Topi ransomware (Improved Guide) - Recovery Instructions Included
Topi virus Removal Guide
What is Topi ransomware?
Topi ransomware – a computer threat that restricts access to pictures, videos, documents, and other files until ransom is paid
Topi ransomware is a file locking virus that focuses on money extortion – it is usually propagated via infectious crack executables[1] or pirated software installers. Once installed, the ransomware disables Windows defenses and begins to scan the system and networked drives, looking for files to encrypt. After that, all personal pictures, videos, documents, databases get appended with .topi file extension, preventing victims from accessing them. During this process, the Topi virus shows a fake Windows update prompt in order to not arouse any suspicions.
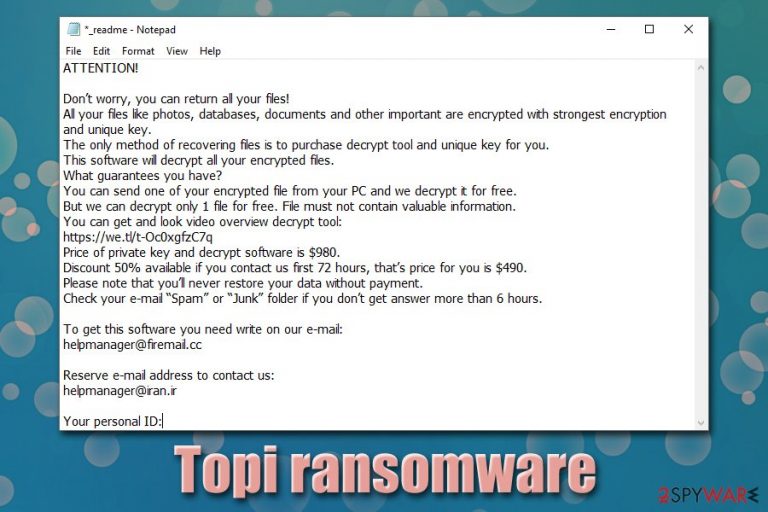
A ransom note _readme.txt is also put into most of the folders where the Topi ransomware encrypted data is located – it explains to users that they need to pay $490 in Bitcoin for Topi ransomware decryptor, as cybercriminals would not hand in the required unique key which is needed to recover data. In case the demands are not met within 72 hours, the file redemption price increases to 980$. Malicious actors also leave contact information for negotiation purposes – helpmanager@firemail.cc, or helpmanager@iran.ir.
| Name | Topi ransomware |
| Type | File locking virus, crypto-malware |
| Family | Djvu/STOP ransomware |
| Distribution | 99% of ransomware from this malware are distributed with the help of software cracks and pirated installers |
| File extension | Most of files located on the infected machine and its networked drives get appended with .topi extension |
| Ransom note | _readme.txt is a simple text file which is dropped into all folders where encrypted files are located, as well as on the desktop |
| Contact information | Hackers provide helpmanager@firemail.cc and helpmanager@iran.ir as contact emails |
| Ransom size | Threat actors ask for $490 worth of Bitcoin for decryption tool, although the sum doubles after 72 hours of the infection |
| Cipher & decryption | Malware uses a sophisticated RSA encryption algorithm, which makes it almost impossible to recover data without paying criminals the ransom. If you were lucky and the virus used an offline ID to encrypt your data, you might be able to restore files with Emsisoft's decrypter. Alternatively, you can contact Dr. Web for help (paid service) or employ third-party recovery tools, which rarely work when dealing with ransomware |
| Termination | Topi ransomware may insert data-stealing modules and remain on the system after data encryption. To get rid of the malware, perform a full system scan with security software (Safe Mode might be required) |
| System fix | Ransomware might damage some system files and wreak havoc in the Windows registry. To fix this damage done and avoid reinstallation of Windows OS, we recommend using FortectIntego |
Topi ransomware is a type of malware that is considered to be one of the most destructive ones – it can result in a permanent loss of files located on the infected computer. Discovered in late January 2019, the malware is yet another member of the STOP/Djvu ransomware family, which currently has almost 200 variants in the wild. While older versions could have been decrypted with security researcher-released tools like STOPDecrypter, Topi virus uses a far more sophisticated data encryption method with the help of secure RSA cipher.
A decryption tool was released by Emsisoft that worked for all variants released before August 2019, as they employed AES cipher, and experts managed to find a few bugs inside of it.[2] Unfortunately, Topi ransomware virus belongs to the new surge of viruses that are not decryptable.
Nevertheless, in case you were lucky, and files on your computer got encrypted with an offline ID, you might be able to recover your files with another decryption tool from Emsisoft. Nevertheless, you need to first backup this encrypted data and remove Topi ransomware from your system. For that, we recommend using security software like SpyHunter 5Combo Cleaner or Malwarebytes, and then scanning the system with FortectIntego to fix virus damage done by this ransomware.
Topi ransomware modifies hosts file to prevents users from entering security-focused sites
Topi virus exclusively targets all versions of Windows operating systems. Its ultimate goal – data encryption and monetary gain from victims who are desperate to recover access to their data. However, the ransomware also performs a variety of system changes before locking the data.
Once the infection routine is triggered, Topi ransomware places an executable file into %AppData% or %Temp% folders, which can be named as anything, i.e., c652.tmp.exe. This allows the malware to launch various malicious processes on the system, disable Windows startup repair, delete Shadow Volume Copies, change Windows registry values, etc.
