Bttu ransomware (virus) - Free Instructions
Bttu virus Removal Guide
What is Bttu ransomware?
Bttu ransomware locks all pictures, videos, documents, and other files on the system for money extortion purposes
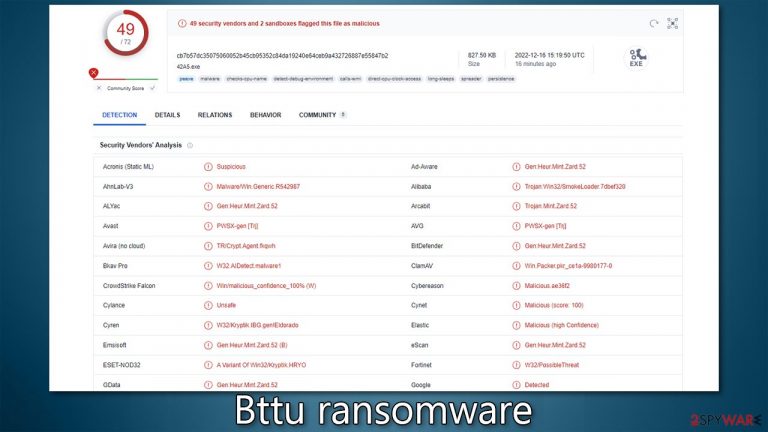
Bttu ransomware is a type of malicious software that is designed to encrypt files on your computer and demand a ransom in exchange for their release. It is one of the most destructive forms of cyberattacks, as it can render entire batches of personal files useless if victims are unable to meet the attacker's demands. Suchlike files are marked with .bttu extension and are also stripped from their original icons, which are replaced by blanks instead.
The decryption key that can unlock files is only known to the attackers behind the Bttu virus, and, of course, they are not willing to provide it for free. According to the ransom note _readme.txt, users are meant to contact crooks by writing to support@fishmail.top or datarestorehelp@airmail.cc emails and including their personal ID.
Victims can only retrieve the unique decryption tool if they are willing to pay $980 (or $490 if paid early) in bitcoin – the funds must be transferred to the cybercriminals' wallet. We recommend avoiding any contact with the perpetrators and instead using alternative methods for data recovery we discuss below.
| Name | Bttu virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .bttu appended to all personal files |
| Family | Djvu |
| Ransom note | _readme.txt |
| Ransom size | $480/$980 |
| Contact | support@fishmail.top or datarestorehelp@airmail.cc |
| File Recovery | There is no guaranteed way to recover locked files without backups. Other options include paying cybercriminals (not recommended, might also lose the paid money), using Emisoft's decryptor (works for a limited number of victims), or using third-party recovery software |
| Malware removal | After disconnecting the computer from the network and the internet, do a complete system scan using the SpyHunter 5Combo Cleaner security program |
| System fix | As soon as it is installed, malware has the potential to severely harm some system files, causing instability problems, including crashes and errors. Any such damage can be automatically repaired by using FortectIntego PC repair |
Djvu is one of the most prominent malware families out there – and that's where Bttu ransomware stems from. Despite efforts to combat it, it remains a significant threat to individuals and organizations, with over a thousand variations identified. It is believed that hundreds of people are affected by it on a daily basis.
Since the release of malware back in 2017, we have seen close to a thousand versions released so far, with variants like Maos, Mppn, Kcvp, showing up weekly. Cybercriminals always use four random letters to name them – one of the more distinctive traits of the virus. Otherwise, version from version does not differ much, as its main goal remains the same – to lock all data and hold it hostage until victims pay the ransom.
