EncoderCSL ransomware (Virus Removal Guide) - Quick Decryption Solution
EncoderCSL virus Removal Guide
What is EncoderCSL ransomware?
EncoderCSL ransomware is a data-locker that targets files with .txt and .test extensions on your computer
EncoderCSL ransomware is a HiddenTear-based file locking malware that was first spotted by multiple security researchers in mid-February 2020. Once inside the system, the virus applies the AES[1] encryption algorithm to lock a limited number of files located on the system, which appends the .locked extension to them as well. EncoderCSL ransomware virus currently only locks .txt and .test files on the host system, which is a clear indication that the malware is still in the experimental stage (fully functional ransomware usually targets all personal data).
After the encryption process, the EncoderCSL virus may drop one of the following ransom notes: READ.txt or READ_IT.txt, although this action is not fully functional yet – experts reported that the malware fails to deliver these text files. Nevertheless, it also displays a pop-up window, which explains why the files were compromised, and also states that victims should not attempt to recover the data without acquiring EncoderCSL ransomware decryptor for the hackers. Even if desired so, reaching criminals is impossible, as no contact details are provided.
| Name | EncoderCSL ransomware |
| Type | File locking virus, cryptomalware |
| Based on | HiddenTear |
| Main executable | EncoderCSL.exe, or another random name |
| File extension | Each .txt and .test file on the system is appended with .locked extension; for example, a “data.txt” file is turned into “data.txt.locked” |
| Encryption method | A symmetric encryption algorithm is used – AES (Advanced Encryption Standard) |
| Ransom notes | A pop-up message asks victims to view the READ.txt or READ_IT.txt files, but they are currently not dropped on the computer during the infection process |
| File recovery | Retrieving personal files without backups is almost impossible unless you were lucky enough and the malware failed to delete Shadow Volume Copies; additionally, in some cases, data recovery software might be able to recover at least some of encrypted files |
| Malware removal | Perform a full system scan with a security program that can recognize the threat |
| System fix | In case your Windows machine is crashing, showing errors, lagging, or suffering from other stability and functionality issues after ransomware termination, fix Windows with repair software FortectIntego |
Because the prevalence of EncoderCSL ransomware is relatively low, it is unknown what type of tactics threat actors use to distribute the malware. Nevertheless, the most common techniques include:
- Malicious spam email attachments or hyperlinks;
- Software vulnerabilities and exploits;
- Poorly protected Remote Desktop connections;
- Pirated program installers and software cracks/keygens;
- Fake update prompts and other fake messages, etc.
Once inside the system, EncoderCSL ransomware places its main executable (can be named as anything, although researchers found the “EncoderCSL.exe” in the wild) into the %Temp%, %Users%, or Desktop location and the begins the infection routine.
During this time, the malware deletes Shadow Volume Copies to prevent victims from recovering from the damages quickly, modifies the Windows registry to establish persistence, starts the “LocalSystem” service, loads several modules, reads computer information, etc.
Finally, EncoderCSL ransomware performs file encryption that only affects .txt and .test files – this will append the .locked extension to these file types. The .locked marker has been extensively used by various other Hidden Tear versions, as it is a default market that indicates which files have been compromised.
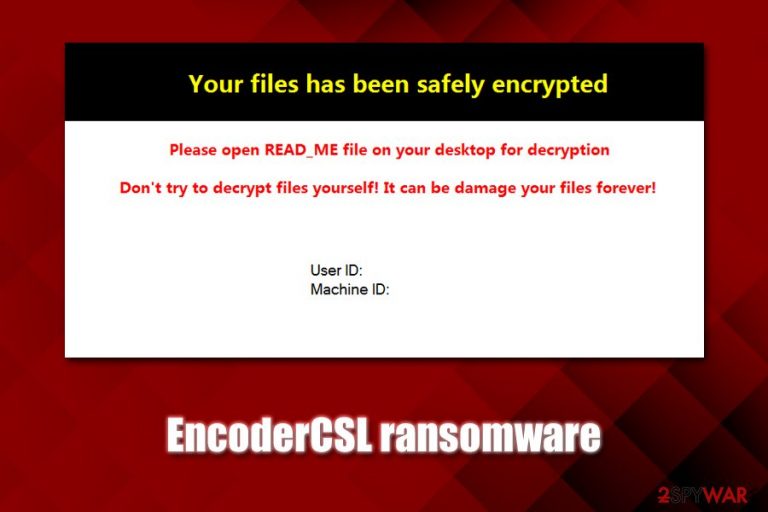
After the encryption process, EncoderCSL ransomware will display a pop-up message with the following text:
Your files has been safely encrypted
Please open READ_ME file on your desktop for decryption
Don't try to decrypt files yourself! It can be damage your files forever!
