Princess Locker ransomware / virus (Removal Instructions) - Mar 2018 update
Princess Locker virus Removal Guide
What is Princess Locker ransomware virus?
Princess Locker – a ransomware virus that is still active in 2018
Princess Locker is a ransomware-type cyber threat that was first detected in autumn 2016.[1]. Malware researchers thought that the virus is no longer active. However, in 2018 a new variant was spotted spreading. The behavior of the virus seems to be the same. However, it uses a new ransom note called “=_HOW_TO_FIX_RQZLIN.txt” and new Tor address.
When her highness Princess Locker was discovered, it resembled the infamous Cerber ransomware[2]. However, it hasn't become as threatening as this ransomware. However, malware uses filthy distribution techniques and once it steps in the computer, it starts encrypting files using AES encryption. Then it demands the ransom for the data recovery. It seemed that it would be hard for malware researchers to create a free decryption tool because malware generated a unique file extension for every victim.
However, researchers managed to crack ransomware’s code and offered a free data recovery solution. Therefore, if your files have been affected, you should remove Princess Locker from the computer and restore your files!
Once all files are locked, the ransomware creates and saves ransom notes that can be named as:
- !_HOW_TO_RESTORE_[the unique file extension].TXT
- !_HOW_TO_RESTORE_[the unique file extension].HTML
- @_USE_TO_FIX_JJnY.txt
- =_HOW_TO_FIX_RQZLIN.txt
The information in ransom notes consists of the ID of the victim, the unique file extension that is appended to encrypted files, and explanation on how to decrypt the corrupted data. The virus provides traditional ransomware instructions – the victim needs to install Tor browser and access a particular .onion website, which is known as “the payment site.”
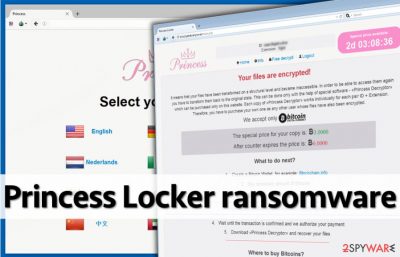
Now this is where things get suspicious. The payment website seems to be a copy of Cerber’s payment website, just with the “Princess” logo on it. Just like Cerber, it provides 12 different languages to choose from, asks to enter victim’s ID to access the payment site, and then presents the following information:
Your files are encrypted!
It means that your files have been transformed on a structural level and became inaccessible. In order to be able to access them again, you have to transform them back to the original state. This can be done only with the help of special software – «Princess Decryptor» which can be purchased only on this website. Each copy of «Princess Decryptor» works individually for each pair ID + Extension. Therefore, you have to purchase your own one as any other user whose files have also been encrypted. We accept only Bitcoin.
The virus asks for a very large sum of money – 3 Bitcoins. Such amount of money approximately is equal to 1812 USD. The virus does not allow the victim to save up money – the ransom should be paid within the time limit; otherwise, the price of the decryptor will double. Princess Locker wants to prove that its intentions are real, so it allows the victim to test the decryptor by uploading one encrypted file.
The website unlocks the file and provides a healthy file version for the victim. If Princess Locker malware has encrypted your files, please, do not waste your money by paying the ransom. This would only fuel up criminals’ efforts and allow them to continue their activities.
Besides, a malware analyst known as hasherezade has created a Princess Locker decryption software that can help you to get your files back for free. For more information about this decryptor, see data recovery instructions (provided at the end of this post). Meanwhile, remove Princess Locker virus with a strong anti-malware tool like FortectIntego or Malwarebytes. Detailed Princess Locker removal instructions are presented below this article.
As soon as malware researchers released a free decryption tool, the rumors about Princess Locker 2.0 version appearance began. Updating and releasing new versions of the powerful viruses is quite common activity. Princess Locker has been known as a hazardous and widely spread computer infection, so the chances that the new version of the malware will attack soon are quite big.
Besides, this file-encrypting virus belongs to a Ransomware-as-a-Service group, so there’s a huge possibility that other hackers are interested in renting and modifying this malware as well. We can expect new versions of this royal virus attacking computer users, so it’s impossible to protect your personal files and make data backups.
They will be helpful if Princess Locker 2.0 virus attacks your computer. Keep in mind that recently discovered decryption tool probably will not be able to recover files encrypted by the newest malware versions. So, it’s better to stay safe than sorry. However, if you encountered malware, do not hesitate and remove Princess Locker 2.0 from the computer immediately.
The new wave of Princess Locker attack was noticed in August 2017
Since malware experts managed to crack Princess Locker's code and find a way to go around the ransom-payment system with a free decryption tool, authors of this virus rushed to fix flaws in the ransomware code that led to a discovery of a free decryption tool.
The appearance of the new variant hasn't been changed. It also uses the same name for the ransom note – !_HOW_TO_RESTORE_[victim's ID].txt and appends the same ID as a new file extension to every encrypted file. The ID is a mixture of 4-6 characters of random letters and digits. However, researchers are aware of Princess Locker 2.0 virus already and currently making every effort to crack the malicious code again.