The ransom note and how to proceed
A ransom note is among the most important components of any ransomware operation, as without it, users would not be able to find out cybercriminals' contact details, reducing their chances for a successful money transfer to zero. Therefore, it is not unusual for a ransom note to pop up right in front of users' faces as soon as all the files are locked with a secure RSA encryption algorithm.[1]
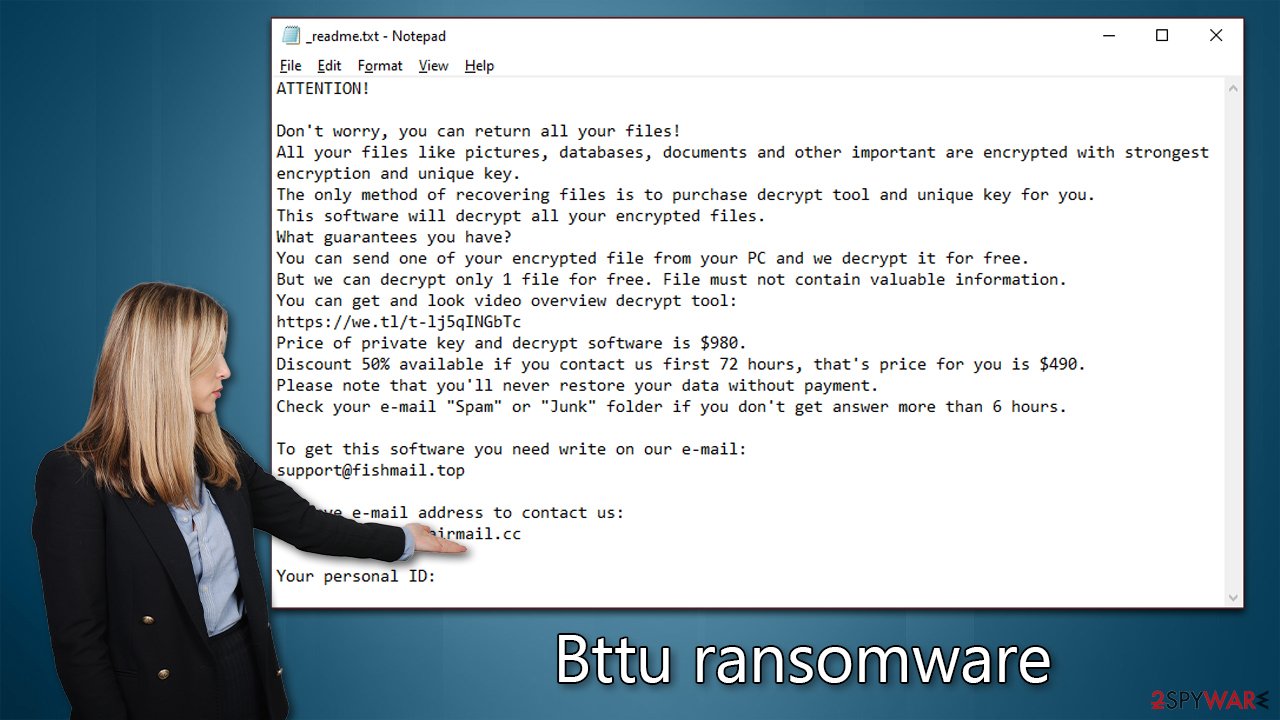
Bttu ransomware uses a simple text-based format to deliver the message to users, which reads:
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-67n37yZLXk
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
support@fishmail.topReserve e-mail address to contact us:
datarestorehelp@airmail.ccYour personal ID:
As is usual for this and many other viruses of this type, the offer to send out a file for test decryption to prove it's possible is there. However, trusting cybercriminals is rather risky, and there is a chance of losing paid money along with the encrypted data. Therefore, we recommend taking an alternative route and removing malware from the system, and then using alternative solutions for data recovery.
How to deal with a ransomware attack
If you've never been infected with ransomware before, it can be a very confusing and frustrating experience. It's important to take the right steps when dealing with ransomware, though, as your chances of restoring your data may depend on it. Your first task is to remove the malware, back up any encrypted files, and only then attempt recovery.
