idp.alexa.51 is it false positive or a virus? 2021 update
idp.alexa.51 Removal Guide
What is idp.alexa.51?
Idp.alexa.51 is a detection name for potentially malicious software by multiple anti-malware vendors
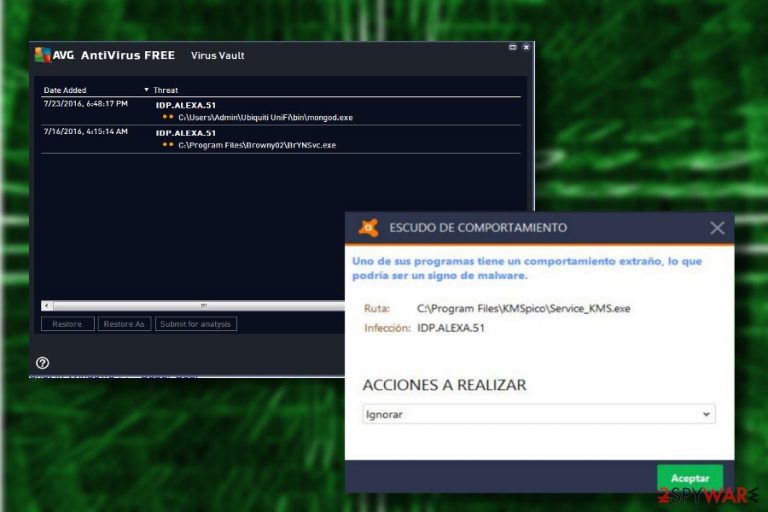
Idp.alexa.51 is a heuristic detection name typically used by Avast, AVG, or Avira[1] to flag potentially malicious activity on the computer. Essentially, it means that the infection has not been identified as such and was not associated with a particular malware family, although its behavior was suspicious enough for the AV application to flag it as malicious.
Users who downloaded and installed seemingly safe applications such as Plants vs. Zombies or SeaMonkey noticed that a pop-up shows up, detecting malicious files belonging to these programs in Temp and AppData folders. However, if these apps were downloaded from legitimate sources, it is highly likely that the Idp.alexa.51 detection is a false positive.[2]
However, you should be aware that this virus could also be a real issue. For example, users who downloaded Windows/MS Office suite crack KMSPico, also reported that they saw the warning from their anti-malware apps. In such a case, the detection is most likely flagging malware that could harm your computer and put your personal safety, as well as privacy, at risk. Thus, you should always check whether the detection is actually a threat or a false positive before performing further actions.
| Name | IDP.ALEXA.51 |
|---|---|
| Type | Malware or false positive detection name presented by AVG, Avira, and Avast |
| Symptoms | The malicious example causes system slowdowns, high CPU usage or system crashes. False positives are harmless |
| Distribution | Spreads in a bundle with SeaMonkey, Plants vs. Zombies, EasySpeedUpManager2, KMSPico, MyDailyLIfe, FiveM, and other games/apps/websites |
| Elimination | We recommend running a full system scan with anti-virus software to remove the infection |
| System recovery | In some cases, malware can damage the system in several ways, rendering it susceptible to lag, crashes, and errors. If you suffer from such issues, scan the computer with FortectIntego |
Idp.alexa.51 started showing up in 2016, when users began flooding the associated antivirus developers' forums with inquiries, asking whether the pop-up is indeed correct. This detection is primarily associated with online games or apps, such as SeaMonkey, Plants vs. Zombies, or potentially unwanted programs like EasySpeedUpManager2, and others.
The AVG scan results usually report this “file” or detection to stem from the .tmp and .exe files (e.g. swUSB.exe) located in c:\windows\, %appdata% and %temp% folders. Just to be clear: you should absolutely not ignore the article's culprit detection and scan a new file with another anti-malware to be sure that it is not a false positive.
According to the analysis being held a year ago, malicious detection prevails on the systems running 8.1 located in Portugal and Brazil. However, the extent of this erroneous detection did not decrease and is currently often found on Windows 10 systems running Avira and AVG. In some of the cases, the AVG firewall may block the installation of HitMan Pro reporting the HitmanPro.exe as an IDP.ALEXA.51 malware.
