Payfast ransomware (virus) - Recovery Instructions Included
Payfast virus Removal Guide
What is Payfast ransomware?
Payfast ransomware is a type of malware that prevents you from accessing your files
Malicious programs are created more rapidly in the past few years, and the illegal business of ransomware has seen an extreme rise. Payfast virus, which belongs to a relatively prominent malware family Zeppelin, is yet another attempt by cybercriminals to monetize victims' misfortune.
Once installed on the system, it performs severe changes to not only the Windows system but also personals files. In fact, the changes of the former are conducted to ensure that the file encryption is performed without any problems. Using a combination of sophisticated algorithms AES and RSA, ransomware encrypts documents, pictures, videos, and all other data on the computer. It excludes several locations on the system, allowing it to function (as destroying system files is not the goal of ransomware infections).
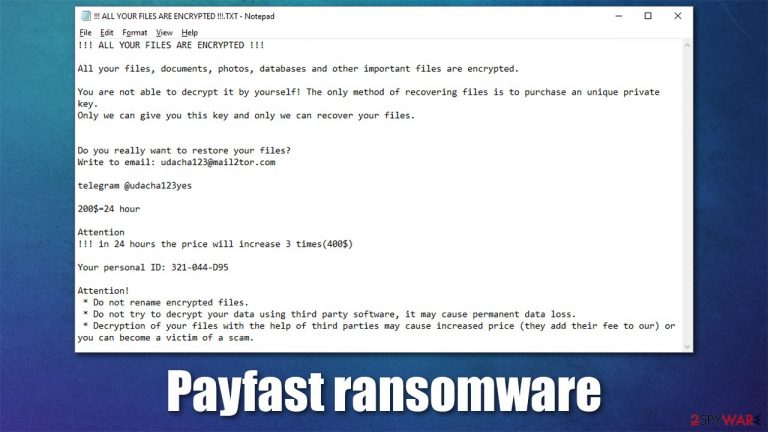
During the encryption process, each file is appended with a specific file extension – .payfast[ID]. While being a later stage of the infection, this symptom is the main one that makes victims realized that something has happened to their machines. For example, a file called picture.jpg would be changed into something like picture.jpg.payfast500.XXX-XXX-XXX (the X's are usually replaced with alphanumeric characters – they change from victim to victim). Also, .payfast290.XXX-XXX-XXX extensions were recently spotted as well. This tendency will likely continue in the future.
Soon after the data locking process, it delivers a ransom note titled !!! ALL YOUR FILES ARE ENCRYPTED !!!.TXT. Within the note, cybercriminals explain that users have to pay 0.013 BTC (although this sum is to double within a day) to retrieve a decryption tool that allegedly would restore all the files. Crooks also offer to send a file via payfast290@mail2tor.com or payfast500@mail2tor.com for test decryption – it should hold no important information.
However, security experts do not recommend contacting criminals as they are not obligated to send the decryptor for you. In this article, we will provide you with instructions on dealing with the dangerous ransomware infection for the best outcome for you.
| Name | Payfast ransomware |
|---|---|
| Type | Ransomware, data locking malware, cryptovirus |
| Malware family | Zeppelin |
| Encryption method | AES + RSA |
| File extension | .payfast[ID] |
| Ransom note | !!! ALL YOUR FILES ARE ENCRYPTED !!!.TXT |
| Ransom demand | 0.013 BTC |
| File Recovery | If no backups are available, recovering data is almost impossible. We recommend you try alternative methods which we list below |
| Malware removal | Perform a full system scan with powerful security software |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with the FortectIntego repair tool |
Zeppelin ransomware is not new in the cybersecurity world
While it can be easily said that Djvu is the most prominent ransomware family which targets home users, there are plenty of other strains that also want to benefit from the illegal activity of money extortion. First seen in November 2019, this malware has seen steady growth over the years, and new variants keep emerging regularly. The lineage comes from other ransomware strains, including VegaLocker and Buran.
The virus mainly spreads via contaminated email attachments or links – malspam[1] remains the most popular malware delivery technique to this day. In order to protect yourself from malware infections, you should always be careful when opening new emails, especially if they include an MS Office file. Never allow macros from these documents to be run on your PC; otherwise, the infection of the system might start immediately. As evident, running a powerful security application at all times should always be something you do.
