victim to enable macro settings. This functionality is expressed as a set of codes and ciphers presented in a .doc file.
If a user accidentally grants the permission, he or she activates CryptoWall. Then, the virus starts its data hunt. Within a couple of minutes, the mentioned DECRYPT_INSTRUCTIONS.txt and DECRYPT_INSTRUCTIONS.html files will appear on the device. In addition, the late versions of CryptoLocker might have been relying on trojans and exploit kits to multiple the range of the attack. In that case, you will need to arm up with proper cybersecurity programs.
DECRYPT_INSTRUCTIONS.html elimination is just a part of malware's removal
If you remove DECRYPT_INSTRUCTIONS.html file, the malware will keep rampaging on your computer. Banish the malware and all its components with the reliable anti-spyware application. Then you can try to fix the possible virus damage using repair tools like system applications. FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes may indicate affected or damaged files for you.
Do not forget to update the AV program for it to fully complete DECRYPT_INSTRUCTIONS.html removal and the elimination of the file-encrypting threat. After eliminating the infection, you can consider alternative methods to recover your data.