If you have been infected with Princess Locker virus but you do not know which version is it, try the decryption tool suggested below. If the tool doesn't generate the decryption tool within a few minutes, most likely you have been hit by Princess Locker 2 ransomware. In such case, we suggest you remove Princess Locker virus, back up encrypted data and stay patient. An updated decrypter can be released anytime soon. 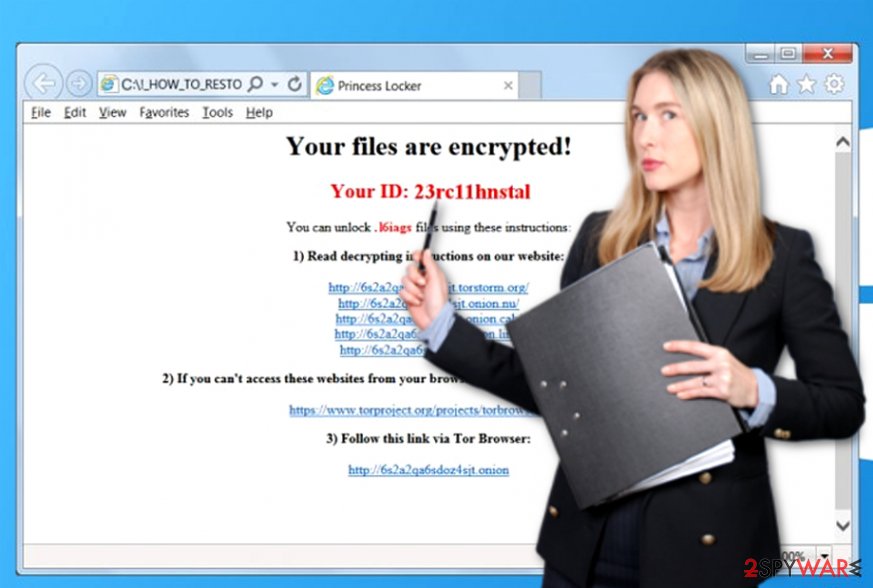
The story of this malware might resemble the case of CryptXXX when the felons and IT researchers continuously play the game of cat-and-mouse. Similarly, besides fixing the flaws in the source code, now developers decided to draw a trump card – RIG exploit kit.
Specifically, the hacking tool is laced in certain websites. If users visit them, they risk accelerating PrincessLocker 2.0 installation. Specifically, this exploit is based on Internet Explorer (CVE-2013-2551, CVE-2014-6332, CVE-2015-2419, CVE-2016-0189) and Flash Player (CVE-2015-8651) vulnerabilities[3].
The attack is also associated with 188.225.84.28 IP address. After the encryption process is done, the malware leaves _USE_TO_REPAIR_[random number].html file with further instructions. At the moment, the crypto-virus demands 0.0770 bitcoins which amounts to $368.
Malicious spam emails continue spreading ransomware virus
Just like Cerber or any other ransomware, Princess Locker virus is believed to be distributed via email, malware-laden ads and exploit kits[4]. The virus can drop its payload on the system after opening a malicious email attachment. Be aware that malicious file attachments are designed to look safe – criminals rename files as “invoice,” “speeding_ticket,” “test_results” or similarly[5].
The main way of preventing ransomware attacks is to avoid suspicious emails sent from unknown individuals. Another way of downloading malware is careless clicking on phony ads and browsing through questionable websites. Beware of malicious redirects that can throw you onto harmful web pages that contain exploit kits!
However, we understand that even the most careful users can be deceived by delusive techniques that criminals use. The most secure way to defend your computer from malware attacks is to install a reliable anti-malware tool.
Delete Princess Locker ransomware virus and decrypt your files without paying the ransom
Princess Locker virus is a highly dangerous computer infection, so please do not try to remove it manually. We recommend you to run a powerful malware remover[6] and allow it to find and remove files that belong to this virus. If you need advice which program to choose, we recommend FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
Besides, if you have been infected with Princess Locker 2.0 ransomware or other its versions, these tools should be able to help you to eliminate malware from the system. Once Princess Locker removal is completed, look at data recovery options provided below.
Fortunately, malware researchers managed to crack ransomware's code and created a free decryption tool. If you have been infected with updated or modified ransomware's version, probably you wouldn't be able to decrypt your files using this tool. In this case, check additional data recovery methods below.
Getting rid of Princess Locker virus. Follow these steps
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Princess Locker using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Princess Locker. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Princess Locker from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Do not pay the ransom. The decryptor offered by criminals is very expensive; however, there is no guarantee that it works. Besides, criminals can send you another malicious program together with the so-called decrypter. Instead, use a decryption program created by an experienced malware analyst. You can find instructions how to use it and its download link below.
If your files are encrypted by Princess Locker, you can use several methods to restore them:
Decrypt your files with Data Recovery Pro
You can try to restore files encrypted by Princess Locker ransomware with Data Recovery Pro. Instructions on how to use this tool are provided below.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Princess Locker ransomware;
- Restore them.
Use Princess Locker Decryptor
This decryptor consists of two programs – decryptor and keygen. Firstly, you will need to use the keygen to find out what is the decryption key. You need to have a copy of an original file (find it in your USB, email, CD, or DVD) and the same encrypted file. You will also need to know your unique victim's ID number and the file extension that virus has appended to your files. You will need to enter the exact name of the encrypted file, then the name of the original file, added extension, and (optional) your unique victim's ID into the keygen. If your antivirus has deleted the ransom note, and you do not know what your victim's ID is, just provide the file extension – the only problem is that this decryption method requires more time. Download the Princess Locker decryptor here. If you want to know how to use it properly, watch an informative video here.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Princess Locker and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Justin Luna. Princess Locker ransomware demands a royalty of 3 bitcoins to unlock your files. Neowin. News, Reviews .
- ^ Newly discovered versions of Cerber virus attack unsuspecting users. Virus Activity Blog. The newest information about security threats .
- ^ Jérôme Segura. RIG exploit kit distributes Princess ransomware. Malwarebytes Lab. The Security Blog from Malwarebytes.
- ^ Ransomware. Trend Micro. Securing Your Journey to the Cloud.
- ^ Cammy Harbison. New ‘Locky’ Ransomware Virus Spreading At Alarming Rate: Can The Malware Be Removed And Files Decrypted?. iDigitalTimes. A New York-based news website dedicated to covering everything digital.
- ^ Lucia Danes. Malware removal tools. 2-Spyware. Fighting against spyware.





















