Twitter virus (Removal Guide) - updated Aug 2019
Twitter virus Removal Guide
What is Twitter virus?
Twitter virus – a term used to describe various types of malware spreading on the social platform via links or “Only for you” DMs
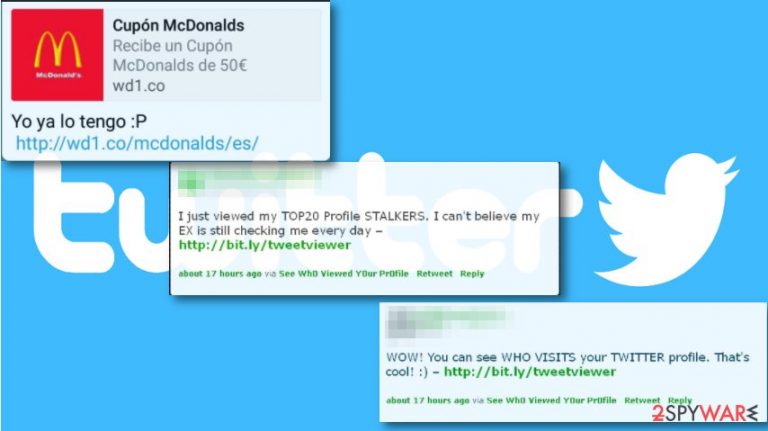
Twitter virus is a name of the threat created to describe the particular malware that affects social media users. This name is used for spam activities on a popular social network, malicious links delivering malware or commercial content campaigns showing questionable material via private messages. Usually, such malware delivers spam posts or sends private DMs that contain a shortened link redirecting to shady pages. Unfortunately, once clicked, it might show or install a highly suspicious application that might be created for spreading malware or phishing attempts.
However, according to the latest trends, Twitter malware can install on the target system and then use Twitter posts from its owner for communication. This is a totally new feature that could lead the IoT community to serious outcomes. The more recent campaigns distributing on the social platform spread via messages with “Only for you”. This type of Twitter virus contains users name, links to suspicious sites. Some users stated that the redirect took them to a particular account and that the DM comes from the known person.[1]
| Name | Twitter virus |
| Category | Malware |
| Infiltration | Malicious posts on social networks; infected emails or links/ads on the Internet |
| Main signs | Intriguing headlines which trying to convince victims into clicking the link or downloading the malicious file onto the system |
| Examples of potentially dangerous headlines |
|
| Main dangers | Getting infected with malware, losing personal information, damaging files, etc. |
| Prevention | Avoid pesky links on Twitter or that you receive via the direct message, always keep your anti-virus up-to-date |
| Elimination | Use FortectIntego to spot potential danger on your computer |
Twitter malware has been known since 2009. It acts similarly to any of the Facebook virus, iPhone virus, Android virus, and others. If it manages to affect one’s account, it starts sending out spammy messages to its contacts and may also initiate other issues for its victim, such as disable his/her account, etc.
This virus is based on malicious posts that appear on Twitter's timeline. To draw people’s attention, this virus uses infected or fake accounts to post misleading tweets saying something like:
- OMG, I can’t believe that;
- OMG look what they’re saying about you;
- Is this you in this photo?;
- Only for you;
- Check this!!!
Of course, these tweets are filled with invented content, which is supposed to draw people's attention and convince them to click on it. Misleading tweets is not the only way how this virus spreads around. Twitter virus may try to affect your account via direct messages that can be sent to you by unknown people. They can also be filled with links and similar content. In fact, these malicious links that are usually included to these fake messages are the main helpers for this virus to spread around.
Typically, these links redirect to phishing and malware-laden websites that ask the victim to install a certain plug-in, update or a program that is required in order to see the intriguing content. Such downloads are infectious and should be avoided! However, if you clicked on such link or installed suspicious content, you should carry out Twitter virus removal immediately.
To remove Twitter virus, you need to disable application access via Settings and uninstall questionable programs or browser add-ons you were tricked to install. However, you can speed up this procedure by scanning the system with FortectIntego and changing your password.
