Qlkm ransomware (guide) - Decryption Methods Included
Qlkm virus Removal Guide
What is Qlkm ransomware?
The dangers of Qlkm ransomware: here's what you should know
Qlkm ransomware is a new cryptovirus from the villainous Djvu ransomware family. As soon as this computer virus gets into a device, it encrypts all personal victim files (archives, documents, pictures, backups, etc.), thus preventing their owner from accessing them until a necessary decryption tool is used.
This virus also renames all files by appointing a .qlkm extension to all non-executable files. Until 2018, members of this family used AES-256 coding algorithm for encryption, but all the latest file-locking viruses from this lineage, use a military-grade RSA-2048 algorithm, making it very difficult to decipher the files without the help of the assailants.
Immediately after the encryption is completed, ransom note text files, titled _readme.txt, are created and scattered around the device's folders so the victims would find them wherever they look. Within those files, hackers state their demands and instructions for their victims.
One more resemblance of this virus to its previous versions is that the ransom notes are almost identical and that the creators of this cyber threat would provide two email addresses to establish contact with them – helpmanager@mail.ch and restoremanager@airmail.cc.
| name | Qlkm ransomware |
|---|---|
| Type | Ransomware |
| Family | Djvu ransomware |
| Appended file extension | Personal files are appended with .qlkm extension |
| Ransom note | _readme.txt text files are created and placed in all folders with encrypted files |
| Ransom amount | The original price for the decryption tool/key is $980, but if the victims are hasty and contact their attackers within 72 hours, then a 50% discount will be applied to lower the ransom sum to $490 |
| Criminal contact details | helpmanager@mail.ch and restoremanager@airmail.cc |
| Virus removal | Malware, including ransomware, should be removed only with the help of professional anti-malware tools to ensure their elimination is done correctly |
| System tune-up | We recommend using powerful system repair tools like the FortectIntego or similar to scan the affected computer system and fix all irregularities that the virus infection might have caused to the system registry or other key system settings or files |
Reports shows [1] that of all reported ransomware strains in the Q3 of 2020, Djvu family ransomware was in the first place with 69.9%. Our research shows that new versions are introduced nearly every week (sometimes even two in a week). Here's a list of the latest variations from this lineage:
Ransom note differs very slightly from its former versions (the whole message is displayed at the bottom of this chapter). In summary, cybercriminals are trying their hardest to convince their victims to meet their demands.
They provide a free decryption guarantee where the victims can send them a few files for test decryption. Moreover, a link to a video is provided, which shows how the decryption tool works. In other terms, cyber thieves are trying to prove that such a tool exists.
The ransom amount, or the original price for the decryption toolkit, is $980. But for victims that will contact within 72 hours of the cyberattack, the threat actors are offering a 50% discount, thus lowering the ransom sum to $490. Although meeting the assailants' demands might seem like the easiest way out of this sticky situation, we're recommending to remove Qlkm ransomware instead.
Computer virus infection elimination isn't a walk in the park and should be left to professionals. We recommend performing a full system scan with trustworthy anti-malware software such as SpyHunter 5Combo Cleaner or Malwarebytes to find, isolate, and remove the cryptovirus with all its components.
Although, before removing ransomware, users should export all encrypted files from the infected devices to an offline storage device, like a USB drive or similar. Of course, this applies only to users that didn't keep backups of their essential data.
Ransomware usually makes changes to the system registry and other core system settings and files. So following a successful cyber threat elimination, we highly recommend taking care of your devices' overall health. Do that with a powerful system repair tool such as the FortectIntego.
