Mike ransomware (Quick Decryption Solution) - Virus Removal Guide
Mike virus Removal Guide
What is Mike ransomware?
Mike ransomware – a money-demanding threat that originates from the HildaCrypt malware family
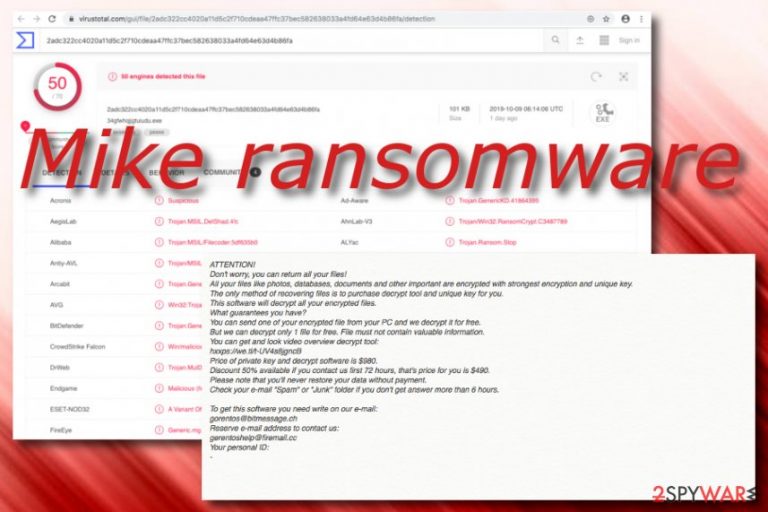
Mike ransomware, found by GrujaRS researcher,[1] is a newly-released malware strain that comes from HildaCrypt ransomware category. Asymmetric/symmetric encryption such as AES-256 and RSA-2048 is used to lock up files and add the .mike appendix next to each file name. For example, if you have a file named flower.png, it will be modified to flower.png.mike. After that, Mike virus will drop a ransom-demanding message named _readme.txt which is the same one used by Djvu ransomware forms. The message urges for $490 as a 50% discount from the original price if the victims are fast to contact the criminals in 72 hours. Also, gorentos@bitmessage.ch and gerentoshelp@firemail.cc email addresses are provided for communication purposes. However, some good news is that the criminals have already released the decryption software for .mike files and no ransom payments are needed anymore.[2]
| Name | Mike ransomware |
|---|---|
| Type | Ransomware virus |
| Family | This newly-released cyber threat originates from HildaCrypt malware family |
| Appendix | After files are locked, the ransomware virus places the .mike appendix next to each file name |
| Cipher | Data is encrypted by using unique encryption algorithms such as AES-256 and RSA-2048 |
| Ransom note | This malware strain employs the same _readme.txt ransom message which is used by Djvu ransomware versions |
| Price | The criminals urge for $490 as a 50% discount from the original price. If the victims are too late to pay the demanded ransom in 72 hours, they will have to transfer the whole $980 amount |
| Contacts | The hackers provide two email addresses for communication purposes: gerentoshelp@firemail.cc, and gorentos@bitmessage.ch |
| Spreading | Ransomware viruses are capable of spreading through hacked TCP port 3389, fake email messages that supposedly come from FedEx or other reputable companies, software cracks that are placed on p2p networks such as The Pirate Bay |
| Removal | First, scan your entire Windows computer system with FortectIntego. Afterward, go to the end of our article an view the automatical removal possibility for Mike virus or use the official key |
Mike ransomware tries to scare people by claiming that the only way to restore your data is by purchasing the decryption tool from the cybercriminals. However, we do not recommend doing that as you might get scammed and waste your money for completely nothing. Besides, there are other alternatives instead as the developer of this malware has recently released the official decryption key himself.
Continuously, note that Mike ransomware might also be capable of damaging the Windows hosts file. Such threats do that because it prevents victims from accessing security-related forums. This decreases the chances that the victim will not find proper removal instructions for the ransomware virus and data recovery tips.
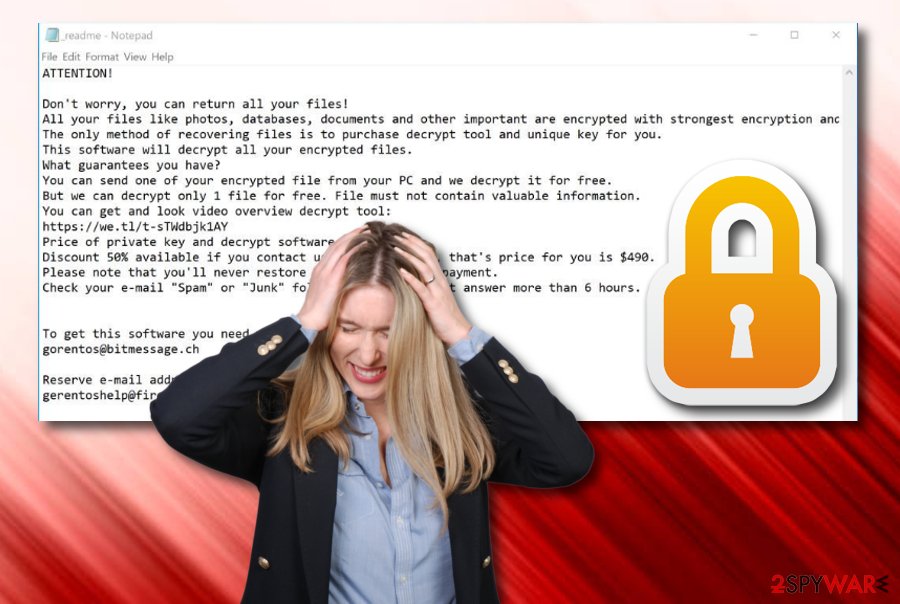
Continuously, Mike ransomware, just like other file lockers, can delete Shadow Volume Copies of encrypted documents/files by executing specific PowerShell commands. If this happens, it will harden the data recovery process for you. However, there still is no reason for letting the cybercriminals scam you and swindle your money.
