I hacked your device (Removal Guide) - updated May 2020
I hacked your device Removal Guide
What is I hacked your device?
I hacked your device is the email scam that tricks people into thinking their device has been hacked to demand payment
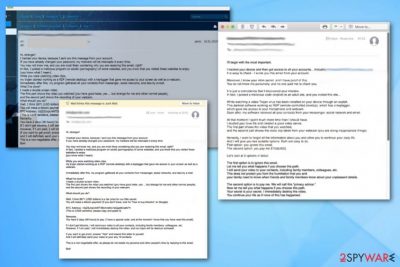
I hacked your device is the fake email message stating about the infected or hacked device and email. This is a social engineering attack that focuses on scaring people and demanding payments.[1] Senders claim that they have some compromising information collected with the help of the keylogger or the trojan horse that will be revealed if the victims don't pay the ransom. High-pressure Porn blackmail scam informs the user that personal images, porn-related browsing history, and similar personal data were captured by a camera on the device, and can be leaked to friends from the contact list.
These types of scams are everlasting and there are tons of versions of emails that state about hacked, infected devices, or sensitive information. Some of them ask for payments directly like I know your password email scam, so the keystroke loggers and malicious sites with such functions can record credentials of cryptocurrency exchange platforms, and similar services. But other tactics may include redirects to malware- delivering pages or direct contact with scammers. There is no reason to think that your device is really affected or hacked when you receive such notification. Try to ignore the email itself and scan the machine with AV tool to ensure that any possible intruders get removed completely.
| Name | I hacked your device |
|---|---|
| Type | Email Scam |
| Category | Malware |
| Symptoms | Email stating about possibly hacked account or device, questionable activities on the system, online banking or shopping accounts |
| Main danger | Identity theft, changed or stolen passwords, illegal access to your accounts/devices |
| Tactics | Tricks people into paying the demanded ransom to avoid revealing compromising/personal information |
| Distribution | Email messages |
| Elimination | Get an antivirus tool and scan the machine fully to remove I hacked your device |
| Payment amount | The amount, most of the cases, is around $1000. The price can go up or down depending on the variant and scammer. It also can be demanded to transfer funds in the form of cryptocurrency |
| Main purpose | To get profit from scared victims, gain access to devices and steal valuable information |
| Additional tip | Anything related to the malware infiltration and system damage can lead to serious issues and affected machines, so you should run FortectIntego or a PC repair tool that can find affected files and replace corrupted system files with safe ones |
To fake the credibility, scammers who spread I hacked your device email scam messages may even include your real password of the email account. This is possible because people keep using the same passwords for different accounts that can be hacked if not protected properly. Additionally, they claim that they installed a keylogger or the Trojan horse on the system. In this case, you cannot be sure that they haven't, so a proper system scan is highly recommended to prevent serious problems.[2]
However, in most cases, I hacked your device scam is the malware that emerges inside an email only. If you received such spam, reset your passwords immediately. While in most of the cases, the statement about your hacked device or email account is false, renewing your passwords won't do harm.
The message stating “I hacked your device” seems credible because it reveals some confidential information like victim's email address, some passwords or states about videos or photos captured via the camera on the affected device. Scammers have also been using a technique helping them to make the email look like it came from the victim's email address. However, this technique doesn't mean that your email account got hacked and is rather social engineering than truth.
The scam is similar to other spam campaigns:
- Your account was hacked
- I have bad news for you
- I'm a programmer who cracked your email
- I know your password email scam
- I infected you with RAT
I Hacked Your Device email messages can differ from victim to victim, but the more recent variant looks like this:
Hi, stranger!
I hacked your device, because I sent you this message from your account.
If you have already changed your password, my malware will be intercepts it every time.You may not know me, and you are most likely wondering why you are receiving this email, right?
In fact, I posted a malicious program on adults (pornography) of some websites, and you know that you visited these websites to enjoy
(you know what I mean).While you were watching video clips,
my trojan started working as a RDP (remote desktop) with a keylogger that gave me access to your screen as well as a webcam.Immediately after this, my program gathered all your contacts from messenger, social networks, and also by e-mail.
What I’ve done?
I made a double screen video.
