Dodged ransomware (Virus Removal Instructions) - Free Guide
Dodged virus Removal Guide
What is Dodged ransomware?
Dodged ransomware is data locking malware that targets Italian users with COVID-19-themed phishing emails
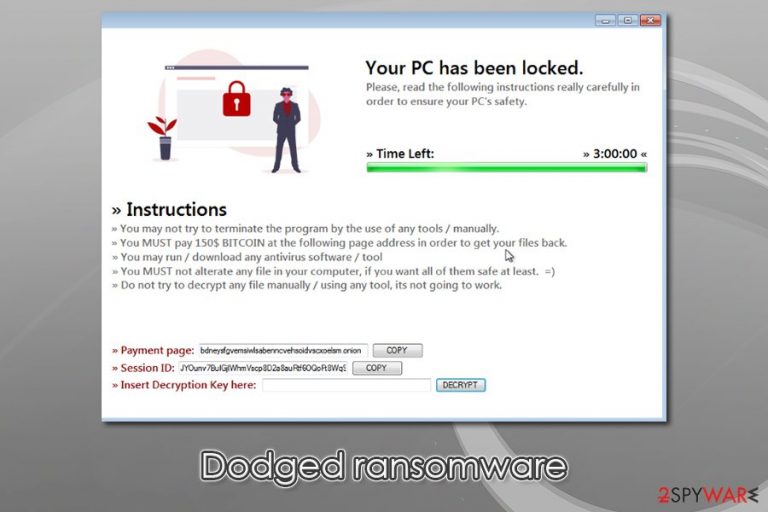
Dodged ransomware is a data-locking malware sample that was spotted by MalwareHunterTeam,[1] the prevalence of which is not defined yet. However, security researchers pointed out that the infection mainly targets users in Italy, although the data redemption instructions are written in English. Also, the executable of Dodged ransomware that was seen in the sample came as COVID-20.exe, which is highly likely to stem from a coronavirus-themed phishing email.
Once inside the system, the Dodged virus begins to look for files to encrypt and then appends .dodged extension to each. It then delivers a pop-up window, which explains that victims should transfer $150 worth of Bitcoin via the onion page, accessible only via the Tor network. However, you should avoid paying the ransom to cybercriminals, as chances of getting scammed are quite high. Instead, you should focus on Dodged ransomware removal and alternative methods for data recovery.
| Name | Dodged ransomware |
| Type | File locking virus, cryptomalware, wiper |
| Related files | COVID-20.exe, Non.exe – other executable names might also be used |
| Distribution | It is highly likely that the malware is mainly spread via spam email attachments, although other methods might also be used, including exploits, weakly protected RDP connections, web injects, fake updates, software cracks, etc. |
| Malware family | No connections to other malware families have been discovered so far |
| Features | Anti-analysis, data wiper, mouse inputs capture, etc. |
| File extension | Each of the encrypted files are appended with .dodged marker, and can no longer be accessed by the users. Example of the encrypted file: picture.jpg.dodged |
| Ransom size | Users are asked to pay $150 in Bitcoin for an alleged file recovery tool |
| Detection | Ransom:MSIL/Skidware.PI!MTB, Mal/Generic-S, Win32:RansomX-gen [Ransom], Gen:Heur.Ransom.Imps.3, ML.Attribute.HighConfidence, Trojan/Win32.Wacatac, Malicious.bd1c67, Gen:NN.ZemsilF.34108.qm0@ayJxXMe (Virus Total results) |
| File recovery | If no data backups were retained, there is no 100% secure method to recover the encrypted files. While using third-party tools (we list a few in the recovery section below) might not be successful, paying cybercriminals is not recommended |
| Malware removal | To eliminate the infection, you should scan your machine with a reputable security program, such as SpyHunter 5Combo Cleaner or Malwarebytes |
| System fix | After infection elimination, some changes made to the system previously might cause stability issues. If you experience lag, crashes, errors, and similar problems, utilize FortectIntego to fix them for you |
While there are no definite answers on how exactly Dodged ransomware is propagated, it is highly likely to be phishing spam emails that are sent to thousands of users thanks to tools like botnets. Nonetheless, there might be other methods the attackers may use, such as malicious ads, software vulnerabilities, drive-by downloads, software cracks, and many others.
Dodged ransomware is a new strain that was deployed by unknown actors. However, it has several functionality features that suggest that the attackers are planning on making it into a larger campaign later. The analysis shows that malware is equipped with anti-analysis features, which attempts to prevent the researchers from dissecting the sample in a sandbox or virtual machine environment. Typically, such malware exists without triggering the infection routine and performing other predetermined actions.
Besides this, Dodged ransomware is also capable of the following:
- hides its tracks by altering the appearance of some files/folders on the infected system
- exhibits system monitoring features by tracking mouse movements
- creates a variety of malicious files and places them on the system
- removes certain user files from the system (wiper)[2]
- deletes the shadow volume copies to prevent easy data recovery
- modifies Windows registry to establish persistence, etc.
Once the system modifications are complete, (note, not all of these can be reverted manually – you should use such repair software like FortectIntego to avoid reinstallation of the entire operating system) Dodged ransomware begins to scan the system for the relevant files. Typically, crypto-malware is programmed to encrypt files that are most commonly used, such as .pdf, .jpg, .doc, .zip, .mp4, and many others.