Remove your computer from the network and scan the PC with anti-malware
To start, you should take some time to remove any ransomware-affected machine's internet or network connection. This will sever the communication between the ransomware and the remote C&C server[2] controlled by criminals.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
By disconnecting your system from the internet, you can scan and clear it of infection using SpyHunter 5Combo Cleaner, Malwarebytes, or another reliable security software. Although ransomware typically self-destructs after job completion, there is always a chance it will linger. Ransomware commonly comes hand-in-hand with other computer infections (mostly data-stealing[3] Trojans), which raises the stakes in terms of privacy and computer security damage.
Repair your system files
There are thousands of files on any Windows operating system, some of which belong to the OS itself, third-party apps, or those that are personal files, such as pictures or videos. Ransomware targets the latter and mainly leaves system files intact, although this is not always the case.
Ransomware can sometimes have bugs, or its developer might intentionally include modules that would interact with the registry or other components. For example, Djvu variants such as Bttu are programmed to alter the host file on the system, preventing users from accessing certain security-related websites online. This can be everted by deleting the file, which Windows would recreate later. It can be found in the following location:
C:\Windows\System32\drivers\etc\
To repair potential damage to other sectors of the operating system, we recommend running a PC repair tool.
- Download FortectIntego
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
Recovery of personal (Bttu) files
The last step is to retrieve the locked files without paying cybercriminals. Many people don't understand how data encryption works or know anything about it. Some believe that they can restore their data as soon as they scan their computer with an anti-virus program, while others think that once their files are encrypted, they're gone for good – neither of these scenarios is accurate in this case.
When attempting to recover data affected by ransomware, you should first make backups of all your personal files. Otherwise, they might be permanently damaged, and even a working decryptor will no longer be useful. once done, we recommend trying Emsisoft's decryption tool first:
- Download the app from the official Emsisoft website.
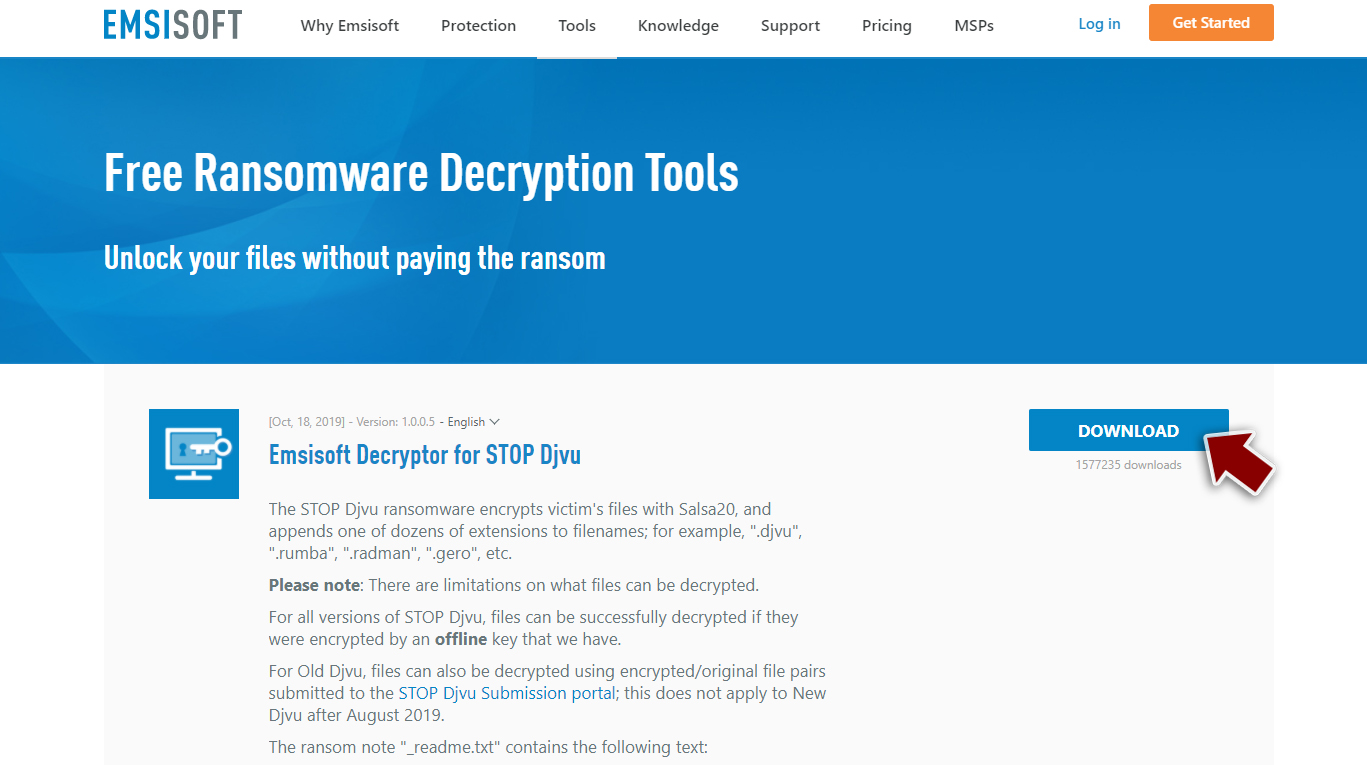
- After pressing Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe should show up – click it.

- If User Account Control (UAC) message shows up, press Yes.
- Agree to License Terms by pressing Yes.
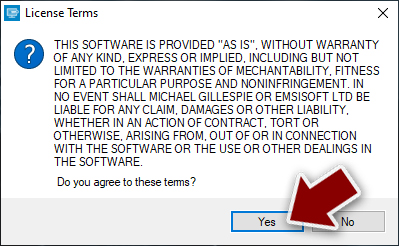
- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.

- Press Decrypt.

From here, there are three available outcomes:
- “Decrypted!” will be shown under files that were decrypted successfully – they are now usable again.
- “Error: Unable to decrypt file with ID:” means that the keys for this version of the virus have not yet been retrieved, so you should try later.
- “This ID appears to be an online ID, decryption is impossible” – you are unable to decrypt files with this tool.
If this method was unsuccessful, you can find more options below.
Getting rid of Bttu virus. Follow these steps
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Find a working decryptor for your files
File encryption is a process that is similar to applying a password to a particular file or folder. However, from a technical point of view, encryption is fundamentally different due to its complexity. By using encryption, threat actors use a unique set of alphanumeric characters as a password that can not easily be deciphered if the process is performed correctly.
There are several algorithms that can be used to lock data (whether for good or bad reasons); for example, AES uses the symmetric method of encryption, meaning that the key used to lock and unlock files is the same. Unfortunately, it is only accessible to the attackers who hold it on a remote server – they ask for a payment in exchange for it. This simple principle is what allows ransomware authors to prosper in this illegal business.
While many high-profile ransomware strains such as Djvu or Dharma use immaculate encryption methods, there are plenty of failures that can be observed within the code of some novice malware developers. For example, the keys could be stored locally, which would allow users to regain access to their files without paying. In some cases, ransomware does not even encrypt files due to bugs, although victims might believe the opposite due to the ransom note that shows up right after the infection and data encryption is completed.
Therefore, regardless of which crypto-malware affects your files, you should try to find the relevant decryptor if such exists. Security researchers are in a constant battle against cybercriminals. In some cases, they manage to create a working decryption tool that would allow victims to recover files for free.
Once you have identified which ransomware you are affected by, you should check the following links for a decryptor:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

If you can't find a decryptor that works for you, you should try the alternative methods we list below. Additionally, it is worth mentioning that it sometimes takes years for a working decryption tool to be developed, so there are always hopes for the future.
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Ron Franklin. AES vs. RSA Encryption: What Are the Differences?. Precisely. Data analysis.
- ^ Command and Control [C&C] Server. Trend Micro. Security blog.
- ^ Danny Palmer. This data-stealing Trojan is the first to also infect you with ransomware. ZDNet. News and Advice on the World's Latest Innovations.