Developers of the virus enclose this message to their victims in the ransom notes (_readme.txt):
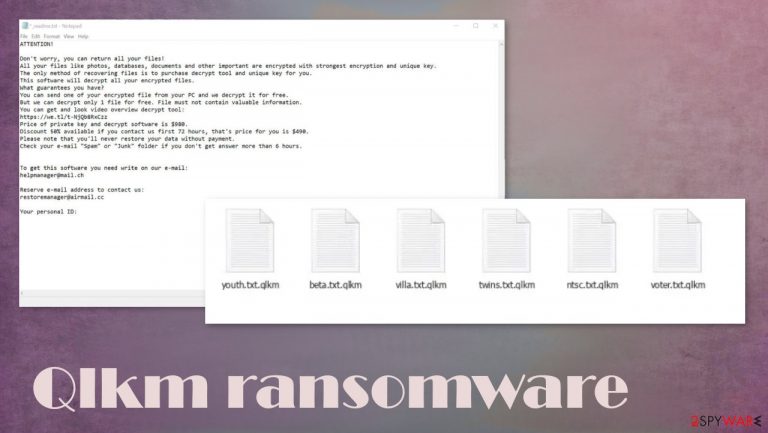
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-Dz5odBd07y
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
helpmanager@mail.chReserve e-mail address to contact us:
restoremanager@airmail.ccYour personal ID:
Avoid becoming a victim of Djvu family ransomware
Leading technology companies like Google, Microsoft, and others are constantly creating improved security measures to make everyday computer users safe while their browsing or in any other way enjoying the usefulness of the world wide web.
But cybercriminals aren't sleeping either. They're always researching new ways to attack unaware users and developing new, more sophisticated, more persistent malware. A reliable anti-malware tool is a must these days to increase home or company cybersecurity level.
Another good way to improve it is by learning how the malware is distributed. Our research shows that most of the Djvu family ransomware is spread using file-sharing platforms. To be even more specific – game cracks[2] and installers of pirated software.
So to avoid file-locking parasites from this lineage, users have to avoid file-sharing platforms, like most popular torrent sites, because cybercriminals love to exploit those types of portals by uploading their creations, camouflaged as the latest game cracks, or any other pirated expensive software.
.qlkm file recovery and infection elimination from affected devices
Getting your devices infected with ransomware is a nightmare. The only right thing to do for the owners of infected machines is to eliminate ransomware. But before doing that, they should consider using Emisoft or other third-party decryption software to try and recover encrypted files, of course, if the users didn't keep backups.
If you were lucky enough and the cyber infection didn't remove Shadow Volume Copies when encrypting your files, then Shadow Explorer might be able to recover your data from said copies. Otherwise, before Qlkm ransomware removal, export all locked files to an offline storage device and check on us later as we update our readers with the latest news.
Professional, reliable anti-malware software should be installed in every device that's connected to the internet. Applications such as SpyHunter 5Combo Cleaner or Malwarebytes should be able not only to protect your computers from cryptoviruses but also to remove the infection of ransomware at once.
Djvu family ransomware is known for making modifications in the Windows Registry to establish persistence, inserting URLs' into Windows core files preventing victims from accessing popular cybersecurity-related websites (including 2-spyware.com), and other mischiefs.
To fix all these system irregularities and get your computer back to the pre-contamination phase, experts[3] recommend using the FortectIntego tool to perform a system tune-up. If left unattended, these system changes could lead to crashing, severe lag, and other abnormal behavior.
Getting rid of Qlkm virus. Follow these steps
Important steps to take before you begin malware removal
File encryption and ransomware infection are two independent processes (although the latter would not be possible without the former). However, it is important to understand that malware performs various changes within a Windows operating system, fundamentally changing the way it works.
IMPORTANT for those without backups! →
If you attempt to use security or recovery software immediately, you might permanently damage your files, and even a working decryptor then would not be able to save them.
Before you proceed with the removal instructions below, you should copy the encrypted files onto a separate medium, such as USB flash drive or SSD, and then disconnect them from your computer. Encrypted data does not hold any malicious code, so it is safe to transfer to other devices.
The instructions below might initially seem overwhelming and complicated, but they are not difficult to understand as long as you follow each step in the appropriate order. This comprehensive free guide will help you to handle the malware removal and data recovery process correctly.
If you have any questions, comments, or are having troubles with following the instructions, please do not hesitate to contact us via the Ask Us section.
IMPORTANT! →
It is vital to eliminate malware infection from the computer fully before starting the data recovery process, otherwise ransomware might re-encrypt retrieved files from backups repeatedly.
Scan your system with anti-malware
If you are a victim of ransomware, you should employ anti-malware software for its removal. Some ransomware can self-destruct after the file encryption process is finished. Even in such cases, malware might leave various data-stealing modules or could operate in conjunction with other malicious programs on your device.
