Crypted virus (Easy Removal Guide) - Oct 2020 update
Crypted virus Removal Guide
What is Crypted virus?
Crypted ransomware is back with a new version where james.roach.10@gmail.com is given to contact the ransomware actors
Crypted is a ransomware-type cyber infection that was first spotted in the spring of 2016, appending .crypted file extension to various files on the targeted computer. It is a common extension that many ransomware families might be using for their file encryption. Most of your files that will be affected by this ransomware will change their name to .crypted. For example, most of us have files like me.jpg, document.pdf, or calendar.xls, and no matter what the file type is, they will all change to me.jpg.crypted, document.pdf.crypted, and calendar.xls.crypted.
It is not a secret that several different malware families can use the same extension after the encryption is performed, and .crypted is no exception. While older versions of the virus can be decrypted with free tools, newer variants, such as James Roach ransomware, can not. If you wonder which version of this malware you have on your Windows computer, check for more details below.
| Name | Crypted ransomware, Crypted files virus |
|---|---|
| Type | Ransomware, data locking malware, cryptovirus |
| Malware family | Nemucod, PyCL, MegaLocker, James Roach, Pay_creditcard, and others |
| Encryption methods | RSA, AES, and others (depending on a version) |
| File extension | .crypted is appended to all non-system and non-executable files |
| Ransom note | DECRYPT.txt, pay_creditcard.html, etc. |
| File Recovery | If no backups are available, recovering data is almost impossible. Nonetheless, we suggest you try the alternative methods that could help you in some cases – we list them below |
| Malware removal | Perform a full system scan with powerful security software, such as SpyHunter 5Combo Cleaner |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with the FortectIntego repair tool |
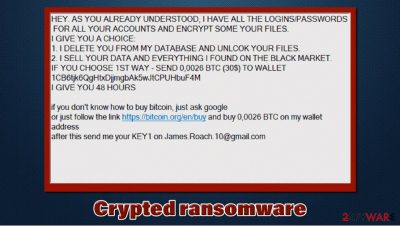
In October 2020, a new version of .crypted file virus has attracted the attention of cyber researchers where the so far unknown ransomware actors are asking to be contacted via email james.roach.10@gmail.com. Some sources call the new ransomware following the email address, so it has gained the James Roach ransomware name. Malware authors ask for 0.0026 BTC (around $35 at the time of the writing) for data recovery, so the demand is relatively low. However, we suggest you remove Crypted ransomware instead and do not communicate with the attackers. Otherwise, you might lose the money as well.
There are several older versions of this virus. In November 2017, computer users reported about data being locked with .crypted_uridzu@aaathats3as_com extension. Malware researchers have assumed that criminals created a new, undecryptable version of the malware.
Crypted virus was also known as Nemucod ransomware[1]. The file extension that it originally appends is also used by PyCL ransomware virus. When audio, video, music, images, documents, and other necessary files are encrypted, malware drops a ransom note. Depending on the ransom note, you might be able to define which of the ransomware has affected your pc.
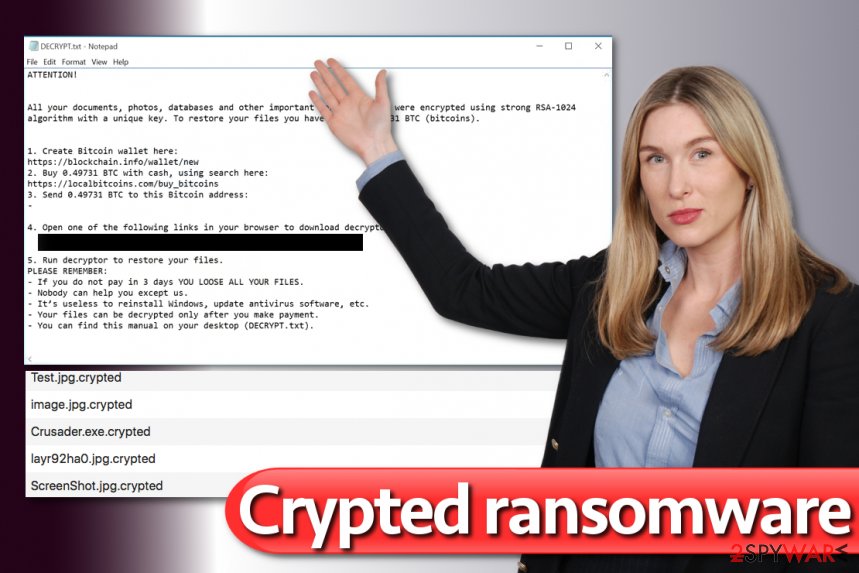
Ransom-demanding of the old .crypted virus version instructions is delivered in two files – Decrypt.txt or Decrypt.hta. They state that that victim’s files were encrypted and that one needs to buy a private decryption key[2], which can be used for data decryption. In case you see these files, follow the links to Nemucod and PyCL that were given above.
