LockerGoga ransomware (Virus Removal Instructions) - Mar 2019 update
LockerGoga virus Removal Guide
What is LockerGoga ransomware?
LockerGoga is a ransomware-type virus that recently attacked Norwegian aluminum producer Norsk Hydro and other companies
LockerGoga ransomware is a file locking virus that was initially discovered after attacks were launched against European companies, such as Altran Technologies in France.[1] Most recently, malware attacked high-profile Norwegian aluminum manufacturer Norsk Hydro, stopping some production lines, crippling its IT systems across most business areas, and forcing the company to switch to manual operations instead.[2] LockerGoga ransomware works very similarly to any other crypto-viruses: locks up files using AES-256 + RSA-1024 encryption algorithms, appends a file extension (in this case – .locked) and drops a ransom-demanding message README-NOW.txt. To free the data held hostage, victims have to email hackers via CottleAkela@protonmail.com, QyavauZehyco1994@o2.pl, DharmaParrack@protonmail.com, wyattpettigrew8922555@mail.com, or other, and find out what amount of Bitcoin is required for the alleged decryptor. The price usually varies, depending on how fast the company contacts cybercriminals. The malware also does a good job at evading detection, as the initial file is digitally signed (nevertheless, the certificates are now revoked). The malware was found changing victims' passwords and locking them out of the system. LockerGoga virus has similarities with such viruses like Everbe, GusCrypter, and Vurten.
| Name | LockerGoga ransomware |
|---|---|
| Type | Cryptovirus |
| First target | The French engineering consultancy Altran Technologies in January 2019 |
| Ransom note | README-NOW.txt |
| File extension | .locked |
| Related files | hvwfcsky1377.bin, Kopya.exe, worker32, b3d3da12ca3b9efd042953caa6c3b8cd, tgytutrc7290.exe |
| SSL signatures | Alisa LTD, Sectigo RSA Code Signing CA, USERTrust Secure, Kitty’s Ltd., Mikl Limited (all revoked) |
| Detected as |
|
| Contact emails | CottleAkela@protonmail.com, QyavauZehyco1994@o2.pl, DharmaParrack@protonmail.com, wyattpettigrew8922555@mail.com |
| Encryption algorithm | RSA-1024 and AES-256 |
| Distribution | Spam email attachments, brute-force attacks |
| Elimination | Use Malwarebytes for LockerGoga ransomware removal |
The first instance of this Goga ransomware virus was discovered involved the malware attack on an engineering consultancy firm that released an official press release to protect their users' data.[3] The company also shut down their network and applications because operations were already affected in some European countries due to this attack.
The victim of this LockerGoga ransomware, Altran Technologies revealed little information about the attack. Stephanie Bia stated in the press release:
On the 24th of January 2019, Altran was the target of a cyber attack affecting operations in some European countries.
To protect our clients, employees and partners, we immediately shut down our IT network and all applications. The security of our clients and of data is and will always be our top priority. We have mobilized leading global third-party technical experts and forensics, and the investigation we have conducted with them has not identified any stolen data nor instances of a propagation of the incident to our clients.
Our recovery plan is unfolding as expected and our technical teams are fully mobilized.
Throughout the process, Altran has been in contact with its clients, relevant governmental authorities and regulators.
Since LockerGoga ransomware virus is a cryptovirus, the main purpose is to encrypt files on the targeted system and then demand ransom for the alleged decryption. From the sample that has been analyzed “worker” and “worker32” are the processes this ransomware launches on the infected device.
The initial payload, however, often comes with files that are digitally signed by Alisa Ltd., Kitty’s Ltd., or Mikl Limited. This technique can help LockerGoga virus to evade detection. Fortunately, the digital signatures have since then been invalidated.
Before engaging in any type of activities, LockerGoga ransomware makes sure that the attacked device is not a sandbox[4] or a virtual machine. It was also spotted evading machine-learning kind of AV engines and sleeping over 100 times in some cases.[5]
When the payload is launched LockerGoga ransomware starts with its encryption and uses army-grade encryption algorithms RSA-1024 and AES-256.[6] Because the virus authors target large-scale organizations, the locked files are mainly document extensions, such as .doc, .pdf, .ppt, .xlm, .xlsx, .js, .pptx, .,db, etc. (31 document extensions in total). According to research, the encryption process only takes a couple of minutes, as LockerGoga utilizes every CPU core to run the process as fast as possible.