User ID:
Machine ID:
As evident, EncoderCSL ransomware virus developers are not native English language users, although guessing the origin of these people is impossible. Regardless of that, contacting them is impossible anyways, as they do not provide contact details, as there are supposed to be included within the text file on the desktop – it is nowhere to be found.
Even if the ransom note would provide the contact details, security experts[2] highly discourage users from paying the ransom, as victims may get scammed and never received the promised decryption tool. If you had no backups to restore your data, you could try using alternative solutions listed in our recovery section below.
The legacy of HiddenTear: malicious actors keep abusing the open-source project
HiddenTear is a notorious open-source project that was developed by a researcher from Turkey back in 2015. Since then, the code was leaked, and malicious actors quickly learned how to utilize it for illegal monetization purposes. Even many years after its release, various threat actors may attempt to modify the code and start distributing it using various methods, as it happened with EncoderCSL ransomware.
Nevertheless, the EncoderCSL virus is in the early development stage, as it does not match the criteria of fully functional ransomware just yet. Those infected, however, might lose all the encrypted files forever, as there is no way to contact malicious actors at present.
EncoderCSL ransomware removal is necessary, however, as the improved versions might be employed by authors in the future, applying a fully-working encryption function. In such a case, victims may not only lose their .txt or .test files, but also pictures, videos, music, documents, databases, PDF, and other data.
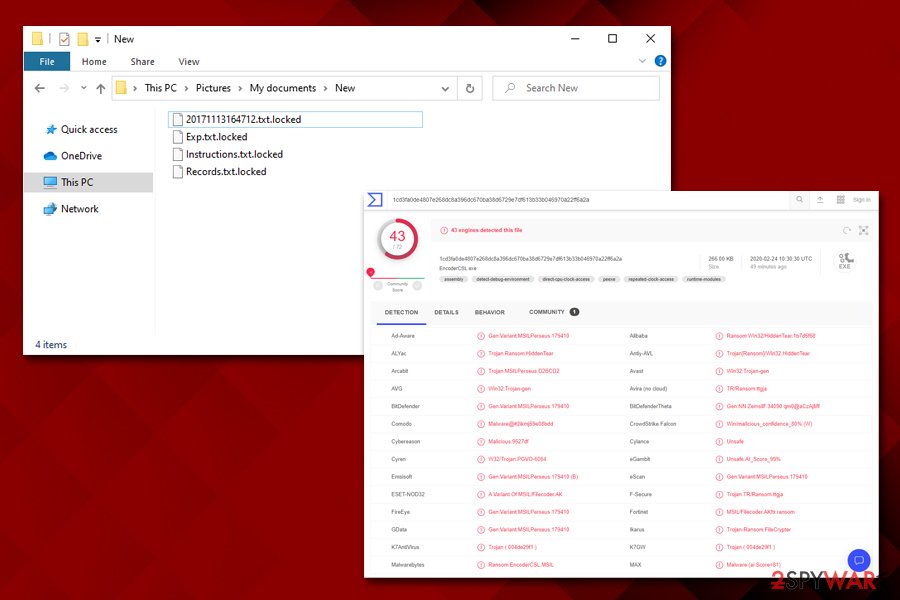
To remove EncoderCSL ransomware from the system, users need to scan their machines with anti-malware software that is capable of detecting and eliminating the threat automatically. According to Virus Total results, more than 40 different anti-malware engines recognize the main executable as follows:[3]
- Ransom:Win32/HiddenTear.gen
- Gen:Variant.MSILPerseus.179410
- A Variant Of MSIL/Filecoder.AK
- Win32:Trojan-gen
- Trojan[Ransom]/Win32.HiddenTear
- MSIL/Filecoder.AK!tr.ransom
- RDN/Ransom
- Mal/Generic-S, etc.
