Kasp ransomware (Virus Removal Guide) - Decryption Methods Included
Kasp virus Removal Guide
What is Kasp ransomware?
Kasp ransomware is yet another version in the Djvu virus family that cannot be decrypted
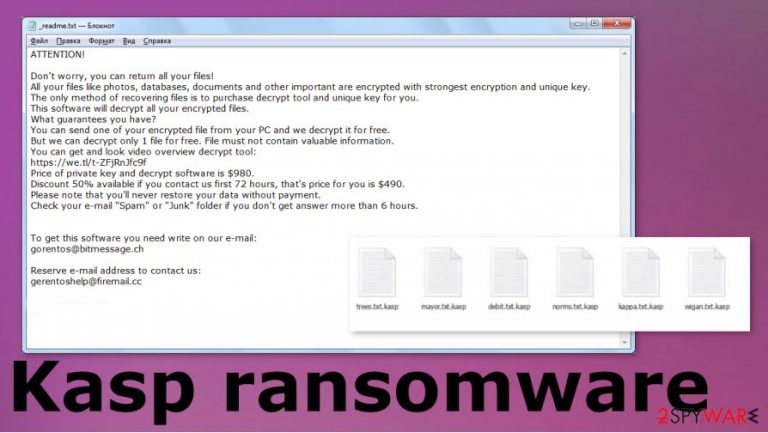
Kasp ransomware – a cryptovirus that adds .kasp file extension to pictures, documents, videos, and other data located on the compromised PC. Users[1] fill up online forums with questions about decryption and solutions to repair affected files and clear the infection. However, there are not many solutions available, since the virus employs powerful encryption[2] methods with the help of RSA cryptosystem – it ensures that files would require a unique key that is sent to cybercriminals' server, although they are not willing to provide it for free, as evident.
The identification ID is displayed in the ransom note file _readme.txt, which is dropped on various places on the system, as well as the desktop. The body text did not change for many versions so far – victims who get infected with Ogdo, Geno, and other variants will see an almost identical message from the Kasp ransomware virus creators; although contact emails this time are helpmanager@mail.ch and restoremanager@airmail.cc.
The note details the encryption impact on files and claims that the only option for the victim is paying a ransom of $980/$490. However, we do not recommend even contacting these people since criminals cannot be trusted. Remember that cryptocurrency extortionists are not focused on your belongings; they only want to make money from victims, so they might never provide the required Kast file virus decryption tool.
| Name | Kasp ransomware |
|---|---|
| Family | Kasp virus is the version of Djvu ransomware that is coming from a family of STOP ransomware viruses |
| File appendix | .kasp is the file extension that comes right after the original name of the file and file type indicating extensions. These marked files are encrypted and cannot be used nor opened without decryption |
| Ransom note | _readme.txt – a file that is used to inform people about the virus behavior and possible solutions. However, criminals state that the only possible next step is paying the ransom of $980 or $490 in Bitcoin for the alleged decryption tool |
| Distribution | The file encryption virus is spread using malicious files with ransomware payload. Such data is distributed via pirated file services, torrent sites, spam email campaigns. It is known that this virus family relies on fake Flash Updates and Adobe Photoshop cracks to inject systems with malicious ransomware payload |
| Fie recovery options |
|
| Elimination | You should think about Kasp ransomware removal immediately when the ransom demands appear on the screen. To get rid of the ransomware – get a proper anti-malware tool and run the thorough system scan that allows the program to find all the malicious files and associated programs |
| System repair solution | Besides the proper virus removal procedures, you should also make sure that traces of the ransomware and virus damage is not affecting the performance of your machine in the future. That can be ensured with tools like FortectIntego that check for damaged, affected files and can repair various functions, system files for you |
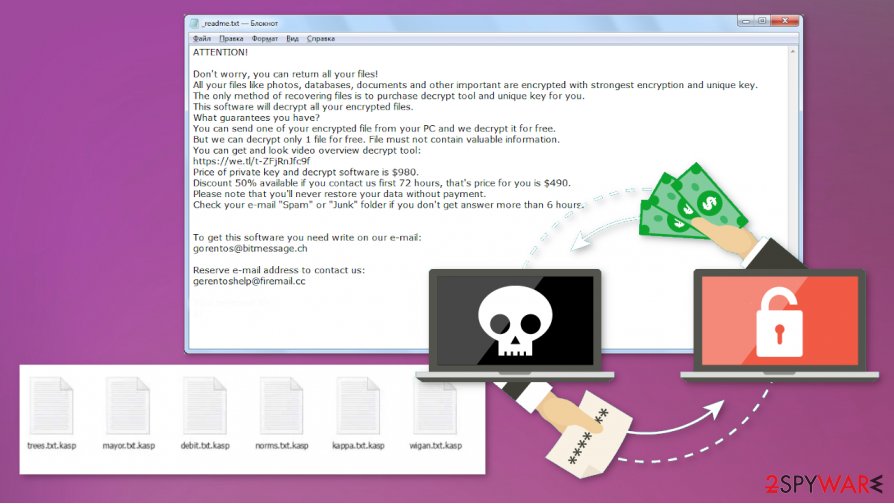
