Gilfillan ransomware (virus) - Free Instructions
Gilfillan virus Removal Guide
What is Gilfillan ransomware?
Gilfillan ransomware is a dangerous virus that locks all personal files on the system and then asks for a ransom
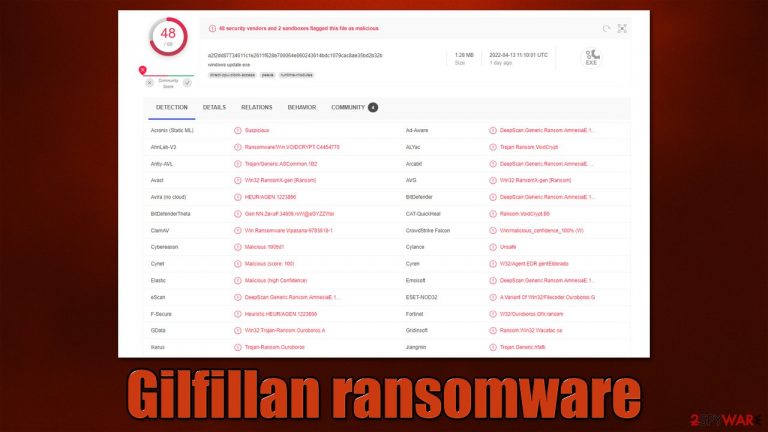
Gilfillan is a Windows computer virus that focuses on money extortion after locking all personal files. Suchlike data would be marked with .(ID)((PaulGilfillan@cyberfear.com).Gilfillan extension and would no longer be accessible to victims. In the ransom note Decryption-Guide.HTA or Decryption-Guide.txt, crooks claim that the only way to restore personal files is by paying ransom in Bitcoin cryptocurrency.
Since most home or work computers hold valuable documents and pictures, crooks are more likely to receive payments from victims who are desperate to get them back.
Ransomware is considered to be one of the most destructive types of computer viruses, although panicking now would not bring many positives. Instead, we recommend dealing with the infection correctly – we will explain how to remove the Gilfillan virus and provide alternative methods for data recovery.
| Name | Gilfillan virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .(ID)((PaulGilfillan@cyberfear.com).Gilfillan |
| Ransom note | Decryption-Guide.HTA, Decryption-Guide.txt |
| Contact | PaulGilfillan@cyberfear.com |
| File Recovery | The only secure way to restore files is by using data backups. If such is not available or were encrypted as well, options for recovery are very limited – we provide all possible solutions below |
| Malware removal | Disconnect the computer from the network and internet and then perform a full system scan with SpyHunter 5Combo Cleaner security software |
| System fix | Once installed on the system, malware might seriously damage some system files, resulting in crashes, errors, and other stability issues. You can employ FortectIntego PC repair to fix any of such damage automatically by replacing system corruption |
Malware family
Gilfillan ransomware stems from a relatively established malware family known as VoidCrypt, which first showed up in the spring of 2020 as a descendant of Ouroboros malware. Previous versions of the strain include GGR, RTX, Temlown, and many dozens of others.
The malware family is known for its use of rather complex extensions, which commonly include victims' ID, contact email, and an additional extension that matches the virus' version name. It typically uses AES + RSA encryption[1] method to lock files, although this may vary slightly depending on the version.
It was also noticed by security researchers that not all victims who paid the ransom had received the promised decryptor thus, cooperating with malware authors is highly risky.
Gilfillan ransomware characteristics and ransom note
There are plenty of ways for the ransomware to access victims' computers – malicious spam emails, fake updates, software vulnerabilities, software cracks, and other typical ransomware distribution methods used by criminals. Experts[2] recommend equipping the system with powerful security software to avoid similar infections in the future – we recommend using SpyHunter 5Combo Cleaner or Malwarebytes.
Once installed, the malware uses a combination of AES and RSA encryption algorithms to lock all data on the Windows machine. Before that, the system is configured and prepared for the data locking process – registry entries are altered, malicious files are dropped, and a connection with a remote server is established.