Nevertheless, we strongly advise you to make a copy of encrypted files before you get rid of the EncoderCSL virus, as its termination might permanently damage the data.
Ransomware distribution methods vary, so be prepared for all types of attacks
Ransomware is a very lucrative business currently, with many attacks being carried out against high profile companies, industries, government institutions, and also regular users.[4] The problem is highly complicated by the fact that ransoms are paid to criminals – these payments only fuels the illegal business. However, in some cases, enterprise entities and individuals simply have no other choice.
The best solution would be not being infected in the first place, and for that, adequate security measures are required. As mentioned previously, hackers may employ a single or multiple attack vectors (for example, Mool, Nppp, and other Djvu variants are being spread across the world with the help of software cracks exclusively, and this technique works extremely well, infecting hundreds daily), so it is important to ensure that comprehensive precautionary measures are applied:
- Do not let spam email attachment run a macro function (“Allow content”) or click on links inside;
- Update Windows and the installed programs as soon as possible to avoid software vulnerabilities from being exploited to infect malware automatically;
- Protect all your accounts with security passwords and use two-factor authentication where possible;
- Never download software cracks or pirated program installers from torrent and similar sites;
- Install anti-malware software that would use advanced protection measures, such as machine-learning technology;
- Backup your most important files regularly.
You should remove EncoderCSL ransomware after you backup the locked data
The immediate EncoderCSL ransomware removal might result in data compromise, so it is important not to do this immediately. As evident, the malware should be eliminated from the computer as soon as possible, as the infection may render it vulnerable to other cyber attacks.
Therefore, before you remove EncoderCSL ransomware virus from your computer, backup the encrypted files. If you do not care about the text files you have, you can skip this step and simply terminate the malware with the help of powerful anti-malware. Note that, in some cases, you will have to access Safe Mode with networking to prevent the EncoderCSL virus from tampering with your security tool.
Once you are sure that your system is clean, you can employ data recovery methods we provide below, although note that chances of these techniques being successful are very slim. Nevertheless, malware developers, including those behind EncoderCSL, might make mistakes that would allow security experts to create a free decryption tool. Considering how low the distribution of this malware is, the action is highly unlikely, unfortunately.
Getting rid of EncoderCSL virus. Follow these steps
Manual removal using Safe Mode
If your anti-virus cannot function in normal mode, access Safe Mode as explained below:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove EncoderCSL using System Restore
System Restore can also be used for EncoderCSL ransomware removal:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of EncoderCSL. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove EncoderCSL from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by EncoderCSL, you can use several methods to restore them:
Data Recovery Pro solution might be the right tool for you
While data recovery software is not designed to restore files that were encrypted by ransomware, they might be successful in retrieving at least some of the file copies from the hard drive.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by EncoderCSL ransomware;
- Restore them.
Try out Windows Previous Versions feature
This method will only work if you had System Restore enabled before the infection occurred.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer might save you from data loss
In case Shadow Volume Copies were preserved, ShadowExplorer should be able to recover all your files automatically.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No decryption tool is currently available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from EncoderCSL and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Advanced Encryption Standard. Wikipedia. The free encyclopedia.
- ^ Zondervirus. Zondervirus. Cybersecurity and malware insights.
- ^ EncoderCSL.exe. Virus Total. File and URL analysis.
- ^ Bianca Soare. This Year in Ransomware Payouts (2019 Edition). Heimdal Security. Security blog.