SpyHunter 5Combo Cleaner or Malwarebytes can detect and eliminate all ransomware-related files, additional modules, along with other viruses that could be hiding on your system. The security software is really easy to use and does not require any prior IT knowledge to succeed in the malware removal process.
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
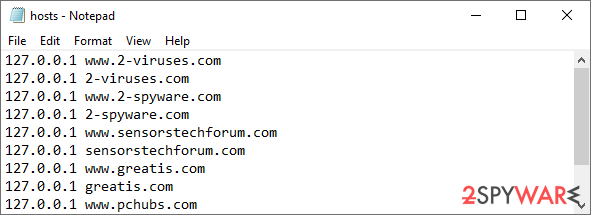
Restore Windows "hosts" file to its original state
Some ransomware might modify Windows hosts file in order to prevent users from accessing certain websites online. For example, Djvu ransomware variants add dozens of entries containing URLs of security-related websites, such as 2-spyware.com. Each of the entries means that users will not be able to access the listed web addresses and will receive an error instead.
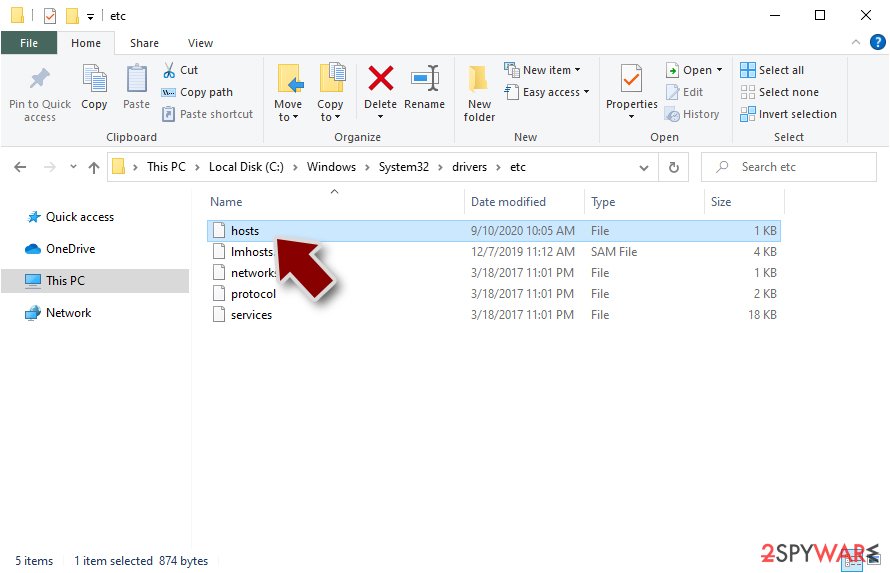
Here's an example of “hosts” file entries that were injected by ransomware:
In order to restore your ability to access all websites without restrictions, you should either delete the file (Windows will automatically recreate it) or remove all the malware-created entries. If you have never touched the “hosts” file before, you should simply delete it by marking it and pressing Shift + Del on your keyboard. For that, navigate to the following location:
C:\\Windows\\System32\\drivers\\etc\\
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Use Emsisoft decrytor for Djvu/STOP
If your computer got infected with one of the Djvu variants, you should try using Emsisoft decryptor for Djvu/STOP. It is important to mention that this tool will not work for everyone – it only works if data was locked with an offline ID due to malware failing to communicate with its remote servers.
Even if your case meets this condition, somebody from the victims has to pay criminals, retrieve an offline key, and then share it with security researchers at Emsisoft. As a result, you might not be able to restore the encrypted files immediately. Thus, if the decryptor says your data was locked with an offline ID but cannot be recovered currently, you should try later. You also need to upload a set of files – one encrypted and a healthy one to the company's servers before you proceed.
- Download the app from the official Emsisoft website.