Malware detected as TROJAN.MSIL.BERBOMTHUM.AA is using Twitter to reach its owners
Twitter virus has numerous forms and features. While TROJAN.MSIL.BERBOMTHUM.AA is not using this network to get into the target computer, once inside it, it starts reaching out to its owners by using the special technique that uses the payload hidden in the Twitter images.[2]
These Twitter memes are filled with special commands, e.g. “print,” “processos” or “clip,” which mean exact actions, such as making the screenshot of the screen, copying running processes, retrieving the username and so on. This is a great danger as the victim can be lead to identity theft and similar loss.
The operation principle, which is known as steganography, is not a common case these days. Unfortunately, there is a great possibility that such viruses will become more common in 2019. While the Twitter virus, which was used for communication with the virus owners, is down, the appearance of similar viruses can be expected in the nearest future.
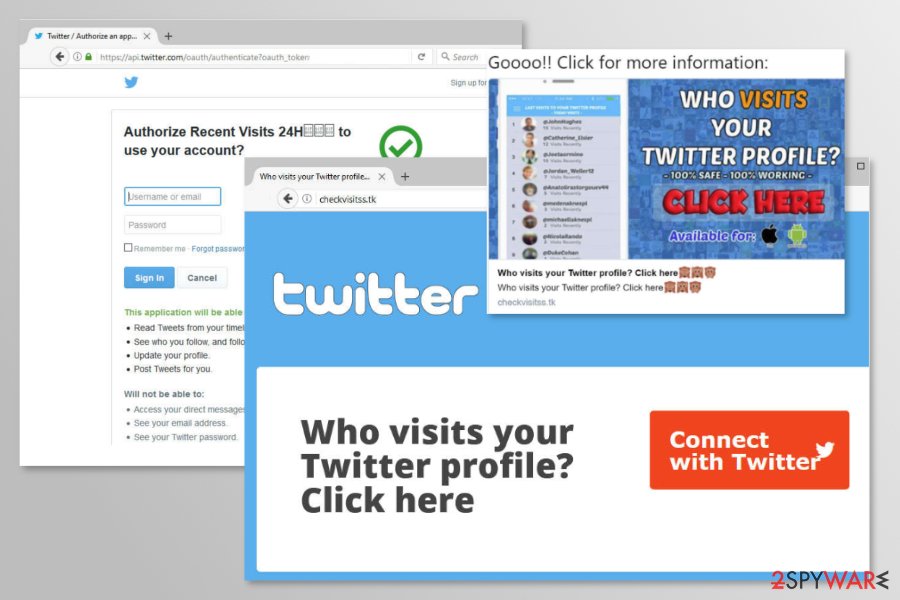
Twitter scam “Who visits your Twitter profile” is yet another way to get infected
In January 2018, a new variant of Twitter spam was detected.[3] Numerous people were tweeting with a hashtag #FBPE which included the link to a website that claims to reveal the sweet information about who has viewed your profile.
There a couple of different spam messages, for instance:
Goooo!! Click for more information:
Who visits your Twitter profile
100% safe, 100% working
Click here, available for iOS and Android
or
Sign in and download this fantastic app – only available today
However, all of them contains the link to checkvisitss[.]tk website that offers to connect with Twitter account and learn who visited your profile. Once this button is clicked, users are redirected to authorization website which asks for regular Twitter app permissions:
- Read tweets from your timeline
- See who you follow and follow new people
- Update your profile
- Find Tweets for you
Indeed, after the installation, the Twitter virus continues posting lots of annoying content on behalf of you. Though, the redirected website and app itself don’t perform any malicious activities. However, it might be just a matter of time. You can never be sure if scammers wouldn’t think of the way to spread malware.
Thus, if your account was posting spam, you should navigate to Applications tab under Settings and Privacy, and disconnect all suspicious apps to remove Twitter scam entirely.
Other examples of Twitter virus
Money-based schemes
Scammers used the names of popular companies, such as Google, in order to convince users that they can make money while working from home. However, they were asked to pay a small sign-up fee. In this case, crooks get the victim’s credit card information and can charge them every single month.
Pay-For-Followers scams
These types of posts included a possibility to increase user’s followers. Scammers claimed that for a small amount of money (e.g. $5) they can get more than 2000 followers within a day.
Twitter worms
In 2009 “Mikeyy” or “StalkDaily” worm[4] was noticed spreading on the social network asking to access a StalkDaily.com website. As soon as users clicked on a link, her or his account was infected and continues spreading the malware further.