In addition, Mike ransomware offers to provide evidence of the existing decryption software. According to the _readme.txt ransom message, the crooks suggest sending them one small file for free recovery:
ATTENTION!
Don't worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-UV4s8jgncB
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
gorentos@bitmessage.chReserve e-mail address to contact us:
gerentoshelp@firemail.ccYour personal ID:
–
Furthermore, Mike ransomware might add additional malware to your computer system during its installation process. For example, you might end up with a Trojan horse, worm, or cryptocurrency mining virus on your machine. These threats also posses big harm to the system and software of your PC.
If you want to prevent all of the risks mentioned above, you should remove Mike ransomware from your Windows operating system by employing reputable antimalware products. Besides, carry out a full system scan with a tool such as FortectIntego to locate all the malicious entries and files that the threat might have left in your Windows Registry or Task Manager.
Depending on what type of antivirus program you are employing, it can should different detection names for Mike ransomware. According to the VirusTotal database,[3] this malware is detected as Win32:Trojan-gen, Trojan.MulDrop11.18818, Trojan.GenericKD.41864395 (B), Ransom.HildaCrypt, etc.
Note that, Mike ransomware removal is not a process to play with so you have to eliminate the malware only with professional software, otherwise, you might bring harm to your system. Once you are done with the deletion, continue by reading valuable tips on how to prevent repeated ransomware infections in the future.
Spreading capabilities of ransomware viruses
Developers who promote ransom-demanding malware often camouflage the malicious payload in different ways so that it would have a better chance of reaching victims' computers. Very often, the criminals pretend to be from official shipping organizations such as FedEx/DHL, banking companies, and other reputable firms.
The hackers aim to drop harmless-looking email messages to random people and wait for them to get tricked. Usually, cybercriminals add attachments that include “important information” or drop links straightly into email messages that are supposed to look like “order confirmation” hyperlinks.
Continuously, some ransomware forms are delivered to the computer system via vulnerable programs that lack updates or through cracked software that one can get on a p2p network[4] such as The Pirate Bay, eMule, or Torrents. The original program or file here is usually replaced with the malicious payload.
Last but not least, some crooks manipulate vulnerable RDP configuration and reach the targeted OS by hacking the RDP and forcible inserting the password required for accessing the machine. It is known that criminals often abuse the TCP port 3389 for their malicious activities.
Secure yourself from ransomware attacks and keep data safe
Security experts from LesVirus.fr[5] want to underline the importance of keeping your computer system ultimately secured. First of all, every user needs to ensure that he/she holds reliable AV protection. If you already have antimalware software, just make sure that the program is regularly updated.
Continuously, DO NOT open any email messages that bring a bogus look to you, especially, if the letters have traveled to the spam section. However, finding unexpected email in your inbox still needs an investigation. Check the message for possible grammar mistakes, evaluate the entire content, and scan the attached files (if there are any) with antimalware.
To add, you should always stay away from third-party downloading websites, the so-called peer-to-peer sites. If you want to download/install a particular product, you should better get it from the original developer or secure sources at least. Make sure to avoid any web pages that are marked as unsafe to proceed with.
For data safety, you should always store copies of important documents and files on multiple remote devices/servers. For example, you can copy files to another computer, iCloud/Dropbox, and also put them safely in a USB flash drive. This makes your data files almost impossible to access for other people, including bad actors.
Mike ransomware removal + data recovery
We are here to help you to remove Mike ransomware from your Windows OS properly. First, note that a thorough system scan is required for a successful removal process. In this case, you should employ a trustworthy system scanning program such as FortectIntego, SpyHunter 5Combo Cleaner, or Malwarebytes.
Afterward, you can continue with the Mike ransomware removal process automatically. Keep in mind that you should not try to get rid of the cyber threat without any professional help as you might make system-damaging mistakes some of which can even result in severe unrepairable machine damage.
Once your computer has been cleaned from .mike files virus, you can start looking for data recovery possibilities. We have placed some methods below and hope that you will find them advantageous. Remember that almost any other alternative is definitely a better option than paying the crooks.
Getting rid of Mike virus. Follow these steps
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Mike from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Mike, you can use several methods to restore them:
Employ Data Recovery Pro to reverse some data back to its previous state:
Use this software to recover some files that were encrypted by the ransomware virus.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Mike ransomware;
- Restore them.
Windows Previous Versions feature might help you with file restoring:
Employ this software for file recovery. However, ensure that you have launched System Restore in the past.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Use Shadow Explorer for unlocking some data:
If the ransomware virus did not eliminate Shadow Volume Copies on your Windows OS, use the following instructions to activate this tool.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Download the decryption tool here.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Mike and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ GrujaRS. GrujaRS. Cybersecurity reseacher. Twitter. Social platform.
- ^ Emsisoft Decryptor for HildaCrypt. Emsisoft. Unlock your files without paying the ransom.
- ^ 50 engines detected this file. VirusTotal. File information.
- ^ P2P. Tech Terms. Definitions.
- ^ LesVirus.fr. LesVirus. Cybersecurity news source.
