R3f5s ransomware (Virus Removal Guide) - Free Instructions
R3f5s virus Removal Guide
What is R3f5s ransomware?
R3f5s ransomware – Dharma family member that will not let go of your files until you pay
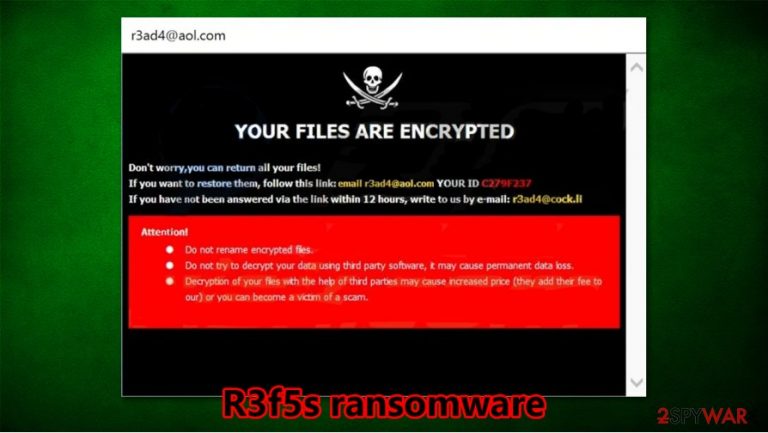
R3f5s ransomware is a cryptovirus that locks all files on the targeted computer until a ransom is paid to the cybercriminals. R3f5s virus belongs to the infamous Dharma ransomware family, which has been spewing out new versions of itself since 2016. As soon as the payload file of R3f5s file-locking parasite lands in a computer system, the encryption of victims' personal data begins. Consequently, just like with its previous versions (RDX, Kut or 259) all files are renamed and appended with a complex three-part extension (assigned victim ID, criminals contact email in brackets, and .r3f5s appendix).
Following successful encryption, two ransom notes show up – one as a pop-up window, the other one as a text file (FILES ENCRYPTED.txt). The latter one is very short and consists only of two emails provided (r3ad4@aol.com and r3ad4@cock.li) to establish contact with the developers of the .r3f5s virus in order to decrypt locked data. The pop-up ransom note is a bit more comprehensive and states that victims shouldn't try to rename or unlock their files with third-party tools, as this may cause permanent data loss. The cybercriminals also provide a unique ID that should be sent to them upon contact. The same two emails are provided. Further details, like ransom amount, preferred payment method, or timeline, are not specified. Both ransom notes are published at the end of this paragraph.
| name | R3f5s ransomware, .r3f5s virus |
|---|---|
| type | Ransomware, Cryptovirus |
| Family | Dharma ransomware family |
| ransom note | FILES ENCRYPTED.txt file and a pop-up window appear after encryption is completed |
| appended file extension | A difficult three-part extension is appended to all non-system files. |
| issues | All personal data is renamed and inaccessible |
| malware removal | Trustworthy anti-malware software should be used to remove R3f5s ransomware |
| system checkup | Once R3f5s ransomware removal is completed, a system tune-up should be done with the FortectIntego tool to eradicate any changes that the virus has done to computer system-related files and device settings |
As always, we strongly advise against any contact with the cybercriminals. Study shows[1] that victims who paid the threat actors ended up spending twice as much, as those who focused on system restoration. In addition to that, when the developers of R3f5s virus, and malware alike, are paid, this encourages them to attack more people, this fuels their mischievous campaigns.
We suggest using SpyHunter 5Combo Cleaner or Malwarebytes to automatically remove R3f5s ransomware from infected devices. The longer the malware stays in a computer, the more harm it could do. In the future, be sure to have a trusty anti-malware software like mentioned above to watch your back.
After you are done with R3f5s ransomware removal, we strongly advise doing a complete system checkup with the FortectIntego tool because Dharma family members do extensive damage to computer system files, start-up, and other settings. If neglected, these altercations might lead to crashes, malware renewal, constant error messages, etc.
In the pop-up ransom window, creators of .r3f5s ransomware state:
YOUR FILES ARE ENCRYPTED
Don't worry,you can return all your files!
If you want to restore them, follow this link:email r3ad4@aol.com YOUR ID 1E857D00
If you have not been answered via the link within 12 hours, write to us by e-mail:r3ad4@cock.li
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
If victims somehow missed the pop-up window, cybercriminals leave their contact info in a text file on all contaminated folders:
all your data has been locked us
You want to return?
write email r3ad4@aol.com or r3ad4@cock.li
Methods of malware distribution
As strange as it may sound, hackers are working their butts off to outsmart everyday computer users. There are various types of malware[2], and then there are numerous variants of those types. It would take us forever to expand on each category and their variations.
Entirely another thing is with the distribution of their creations. These opportunities are limited, so cybercriminals try to camouflage their malware as unsuspiciously as possible. For example, we all have received spam emails. Most of them are harmless because they go where they supposed to – the spam inbox folder, where they are constantly deleted; but if you'd receive a letter appearing as a legitimate letter from your bank saying that there have been some errors on your account and that an updated invoice is in the attached file, or that you must push a link to go to your account now to do some urgent adjustments. You would be very intrigued to do that, wouldn't you? STOP!
This is just one example of how cybercriminals try and fool everyday people. Stay aware, get to know their body of work, acquire a trustworthy anti-virus software to watch over you, and stay safe.
Remove R3f5s ransomware and tune-up your computer afterward
Once a computer is infected with any kind of malware, a chain reaction starts, and victims could end up losing not only their data but their identities, savings, etc. As soon as any malicious program is detected, it must be removed swiftly. To remove R3f5s virus experts[3] advise using time-proven anti-malware software such as SpyHunter 5Combo Cleaner and Malwarebytes.
Unfortunately, R3f5s ransomware removal won't magically decrypt your files. But you can restore them from backups as soon as you run as full system scan with the FortectIntego tool to make sure that there are no changes made to system start-up items and other settings, along with system files. If the .r3f5s ransomware got its hands on some of them, the app will automatically find them and reverse them.
Getting rid of R3f5s virus. Follow these steps
Manual removal using Safe Mode
Access Safe Mode with Networking if you can not eliminate the virus normally:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove R3f5s using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of R3f5s. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove R3f5s from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by R3f5s, you can use several methods to restore them:
Data Recovery Pro could be a solution
This software might be able to retrieve working copies of files from your hard drive.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by R3f5s ransomware;
- Restore them.
Choose Windows Previous Versions for data restore
You might be able to restore files one-by-one with Windows Previous Versions feature.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer might be useful
This app could automate data recovery process (as long as Shadow Copies were not deleted by ransomware).
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No dectryption tool is currently available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from R3f5s and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Study Suggests Paying a Ransom Doubles the Cost of Recovery from a Ransomware Attack. HippaJournal. Jews and articles about HIPPA.
- ^ All about malware. Malwarebitrs. Cybersecurity for home and business.
- ^ Uirusu. Uirusu. Spyware news and security.