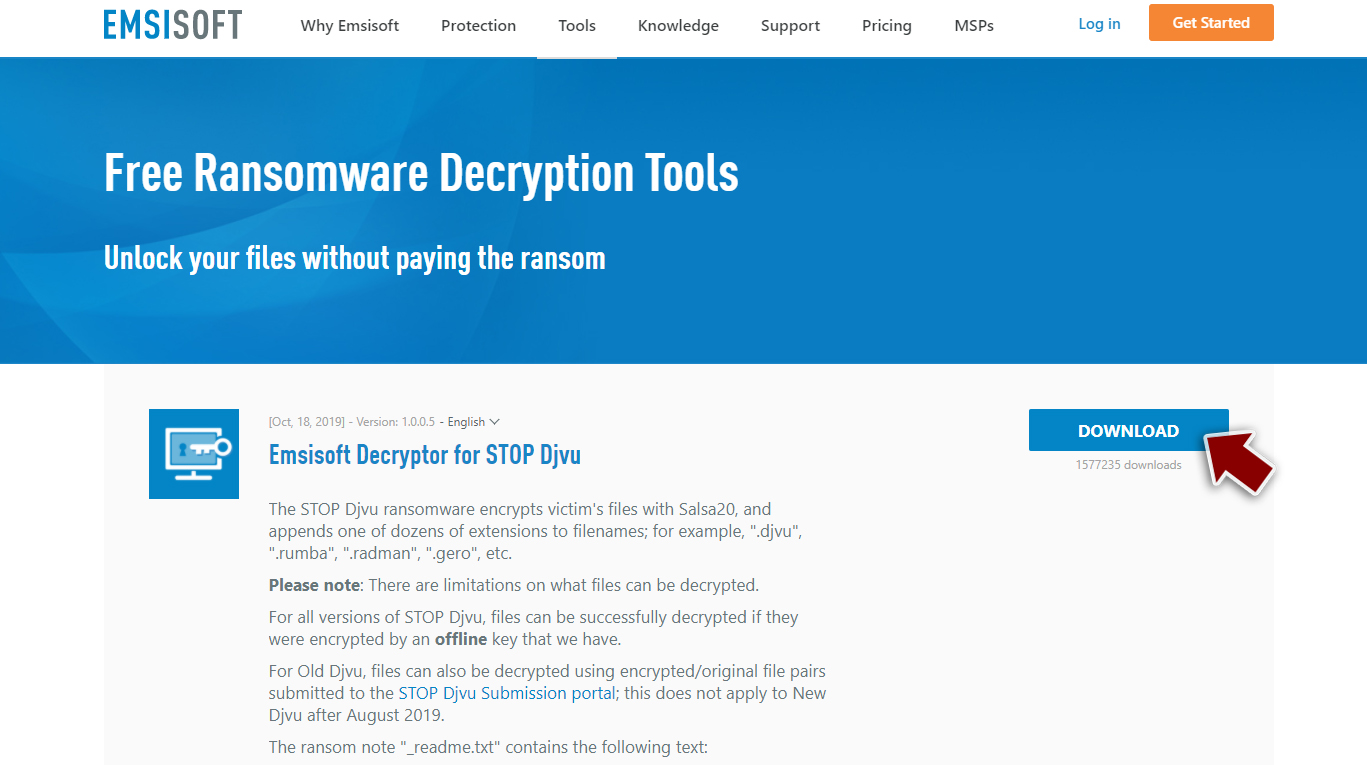
- After pressing Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe should show up – click it.

- If User Account Control (UAC) message shows up, press Yes.
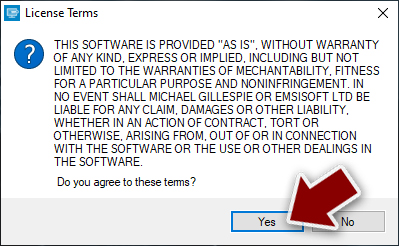
- Agree to License Terms by pressing Yes.
- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.

- Press Decrypt.

From here, there are three available outcomes:
- “Decrypted!” will be shown under files that were decrypted successfully – they are now usable again.
- “Error: Unable to decrypt file with ID:” means that the keys for this version of the virus have not yet been retrieved, so you should try later.
- “This ID appears to be an online ID, decryption is impossible” – you are unable to decrypt files with this tool.
Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Qlkm and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Ransomware statistics for 2020: Q3 report. Emisoft. Home and business computer security.
- ^ Vishal Thakur. How Are Computer Games ‘Cracked’?. Scienceabc. Fun and interesting facts from science and the universe.
- ^ Viruset. Viruset. Spyware news and security.
