Your account was hacked (virus) - fake
Your account was hacked Removal Guide
What is Your account was hacked?
Your account was hacked scam is the message used for direct extortion via email
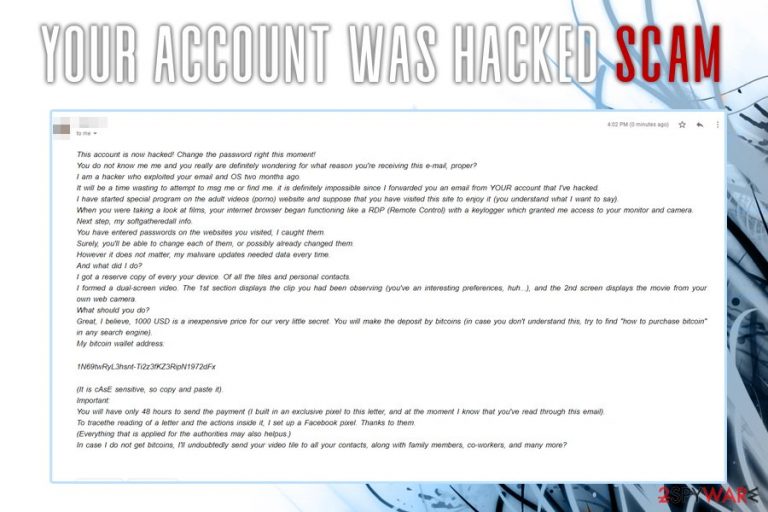
Your account was hacked is a scam email message used by scammers as a social engineering[1] technique to trick people and extort their money. The message contains alleged information about the supposed hacker attack during which a supposed victim has been caught on a webcam while visiting porn sites and now has to pay $1,000 in Bitcoins within 48 hours to prevent public exposure. This fake email message is distributed via inboxes of random e-mail users whose e-mail addresses have been leaked somewhere.
The scam attempts to convince victims that malware is installed on their machines and that it managed to breach the installed camera (regardless if it is the case in reality). Allegedly, the bad actors planted spyware into adult-oriented websites, and the user managed to get infected there.
The fraudulent email author then claims that the recording of the user via the webcam was taken when he or she visited porn sites. The hacker then asks for as much as $1,000 to be transferred to a provided Bitcoin wallet to keep the allegedly recorded video away from the victim's family and friends.
| Summary | |
| Name | Your account was hacked |
| Type | Money extortion scam |
| Distribution | Via email service |
| Similar scams | I have bad news for you, I'm a programmer who cracked your email scam, I am a spyware software developer email scam, Porn Blackmail scam, etc. |
| Risk factors | Money loss, sensitive information disclosure to hackers, malware infections, etc. |
| Actions to be taken | Delete the email and never contact crooks, scan your computer with anti-malware and change all your passwords |
| Recovery | If your system was infected, scan it with FortectIntego to fix virus damage |
As evident, this is merely a scam and should never be trusted, as these emails are just a part of a much broader campaign that targeted tens of thousands of users worldwide. If you received such an email, immediately remove Your account was hacked email from your inbox and never communicate with cybercriminals.
In this article, we will provide scam removal instructions, along with what to do to increase your online safety after a potential account compromise.
Scam authors claim that the email address itself is compromised
Despite that many different scams were created previously, they all had one goal: to make victims believe that their computers are infected with malware and that they need to pay Bitcoins to keep the compromising video away from their friends and family.
In most of the previous cases, bad actors used a compromised email password as a “proof” that the allegations about malware infection are true. Data breaches are relatively common and affect industry giants, including:
This time, however, Your account has been hacked email scam authors claim that the email address itself is compromised, as the “From” address appears to be from the victim himself/herself. This is due to a technique called email spoofing – it allows hackers to any type of email address to appear in the “From” line. It is very typical for scams where users are misled by seemingly original Amazon, Google, UPS, or other contact email address.