Currently, it is unknown which encryption method Dodged file virus is using to encrypt data. There are two different categories of encryption, symmetric (such as AES) and asymmetric (such as RSA).[3] While the way these two mothers operate differ, it does not make much difference for victims, as they are unable to access their files afterward regardless.
Besides encrypting files, Dodged ransomware is currently programmed to delete some personal files as well. This feature is typical of wiper-type ransomware, so the threat seems to be a hybrid.
At the final stage of the attack, Dodged ransomware drops a ransom note, (it also contains a 3 hour timer, although it is unknown if it actually change anything after the expiration) which reads:
Your PC has been locked.
Please, read the following instructions really carefully in order to ensure your PC's safety.Instructions
You may not try to terminate the program by the use of any tools / manually.
You MUST pay 150$ BITCOIN at the following page address in order to get your files back.
You may run / download any antivirus software / tool
You MUST not alterate any file in your computer, if you want all of them safe at least. =)
Do not try to decrypt any file manually / using any tool, its not going to work.Payment page:
Session ID:
Insert Decryption Key here:
While the attacks cannot be trusted, they are correct about file alternation using recovery software, as it may damage encrypted data permanently. To avoid that, you should make a copy of your hard drive (encrypted files, registry database, etc.) and only then remove Dodged ransomware from the system, followed up by attempts to recover files in an alternative way.
Spam emails – one of the most prominent malware distribution techniques
Ransomware is a lucrative business – there are experienced cybercriminal gangs operating some strains, while others are made by amateur hackers. Nonetheless, both types can cause significant damage to users who get infected with malware, as they might permanently lose access to their files. This is because malware infection and file encryption are two different processes, although the latter is only possible after the former is executed. Besides data locking, crooks now often leak the files before encrypting them to be able to threaten with public exposure – this is another extortion method that has been employed for a while now by major ransomware players, such as Maze, Sodinokibi, DoppelPaymer, and many others.[4]
What makes the situation worse is the COVID-19 pandemic, as the criminals rush to abuse the global situation and the relevance of the topic.[5] Many people are concerned and want to know as much as possible about the disease. For awhile now, cybersecurity researchers spotted multiple campaigns that target users and companies with coronavirus-themed phishing emails.
Typically, the attackers pretend to be from a reputable organization, such as World Health Organization or Centers for Disease Control and Prevention, as they use familiar logos, similar email addresses, social engineering, and other tactics. These emails are equipped with an attachment, which can come in various formats, including .doc, .pdf, .vbs, .exe, .zip, and others. Once opened, these files begin the infection process of the computer, finalizing it with data encryption.
Eliminate Dodged ransomware correctly
Many users are shocked or straight out confused as soon as they encounter ransomware. Some are not even aware of what ransomware is, or what it does, so locked data becomes a mystery. In many cases, such users also believe that they can return their data with Dodged ransomware removal, which is not the case at all.
While many ransomware viruses automatically delete themselves after the encryption is performed, others tent to operate on the system even after the process is complete with locking the incoming files. Therefore, it is best to scan the machine with anti-malware software and remove Dodged ransomware, its secondary payloads, and malicious components. However, this process should not be done before a full backup of the hard drive is prepared.
Once malware is eliminated (in case the Dodged virus is tampering with your anti-malware software, access Safe Mode with Networking as explained below), you can attempt to recover your data with the help of instructions we provide below. Unfortunately, there are no other safe methods to recover files currently, although security researchers might find bugs within malware's code that would help them create a free Dodged ransomware decryptor in the future.
Getting rid of Dodged virus. Follow these steps
Manual removal using Safe Mode
To access Safe Mode with Networking, perform the following actions:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Dodged using System Restore
System Restore might also be used for Dodged malware removal:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Dodged. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Dodged from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Dodged, you can use several methods to restore them:
Data Recovery Pro might be helpful in some cases
Data recovery software does not attempt to decipher encrypted files, but rather recover working copies from the hard drive. The less you use your machine post-infection, the more chances there are for this method to work.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Dodged ransomware;
- Restore them.
Make use of Windows Previous Versions feature
This method will only work if you had System Restore enabled prior to the infection, and the process is only applicable to separate files, and not data batches.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Employ ShaodwExplorer for data restoration
If you were lucky enough and Dodged ransomware failed to eliminate Shadow Volume Copies, use ShaodwExplorer to return your files.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No decryption tool is currently available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Dodged and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ MalwareHunterTeam. Some skidware ransomware sample as "COVID-20.exe". Twitter. Social network.
- ^ Sean Gallagher. Ransomware, “wiper” malware attacks have more than doubled, IBM team says. Ars Technica. IT news, reviews, and analysis.
- ^ Fundamental Differences between Symmetric and Asymmetric Encryption. RapidSSLonline. Partner of Trusted SSL Brands.
- ^ Tristan de Souza. Ransomware operators now publicly leaking victim data. Cyjax. Blog.
- ^ Danny Palmer. Coronavirus-themed phishing attacks and hacking campaigns are on the rise. ZDNet. Technology News, Analysis, Comments.







