Extension Settings browser hijacker (Free Instructions)
Extension Settings browser hijacker Removal Guide
What is Extension Settings browser hijacker?
Extension Settings is a potentially unwanted application designed to show fake search results filled with ads
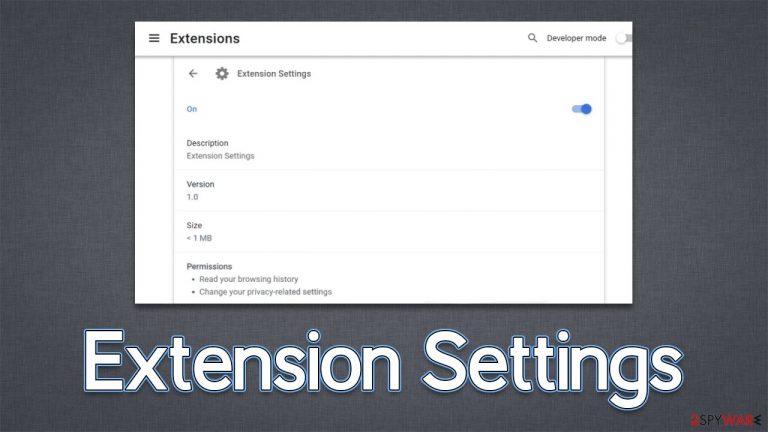
Extension Settings is a suspicious browser extension that you may find running on your Google Chrome, MS Edge, Mozilla Firefox, or another web browser. Most commonly, users install the app completely accidentally; this one can often be downloaded with freeware[1] from suspicious third-party websites, although installations via phishing websites are also just as common. In both cases, people don't willingly install the app.
As a browser hijacker,[2] the Extension Settings virus alters various browser settings and may start redirecting all search queries through ardslediana.com, consequently showing results via Yahoo or Google. While these providers are legitimate, their results can't be considered as such because they are altered by the hijacker. Thus, those infected would see plenty of intrusive ads while browsing the internet and also see promotional links at the top of the results.
We recommend you get rid of the infection as soon as possible, as this PUP is known to show malicious ads and direct people to phishing[3] websites. Keeping the app installed may result in you installing additional unwanted programs or even malware. Likewise, hijackers are known for their data tracking capabilities, so privacy is at risk as well.
| Name | Extension Settings |
| Type | Browser hijacker, potentially unwanted browser extension |
| Distribution | Software bundles, ads, redirects |
| Symptoms | Homepage and new tab address hijacked by the extension; promotional links are displayed as top search results; intrusive ads on various visited websites |
| Risks | Installation of other potentially unwanted programs or even malware, privacy risks due to information gathering practices, monetary losses |
| Removal | To remove the unwanted browser extension, you should access your browser's settings. Checking the system with SpyHunter 5Combo Cleaner security software can also ensure that there is no adware or malware running in the background |
| Other tips | Once you eliminate all unwanted and malicious programs from your system, make sure you clean your web browsers and repair system files. You can do that automatically with FortectIntego or refer to our manual guide |
How browser hijackers spread and how to avoid them
Browser hijackers are nothing new and have been around for quite some time. They fall into the “potentially unwanted program” category due to a few traits that the Extension Settings browser extension possesses as well. For instance, it is often installed alongside other freeware or shareware downloaded from third-party sources without user consent.
Software bundling is a common technique used by distributors to sneak additional, unwanted programs onto people's computers. This happens during the installation process of another program, which often occurs quickly and without much thought from the person installing it. For example, pre-ticked checkboxes give automatic permission to install extra apps, or there might be fine print that's difficult to notice.
In other cases, people may be tricked into installing suspicious software via misleading messages they encounter online. For example, Adshome.xyz, Julypromob2.click, or Magmaaffiliate.store might be spreading unwanted extensions using dubious methods. The best thing is to ignore these requests to download questionable software, as malware could be propagated via such sites as well.
Remove the Extension Settings virus
It shouldn't be a surprise that most browser hijackers are distributed via browser add-ons, as they are simple to create and modify. In reality, many hijackers are repackaged as new applications with no changes to the features they contain – save for a few cosmetic updates.
Extension Settings is not an exception to this, as its ads come from a browser. Removing an extension is easy; all you have to do is click on the “Extensions” button next to your browser's Settings menu and click “Uninstall.” If you want more direction, follow the instructions below.
However, we strongly recommend scanning the system with SpyHunter 5Combo Cleaner or Malwarebytes for the Extension Settings browser hijacker. Upon infiltration, it may create persistent items on the device and may return those if items are not eliminated as well.
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Mozilla Firefox
- Open the Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- Here, select the unwanted plugin and click Remove.