Variants of this ransomware family are known to target high-profile organizations such as hospitals, although small businesses and regular users can also be infected due to the nature of the attack vector. Cybercriminals also choose targets by exploiting vulnerabilities[2] in corporate network software such as ConnectWise Control.
What to do after you get infected with Payfast ransomware?
First of all, you should not panic. While ransomware is indeed the most devastating infection to home users and corporations, the best thing to do now is to focus on Payfast removal and file recovery. However, it is important to do this correctly, as bad actions can result in personal files being permanently corrupted.
As malware can affect Windows in numerous ways, it might prevent you from removing it. Therefore, you should access Safe Mode with Networking in order to temporarily disable its functions:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.

Once in Safe Mode, you should remove the Payfast virus with the help of anti-malware software such as SpyHunter 5Combo Cleaner or Malwarebytes. Security software should be able to find all the malicious files and entries and remove them automatically for you. Doing this manually should not even be considered. Once malware is deleted, you can proceed with the alternative data recovery methods we provide below.
Next step: what to do with the files
File encryption is the feature of ransomware that makes it so terrible. Many users believe that they will restore their data as soon as they scan their systems with anti-virus software. However, it is not designed for such a purpose and will not restore your files.
The best thing to do would be to recover your files via backups. Your situation is quite a bit more complicated if you have no such backups ready. However, not everything is lost, and you should definitely not rush and pay criminals. They might never send you the decryption tool, or it might simply not work. You will end up losing your money along with your data.
Instead, you should try using recovery software. Before you proceed, however, you should copy the encrypted files onto a separate medium, such as a USB flash drive or SSD, and then disconnect them from your computer. Encrypted data does not hold any malicious code, so it is safe to transfer to other devices.
Once that is done, proceed with using recovery software:
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Security researchers are constantly working on battling malicious actors and helping victims by creating free decryptors. Unfortunately, such a tool is not yet developed for this malware family. There are several places where you could look for decryptors in the future:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors
Remediate your Windows after malware elimination
In order for Payfast ransomware to be successful, it needs to beat all the obstacles that stand in front of it. First of all, the malware checks the default language of the system and exits without infecting anything when it is set to the following languages:
- Russia
- Belarus
- Ukraine
- Kazakhstan
This tactic is not new and is commonly used by eastern criminals to avoid attention from local authorities. Only if the victim does not come from the aforementioned countries, the infection is immediately initiated.
This then prompts malware to perform multiple malicious tasks, including deleting Shadow Volume Copies to prevent easy data recovery, altering Windows registry[3] for automatic startup, settings itself to be run with elevated permissions, disabling security software of the most popular anti-malware tools, and much more.
Changes to the system can seriously damage it, resulting in crashes, errors, and other malfunctions after malware elimination. Therefore, in order to fix these problems, we recommend you fix your system using automatic repair software:
- Download FortectIntego
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing this tool, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
Below you will also find several tips that should help you improve your online security and make data backups to avoid its loss in the future.
Getting rid of Payfast virus. Follow these steps
Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
Report the incident to your local authorities
Ransomware is a huge business that is highly illegal, and authorities are very involved in catching malware operators. To have increased chances of identifying the culprits, the agencies need information. Therefore, by reporting the crime, you could help with stopping the cybercriminal activities and catching the threat actors. Make sure you include all the possible details, including how did you notice the attack, when it happened, etc. Additionally, providing documents such as ransom notes, examples of encrypted files, or malware executables would also be beneficial.
Law enforcement agencies typically deal with online fraud and cybercrime, although it depends on where you live. Here is the list of local authority groups that handle incidents like ransomware attacks, sorted by country:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

If your country is not listed above, you should contact the local police department or communications center.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Payfast and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Malspam. Malwarebytes Labs. Glossary.
- ^ Thomas Holt. What Are Software Vulnerabilities, and Why Are There So Many of Them?. Scientific American. Popular science magazine.
- ^ Windows registry. Wikipedia. The free encyclopedia.