The ransom letter of the nowadays spreading James Roach ransomware will be shown in a pop-up window that will show up as desktop wallpaper and will display the text given below:
HEY. AS YOU ALREADY UNDERSTOOD, I HAVE ALL THE LOGINS/PASSWORDS
FOR ALL YOUR ACCOUNTS AND ENCRYPT SOME YOUR FILES.
I GIVE YOU A CHOICE:
1. I DELETE YOU FROM MY DATABASE AND UNLCOK YOUR FILES.
2. I SELL YOUR DATA AND EVERYTHING I FOUND ON THE BLACK MARKET.IF YOU CHOOSE 1ST WAY – SEND 0,0026 BTC (30$) TO WALLET
1CB6tjk6QgHtxDjjmgbAk5wJtCPUHbuF4M
I GIVE YOU 48 HOURSFOR MORE INFORMATION CHECK INSTALL.EXE
It is quite funny how ransomware actors try to sell their “product” in a “user-friendly way”. The removal of .crypted virus is offered for ~30 USD in bitcoin and the ransom note is available in three languages: Russian, English, and Spanish. Surely you must understand we are being sarcastic about calling this ransomware user-friendly and is always clear the ransom should not be paid. Even the amount is not big in this case, remember it is criminals who created it and you may never trust them.
The ransom note of crypted virus in Spanish will look the following:
HOLA. COMO USTED YA ENTIENDE, SUS INICIOS DE SESIÓN/CONTRASEÑAS
PARA TODAS LAS CUENTAS CONMIGO, TAMBIÉN ENCRIPTÉ ALGUNOS DE SUS ARCHIVOS.LE OFRECGO UNA OPCIÓN:
1. ELIMINARÉ SUS DATOS DE MI BASE DE DATOS Y DESCODIFICARÉ SUS ARCHIVOS.
2. VENDO TUS DATOS EN EL MERCADO NEGRO.SI ELIGE LA PRIMERA MANERA – ENVÍE 0.0026 BTC ($ 30) A WALLET
1CB6tjk6QgHtxDjjmgbAk5wJtCPUHbuF4M
TE DOY 48 HORASsi no sabes cómo comprar bitcoin – pregunta a google
o simplemente sigue el enlace hxxps://bitcoin.org/en/buy y comprar 0.0026 bitcoins a mi número de billetera.
y luego envíeme su KEY1 a James.Roach.10@gmail.com
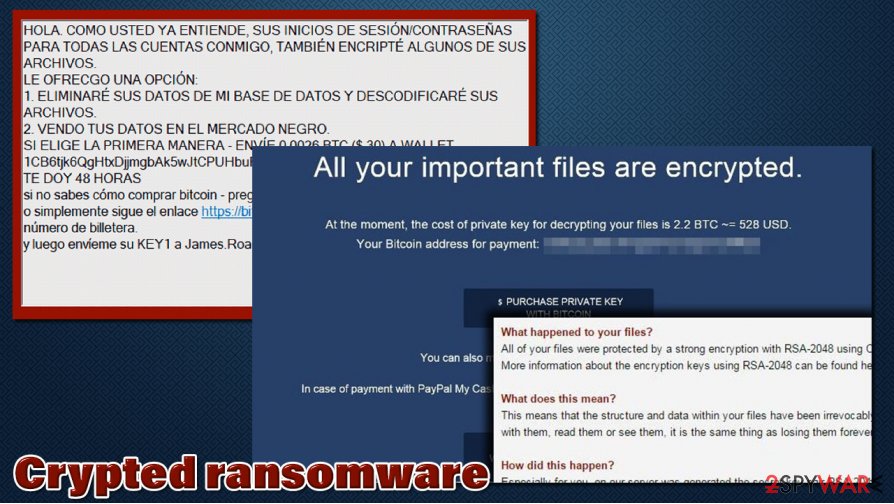
Russian version of Crypted ransomware message sounds like this:
ПРИВЕТ. КАК ТЫ УЖЕ ПОНЯЛ, ТВОИ ЛОГИНЫ/ПАРОЛИ ОТ ВСЕХ УЧЕТНЫХ ЗАПИСЕЙ У МЕНЯ
ТАК ЖЕ Я ЗАШИФРОВАЛ НЕКОТОРЫЕ ТВОИ ФАЙЛЫ.Я ПРЕДЛАГАЮ ТЕБЕ ВЫБОР:
1. Я УДАЛЯЮ ТВОИ ДАННЫЕ ИЗ МОЕЙ БАЗЫ И РАСШИФРОВЫВАЮ ФАЙЛЫ.
2. Я ПРОДАЮ ТВОИ ДАННЫЕ И ВСЁ ЧТО НАЙДУ, НА ЧЕРНОМ РЫНКЕ.ЕСЛИ ТЫ ВЫБИРАЕШЬ ПЕРВЫЙ ПУТЬ – ОТПРАВЬ 0,0026 BTC (30 $) НА КОШЕЛЕК
1CB6tjk6QgHtxDjjmgbAk5wJtCPUHbuF4M
Я ДАЮ ТЕБЕ 48 ЧАСОВесли ты не знаешь как купить биткойн – спроси гугл
или просто перейдите по ссылке hxxps://bitcoin.org/en/buy и купи 0,0026 биткойна на мой кошелек
после этого пришли мне свой KEY1 на почту James.Roach.10@gmail.com
Just like any other ransomware, Crypted virus commands to make the payment in Bitcoins.[3] However, if you are a victim of this ransomware, we recommend you to think about Crypted removal instead of paying the ransom because:
- First of all, you can never know if cyber criminals will actually provide the decryption key, or if they just want to steal your money;
- Second, think if you want to support cyber criminals in such way. The more ransoms they gather, the more motivation they get, therefore, it encourages them to continue their fraudulent activities;
- Finally, in this case, you can recover your files without paying the ransom!
