.STOLEN ransomware (virus) - Recovery Instructions Included
.STOLEN virus Removal Guide
What is .STOLEN ransomware?
.STOLEN ransomware asks for ridiculous amounts of money for the locked data to be returned
Ransomware has been rampant in the last few years due to it being so lucrative. While strains like Djvu focus on home users and prevalence across the board with random targets, some malware authors tend to lean towards targeted attacks against businesses, organizations, and companies.
STOLEN ransomware has been spotted in the beginning au August 2021 and belongs to the group of crypto-malware that locks all documents, pictures, databases, and other files on the targeted network or server – and it does it in a rather interesting way. All the data is then merged into a singular file under every partition within each of the partitions under the name “ALLDATA.STOLEN.”
According to the ransom note titled READ_ME_SECURITY_WARNING.txt provided by the attackers, victims must pay a whopping 3,000 Bitcoin (approx. $137 million at the time of the writing) in order to regain access to files. After 30 days of the attack, if no payment is received, criminals claim the sum will double.
As it is not common for many other ransomware strains that target corporate networks, hackers say they would sell the secret information found to the highest bidder on the underground forums. The best solution would be not listening to cybercriminals and retrieving data from backups.
| Name | .STOLEN ransomware |
|---|---|
| Type | Cryptovirus, file-locking malware |
| Encryption method | All data is compiled into a standalone file and is renamed to ALLDATA.STOLEN |
| Ransom note | READ_ME_SECURITY_WARNING.txt |
| Contact | Via Bitmessage address BM-NBaptUA9UYd1LNe19A13YRVduqXjDZkK |
| Ransom size | 3,000 Bitcoin |
| File Recovery | If no backups are available, recovering data is almost impossible. Nonetheless, we suggest you try the alternative methods that could help you in some cases |
| Malware removal | Perform a full system scan with powerful security software, such as SpyHunter 5Combo Cleaner |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with the FortectIntego repair tool |
How large-scale attacks work
Once the attackers manage to break into the compromised network, they usually escalate privileges and move laterally as required. Typically, they spend several days or even weeks before ransomware is deployed, and only then do systems get encrypted. If the security suite is strong enough, it should detect suspicious network activities during this time. However, attackers are often pretty good at hiding their footprints, hence so many successful ransomware attacks were conducted in recent years.
Typically, ransomware encrypts several bytes of each of the non-system files located on a Windows machine. At this time, malware appends a particular file extension to each of them. It then delivers a unique victim ID to the remote server, generating a unique key for it, providing association marks.
Instead of doing this, .STOLEN virus compiles all the data available in each logical drive, clumping all the files into one file, making it extremely large (considering that companies hold a lot of data on their networks, this file can reach hundreds of gigabytes in size).
Once the systems are encrypted, hackers can then demand a ransom for the decryption key. They also threaten the company's secret information to be exposed if the payment is not transferred in time. This is a typical extortion technique that many high-profile ransomware strains, such as Maze, Ryuk, or Phobos.
