Mokes malware (Simple Removal Guide) - Free Instructions
Mokes malware Removal Guide
What is Mokes malware?
Mokes malware – malicious software that targets users' banking credentials

Mokes is a cross-platform backdoor that was first discovered in 2016 by Kaspersky security researchers.[1] Malware targets Windows, macOS/Mac OS X, as well as Linux users and is packed of various capabilities, including data theft, keystroke capture, screenshot making, audio/video footage recording, and much more. While over the years, the developers used different tactics to distribute the malware, most recently Mokes virus was spotted being delivered with the help of online scams, which shows users that the security certificate has expired as soon as they land on a malicious website.[2]
Mokes malware removal is crucial to every computer owner who was infected with it. In case it is allowed to run for a prolonged time, it can steal and deliver the most sensitive data to malicious actors behind it. As a result, victims might suffer from monetary losses, installation of other malware, or even identity theft.
| Name | Mokes malware |
| Type | Backdoor |
| Platform | The malware is cross-platform – it targets Windows (Backdoor.Win32.Mokes.imv), macOS (OSX.Mokes), and Linux (Backdoor.Linux.Mokes.a) users |
| Distribution | The malware is delivered with the help of various methods, including spam emails, exploits, file sharing sites, hacked sites, and, most recently, fake security certificate alerts |
| Capabilities |
|
| Dangers | Infection of another malware, such as ransomware, financial losses, identity theft |
| Symptoms | Rarely any, although more advanced users can spot new folders and other entries created by Mokes |
| Termination | Use reputable anti-malware software that can detect and eliminate malware and all its files from the system safely – we recommend using SpyHunter 5Combo Cleaner or Malwarebytes |
| System fix | In case your Windows system is malfunctioning after you get rid of the infection (lag, crashes, errors), you can repair virus damage with the help of FortectIntego |
Mokes malware is a sophisticated backdoor that can steal information without victims noticing its presence on the device. As a result, they might suffer from significant monetary losses due to banking credential theft and also be exposed to the Dark Web, which means that the stolen data can be used to purchase goods online in victims' names, take out loans, etc. In other words, Mokes virus can result in identity theft, which can be disastrous to any individual.
Over time, Mokes malware developers used a variety of distribution techniques, including:
- spam email attachments
- targeted phishing attacks
- (zero-day) exploits
- repacked software installers
- fake updates, etc.
Once executed, Mokes virus will begin the infection of the system, which also differs, depending on the platform that is used. After the infiltration, malware will drop a variety of malicious files on the infected device and also connect to a remote C&C server, which is used to deliver stolen information, as well as receive commands from malicious actors.
Mokes malware will begin to steal valuable data from the infected individual, including keystrokes, which means that everything that is typed on online banking, social media, and other websites can be retrieved by cybercriminals. Additionally, it may take screenshots every 30 seconds and also record audio. Unfortunately, because Mokes is a silent virus, most users will be unaware that it is operating in the background and stealing an excessive amount of information about them.
Therefore, the only way to detect and remove Mokes malware is by employing anti-virus software that can scan the machine thoroughly and eliminate all the malicious files and traces. Additionally, to fix virus damage, users are recommended using FortectIntego.
Mokes malware recreates its nine times in different locations on Windows
When the Windows version of the malware was initially noticed, it also came with a valid certificate – it meant that users were not asked whether they want to execute the malicious file on their computers.
Upon infiltration on Windows machines, Mokes malware chooses nine random locations on Windows' %AppData% folder and then copies itself there. Additionally, the virus creates a folder called “version,” which holds information about a version of the installed malicious software.
For persistence, Mokes virus will create the registry keys under the following entry (this ensures that malware launches with every Windows boot – typical behavior of most malicious programs):
HKCU\Software\Microsoft\Windows\CurrentVersion\Run
Later, Mokes malware uses a built-in Windows API in order to enable the keylogger functionality on the computer, as well as record the mouse inputs of the victim. As a final step, it contacts its C&C server, which it can receive commands from every 60 seconds. All the communications are encrypted with a secure AES encryption algorithm, along with all the stolen data from the victim's machine.
Mokes for Mac creates a folder that may seem legitimate to regular users
On macOS, Mokes malware is known as OSX.Mokes or Backdoor.OSX.Mokes.a, and is written in C++ by utilizing the Qt framework. Initially, Apple patched the vulnerability that was used to proliferate the infection, but new variants of Mokes virus soon showed up, and these could bypass the newly implemented security measures.
Just like on Windows, Mokes malware typically operates silently in the background, without showing any signs or symptoms to regular users. Nevertheless, some might notice suspicious or erratic Mac behavior when the infection is present. For example, if you notice pop-ups like “Install.app wants access to control” should never be ignored, as it is an unusual behavior of the computer.
After gaining access to a Mac, Mokes will create a new folder labeled as “App Store” in the Home Library folder. This folder typically does not exist on macOS systems, but the name is used to deliberately mislead users if they happen to encounter it on their devices. Inside, it will create a service “storeuserd,” which is used to hide Mokes from being detected.