MS Edge
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

MS Edge (legacy)
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

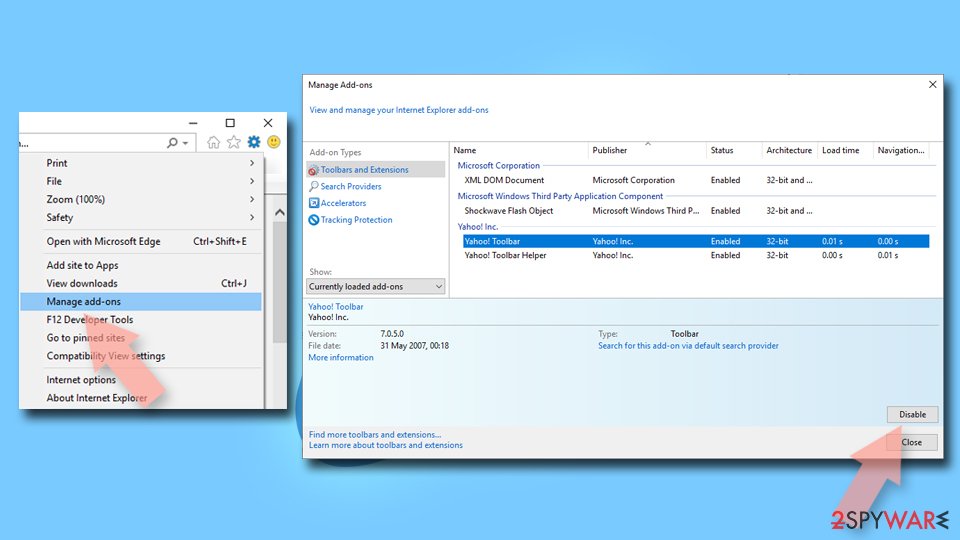
Internet Explorer
- Open Internet Explorer, click on the Gear icon (IE menu) on the top-right corner of the browser
- Pick Manage Add-ons.
- You will see a Manage Add-ons window. Here, look for suspicious plugins. Click on these entries and select Disable.
How to take care of your browser and other security tips
Browser hijackers, as we already stated, are notorious for their data-collecting abilities, and there are a number of things you can do to counteract them. Unfortunately, removing the extension would not achieve that aim because tracking cookies may remain in local cache directories. Use a PC maintenance and repair program FortectIntego if you want to remove them easily. If you'd prefer to perform it manually, go ahead and follow these steps:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

MS Edge (legacy)
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

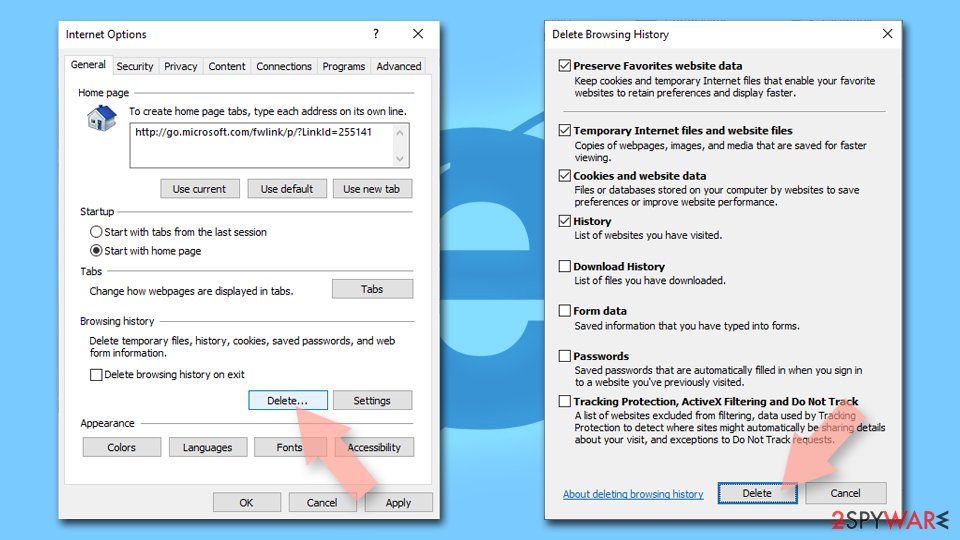
Internet Explorer
- Press on the Gear icon and select Internet Options.
- Under Browsing history, click Delete…
- Select relevant fields and press Delete.
How to prevent from getting browser hijacker
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ What Is Freeware?. Lifewire. Tech News, Reviews, Help & How-Tos.
- ^ Browser hijacking. Wikipedia. The free encyclopedia.
- ^ Phishing attacks. Imperva. Application and data security.