Kasp ransomware is the virus that gets distributed via malicious files and holds the particular data for ransom, so criminals gain cryptocurrency from the victims. The message that creators deliver straight to your desktop and other folders states that paying is the best solution and that you have no other options for file restoring.
However, the _readme.txt file provides contact information and steps needed to take, so you can get your files recovered, but criminals are dangerous, and based on the past versions, there is no need to contact virus creators since Kasp ransomware infection may lead to other malware attacks. Criminals can send you malicious files instead of the proper decryption tool, so ignore the message and all the claims.
Kasp file virus creators deliver the text file with a message:
ATTENTION!
Don't worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-ccUfUrQOhF
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
helpmanager@mail.chReserve e-mail address to contact us:
restoremanager@airmail.ccYour personal ID:
As any other cryptovirus, this threat demands money and tries to scare victims into providing payments. Those claims about decryption tools are not trustworthy, especially when this threat is not new and based on powerful methods and widely spread ransomware creators. You should rely on anti-malware tools and remove Kasp ransomware as soon as you got the ransom note on the system, so the threat is properly detected and terminated.[3]
Kasp ransomware should be terminated so that you can rely on options available for the system repair and file recovery. Typically, the malware attempts to contact its Command & Control server to retrieve a unique key that can only be useful for one victim. However, if this process fails, .kasp extension files might be able to be recovered with the help of the Djvu decryption tool in the future. Thus, it is extremely important that you would keep affected data on a separate medium until somebody pays the ransom and shares an offline ID with security researchers from Emsisoft.
Since there is no way to know when such events would occur precisely, you can keep running the updated version of the decryption tool. If .kasp files are encrypted with an online ID (which means that the virus successfully contacted its Command & Control server), you will see a similar message:
Error: No key for New Variant online ID: zGFdql6hM5fwiUxSnWic63XlOuDCeoRUhF47vKUA
Notice: this ID appears to be an online ID, decryption is impossible
This notification means that the decryption tool will not work for your particular case, and it will be impossible to retrieve encrypted files using the Djvu decryption tool. Keep in mind that Kasp ransomware removal with security software will not remove .kasp extension from the affected data, as anti-malware solutions are not designed for that.
To get rid of the Kasp files virus, you should employ powerful anti-malware programs, such as SpyHunter 5Combo Cleaner or Malwarebytes. While Djvu variants are known to eliminate themselves after the initial encryption is performed, it is important to note that security experts previously spotted malware being spread with other infections, such as AZORult.[4]
Besides, the malware might also inject malicious components into Google Chrome, Mozilla Firefox, or another web browser in order to steal sensitive information about you, e.g., login data or banking details. Data theft is very common when Kasp ransomware infection occurs, as malware authors can sell harvested information on the underground forums for profits.