The following is the ransom note message that was received by one of the victims of ransomware:
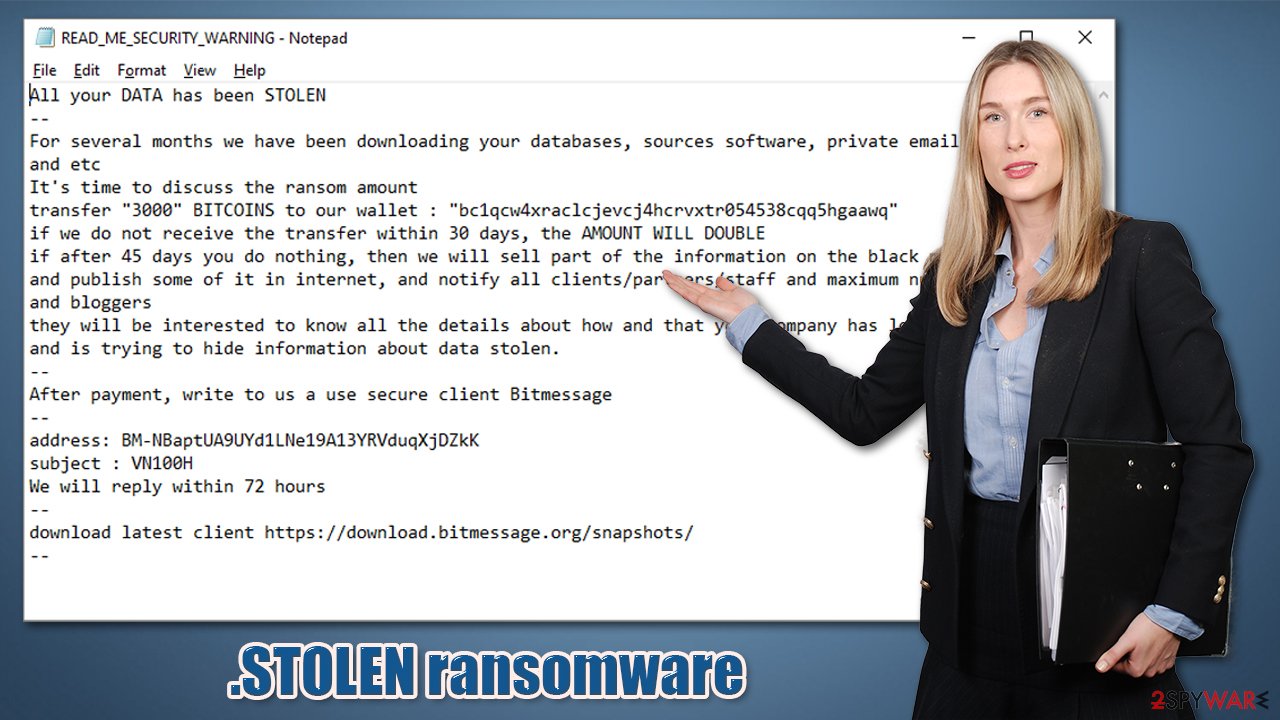
All your DATA has been STOLEN
—
For several months we have been downloading your databases, sources software, private email, documents and etc
It's time to discuss the ransom amount
transfer “3000” BITCOINS to our wallet : “bc1qcw4xraclcjevcj4hcrvxtr054538cqq5hgaawq”
if we do not receive the transfer within 30 days, the AMOUNT WILL DOUBLE
if after 45 days you do nothing, then we will sell part of the information on the black market,
and publish some of it in internet, and notify all clients/partners/staff and maximum number of media and bloggers
they will be interested to know all the details about how and that your company has lost the data,
and is trying to hide information about data stolen.
—
After payment, write to us a use secure client Bitmessage
—
address: BM-NBaptUA9UYd1LNe19A13YRVduqXjDZkK
subject : VN100H
We will reply within 72 hours
—
download latest client https://download.bitmessage.org/snapshots/
It is unclear why the attackers are asking for a ridiculous sum of money, as the average ransom payment is $178,254 for corporations.[1]
While .STOLEN files can be recovered from backups, the threat of the sensitive information being disclosed online remains. Cybersecurity experts, the FBI, and many other parties agree that ransom payments should be avoided at all costs, as it only motivates the attackers and proves that their illegal business model works.
To begin recovery process, disconnect computers from the network
The recovery process after being hit by ransomware can be difficult and lengthy. If the network has been breached, it is important to disconnect each of the machines from the network:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet

- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
If you are using some type of cloud storage you are connected to, you should disconnect from it immediately. It is also advisable to disconnect all the external devices, such as USB flash sticks, external HDDs, etc.
Once this step is complete, it is important to eliminate all the possible malicious files belonging to malware. Keep in mind that the attackers could have planted a backdoor or another malicious program on the system to exploit it later. This is why using anti-malware software, such as SpyHunter 5Combo Cleaner or Malwarebytes, is important. To ensure that malware is not interfering with this process, running the scan in Safe Mode is recommended:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.
- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.

Data recovery options
Every company needs to have a reliable data backup system that could and should be used in the case of a ransomware attack. This step should only be done once all malware traces are deleted from the network and each system is clean. We also recommend running a scan with a PC repair and maintenance utility to ensure that Windows is remediated fully:
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

Finally, you can then proceed with data recovery from NAS or other storage that was used for backups. In case malware managed to encrypt backups as well or they were unavailable at the time of the attack, there are little chances of restoring files without paying attackers (although there is no guarantee that it is possible after paying criminals, either).
One last thing we would recommend is trying a data recovery software that might be able to restore at least some of the lost files:
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Ransomware spreading techniques speculated
When it comes to regular crypto-malware, which targets home users, these are commonly distributed via methods that would reach a large number of victims. Most commonly, spam emails are sent out to thousands of people, or a malicious payload is placed on a website that distributes illegal software installers or program cracks. This makes victims to be random, and the scheme works very well considering the goal of the attackers (higher number of victims – smaller payments they are likely to afford if required).
However, attacks on businesses and companies are not that simple and often completed in multi-stages. These types of attacks focus on larger sums to be acquired from one target at a time. Targeted attacks require much more planning and a higher skill level within the hacking sphere, as corporations often use end-point protection to prevent such attacks from happening. No security measure is fail-proof, however, and cybercriminals are well aware of that.
Most commonly, the following intrusion methods could be used against large-scale targets:
- Poorly protected or unprotected RDP[2] connections
- Vulnerabilities[3] present in the corporate software
- Targeted phishing e-mails.
In order to prevent future attacks, one must ensure that network accesses is secured with strong passwords, end-point security employed, and consistent staff security training is conducted.
Getting rid of .STOLEN virus. Follow these steps
Restore Windows "hosts" file to its original state
Some ransomware might modify Windows hosts file in order to prevent users from accessing certain websites online. For example, Djvu ransomware variants add dozens of entries containing URLs of security-related websites, such as 2-spyware.com. Each of the entries means that users will not be able to access the listed web addresses and will receive an error instead.
Here's an example of “hosts” file entries that were injected by ransomware:
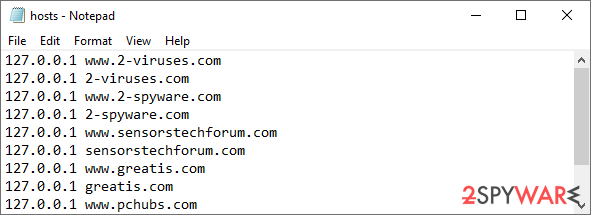
In order to restore your ability to access all websites without restrictions, you should either delete the file (Windows will automatically recreate it) or remove all the malware-created entries. If you have never touched the “hosts” file before, you should simply delete it by marking it and pressing Shift + Del on your keyboard. For that, navigate to the following location:
C:\\Windows\\System32\\drivers\\etc\\
Report the incident to your local authorities
Ransomware is a huge business that is highly illegal, and authorities are very involved in catching malware operators. To have increased chances of identifying the culprits, the agencies need information. Therefore, by reporting the crime, you could help with stopping the cybercriminal activities and catching the threat actors. Make sure you include all the possible details, including how did you notice the attack, when it happened, etc. Additionally, providing documents such as ransom notes, examples of encrypted files, or malware executables would also be beneficial.
Law enforcement agencies typically deal with online fraud and cybercrime, although it depends on where you live. Here is the list of local authority groups that handle incidents like ransomware attacks, sorted by country:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

If your country is not listed above, you should contact the local police department or communications center.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from .STOLEN and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Ransomware Attacks Fracture Between Enterprise and Ransomware-as-a-Service in Q2 as Demands Increase. Coveware. Ransomware incident response.
- ^ Danny Palmer. Big jump in RDP attacks as hackers target staff working from home. ZDNet. Technology News, Analysis, Comments.
- ^ Vulnerability (computing). Wikipedia. The free encyclopedia.