The first part shows the video you watched (you have good taste, yes … but strange for me and other normal people),
and the second part shows the recording of your webcam.What should you do?
Well, I think $671 (USD dollars) is a fair price for our little secret.
You will make a bitcoin payment (if you don’t know, look for “how to buy bitcoins” on Google).BTC Address: 1GjZSJnpU4AfTS8vmre6rx7eQgeMUq8VYr
(This is CASE sensitive, please copy and paste it)Remarks:
You have 2 days (48 hours) to pay. (I have a special code, and at the moment I know that you have read this email).If I don’t get bitcoins, I will send your video to all your contacts, including family members, colleagues, etc.
However, if I am paid, I will immediately destroy the video, and my trojan will be destruct someself.If you want to get proof, answer “Yes!” and resend this letter to youself.
And I will definitely send your video to your any 19 contacts.This is a non-negotiable offer, so please do not waste my personal and other people’s time by replying to this email.
Bye!
The I hacked your device virus should be safely ignored and deleted from the inbox. However, if you clicked some link or downloaded the attachment to your computer, you can become a victim of a targeted virus attack that aims to infect the system with serious malware and cause more havoc on it.
I hacked your device is not a real message you should trust. It is trying to extort money from huge and profitable companies or rich people in particular. The email is typically sent over the internet to numerous victims to increase the chances of extorting money from unaware people. This method works because people are typically trying to avoid any data loss. However, scammers have nothing on you and the alleged compromised information is non-existent.
You need to remove I hacked your device message from the email box and avoid clicking anything on the email itself or contacting people behind this scam. Make sure to avoid paying the ransom because any interaction with scammers can lead you to permanent money loss. Remember that there is no need to pay because your device is not hacked at all.
To make sure that I hacked your device scam hasn't infected your computer with malware (trojan, keylogger, etc.), scan the machine thoroughly with anti-malware program. These viruses can pose a serious danger on your computer, so their removal is a must. We can recommend using FortectIntego for the possible virus damage elimination. Make sure to choose a reputable program when selecting anti-malware tool, so there is no risk of getting affected by other cyber infections.
Interacting with hackers can lead you to numerous dangers
I hacked your device removal is especially needed because this email scam focuses on getting money from its victims. The data that is allegedly captured by scammers is not going to be leaked even when you do not pay the demanded ransom. Experts[3] note that cybercriminals may also request more money when you pay the first sum.
Interacting with I hacked your device email scam message can lead to:
- installation of malware like keystroke loggers[4] or trojans;
- remote hacker access on the system;
- directly installed ransomware;
- real privacy issues due to revealed or stolen data.
I hacked your device is not a message you should trust and the best thing to do is to ignore it. If you ever run in similar scams in the future, be aware that any information that you reveal can be misused against you, so avoid any contact with these hackers as all of their claims are stated just to gain income from gullible people.
Additionally, in some cases, scams such as I hacked your device might enter the computer system if any type of potentially unwanted program is installed on it. If you have been receiving specific scam apps regularly, you should perform a full computer scan and check the possibility that an adware app or similar program might be hiding on your machine.
