Zery ransomware (virus) - Free Instructions
Zery virus Removal Guide
What is Zery ransomware?
Zery ransomware – a malicious Windows program that might prevent you from accessing your personal files indefinitely
Zery ransomware is a variant of Xorist – a broad ransomware family that has its roots as early as 2012. Today, malware creators have numerous variants that infect thousands of users with versions such as Crysphere, Feg, and Trg.
Once malware manages to break in using illegal methods such as malicious spam email attachments or software cracks, it immediately begins to change the operating system in a way that would allow it to perform its main task – to encrypt all files located on local or networked drives with a TEA[1] encryption algorithm, preventing its access completely.
All altered files would have .ZeRy extension appended to them – this is possibly one of the most distinctive characteristics of a ransomware infection that users notice. In addition, the virus would immediately show a pop-up window titled “Error” along with the HOW TO DECRYPT FILES.txt file, both of which include identical messages.
They say that users have to transfer 0.05 bitcoins to a predetermined crypto-wallet for the decryptor that is meant to restore locked files and then email them to zery@tuta.io. Communicating with the attackers is not recommended, as they might never deliver what they have promised.
| Name | Zery virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .ZeRy extension is appended to every personal file on the system |
| Ransom note | HOW TO DECRYPT FILES.txt |
| Malware family | Xorist |
| File Recovery | The only method to recover files is through data backups. If such is not accessible, or if it has also been encrypted, your options for recovery are extremely limited, although we recommend trying them |
| Malware removal | Disconnect the computer from the network and internet and then perform a full system scan with SpyHunter 5Combo Cleaner security software |
| System fix | After malware infects a system, it can corrupt several important files, which often leads to crashes, errors, and other issues. FortectIntego PC repair is an effective solution to automatically replacing any corrupted system files |
A pop-up window is meant to drive users' attention to the attackers' message
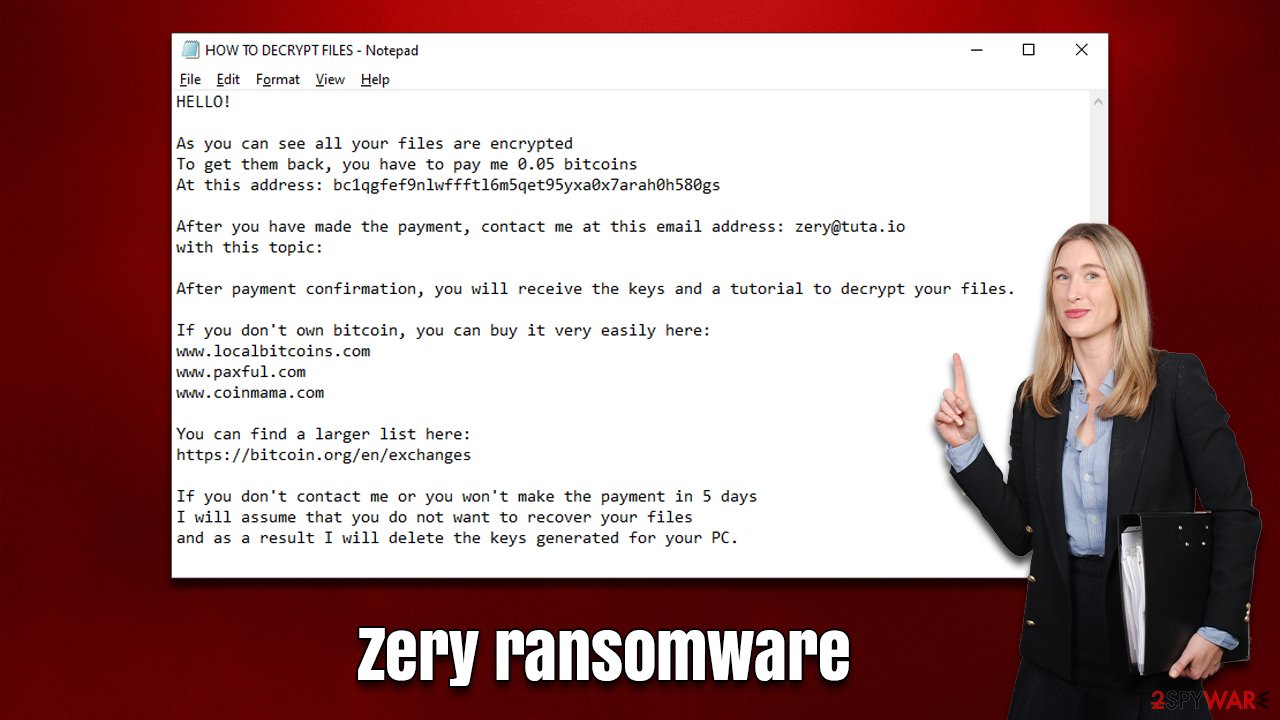
There are two ransom notes that are delivered right upon the file encryption process is finished, both of which include identical text, which reads:
HELLO!