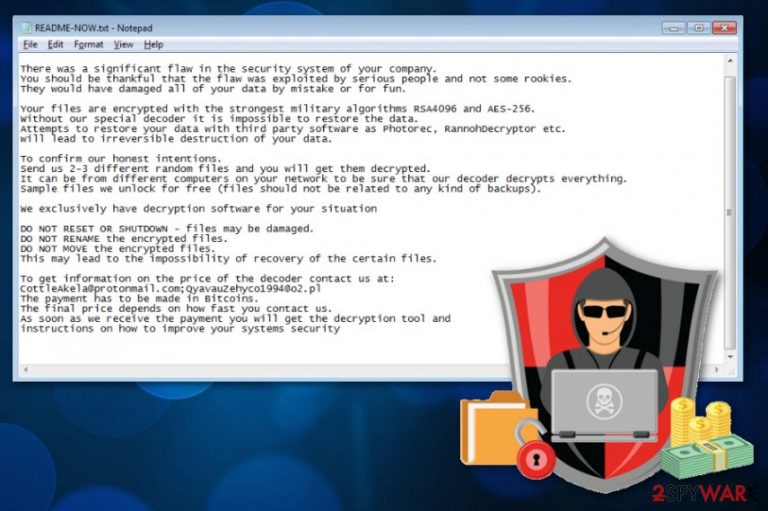
After the enctyption process, LockerGoga ransomware drops a ransom note which reads:
Greetings!
There was a significant flaw in the security system of your company. You should be thankful that the flaw was exploited by serious people and not some rookies. They would have damaged all of your data by mistake or for fun.
Your files are encrypted with the strongest military algorithms RSA4096 and AES-256. Without our special decoder it is impossible to restore the data. Attempts to restore your data with third party software as Photorec, RannohDecryptor etc. will lead to irreversible destruction of your data.
To confirm our honest intentions. Send us 2-3 different random files and you will get them decrypted. It can be from different computers on your network to be sure that our decoder decrypts everything. Sample files we unlock for free (files should not be related to any kind of backups).
We exclusively have decryption software for your situation
DO NOT RESET OR SHUTDOWN – files may be damaged.
DO NOT RENAME the encrypted files.
DO NOT MOVE the encrypted files.
This may lead to the impossibility of recovery of the certain files.
To get information on the price of the decoder contact us at: CottleAkela@protonmail.com;QyavauZehyco1994@o2.pl The payment has to be made in Bitcoins. The final price depends on how fast you contact us. As soon as we receive the payment you will get the decryption tool and instructions on how to improve your systems security
LockerGoga ransomware developers encourage victims to contact them via CottleAkela@protonmail.com and QyavauZehyco1994@o2.pl, but you shouldn't do that since it may lead to permanent data and money loss. As many researchers[7] advise, you need to terminate this virus and then focus on data recovery.
It is known that LockerGoga brings some malicious files together with it. Cybersecurity experts have discovered that the data is named hvwfcsky1377.bin – Kopya.exe, b3d3da12ca3b9efd042953caa6c3b8cd. Additionally, some computer security programs such as AVG and Avast detect the virus as Win32:Trojan-gen.
According to British security researcher Kevin Beaumont, LockerGoga did the following to the infected systems:[8]
Each impacted system had three key elements:
- They all ran Microsoft Windows.
- Files, including some system files, had been encrypted.
- The network interface on every system had been disabled.
- The local user accounts on every system had their password changed.
Nevertheless, this sample comes from the renowned Norsk Hyrdo attack, so the infection type might vary.
However, when it comes to LockerGoga ransomware removal from the network of a company, you need to employ experts, IT specialists and take the internet security seriously. Professional cyber security experts can determine the damage and possible fix issues with affected data. If you as an everyday user need similar help with your encrypted files, check our software suggestions below the article.
You need to remove LockerGoga ransomware using anti-malware tools like Malwarebytes because this threat installs more files on the system and affects other parts of the device. You may also benefit from virus damage removal using FortectIntego or similar PC repair tools.
Another high-profile LockerGoga target: Norsk Hydro
Located in Oslo, Norway, Norsk Hydro is the largest aluminum producer in the world, manufacturing almost half a million tons of the material a year. The company is also known for its activity in other sectors like solar power technologies, hydropower, and oil industry.

The attack occurred on late Monday, January the 18th when Norsk Hydro IT staff noticed suspicious activity on the IT systems. Initially, and up till now, the company does not directly relate the compromise to LockerGaga ransomware, although Norsk Hydro CFO Eivind Kallevik did confirm that the attack is related to a file locking virus and that the situation is “quite severe.”
Norsk Hydro is now forced to switch to manual handling of the operations, and the staff is told not to log in to any IT systems. The company immediately contacted third-party security forensics to assist with the situation, and are actively trying to recover from the attack. Many workers are asked to work multiple shifts to minimize the losses. Kallevik commented to Reuters:[9]
It is mostly direct labor: some of the activities that we use computers to do, today we use manual labor. We have to add some more people.
According to him, the company is able to provide all the services and process all customer orders as usual, although it is not clear whether the future procedures will be affected, as the official website is down currently. Norsk Hydro is now focusing on continuing regular operations via manual methods, minimizing the financial and operational losses, and recovering the IT systems using backups.
Due to LockerGoga ransomware attack, the aluminum prices went up to record-high in the past three months, and the company's stock price went down by 3.4%, which later went back up by 0.8%.
Update: Norsk Hydro is recovering from the attack with the help of such sources like Microsoft
Later in March, MalwareHunterTeam discovered a new sample of LockerGoga which was also uploaded from Norway, so security team believes that it was used in the Norsk Hydro attack. This variant of the virus uses new contact details – DharmaParrack@protonmail.com and wyattpettigrew8922555@mail.com.