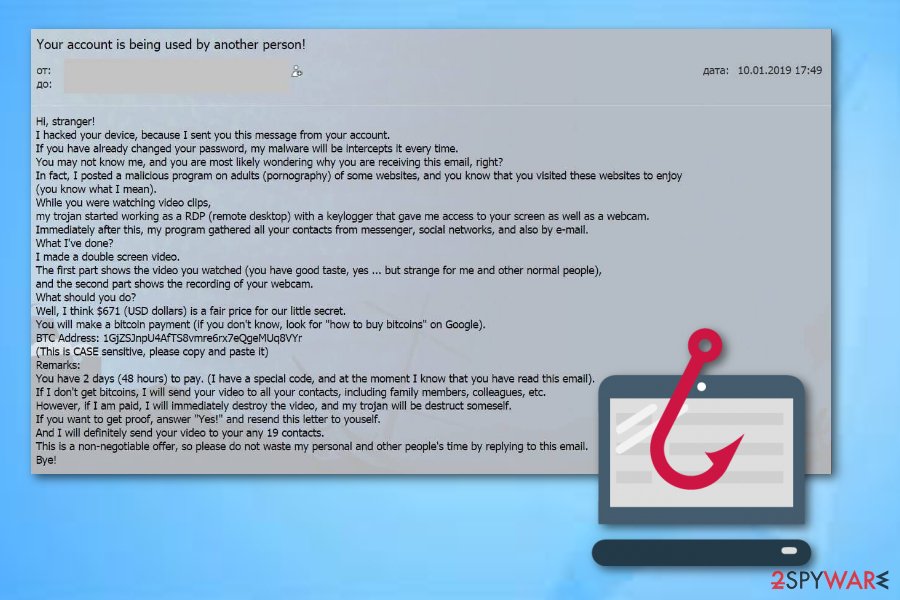
A popular version of the scam – I installed RAT into your device
I hacked your device is a scam that has some similar versions and I installed RAT into your device is one of them. Talking about this current variant, it tricks people by claiming that a Remote Access Trojan (RAT) has been installed on the system by using the EternalBlue exploit.[5]
The main goal of I installed RAT into your device scam is to trick people and swindle money from them. This misleading message states that adult-themed videos of the user will be posted on the web if a particular amount of money is not transferred to prevent such exposure.
RATs, also known as Remote Administration Tools, are used to give cybercriminals remote access to the targeted machine or device. This way, such tool (either legitimate or illegal) allows completing suspicious activities, e.g. running malware in the background, collecting personal information, swindling money, and so on.
However, Remote Administration Tools are not always malicious. Some of them might be used by trustworthy security experts that tend to fix system-related errors remotely. Sadly, RATs are often used for malware-based purposes all over the Internet and it might be hard to identify a harmful one at first.
Spam email campaigns distribute malware due to careless user behavior
Paying close attention to emails you get and files you open from the attachments can help you avoid various cyber infections and scary attacks like email scams or different phishing campaigns. Scammers can achieve their goals when users open and download such files from attachments.
Often documents, PDFs and archive files contain malicious scripts or even virus payloads. Installation of such scripts lead to cyber infections and appearing of such scam messages. Unfortunately, you cannot see the initial virus infiltration because there is no permission of the user required.
You can avoid the installation of malware if you keep away from opening suspicious and unknown emails or their attachments. This is the best way to keep your machine virus-free. Additionally, you should keep the anti-malware program on the machine and run the full system scan from time to time. This way any suspicious behavior and applications get blocked.
Eliminate I hacked your device email scam and clean the machine entirely
Having a computer infected by I hacked your device scam can cause more issues on your system in general because your privacy, financial data, and online browsing safety can be at risk. However, don't believe the message claiming that scammers have information about you or compromising videos. This is a lie used to swindle your money or installing real malware.
If you got this message from scammers, make sure you remove I hacked your device scam from your email because keeping it there is no point or can even be dangerous. Additionally, make sure you are not infected because there is always recommended checking the system to make sure that there is no need to remove malware. For that, opt for the automatic system cleaning solution.
While I hacked your device removal is an easy part, the system check requires attention and professional anti-malware tools. These programs can remove all intruders and fix possible damage, clean the machine from infected files, and other malware-related to this scam. Some security and PC repair applications can also work for additional double-checking and virus damage fixing. Try FortectIntego, SpyHunter 5Combo Cleaner, or Malwarebytes.
Getting rid of I hacked your device. Follow these steps
Manual removal using Safe Mode
You may benefit from Safe Mode with Networking while removing viruses caused by I hacked your device email scam:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove I hacked your device using System Restore
Try recovering the system with System Restore feature:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of I hacked your device. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from I hacked your device and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting mac viruses
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Social engineering. Wikipedia. The free encyclopedia.
- ^ Francis Navarro. This new email scam can steal your direct deposit paycheck. Komando. WestStar Multimedia Entertainment.
- ^ Viruset. Viruset. Spyware related news.
- ^ Margaret Rouse. Keylogger. TechTarget. Search security.
- ^ ETERNALBLUE | THE NSA-DEVELOPED EXPLOIT THAT JUST WON’T DIE. Sentinelone.com. Tech blog.





















