Copa ransomware (Virus Removal Guide) - updated Sep 2020
Copa virus Removal Guide
What is Copa ransomware?
Copa ransomware is money extortion-based malware that belongs to the most prominent family
Copa ransomware is a data-locking computer infection that first showed up in late September of 2020, which belongs to the broad family of Djvu ransomware. Mainly spreading via software cracks on pirated software installers, the malware locks all the personal files with a sophisticated encryption algorithm. During this process, pictures, documents, videos, databases, and all the other files on the local and networked drives are appended with .copa extension and can no longer be accessed.
Threat actors behind the infection then receive a decryption key that is needed to unlock all the files. As evident, they are not willing to give it away for free and are asking for a $980 (or $490 if the contact is made within 72 hours of the infection) ransom, which is meant to be paid in bitcoin. To ensure that victims can easily contact Copa file virus authors, they leave a ransom note _readme.txt and ask users to email them at restoremanager@mail.ch or restoremanager@airmail.cc.
Since the virus belongs to the STOP/Djvu ransomware strain, there is a free decryption tool available that could help victims whose files were encrypted with an offline ID. Additionally, there are a few alternative methods that could sometimes help to recover .copa files – they can be found at the bottom of this article.
| Name | Copa ransomware |
|---|---|
| Malware family | Djvu/STOP ransomware |
| Functionality | Encrypts personal files on the computer to demand money for the alleged recovery, deletes Shadow Copies, injects data-stealing modules, modifies Windows “hosts” file, installs other malware, etc. |
| Encryption method | RSA and AES algorithms |
| File extension | .copa extension is added at the end of every file |
| Ransom note | _readme.txt is dropped on several locations on the infected computer |
| File Recovery |
The only secure method to recover files safely is by copying them from backups. Other options include:
|
| Malware removal |
To completely terminate Copa ransomware virus from the infected computer, a full system scan with powerful anti-malware should be performed – we recommend using SpyHunter 5Combo Cleaner or Malwarebytes |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with the FortectIntego repair tool |
Having your computer infected with Copa ransomware is not a pleasant experience, which can be extremely damaging. Unlike other malware, its effects on files are still present even after its removal, which can be performed with anti-malware tools. However, security software is not equipped with functionality to decrypt .copa files, as specific decryption tools are required.
To stop users from seeking help with Copa ransomware removal and alternative data recovery solutions, hackers also modify the Windows “hosts” file in order to prevent security-focused website access – 2-spyware.com is among them. To revert these changes, you should go to the following location on your PC and either delete the “hosts” file or remove the added web addresses and their IPs:
C:\Windows\System32\drivers\etc\
Finally, Copa ransomware virus begins the file encryption process – it targets PDF, MS Office, and other popular file types. At this stage, the malware shows using a seemingly legitimate Windows update popup window – it is there to deceive users and prevent them from canceling the encryption procedure. After data is locked, ransomware contacts its remote Command & Control server and retrieves a unique identifier, generating a ransom note in the process.
Learn how to recover .copa files without paying the ransom
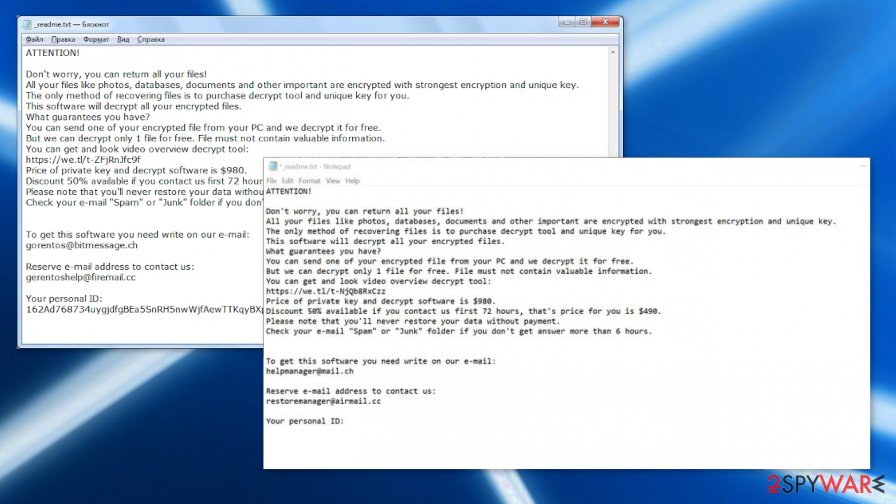
According to criminals, the only way to open .copa files is by paying them either $980 or $490 (depending on how fast you contact them) ransom:
ATTENTION!
Don't worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-NjQb8RxCzz
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
helpmanager@mail.chReserve e-mail address to contact us:
restoremanager@airmail.ccYour personal ID:
Security experts[1] to not recommend immediately obliging to the attackers and sending them Bitcoins to recover your files. They might fail to deliver the required decryptor, or it might simply not work, so there is always a risk of losing not only files but also the money.
Unfortunately, in some cases, paying hackers might be the only opportunity at recovering your Copa ransomware-affected data. But businesses, larger targets like companies or healthcare institutions stay away from such options because any contact with hackers that develop such threats like Copa virus can lead to more issues.