The company published a press release announcement[10] that explains the situation further. According to Norsk Hydro, it is recovering from the attack with the help of external parties, such as Microsoft, and are not planning on paying ransom to LockerGoga authors. Instead, the company is focusing on recovering all the crucial data from backups.
Most of the company's procedures are running as usual, although some employees are still forced to perform some manual operations. By far the biggest downfall of the attack was that the company could not access a full list of customer orders, as stated in the press conference release by Chief Financial Officer Eivind Kallevik on Thursday.[11]
Despite promising leads, Norsk Hydro did not detail anything further:
Hydro still does not have the full overview of the timeline towards normal operations, and it is still too early to estimate the exact operational and financial impact.
Despite that, based on the samples published on Virus Total and insight from multiple security researchers, it is clear that hackers managed to break-in to the company's networks and then gained access to Active Directory server. From there, the attackers spread LockerGoga ransomware laterally, as the virus does not have the capability of propagating itself on the network.
After encrypting files, LockerGoga disabled hardware (network cards) from working and also changed passwords of every account, preventing anybody from accessing their workstations. This scheme is performed in order to slow down the recovery operations, as each PC needs to be taken care of separately, instead of uploading backups from a cloud service.
According to research from Cisco Talos team,[12] LockerGoga is much closer to a destructive type of malware – wiper, rather than ransomware. Nevertheless, it is just a theory, and the real goals of hackers are only known by them.
Email box may get filled with infected emails
Spam email campaigns grow to a new level when emails may even go to your regular email box directly and look legitimate and safe because malicious actors use names like DHL, FedEx, Amazon or PayPal to make the impression of legitimacy.
When you receive an email, you were not expecting to get make sure to pay more attention to details. Often subject lines like Invoice or Order information tell about the questionable content of the email, especially when the name of a service is not familiar.
You should delete suspicious emails and avoid opening files attached because documents or PDF files can contain malicious macros or even direct payload. This is the main distribution technique when it comes to crypto malware like miners or ransomware.
Eliminate LockerGoga ransomware and check if the system is clear before other steps
We can understand that LockerGoga ransomware virus is a severe threat and file encryption is the primary concern of yours. However, we cannot stress enough how important it is to terminate all related processes and clean the device entirely before focusing on anything else.
Remove LockerGoga ransomware using anti-malware tools like FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes and scan the device fully so that all virus damage can be fixed. You can use a few tools and scan the system a few times to double-check because ransomware is a persistent cyber threat.
When the LockerGoga ransomware removal is done, you can proceed with data recovery options. The best solution for this should be data backups on the external device. However, not everyone has up-to-date backups. For this reason, we have a few suggestions of software and features on your computer that may help in file recovery.
Getting rid of LockerGoga virus. Follow these steps
Manual removal using Safe Mode
Try rebooting the device in the Safe Mode with Networking before a thorough system scan:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove LockerGoga using System Restore
Get rid of LockerGoga ransomware using System Restore feature on your PC:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of LockerGoga. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove LockerGoga from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by LockerGoga, you can use several methods to restore them:
Data Recovery Pro can help with encrypted files
When LockerGoga ransomware encodes your data or you accidentally delete files, Data Recovery Pro helps to restore them
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by LockerGoga ransomware;
- Restore them.
Windows Previous Versions feature helps in file recovery
Try Windows Previous Versions feature as an alternative to file backups
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
You can use ShadowExplorer
It seems that LockerGoga ransomware is not affecting Shadow Volume Copies. If so, you can restore data with ShadowExplorer
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Decryption is not available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from LockerGoga and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ France's Altran Tech hit by cyber attack. Reuters. Business & Financial news, US & International breaking news.
- ^ Norsk Hydro: Hydro subject to cyber-attack. Oslo Bors. Oslo Stock Exchange.
- ^ Stéphanie Bia. Information on a cyber attack. Globenewswire. Resource of press releases.
- ^ Sandbox. Techopedia. Where Information Technology and Business Meet.
- ^ What You Need to Know About the LockerGoga Ransomware. Trend Micro. Security blog.
- ^ AES and RSA encryption. Boxcryptor. Encryption software to secure cloud files.
- ^ Lesvirus. Lesvirus. Spyware related news.
- ^ Kevin Beaumont. How Lockergoga took down Hydro — ransomware used in targeted attacks aimed at big business. Doublepulsar. Cybersecurity from the trenches of reality, written by Kevin Beaumont.
- ^ Gwladys Fouche, Terje Solsvik. Aluminum maker Hydro battles to contain ransomware attack. Reuters. Business & Financial News, US & International Breaking News.
- ^ Update on cyber attacks March 21. Hydro. Official press release announcement.
- ^ Cyber attack on Hydro update and status as of march 20. Webtv. Streaming television.
- ^ Ransomware or Wiper? LockerGoga Straddles the Line. Talos Intelligence. Security research group.