As evident, some macOS users still claim that malware is not an issue to this platform – malware strains like Mokes, Shlayer Trojan, CrescentCore, and many others prove that Macs need extra protection. Besides, the 2019 malware report, delivered by Malwarebytes researchers, claimed that Mac malware is outpacing even Windows machines.
Mokes malware distribution and avoidance techniques
Malicious actors behind the campaign used a variety of techniques to distribute the malicious program. Security researchers spotted it abusing the zero-day vulnerability within the Mozilla Firefox web browser[3] – once users land on a specially crafted site (via the redirects or adware), a weak spot within the software is abused to insert malware automatically. Thus, users are injected with malicious payload without performing any actions at all. Hence, it is vital to patch all the installed software with security updates as soon as possible (this includes the operating system as well).
Another popular technique used by attackers is spam email attachments. These typically include various attributes of legitimate and well-known companies like UPS or Amazon. Using social engineering, malicious actors pretend to be representatives of these corporations and urge users to open the attached file. Thus, make sure you never open an executable file clipped to the mail, or never allow MS Office files to run macro function.
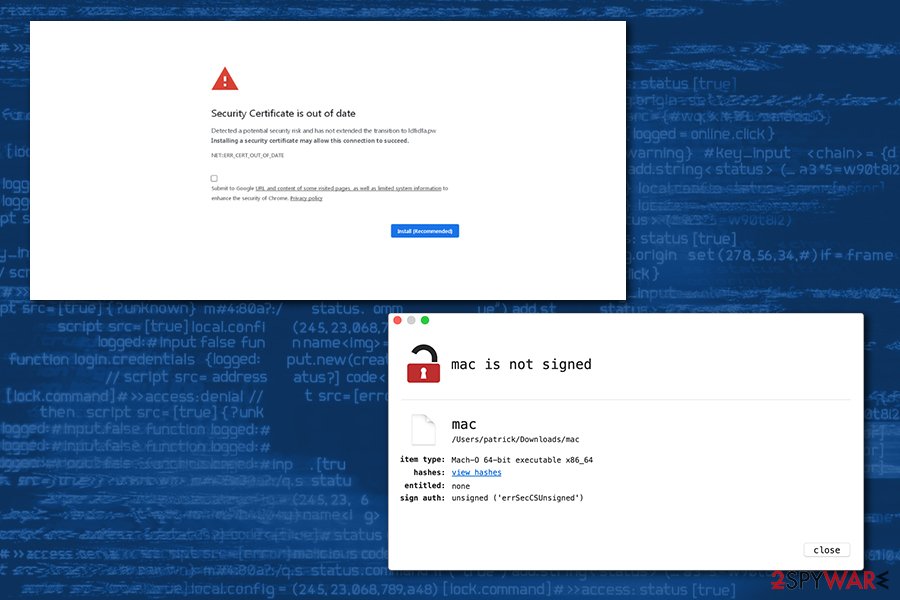
In mid- January 2020, Mokes malware was spotted in a phishing campaign abuse the trusted certificate feature on various websites, including zoo and e-commerce sites. Upon entering the page, users were met with the following message:
Security Certificate is out of date
Detected a potential security risk and has not extended the transition of Idfidfa.pw
Installing a security certificate may allow this connection to succeed.NET::ERR_CERT_OUT_OF_DATE
Submit to to Google URL and content of some visited pages as well as limited system information to enhance the security of Chrome. Privacy policy.
Install (Recommended)
Because the alert uses formatting and attributes that are typical to Google Chrome's warning alerts, many users might not suspect a thing and proceed with the installation process of the “Certificate_Update_v02.2020.exe,” which is actually Mokes malware payload. To avoid the deception, you should use sophisticated anti-malware tools along with web protection shields on your machine.
Terminate Mokes malware
As previously mentioned, Mokes virus is a stealthy backdoor that typically does not emit any symptoms. Therefore, unless you are an advanced user who knows about which files belong to the OS and which are imported by malware, you most likely never know that it is running on the background of your Windows, macOS, or Linux computer. Thus, you should employ anti-malware software to remove Mokes malware from your system at once. If you keep up-to-date security software on your computer, you can avoid most of the malicious intrusions in the future.
Note that Mokes malware removal might get interrupted due to its functionality. In such a case, you can access Safe Mode with Networking, as explained below, and perform a full system scan from there. Additionally, we highly advise you to monitor your online banking activities for unauthorized transactions, as these can often be reverted after contacting the bank. In case you find your credit card compromised, contact your bank and close it down immediately.
Getting rid of Mokes malware. Follow these steps
Manual removal using Safe Mode
Access Safe Mode with Networking by performing the following steps:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Mokes malware and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting malware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Stefan Ortloff. From Linux to Windows – New Family of Cross-Platform Desktop Backdoors Discovered. SecureList. Kaspersky's security blog.
- ^ Charlie Osborne. Backdoor malware is being spread through fake security certificate alerts. ZDNet. Technology News, Analysis, Comments.
- ^ Phil Stokes. How Two Firefox Zero Days Led to Two macOS Backdoors. SentinelOne. Security blog.