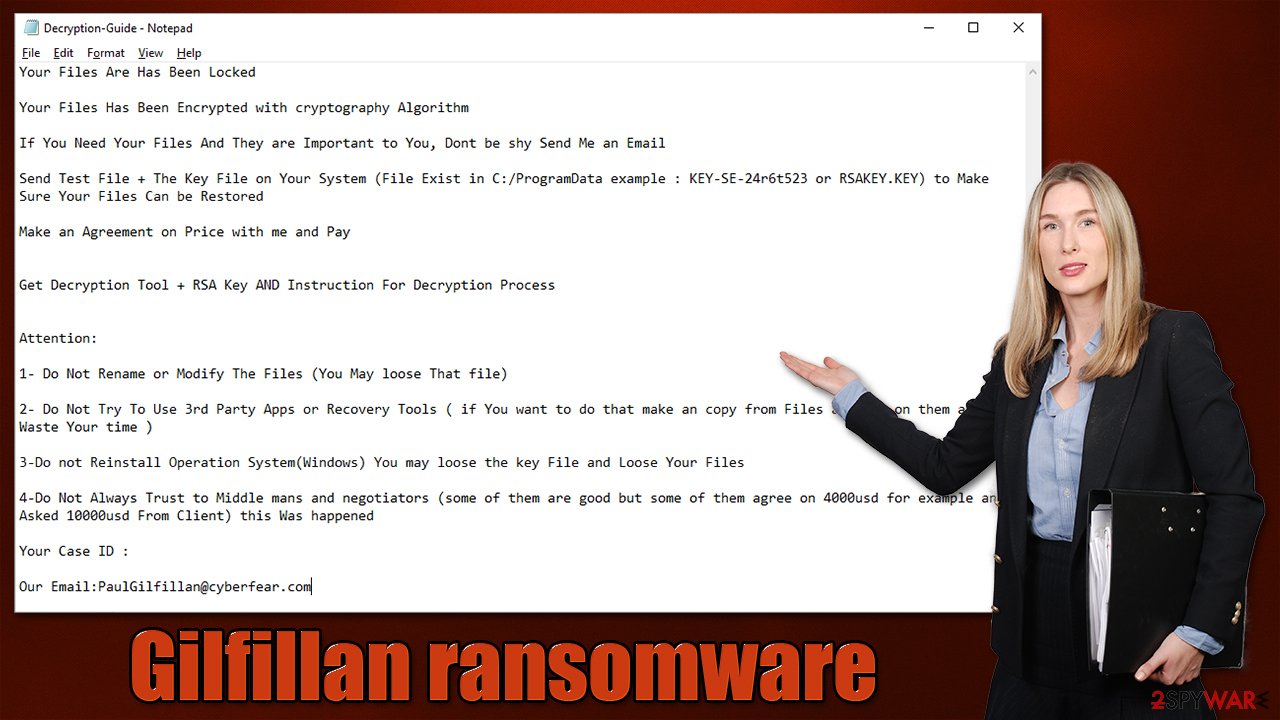
Soon after the data encryption process is finished, malware assigns a unique ID to each of the victims and then delivers two ransom notes – Decryption-Guide.HTA and Decryption-Guide.txt – contents of which are identical. They read:
Your Files Are Has Been Locked
Your Files Has Been Encrypted with cryptography Algorithm
If You Need Your Files And They are Important to You, Dont be shy Send Me an Email
Send Test File + The Key File on Your System (File Exist in C:/ProgramData example : KEY-SE-24r6t523 or RSAKEY.KEY) to Make Sure Your Files Can be Restored
Make an Agreement on Price with me and Pay
Get Decryption Tool + RSA Key AND Instruction For Decryption Process
Attention:
1- Do Not Rename or Modify The Files (You May loose That file)
2- Do Not Try To Use 3rd Party Apps or Recovery Tools ( if You want to do that make an copy from Files and try on them and Waste Your time )
3-Do not Reinstall Operation System(Windows) You may loose the key File and Loose Your Files
4-Do Not Always Trust to Middle mans and negotiators (some of them are good but some of them agree on 4000usd for example and Asked 10000usd From Client) this Was happened
Your Case ID :
Our Email:PaulGilfillan@cyberfear.com
As previously mentioned, Gilfillan ransomware authors might never deliver the required decryption key, even if the payment is made. This would only back up the illegal ransomware business, and crooks will continue their jobs by infecting even more users in the future. Before you decide whether or not to cooperate with the attackers (many security experts and we recommend avoiding all contact with hackers), we recommend trying to use alternative file recovery methods listed below.
Removal instructions
Your first task is to remove Gilfillan ransomware from your system. Before you attempt doing this, you should make sure that the affected machine is disconnected from the network and the internet. You can do that by clicking the “Internet access” button in the taskbar and disconnecting or simply plugging out the internet cable.
Once that's done, you should perform a full system scan with powerful anti-malware software, for example, SpyHunter 5Combo Cleaner or Malwarebytes. In case ransomware is tampering with this process, you can access Safe Mode and perform the scan from there:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
Data recovery
Once the encryption is applied to files, deciphering them becomes almost impossible, as the decryption key required to restore files is large and complex. It is usually stored on a remote server controlled by hackers, and, by using the user ID, they can distinguish which key would decrypt which victims' files.
It is important to note that data recovery and virus infection are two separate instances and should be treated as such. This means that by scanning your computer with security software, you will remove all malicious files that otherwise might continue to operate (and cause all the incoming files to be encrypted, for example). What this would not do is restore .Gilfillan files, as they will remain locked.
As we already mentioned, trusting cybercriminals is highly dangerous, as you might lose your money as well. Thus, we recommend you attempt to recover data using the alternative methods listed below.
Important: before you attempt to recover your files, make sure you make copies of all the encrypted data and put it on a separate medium, for example, a thumb drive.
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders which you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
Decryption tools might also be created for certain ransomware strains thanks to the efforts of security researchers. In some cases, law authorities seize the servers of malicious actors, which allows the keys to be released by the public – this is usually done by reputable security vendors. Here are a few links you might find useful:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

System fix
Once malware enters a Windows machine, it alters its operation in a way so that its goals can be reached. In the case of ransomware, it establishes remote connections, creates new registries or alters the existing ones, drops thousands of malicious files, etc. During this process, malware could potentially damage vital system files and components – damage that would remain after Gilfillan ransomware removal.
Consequently, your computer might start suffering from crashes, BSODs,[3] errors, and more stability issues. Instead of reinstalling the operating system, we recommend fixing it with a potent maintenance tool:
- Download FortectIntego
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ File Encryption. Webopedia. The Online Tech Dictionary for Students, Educators and IT Professionals.
- ^ Novirus. Novirus. Cybersecurity news and malware insights.
- ^ Blue screen of death. Wikipedia. The free encyclopedia.
