Story-board.co scam (fake) - Chrome, Firefox, IE, Edge
Story-board.co scam Removal Guide
What is Story-board.co scam?
Story-board.co lures people in by making them think that they will win a $100 gift card
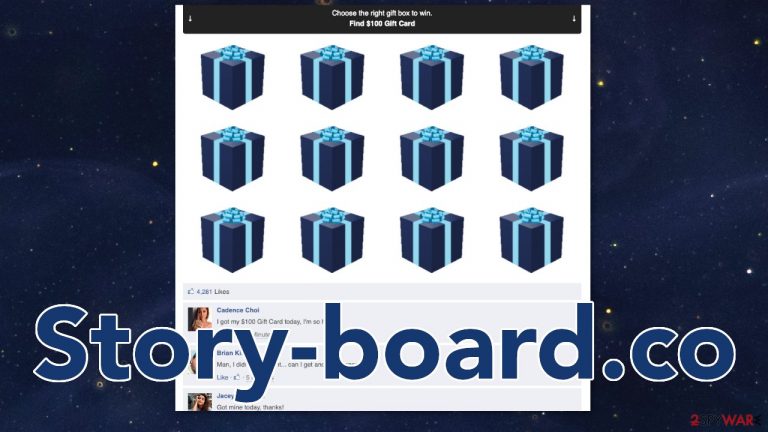
If you have come across the story-board.co website, you should definitely not interact with it. It is a scam website that attempts to gather users' personal information by presenting them with a fake giveaway. Phishing[1] attempts are still very prominent on the Internet, and they target less tech-savvy people that are gullible.
To convince users, the website presents them with gift boxes that they have to choose from. They get 3 attempts, and if they are supposedly lucky, they can win a $100 gift card. The reality is, no matter how many times you play the game, the third attempt always is “the lucky one.”
Below the gift boxes, fake Facebook comments and likes are shown to make the site look more legitimate. This is a common technique used by crooks that develop PUPs[2] (potentially unwanted programs) as well as scam sites. You can easily check if the comments are real by trying to click on the profiles of the people that left them or leave a like. You will not be successful. That means that the comments are not imported straight from Facebook, and it is just a picture embedded in the page.
| NAME | Story-board.co |
| TYPE | Scam, phishing, survey scam; potentially unwanted program |
| SYMPTOMS | Redirects to scam, fake giveaway, software update sites |
| DISTRIBUTION | Shady websites, deceptive ads, software bundling |
| DANGERS | Users may suffer from financial losses by providing their personal information to fake pages and installing PUPs or even malware |
| ELIMINATION | We recommend using professional security tools to scan your system for adware |
| FURTHER STEPS | Use FortectIntego to fix any remaining damage and optimize the machine to improve performance speed |
The purpose of story-board.co is to lure out peoples' personal information. When users see “Congratulations!” and think that they won a gift card, they are asked to fill out their shipping and contact information. It is unknown how this information could be used and who are the individuals behind the site.
What is more, the site does not have a privacy policy or terms of use sections, which is worrying. It is impossible to know what information the website collects while you are using it. Generally, pages use cookies[3] to track users' browsing-related activities and collect data like the IP address, links users click on, and what they purchase.
At face value, there is nothing wrong with that. But if a site is unregulated, does not have end-to-end encryption,[4] SSL certificates – cookies can be stolen by hackers, not to mention that the site's owner could have malicious intentions and make people who entered their information suffer from monetary losses or even identity theft.
This is why it is recommended to clear cookies and cache frequently. You can do that manually in the browser settings, or even better – with a tool like FortectIntego. This powerful software can delete all the data collected by sites automatically. It can also fix various system problems, like corrupted files, registry issues, BSoDs, and other errors, so it is very useful in case of a virus infection.
Ways people stumble upon scam sites
There are many sites that use fake giveaways to attract people. Some of the similar pages we previously wrote about are Cellsignclock.top, You've made the 9.68-billionth search, and Annual Visitor Survey. Although it is unknown where exactly users encountered story-board.co ads, there are distribution channels that generally promote shady sites and products.
It is rare for people to find websites like this in their search results. Usually, other sources are used to promote them. One of the best examples is illegal streaming platforms. They are full of deceptive ads and sneaky redirects. Fake “Download” and “Play” buttons are incredibly annoying because they look real but instead take users to random pages that try to trick them into allowing push notifications, downloading PUAs, or in this case – providing personal information.
The appearance of such pages can also be caused by adware.[5] This type of application operates in the background of the machine and tries to hide its existence. It generates revenue for the developers by causing pop-ups, redirects to promoted pages, and injecting ads in the search results. If that is the case, you might have an extension added to your browser that has permissions to perform such tasks.
Search for suspicious browser plugins
You can remove extensions by going to your browser settings. Step-by-step instructions for Chrome, MS Edge, Firefox, Safari, and Internet Explorer are available below.
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select the unwanted plugin and click Remove.

Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Internet Explorer:
- Open Internet Explorer, click on the Gear icon (IE menu) on the top-right corner of the browser
- Pick Manage Add-ons.
- You will see a Manage Add-ons window. Here, look for suspicious plugins. Click on these entries and select Disable.
In case you have adware
If you do not visit questionable sites but still get thrown into scam pages, we recommend using professional security tools like SpyHunter 5Combo Cleaner or Malwarebytes to get rid of any PUAs that could be hiding in your system. Security software can scan your machine and detect suspicious processes working in the background of your PC. What is more, it can prevent the installations of such programs in the future by warning you about it.
We also suggest you implement some precautionary measures in your routine because PUPs are most often spread on freeware distribution sites that use a method known as software bundling to generate revenue. The first thing you should do is to choose the “Custom” or “Advanced” installation method so that no steps would be hidden from you. The most important part is to look at the file list and untick the boxes next to items you do not need.
If you want to look at the program list yourself, you can follow the guide for Windows and Mac machines below:
Windows 10/8:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till the uninstallation process is complete and click OK.

Windows 7/XP:
- Click on Windows Start > Control Panel located on the right pane (if you are a Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Mac:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

How to prevent from getting adware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ What Is Phishing?. Phishing. Fraud Prevention.
- ^ Potentially unwanted program. Wikipedia. The free encyclopedia.
- ^ Chris Maus. What Are Cookies and Are They Dangerous?. Qkey. Secure Online Payment Provider.
- ^ What end-to-end encryption is, and why you need it. Kaspersky. Daily Tech News.
- ^ All about adware. Malwarebytes. Cybersecurity Basics.