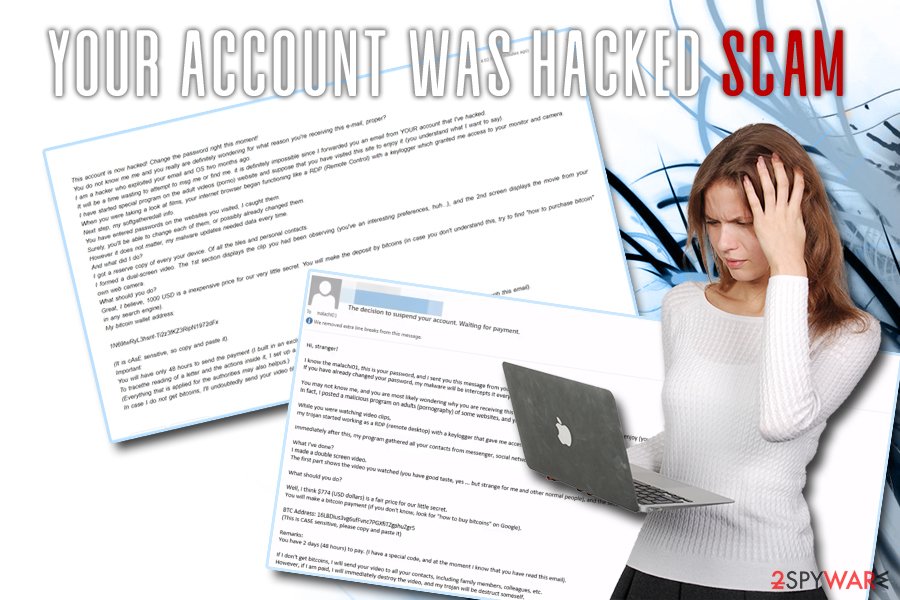
According to cybercriminals, the initial breach occurred when the victim visited porn websites, and the login credentials were stolen. Using the RDP (Remote Desktop Protocol) connection, hacks claim full control of the machine.
This scam is a prime example of social engineering attempts that are aimed at less experienced computer users, as using terms as “malware” and “spyware,” along with a seemingly logical explanation of how the infection occurred might make many believe that the email is real and that their privacy is actually in danger.
Here's what crooks behind Your account was hacked write in one of the variants (be aware that it may differ):
Your account was hacked! Renew the pswd right away!
You probably do not know me me and you may be certainly wanting to know for what reason you're receiving this message, right?
I'm ahacker who burstyour emailand devices and gadgetsnot so long ago.
Do not attempt to msg me or alternatively try to find me, it is definitely hopeless, because I sent you a letter from YOUR hacked account.
I installed spyware on the adult vids (porno) website and suppose you enjoyed this site to enjoy it (you know what I mean).
During you have been watching content, your browser started out operating as a RDP (Remote Control) that have a keylogger that granted me authority to access your desktop and webcam.
Afterward, my programobtainedall information.
You have typed passcodes on the websites you visited, I caught all of them.
Surely, you could possibly change each of them, or perhaps already modified them.
But it really doesn't matter, my malware renews it every time.
And what did I do?
I compiled a reserve copy of every your system. Of all files and personal contacts.
I got a dual-screen video recording. The 1st section demonstrates the video you were observing (you've got a good preferences, ahah…), the second screen demonstrates the movie from your camera.
What should you do?
Great, in my opinion, 1000 USD is basically a reasonable amount of money for this little riddle. You'll do the deposit by bitcoins (in case you don't understand this, go searching “how to purchase bitcoin” in any search engine).
My bitcoin wallet address:
The crooks then further claim that victims only have 48 hours to pay before the shameful video is released. Criminals also claim that they know when the email was read due to the pixel that is inserted inside. Note how they are trying to substantiate every action they allegedly do on users' machines.
Simply because hackers actually use these tools and terms, many can fall for the scam, as they do not wish such a video being exposed to those that matter the most – family and friends. As we previously mentioned – it is a scam, do not trust it and simply delete the malicious email and never contact criminals.