Other worms were spotted in 2014. This time malware was more sophisticated and managed to compromise even BBC News Twitter account.[5]
Fake customer support accounts
In 2014 and 2016, numerous fake customer support accounts were detected.[6] These phishing scams were used for stealing user’s logins and passwords. Typically, users were asked to access a camouflaged website and enter their details.
Users are advised to be careful with such messages. Official accounts always are verified and have a blue tick mark.
Direct message scams
The DM campaign of Only for you Twitter virus, involving the private DMs on the platform delivers questionable links to your account or any other page that shows shady content. Fraudulent messages seem to be sent from the person you know to fake the legitimacy. However, you shouldn't rely on such content and try to stay away from opening, reading and replying to such DMs.
When you receive ONLY FOR YOU message in the private message section or even directly on the phone, you should react and delete such messages ASAP. Those links can be faked and look like a link to some other social platform account or twitter support.
Nevertheless, shortened links even redirect you to malicious content filled pages with the possible download of more severe malware. Your account can even get hacked if you go to the provided page or download anything from the internet. You should remove Only for you Twitter virus or any other shady DM and reset passwords to this social platform, and other accounts.
Virus prevention requires being extra careful when using social media
Such social network malware mostly spreads via direct messages and bogus posts on the timeline of the particular platform. In order to protect yourself, you should ignore all spammy-looking messages that typically announce about shocking news or promote various products, such as drugs, contests for getting the ability to win smartphones, sales, and similar things.
You must never click on the link, which can also be found in these tweets or posts on other media outlets. Typically, such posts contain shortened URLs, and this technique is used to obfuscate suspicious-looking malicious links.
Also, make sure you ignore tweets that may show up on your feet out of nowhere. If you would happen to get infected with a Twitter virus, you should keep in your mind that you can be involved in its distribution. You can start sending out the same or similar spammy messages to all of your followers and friends automatically.
To get rid of the Twitter virus, you should check your profile and the computer system for unwanted alterations
If you clicked on a suspicious link or your followers reported that you are posting spam, you should consider a Twitter virus removal. We recommend terminating the virus with the help of anti-malware software, for instance, FortectIntego or SpyHunter 5Combo Cleaner, Malwarebytes.
The virus can add additional programs to the system, inject suspicious extensions and tracking cookies into web browsers you use, and add registry keys that are hard to identify and delete manually. Thus, you may not be able to remove Twitter virus without security software, specialists from viruset.no[7] say.
Additionally, if you have suffered from “Who visits your Twitter profile” scam, you should follow these steps too:
- Log in to Twitter.
- Access Settings and Privacy.
- Open Applications tab.
- Remove suspicious applications by clicking Revoke access button next to each of them.
If you cannot access your account after the attack, you should follow the guidelines provided by Twitter Help Center.
Getting rid of Twitter virus. Follow these steps
Manual removal using Safe Mode
If you cannot start the anti-malware software, reboot your PC into a Safe Mode with Networking first, and then launch your anti-malware program. You should also carry out the following instructions to protect your Twitter account:
- Change your Twitter password ASAP (you should change it on other accounts as well, if you use the same password there). For that, you should click your username, select “Settings” and then click the “Password” tab. Click “Change” to save these changes.
- Log back into your Twitter account and delete any spammy-looking messages.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Twitter and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting malware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ The messages say ' ONLY FOR YOU ' . Twitter. Social media platform.
- ^ Aliakbar Zahravi. Cybercriminals Use Malicious Memes that Communicate with Malware. Trend Micro. Security Intelligence Blog.
- ^ Christopher Boyd. “Who visits your Twitter profile” spam app brings week of chaos. Malwarebytes Labs. Security blog.
- ^ Ian Paul. Twitter Worm: A Closer Look at What Happened. PCWorld. News, tips and reviews from the experts on PCs, Windows and more.
- ^ Dan Goodin. Powerful worm on Twitter unleashes torrent of out-of-control tweets. ArsTechnica. IT news, reviews, and analysis.
- ^ Harry Readhead. Watch out for this latest scam on Twitter. Metro. News website.
- ^ Viruset. Viruset. Norwegian security news.
