On this day i hacked your OS (Free Guide) - Removal Instructions
On this day i hacked your OS Removal Guide
What is On this day i hacked your OS?
On this day i hacked your OS is a Bitcoin scam that extorts money from victims by claiming to damage their device
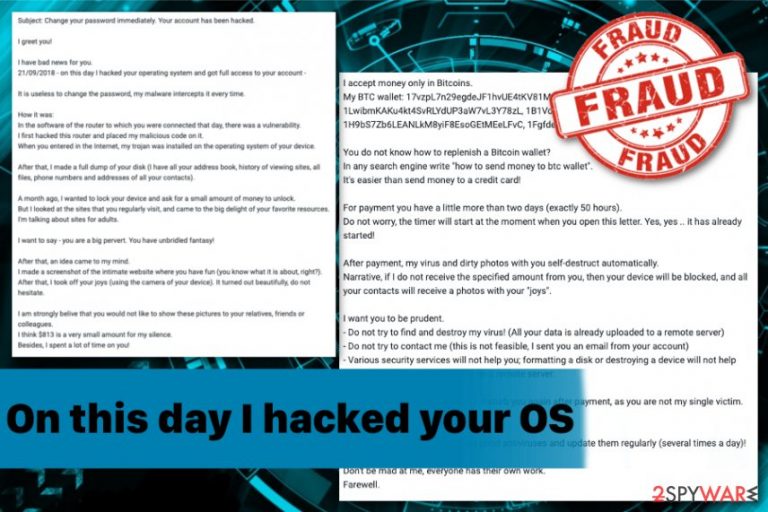
On this day i hacked your OS is the email scam that tricks people into transferring payments to avoid their details leaked. This email message aims to scare victims by telling that users' computer is hacked and the account can be deleted if the demanded amount is not paid in time. Scammers require payment in Bitcoin to their account or information captured from your device, that even includes webcam shots, get send to your colleagues or friends. Various samples of this scam demanded up to $760 in Bitcoin, but you may encounter a different version.
The email message is threatening and even contains information about the particular victim like passwords or their full names. On this day i hacked your OS scam developers gather such information and send the message with the proof that they can access personal details and affect significant parts of the machine. Scammers even claim they have been spying on your for a long time and there is even more sensitive data. However, this is a fraudulent message, and you need to avoid contacting criminals in any way because it may lead to real privacy issues or identity theft.[1]
| Name | On this day i hacked your OS |
|---|---|
| Type | E-mail Scam |
| Tactics | Trick victims into paying demand amount of Bitcoins |
| Ransom amount | $760 |
| Distribution | Phishing email campaigns[2] |
| Elimination | Get the reliable anti-malware program and remove On this day i hacked your OS alongside other malware involved |
| Possible danger | Can lead to exposed personal details, identity theft, privacy issues, installation of more severe malware |
On this day i hacked your OS is the letter that you need to ignore and remove after receiving. Scammers are cybercriminals, and contacting them cannot give positive results. Especially when the message about your OS getting hacked is fake and designed to only scare you into paying the ransom.
This is On this day I hacked your OS virus, not a legitimate message nor the real hacker email. This social engineering technique is used to make ransom demands more convincing. Unfortunately, the email is an indicator of malware program running on the machine.
Note that you need a full system scan to remove On this day I hacked your OS from the computer. Scammers behind the message may even change settings of the device to keep running in the background, so reboot your PC in Safe Mode with Networking before removing viruses with FortectIntego or a similar tool.
Once you encounter such email scams, the message can be especially scary and disturbing. On this day I hacked your OS scam email reads the following:
I have very bad news for you. 03/08/2018 – on this day I hacked your OS and got full access to your account {victim’s bank account} On this day your account {victim account} has password: {some type of password. So, you can change the password, yes.. But my malware intercepts it every time.” [… technical nonsense here …] “And I got an idea…. I made a screenshot of the adult sites where you have fun (do you understand what it is about, huh?). After that, I made a screenshot of your joys (using the camera of your device) and glued them together. Turned out amazing! You are so spectacular! I’m know that you would not like to show these screenshots to your friends, relatives or colleagues. I think $760 is a very, very small amount for my silence. Besides, I have been spying on you for so long, having spent a lot of time! Pay ONLY in Bitcoins! My BTC wallet: 1FgfdebSqbXRciP2DXKJyqPSffX3Sx57RF
Although the contents of the email can differ, the main message is based on extortion. On this day i hacked your OS emails can look even legitimate because of the included personal information, but passwords or full names can be used from previous scams. There are many similar email scams like:
Scammers use fear to convince victims to send them money. This is why you should remove On this day I hacked your OS as soon as possible. There is no guarantee whatsoever that they will delete your data or leak any personal information. You cannot be sure that those files even exist.
Get anti-malware program and scan the machine thoroughly so On this day I hacked your OS removal gives the best results possible. Receiving such emails can result in the installation of other malware. This is the best method of virus removal, according to security professionals.[3] We can recommend FortectIntego or SpyHunter 5Combo Cleaner for this process, make sure to download the application from a legitimate source to avoid additional cyber infections.
Targeted scams go around the world via email campaigns
These scamming emails are caused by malware that runs on the machine and generates additional frustration with background processes. However, the initial email message comes to your email box in particular because scammers already had your email address and other personal details. This is due to other scams and information gathered during such campaigns or even data breaches.[4]
Other malware operations can also be the reason you receive this email scaring into paying the ransom. Malware infiltration either involves email campaigns during which malicious files get installed on the machine or insecure freeware installations that include unwanted programs downloaded behind users' back.
You should remove any suspicious emails that contain questionable information or is sent from service and companies you don't use at the time. Also, note how dangerous it can be to get software cracks or download freeware from unreliable sources. Always choose Advanced or Custom options during such installations and avoid automatically installed PUPs and malware.
Avoid such extortion scams by cleaning the machine thoroughly and terminating On this day I hacked your OS virus as soon as possible
You need to remember that On this day i hacked your OS virus is a result of additional adware or more severe malware that collects your information and this way scammers can use such details to extort cryptocurrency from you. This malware elimination requires professional tools designed to clean the computer fully.
Choose the antivirus program wisely for On this day I hacked your OS removal and download that program from either official developer or reliable provider. This way you can be sure that there is nothing packed with the program.
Remove On this day i hacked your OS with FortectIntego, SpyHunter 5Combo Cleaner, or Malwarebytes and clean the system entirely. Additionally, you can reboot the PC in Safe Mode before running a system check, so all possible intruders get detected and deleted.
Getting rid of On this day i hacked your OS. Follow these steps
Manual removal using Safe Mode
Try rebooting your PC in Safe Mode and then remove On this day I hacked your OS
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from On this day i hacked your OS and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting spam tools
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Identity theft. Wikipedia. The free encyclopedia.
- ^ Alan Yu. Elaborate phishing scams increasingly target universities. Whyy. Media organization.
- ^ Dieviren. Dieviren. Spyware related news.
- ^ Data breach at JustDial leaks 100 million user details. Economictimes. Business news.
