Howgrewchi.live ads (fake) - Free Guide
Howgrewchi.live ads Removal Guide
What is Howgrewchi.live ads?
Howgrewchi.live is a survey scam that seeks to gather user data for malicious purposes
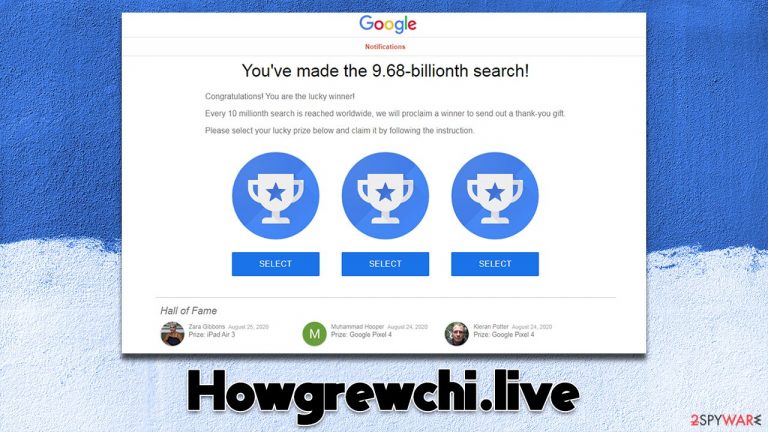
You might come across Howgrewchi.live by accident while using Google Chrome, Mozilla Firefox, Microsoft Edge, or another internet browser. It has been linked to a variety of frauds, although it generally focuses on phony surveys, gift cards, and fake giveaways. In other words, users are told that they can win a genuinely valuable gift by merely answering a few questions or by “selecting the box” from the three choices.
In reality, Howgrewchi.live does not have anything to win, as it is a scam. The main goal of the scammers is to convince people that they are the lucky ones, but when the time comes to retrieve the allegedly won prize, they would be asked to provide their personal details, which cybercriminals could later misuse.
We recommend not associating with this site and anything it offers, as you may differ from financial losses and privacy issues. Likewise, it is important to check the system for adware, as it may be the reason why you get redirected to phishing[1] websites in the first place.
| Name | Howgrewchi.live |
| Type | Scam, phishing, adware |
| Operation | Claims that the user has been selected for a free gift; those who proceed to reclaim the alleged gift are asked to provide personal details |
| Distribution | Adware, redirects from other websites, malicious links |
| Dangers | The objective of gift scams is typically to steal personal user information, but scammers might also lead users to harmful or inaccurate websites. This can result in privacy risks, virus infections, and financial losses |
| Removal | You may manually remove unwanted applications using our removal instructions below. If the nuisance ads and other irritant activities do not cease, you should scan your computer with SpyHunter 5Combo Cleaner antivirus software and eliminate all dangers automatically |
| Tips | We recommend scanning the system with FortectIntego to clean browser caches and repair virus damage automatically after eliminating PUPs and malware |
How manipulation earns illegal money
Technical support scams[2] succeed by taking advantage of people's fears. They try to scam people by showing fave virus infection alerts or imitating official scan results of security software, only to offer the “solution” of calling the fake technical support number, where they are then convinced that they need to pay for the services provided.
Another common type of online fraud is the fake giveaway or gift card scam, which manipulates people's emotions and tries to get them to install phony security software or call the claimed tech support. Happiness is another powerful human feeling that can cause excitement, and individuals may lose their heads when they are in this condition. The use of fake giveaways and gift cards to defraud people is one of the most widespread kinds of cybercrime out there.
Howgrewchi.live is a perfect example of such scamming attempts – it preys on gullible or vulnerable users who easily believe in actually being lucky. One of the best examples is the extremely popular “You've made the 9.68-billionth search!” scam (or its variations), which is hosted on numerous websites to this day – Spreadhugemultiply.xyz or Jsweepus.buzz are just a few examples.
As is common in social engineering[3] attacks, users are shown logos of familiar companies – in this case, Google – and are told that they were lucky and they have already won:
You've made the 9.68-billionth search!
Congratulations! You are the lucky winner!
Every 10 millionth search is reached worldwide, we will proclaim a winner to send out a thank-you gift.
Please select your lucky prize below and claim it by following the instruction.
They are then promised one of the expensive gifts, such as the newest iPhone, a smart TV, a gift card, or another valuable item. When users are convinced that they are lucky and about to receive a prize, they tend to forget what is actually happening and may even provide the information they are asked for.
