Wbxd ransomware (Improved Instructions) - 2021 update
Wbxd virus Removal Guide
What is Wbxd ransomware?
Wbxd ransomware – a file-locking virus that demands cryptocurrency payment for the decryption software
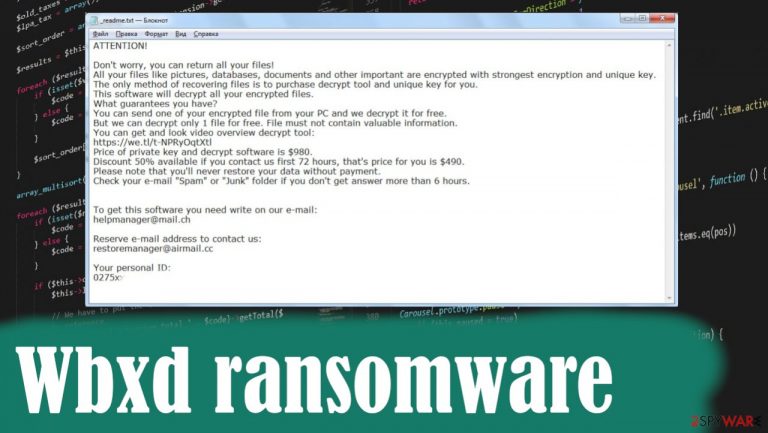
Wbxd ransomware is a cryptovirus that's developed to racketeer its victims to buy an alleged decryption tool after it encrypts personal data with a military-grade RSA coding algorithm. It also generates a ransom note titled _readme.txt and places it on the computer's desktop, in folders with the encoded files. It urges the victims to establish contact via two given emails – helpmanager@mail.ch and restoremanager@airmail.cc. Criminals state that this is the only way to get your files back, but the decryption tool, in most cases, is not provided.
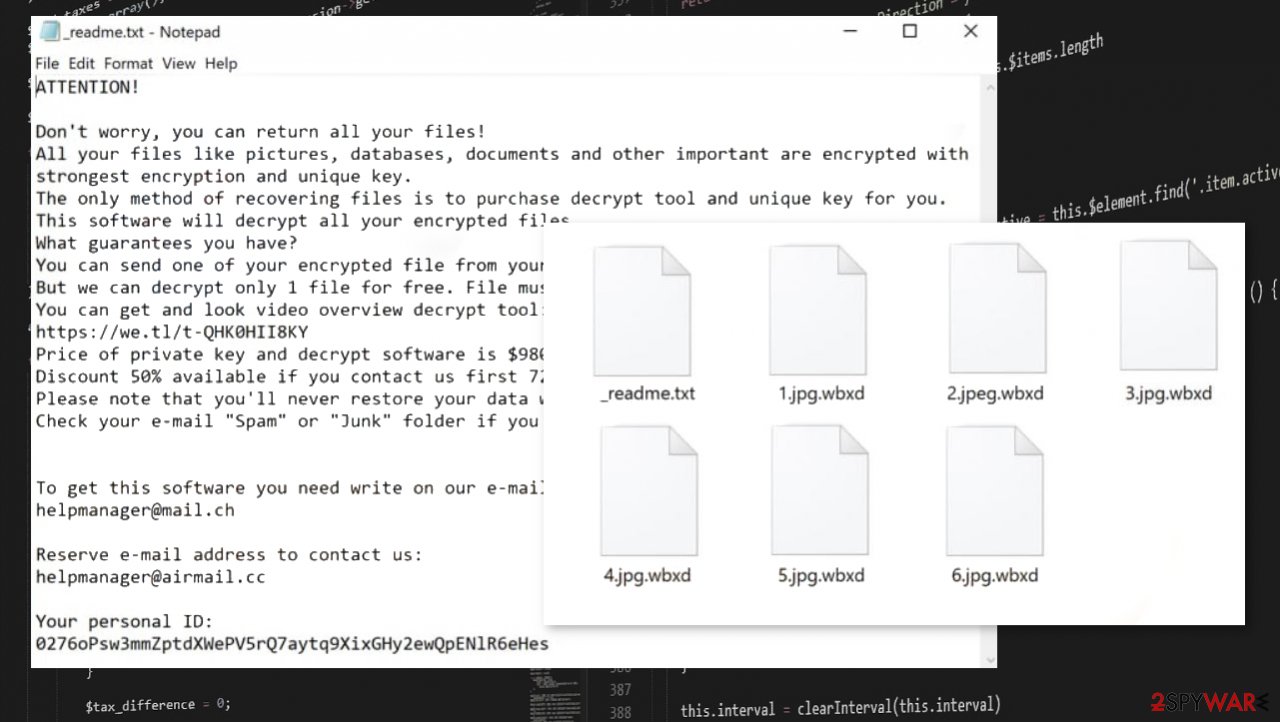
During encryption, personal files such as archives, pictures, documents, etc., are renamed by appointing a .wbxd extension to their original filenames. So if you had a file that was called 1.docx, it would now appear as 1.docx.wbxd. All files are undamaged but rendered inaccessible until a specific decryption software is used that takes the code back to the original.