Before you scan the machine with security software, however, you should copy all the affected files to a separate storage device, such as USB flash. This will ensure that the data will not get corrupted in the process; and note that encrypted .kasp files are not dangerous, as they do not hold any malicious code inside them.
Once that is done, you can attempt to restore all the files encrypted by this infection using alternative methods, which you can find below. Keep in mind that these solutions have low success rates due to the sophistication of the Kasp ransomware virus:
- Windows recovery solutions such as System Restore or Windows Previous Versions feature. Unfortunately, automated recovery backups are usually deleted by the virus during the infection routine;
- Third-party recovery applications. These tools might sometimes be able to retrieve some of the working copies from your hard drive.
Remember that if you add new files on the system before removing Kasp virus completely, you risk getting your files encrypted again. The procedure of terminating the virus can be difficult since there are many changes made in the system folders that affect various functions – these system features can usually be repaired with tools such as FortectIntego.
Malicious files – method of distribution that ransomware employs
The worst thing about all the cyber infections is the spreading method that involves malicious campaigns and services that people often use. This threat can spread quickly because one infected software crack file gets downloaded thousands of times, and this is the only interaction required for the malware to be triggered.
Once the user downloads malicious email attachments from the email notification or gets the pirated software file installed, it allows that malicious script to launch the payload of the ransomware directly on the system. Then ransomware can starts the encryption in the background. There are some reports that Flash Update and Adobe packages can spread this particular version.
Pay attention to sources and files you download, so you can avoid such infections. Also, keeping anti-malware tools on the system could help since these malicious files might be detected and quarantined by your AV tool before the infection even happens.
Get rid of the .Kasp files virus
It is known that Kasp ransomware virus and other threats from the cryptovirus category can act harmless and spread quickly. The coding is powerful, and there are fewer things that can stop the encryption from running quickly. As soon as you get the ransom-demanding message, the threat is pretty much done with its job of affecting your files, so the removal should start ASAP.
You should go for Kasp ransomware removal and get SpyHunter 5Combo Cleaner or Malwarebytes for the job since such anti-malware programs can find these dangerous threats and delete them alongside other associated files and applications. Run a full system scan and follow the steps suggested after that.
When you remove Kasp ransomware, pay attention to indicated intruders and double-check before doing anything else. Then, you can be sure that the virus is no longer activem and the files that you recover can be safe. However, do not forget about the possible damage and system functions. Run FortectIntego for the PC repair functions.
Getting rid of Kasp virus. Follow these steps
Manual removal using Safe Mode
The Safe Mode with Networking can help with the ransomware removal procedure when you need a smooth anti-malware scan. Enter this mode and then launch the AV tool for Kasp ransomware termination
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Kasp using System Restore
Try System Restore feature that provides a solution for Kasp ransomware infection by recovering the machine to a previous state
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Kasp. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Kasp from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Kasp, you can use several methods to restore them:
Try Data Recovery Pro for the file restoring after the Kasp virus attack
You should rely on tool that can provide options, so Data Recovery pro can be the one that restores encrypted data for you
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Kasp ransomware;
- Restore them.
Windows Previous Versions can restore files affected by the ransomware virus
Try the Windows Previous Versions feature for your individual files. However,t his option can work when the System Restore was enabled before
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer – possible solution for encrypted data
Shadow Volume Copies, when not deleted by the Kasp ransomware, can provide the solution for encrypted file recovery
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Possible solution – Djvu virus decrypter
Decryption for particular Kasp ransomware is not possible, but some of the versions can be tackled using Emsisoft Djvu decrypter
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Kasp and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Pls someone help me got .kasp virus. Reddit. Online community forum.
- ^ Encryption. Wikipedia. The free encyclopedia.
- ^ Kasp virus detection rate. VirusTotal. Online malware scanner.
- ^ David Bisson. STOP Ransomware Variant Installing Azorult Infostealer. Tripwire. The State of Security blog.