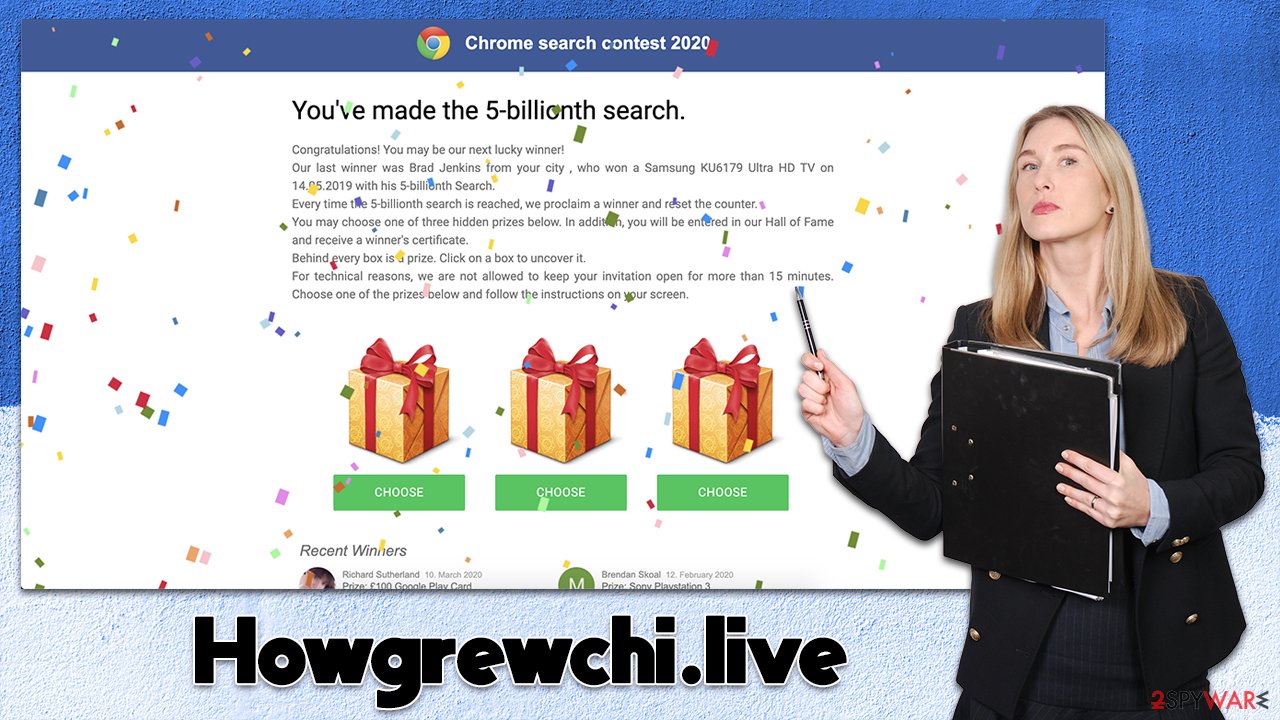
Dangers of survey scams
Once users are hooked, they are ready to receive their prize, although it is not as simple as it may seem initially. At this point, scammers come up with reasons for users to provide a lot of details they shouldn't need – at least they aren't needed to receive the item.
One of the most common details asked in survey scams is contact information (email, phone number). This information is later commonly used to push further scams, such as fraudulent calls. Additionally, email can be used to deliver all sorts of malware or direct people to spoofing websites to steal their credentials.
In other cases, Howgrewchi.live or any other website of this kind may ask for credit card details, usually with the pretense of “verification” or the charge for the alleged delivery fees. The main goal here is to make people provide these deals so they could be stolen and sold to cybercriminals, so please be wary of that.
Stop redirects to Howgrewchi.live and similar sites
We recommend taking these steps to ensure a safer and more pleasant computing experience: uninstalling programs at the system level, getting rid of suspicious extensions, and scanning your computer with SpyHunter 5Combo Cleaner, Malwarebytes, or another anti-malware program. Adware is one of the main reasons for malicious ads and redirects, so it's important to be thorough in your checks. Note that automatic removal with security software guarantees that your system is safe, so there's no need to use the manual steps listed below.
Windows
- Enter Control Panel into the Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till the uninstallation process is complete and click OK.

Mac
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To thoroughly remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Adware might also get installed as a browser extension. Even though this software can't have high permissions on the system and is much less impactful as a result, there are plenty of malicious extensions that could be tied to a program installed on the system. So, it's crucial to remove all potentially malicious browser extensions.
It is easy to get rid of add-ons: all you have to do is click on the “Extensions” button next to the settings menu to the right of the URL bar. Then, select More Actions and click Uninstall/Remove.
Another crucial step toward recovery is to make sure that adware or other unknown parties do not collect information about you automatically. Trackers such as cookies may be utilized when you visit a website or download adware-type software to follow your online activities every time. To prevent this, we suggest cleaning your browser caches right away using FortectIntego. You can also take the manual actions below:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

MS Edge (legacy)
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Internet Explorer
- Press on the Gear icon and select Internet Options.
- Under Browsing history, click Delete…
- Select relevant fields and press Delete.
How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Phishing attacks. Imperva. Application and data security.
- ^ Technical support scam. Wikipedia. The free encyclopedia.
- ^ Social Engineering. Imperva. Application and data security.