Besides, it may also modify the hosts file located in C:\Windows\System32\drivers\etc\ folder in order to prevent users from getting help with Topi ransomware removal. To regain access to all websites, the affected users should go to the mentioned location and delete the hosts file – it will be recreated by Windows automatically without restrictions.
With the preparations and system modifications complete, Topi ransomware begins the encryption process – it scans the machine for files that have certain file extensions (while some other variants of Djvu did not touch executable and system files, Topi virus is known to encrypt some .exe, .dll, and similar files belonging to various applications). During the locking process, users are shown a fake Windows update window, which is designed not to make users suspicious.
Note that Topi ransomware may also insert a data-stealing module or also be related to other malware that fulfills such a role. Previously several versions of Djvu were found incorporating AZORult malware in order to steal banking information from victims. This is another reason to remove Topi ransomware as soon as possible.

After file encryption is complete, Topi ransomware will attempt to connect to its C2[3] server and generate an ID that can be done offline or online. Unfortunately, there is not much hope for recovering data if the latter is the case.
Topi ransomware will show the following ransom note named _readme.txt to its victims:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-Oc0xgfzC7q
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
helpmanager@firemail.ccReserve e-mail address to contact us:
helpmanager@iran.irYour personal ID:
Without a doubt, you should think twice before contacting cybercriminals, as they might not send you the Topi ransomware decryptor even after paying. We suggest you instead copy all the encrypted files over to an external drive and a cloud-based service and then remove the malware from the system. You can then attempt to recover .topi files with the help of our instructions found below in the recovery section.
Software cracks are often malicious and serve as one of the main ransomware distribution methods
While other ransomware developers often resort to a variety of methods when it comes to malware distribution, Djvu variants are almost exclusively spread with the help of pirated software installers and software cracks. These can usually be acquired from less-than-secure torrents and similar sires designed to distribute illegal software. This method is relatively primitive and easy to execute from hackers' point of view, but it is extremely effective, as hundreds of people get infected daily.[4]
As evident, the best way to avoid ransomware is not to download software cracks or attempt to bypass the payment process with pirated program installers. Fundamentally, cracks/loaders/keygens are tools that are designed to alter software's code, when it is considered a malicious behavior on itself. Therefore, almost each of the anti-malware would flag it as malicious, regardless if it has actually been altered to include malware inside of it. Due to this, there is no way for a regular user to determine whether such executables are safe or not.
Besides avoiding obvious online dangers, security experts also recommend following these guidelines that would allow avoiding most of the malware coming your way:
- Install reputable anti-malware software and enable Firewall;
- Do not postpone security updates on your device – software vulnerabilities can result in automatic malware infections;
- Be aware that phishing emails often carry attachments with embedded malicious macros which, once executed, download and install malware from a remote server;
- Disable Remote desktop connection as soon as it is no longer needed, and protect it with a strong password; also, avoid using the default TCP port 3389;
- Use strong passwords for all your accounts and never reuse them;
- Protect your browser: disable Flash, install an ad-blocker, clear browsing data from time to time, enable safe browsing option, etc.
Topi ransomware removal instructions
If you got caught off guard by the Topi virus, it might be extremely overwhelming, especially if you were previously unaware of such a threat before. And while it is not good news, there is still hope that your files might be recovered, so there is no need to panic straight away.
As stated before, you should not immediately perform Topi ransomware removal, however, as such an action might permanently corrupt encrypted files, and even malicious actors would not be able to help you. Therefore, first, make a copy of your encrypted files on the system – you can use USB Flash or another external device or a remote server for that. With the data copied, you can then remove Topi ransomware with the help of anti-malware software.
Note that in some cases, you might need to access Safe Mode with Networking, as malware may not allow security software to work correctly. If you do not know how to do that, please check for the directions below – follow each step carefully. Finally, once you get rid of the Topi file virus, you can then attempt data recovery – you can also find the detailed instructions on how to do that below.
Getting rid of Topi virus. Follow these steps
Manual removal using Safe Mode
In case of Topi ransomware virus is tampering with your security software, access Safe Mode with Networking:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Topi using System Restore
System Restore might work in some cases as well as :
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Topi. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Topi from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Topi, you can use several methods to restore them:
Data Recovery Pro is an excellent choice for file recovery
Data Recovery Pro is an application that might be able to retrieve working copies of your files from your hard drive.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Topi ransomware;
- Restore them.
Use Windows Previous Versions feature to recover files one-by-one
This method is only viable if you had System Restore enabled before ransomware encrypted your files.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Try ShadowExplorer – it might be successful in recovering all your data in some cases
If Shadow Volume Copies were not deleted by Topi ransomware, ShadowExplorer might be able to recover all your data.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Make use of Emsisoft Djvu decryptor
You personally will not know whether the ransomware used an offline or online ID to lock your files. Only once you employ Emsisoft's decrypter, you will see whether you were lucky or not.
Additionally, you can contact Dr.Web for help – the AV maker offers a few options for ransomware file recovery, although this method, if successful, is not free.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Topi and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Cracked software versions are harboring Djvu Ransomware in the form of .TRO files. Cyware. Cyber Fusion & Threat Intelligence Solution Company.
- ^ Zack Whittaker. A set of new tools can decrypt files locked by Stop, a highly active ransomware. Techcrunch. Startup and Technology News.
- ^ Command-and-Control Explained. Paltoalto. Cyberpedia.
- ^ Ransomware statistics for 2019: Q2 to Q3 report. Emsisoft. Security blog.