Nevertheless, it is worth mentioning that, your account or computer safety might be compromised due to the breached personal information, for example, an email address, login credentials of various accounts, etc. Therefore, it is worth scanning your device with tools like SpyHunter 5Combo Cleaner and FortectIntego to ensure it is clean and there is no malware installed.
Extortion scams pose a tremendous risk
Extortion scams are nothing new, although previously the real photos or videos were held hostage to make victims pay. Nevertheless, bad actors are always coming up with new ideas, and sextortion scams now claim malware infections, remote code execution, RDP connection, and other tricks that real cybercriminals use to spread computer viruses.
Nevertheless, some of the extortion scams are real and might affect users in many different ways. For example, a similar form of blackmail is used in ransomware attacks, although it is users' files that get locked, and criminals demand payment for the decryption key that could give back the access to users. Talking about ransomware, some of the extortion scams convince users into installing the infamous Azorult trojan, which consequently downloads GandCrab ransomware.
Sextortion scams might result in not only financial losses but also in psychological problems, as one in four victims seek help from medical professionals[4]. Many people are ashamed of the situation, and some of them even resort to suicide.[5] Due to the nature of such scams, it is believed that the number of the affected is much higher than the estimated, as most of such cases remain unreported.

Do not get tricked by malicious scam emails
The possibility of getting infected with malware that might actually track your every move usually comes from spam emails. The fake messages often include attachments that ask users to enable macro feature or hyperlinks that lead victims to a malicious domain where the virus is downloaded and installed automatically.
Therefore, never trust suspicious emails, and be warned that most of these end up in Spambox, which means that the email was recognized as malicious by built-in scanners. Nevertheless, the ever-evolving techniques might prevent the engine from identifying scam messages, and they might end up in the Inbox. Therefore, exercise extreme caution when dealing with spam.
Other methods hackers use to proliferate malware include:
- Exploit kits;
- Malicious ads;
- Fake updates;
- Infected or repacked installers;
- Unprotected RDP;
- Credential stuffing;[6]
Therefore, make sure you run security application, enable Firewall, update your system regularly and avoid high-risk sites (especially torrents that distribute software cracks or keygens).
You should delete “Your account was hacked” email and never pay the ransom in Bitcoin
If you received an email that claims that this account has been hacked! Change your password right now, you should first report the incident to your local authorities that handle fraud cases. They might ask you to send them the received message, so do not remove fraudulent emails straight away. Nevertheless, do not contact bad actors or pay the demanded sum, as you will only end up losing the money.
The next step would be scanning your device with reputable security software, such as FortectIntego or SpyHunter 5Combo Cleaner. If the cybercriminals did infect your PC with any type of malware, anti-malware software would be able to detect and remove it immediately. However, we recommend performing the scan in Safe Mode with Networking, as some severe infections might tamper with the anti-virus program and prevent it from working correctly. We explain how to access Safe Mode in the instructions below.
Additionally, you should change all your passwords, especially the one you use for your email, and enable two-factor authentication for all your accounts. Finally, use a password managing software that would keep all your accounts away from cybercriminals. Once you complete all these steps, you can proceed with Your account was hacked email removal.
Getting rid of Your account was hacked. Follow these steps
Manual removal using Safe Mode
In case the virus is tampering with your security application, enter Safe Mode with Networking as follows:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Your account was hacked and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting spam tools
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Social engineering (security). Wikipedia. The free encyclopedia.
- ^ David Volodzko. Marriott Breach Exposes Far More Than Just Data. Forbes. American business magazine.
- ^ The Ticketmaster breach – what happened and what to do. Sophos. Cybesecurity blog.
- ^ Aimee O'Driscoll. What is Sextortion (with examples) and how can you avoid it?. Comparitech. Tech researched, compared and rated.
- ^ Lizzie Dearden. Five British men have killed themselves after falling victim to online 'sextortion', police reveal. Independent. International magazine.
- ^ Luke Christou. Cybercriminals have your password, and businesses are paying the price. Verdict. Email newsletter.