Since this infection can be related to various types of malware,[3] note that when AV engines detect this file as a malicious and dangerous one it is possible that the threat can:
- Download other malware;
- Use resources of the computer to run additional processes;
- Give attacker remote access to your device;
- Deliver advertisements, pop-up messages;
- Recommend fake updates, promote programs;
- Redirect to suspicious sites with commercial content;
- Record keystrokes and information you enter on various websites;
- Collect and send information about your PC to a remote server or hacker.
The detection is related to suspicious malware
Some cybersecurity researchers categorize this file as a Trojan horse or Alexa virus. Although there's no clear evidence for such classification, cybersecurity experts warn that the detection might not be a false alarm.
Reputable AV engines like AVG might recognize it as a false-positive detection or threat due to the outdated version running on the system (AVG 8.5, 9.0, 2011, 2012, 2013, 2014, or 2015) or outdated virus database. In 2017, the company acknowledged that this same problem had been triggered by a faulty AVG software update.
However, that's not the only reason why AV engines, not necessarily AVG, can report the article's culprit as a threat detected in various system locations. Malware developers can exploit such files or names of false AV detection to disguise malicious programs or processes.[4]
IDP.ALEXA.51 even has a few similarities with known trojans and other suspicious detection names like FileRepMalware and TrojanWin32/Tiggre!rfn. You should be aware of many possibilities that this is a virus and scan your device using SpyHunter 5Combo Cleaner, or Malwarebytes and see if malware is actually present on your machine. In case you are experiencing any type of post-removal issues, such as computer crashes or system errors, fix malware damage with the help of repair tools such as FortectIntego.
Suspicious files come with the system along with freeware
This is not one of the system's files. It is associated with various applications that can be downloaded from the Internet for free. It's not possible to reject the installation of this file component since it's a part of the software package responsible for its performance.
Although its original version is not considered malicious, it can be misused by hackers for disguising ad-supported apps, rogue software, or even malicious cyber infections. Therefore, each time you install games like Zombie vs. Plants or other free apps, make sure to select the Advanced or Custom installation option and read the terms carefully.
TIP: NoVirus.uk[5] experts recommend people not to let their young children download apps without your intervention as they will undoubtedly skip License Terms and Privacy Policy, thus exposing the system at the risk of being infected with potentially unwanted or malicious programs.
If it is a clear false positive, add IDP.ALEXA.51 to the exclusions list
In case the detection is indeed a false positive, all you have to do is to address your antivirus tool to remove Idp.alexa.51 pop-ups. First of all, you should make sure that your security tool is running the latest versions since the virus detection is often associated with anti-malware tools that run outdated databases.
As soon as you do that, you can check whether the pop-up persists (upon detection, potentially malicious files should be quarantined, so you should not worry about their presence at that point).In case the issue persists, you should download alternative security software and perform a repeated computer scan.
However, make sure you download anti-malware from the developers' website, as there are plenty of fakes that could damage your computer and result in Trojan, Spyware, Keylogger, and similar malware infection. Keep in mind that these infections can seriously compromise your safety and result in monetary losses or even identity theft. Alternative antivirus software would help you with malware removal, although you can also use the original tool for that.
Finally, if you are sure that Idp.alexa.51 detection is indeed a false positive, you can always add an exception via the security application's settings. This process differs depending on the utilized tool, and you can refer to the developer's website for step-by-step instructions on that.
How to prevent from getting malware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Julie Splinters. The Best Free Malware Removal Tools of 2018. 2-Spyware. The largest sources of security and tech-related information.
- ^ Javier Guerrero. False positives – What are they?. Panda. Security blog.
- ^ Roger A. Grimes. 8 types of malware and how to recognize them. CSOonline. Security news, features and analysis.
- ^ Chris Hoffman. How Hackers Can Disguise Malicious Programs With Fake File Extensions. How-To Geek. Online tech publisher.
- ^ NoVirus. NoVirus. Spyware and Virus news.