Multiple processes ensuring the persistence of .Copa files virus
Copa ransomware is just one of the hundreds of variants that belong to the extensive Djvu virus family, predecessors of which include Kolz, Npph, Kasp, Ogdo, and many others. These malicious programs are mainly spread via fake pirated software installers or cracks/keygens,[2], downloaded from insecure torrent websites.
The main executable can be named as anything, for example, “BitTorrent Pro v7.10.5 Crack.exe.” Since users would believe they are installing a BitTorrent client, they would not hesitate to open it. As soon as the executable is launched, it begins the infection process of a Windows machine. It is important to note that robust security programs, such as SpyHunter 5Combo Cleaner or Malwarebytes, could stop an intrusion and remove Copa ransomware before it can cause any damage.
Before the virus begins the encryption process, it performs various changes to the Windows system for the attack to be successful (if your anti-malware is not successful with reverting these modifications, we recommend using FortectIntego for this purpose). The threat performs the following:
- Deletes Shadow Volume Copies to prevent easy data recovery;
- Modifies Windows registry[3] to establish persistence;
- Establishes network communications;
- Injects thousands of malicious files;
- Launches new runtime modules and processes, etc.
During this stage, Copa ransomware virus might also inject additional modules that would harvest sensitive user information, such as login credentials or banking data, and send it directly to the malicious actors. This data can later be sold on underground hacking forums for profits or compromise other user accounts.
One of the most effective methods (besides backups) to restore .copa files is by trying Emsisoft's decryption tool. However, it will not work for every infected user. For the tool to work, your files should be encrypted with an offline ID, which means that the Copa virus is not focusing on keeping contact with its remote servers while creating victim IDs.
It is hard to determine the frequency of such failures, so you should always check by employing the decryptor. Note that somebody with the same .copa extension needs to pay the attackers, retrieve the offline key, and then share it with Emsisoft security researchers. Thus, the recovery might be available only after a significant amount of time has passed.
If your files are encrypted with an online ID, your chances of restoring data are relatively slim. Nonetheless, you can try the following:
- Using automatic System Restore or ShadowExplorer functions if those were not disabled or affected by the Copa virus;
- Employing third-party data recovery software such as Data Recovery Pro.
For more details on how to perform these alternative data restore steps, please check the recovery section at the bottom of this article. You can find tips and functions helping to recover after a ransomware infection. Base your AV detection tool selection on the antivirus detection rate/[4]
Correct steps to take when trying to remove Copa ransomware and recover encrypted data
Most users who get infected with the Copa file virus or similar ransomware have never encountered such an infection before. Suddenly, they can not open their files – an event that could cause major panic. However, panicking will not solve anything, and it is important to take the correct steps to maximize your chances of restoring your files without paying the ransom.
First of all, you should not rush the Copa ransomware removal if you have no backups available. You should first make a copy of all the important files – use cloud services or external storage devices such as USB Flash. As soon as that is complete, you should then scan your machine with powerful anti-malware software.
Security applications like SpyHunter 5Combo Cleaner or Malwarebytes should work great for this. Remember that Copa ransomware virus is dangerous and spread silently, so AV detection tools help to find those components. While the payload of the infection might not be present, there are leftovers that should be deleted in order to remediate a Windows machine. PC repair tools and optimization programs like FortectIntego can do that job for you.
After you remove Copa ransomware and are sure that all the malicious files are gone, you can start the file recovery process. We recommend using the free decryption tool, third-party recovery solutions, or attempting to check whether the automatic Windows backups were not deleted.
If none of the methods below help, there is no other way to recover encrypted .copa files at the present time. Nevertheless, keep in mind that paying criminals is always risky, so be warned before making up your mind to transfer Bitcoins.
Getting rid of Copa virus. Follow these steps
Manual removal using Safe Mode
Safe Mode with Networking can be used if malware is tampering with your security tool:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Copa using System Restore
System Restore can also sometimes be useful when trying to eliminate malicious software from the system:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Copa. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Copa from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Copa, you can use several methods to restore them:
Data Recovery Pro method could be useful when dealing with a ransomware attack
In some cases, Data Recovery Pro might be able to restore at least some of the encrypted files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Copa ransomware;
- Restore them.
Make use of Windows Previous Versions feature
This method only works if System Restore points were not deleted by Copa ransomware.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Recover files with ShadowExplorer
If malware failed to delete Shadow Copies, ShadowExporer is one of the best solutions for effortless data recovery.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Try Emsisoft's decryption tool
If your files were locked with an offline ID and somebody else retrieved the key from criminals, there is a chance that Emsisoft's decryption tool could work for you. Generally, Copa ransomware is one of non-decryptable versions
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Copa and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Lesvirus. Lesvirus. Cybersecurity advice and malware insights.
- ^ Ransomware statistics for 2020: Q1 report. Emsisoft. Security blog.
- ^ Windows Registry. Wikiepdia. The free encyclopedia.
- ^ Copa malicious file detection rate. VirusTotal. Online malware scanner.





