.crypted files can be restored for free
The majority of ransomware viruses are undefeatable, and there is no way to restore files unless the authors of the malware reveal the decryption tool. However, in case of .Crypted ransomware attacks, malware researchers have good news. There's a free decryption tool[4] that can remove .crypted extension. You can find full data recovery instructions in the guide presented below virus' removal instructions. Keep in mind that the tool only works for older versions of the virus.
To remove Crypted virus, we recommend using SpyHunter 5Combo Cleaner or another trustworthy malware removal tool. It is not recommended to play with this ransomware and attempt to remove it manually unless you know what you're doing. If you lack knowledge about computer viruses, please do not try to uninstall this virus manually.
IMPORTANT NOTE. Please remember that .crypted file extension virus differs from .encrypted file extension virus. The latter extension is used by many different ransomware viruses such as CryptoLocker, Keranger and Crypren.
Ransomware mostly spreads via malicious spam emails
Crypted malware usually spreads via infectious emails: the cyber criminals send fake emails that contain attachments. It is vital to check if you know the sender of email before you open it or its attachments. Usually, frauds pretend to be delivering relevant documents, for example, invoices, price charts, bills, resumes, and so on.
Be careful when dealing with such emails. In addition, stay away from Spam/Junk folders as many fraudulent emails do not pass these email security filters and fall into these categories.
You should be attentive when browsing the Internet as cyber criminals tend to spread malicious files and programs by concealing malicious links on some websites. Try to avoid visiting suspicious websites, and refrain from clicking on intrusive pop-up ads or banners.
Also, avoid downloading files from insecure file-sharing networks. You might install a Trojan horse on your computer without even knowing it; reportedly, a trojan named JS.Nemucod spreads this ransomware, as well as other well-known viruses, such as Locky, Teslacrypt, KeRanger, and others.
Nemucod Trojan mostly proliferates via email in a form of malicious JavaScript file. Of course, this JS file is crafted to look safe, so inattentive users can open it without realizing how dangerous it actually is. For this reason, some security researchers[5] identify Crypted as Nemucod ransomware.
Crypted ransomware removal and data recovery
Crypted removal is a hard process. The ransomware is a complicated and well-constructed virus, which hides its components deeply in the computer system. Moreover, components of such viruses use safe-sounding names, which makes it harder to identify them.
For this reason, we recommend you to install a professional malware removal tool and terminate all programs and processes related to it. We recommend using SpyHunter 5Combo Cleaner or another top-rated malware removal software. In case you wish to remove Crypted virus but your anti-malware software won't start, follow these instructions that will help you to prepare your computer for malware removal.
Getting rid of Crypted virus. Follow these steps
Manual removal using Safe Mode
First things first, remove the virus using instructions on how to reboot your PC into Safe Mode with Networking. Once you reboot the computer into the right mode, let an automatic malware removal software do its job.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Crypted using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Crypted. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Crypted from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files have been encrypted by the discussed virus, do not even think about making the payment. Malware researchers have already discovered a method how to crack this ransomware and developed Crypted decryption software. You can find instructions how to use it below.
If your files are encrypted by Crypted, you can use several methods to restore them:
Try Data Recovery Pro software
In case the suggested decrypter doesn't help you to recover your files, you can give Data Recovery Pro a try. This data recovery software is known to be effective when dealing with corrupted or deleted files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Crypted ransomware;
- Restore them.
Use .crypted decryption software to set your files free
To recover your files, download this program – Crypter decryptor, and then find two files – the original one and encrypted version of it. You can use any file you want, and the easiest way is to use sample photos that are stored in My Pictures folder.
Once you have the two files, select both of them and drag them to the icon of the decryptor you have just downloaded and release. The decrypter then brute-forces the key, which is required for data decryption.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Crypted and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Danny Palmer. Ransomware: This free tool lets you decrypt files locked by a common version of the malware. ZDNet. Technology News, Analysis, Comments and Product Reviews.
- ^ Public Key and Private Keys. Comodo. Resources.
- ^ Simon Usborne. Digital gold: why hackers love Bitcoin. The Guardian. Latest US news, world news, sports, business, opinion, analysis and reviews.
- ^ Decrypt latest Nemucod ransomware with Emsisoft’s free decrypter. Emsisfot Blog. Latest security and malware news.
- ^ UdenVirus official website. UdenVirus. Malware Removal Advice, Cyber Security Tips.





