As you can see all your files are encrypted
To get them back, you have to pay me 0.05 bitcoins
At this address: bc1qgfef9nlwffftl6m5qet95yxa0x7arah0h580gsAfter you have made the payment, contact me at this email address: zery@tuta.io
with this topic:After payment confirmation, you will receive the keys and a tutorial to decrypt your files.
If you don't own bitcoin, you can buy it very easily here:
www.localbitcoins.com
www.paxful.com
www.coinmama.comYou can find a larger list here:
https://bitcoin.org/en/exchangesIf you don't contact me or you won't make the payment in 5 days
I will assume that you do not want to recover your files
and as a result I will delete the keys generated for your PC.
A ransom note is a particularly important component of any ransomware infection, as it provides crucial information that could lead to victims paying the ransom (which is the ultimate goal of the attackers). It is likely because of this, cybercriminals programmed the virus to deliver a pop-up window that would immediately grab users' attention.
In the note, crooks claim that users have five days to pay the ransom, or the unique key will be deleted forever. While this might be true, it can also be just one of many scaremongering tactics to make people pay the ransom.
Remove malware from the system
Understandably, when users learn that their files have been encrypted by ransomware and are no longer accessible, they typically become highly worried. The infection has already taken place, so this reaction is not going to help. In fact, panicking victims may make mistakes that result in even more data loss. It's critical to carry out the appropriate steps in the right order to prevent further damage.
To set up a remote connection with an infected Windows device, cybercriminals use what is called a Command & Control server. The communication occurs over the internet, so it's key that the machine is disconnected from any networked connections. If you need to do this quickly and easily, follow these steps:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet

- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
Once your system is disconnected from all the networks, it's time to clear the Zery virus out by using some good security software like SpyHunter 5Combo Cleaner or Malwarebytes. Security software will scan and find all of the malicious files so you can be sure that the infection will not come back and encrypt your system again. Likewise, some ransomware is distributed in bundles with other malware, such as banking Trojans,[2] so a scan with anti-malware is crucial to ensure system security.
Note that anti-malware software operation might be disturbed by the ransomware due to its persistence[3] mechanisms. This can usually be bypassed by accessing Safe Mode and performing malware removal from there – follow these steps:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.
- Go to Advanced options.
- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
Ransomware is one of the most destructive viruses, as it can severely damage a system. Not only does it spread through networks and come with other infections, but it might also insert illegitimate code or damage existing Windows files, resulting in crashes or other stability issues. Therefore, we recommend fixing any such inconsistencies using a sophisticated PC repair tool as follows:
- Download FortectIntego
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

Data recovery without paying
The Zery virus' key objective is to locate and encrypt all non-system files on any Windows machine it can get access to, as well as any other connected devices on the same network. In more severe cases, hackers will also exploit weaknesses in software commonly used for local management to target backup systems.
When it comes to regular computer users, they often fail to create appropriate data backups in the first place, which can be devastating when being infected with ransomware. Paying a ransom to cybercriminals is also a huge risk, as there is never a guarantee that they will provide a working decrytpion tool.
While this news might initially sound disheartening, there is still some hope – data recovery software might be able to assist you depending on the extenuating circumstances (such as the encryption algorithm used or whether ransomware was able to complete its tasks properly).
It is crucial that you back up any encrypted files of value to you before continuing. If not, recovery attempts could permanently damage locked data, and even a working decryptor would be useless. So take a USB flash drive or similar storage device and ensure your important files are safe.
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Tiny Encryption Algorithm. Wikipedia. The free encyclopedia.
- ^ Trojans. Imperva. Application and data security.
- ^ Common Techniques by Which Malware Makes Itself Persistent. Lifars. Security Scorecard Company.