An official tool that could surely help with encrypted files is not developed yet, but the Emsisofts Djvu decryption tool can work in some of the cases. It operates by determining if encryption happened using offline or online IDs. If the procedure was launched with the help of offline keys – the tool could restore affected files. You can upload your files to check if that is even possible. Otherwise, the best option for such infection remains data backups and thorough system cleaning using AV tools.
Reports indicate[1] that the Djvu ransomware family was the most commonly reported ransomware strain in the third quarter of 2020, and the Wbxd virus belongs to this family. File-locking malware from this lineage was first detected in December of 2018, and since then, it's been terrorizing everyday computer users all over the world. Many changes have been done, so each version that comes out is more powerful.
| name | Wbxd ransomware |
|---|---|
| Type | Malware, ransomware |
| Family | Djvu |
| appended file extension | Original filenames receive .wbxd extension |
| Ransom note | _readme.txt |
| Ransom amount | $490/$980 depends on whether the victims contact their assailants within 72 hours of the attack |
| Criminal contact details | Threat actors provide two emails to reach out to them: helpmanager@mail.ch and restoremanager@airmail.cc |
| Distribution | File-sharing platforms, spam emails, deceptive ads |
| Data recovery options | You can try using the tool from Emsisoft, but that decryptor only works for particular versions. Another option is the media file repair tool that restores particular types of data. The best option would be replacing those affected files with data from backups or using third-party software. You can find a guide below with alternatives |
| Virus removal | Eliminate ransomware by using trustworthy anti-malware software and a helpful guide below |
| System Repair | Use the FortectIntego system repair tool (or similar apps) to fix any damage that the system files and settings sustained |
Ransomware isn't a newly created cyberthreat as it's been around for decades.[2] Since then, it has evolved into an extremely hard to detect, persistent, hard to decrypt, easily delivered strain of malware that's use is increasing year after year.
Djvu family ransomware has also evolved since it was first spotted. To mention one example, cryptoviruses from this lineage were used to encrypt all personal data on the victims' computers by using the AES coding algorithm. The latest versions use the RSA method. And those new variations are popping up each week. Here's a few examples of them:
Within the ransom note cybercriminals state what happened to the victims' computers and what do they need to do to get back access to their files. The purpose of the note is to convince the victim to buy the decryption software, i.e., meet the demands by paying the ransom.
And the threat actors behind ransomware are trying their best to do that – they offer to send one file to them for free decryption and even provide a link to a video where the decryptor is seen in action. Moreover, they offer a 50% discount for the ransom amount if the victims contact within 72 hours of the attack, which lowers the price from $980 to $490.
The developers of the Wbxd ransomware virus send this message to their victims within the _readme.txt ransom note:
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-EtT4dX8q3X
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
helpmanager@mail.chReserve e-mail address to contact us:
restoremanager@airmail.ccYour personal ID:
–
The convincing techniques are used so the victims would jump to rash decisions and pay their assailants to get their sensitive files back. But by doing that, ransomware victims are encouraging cyberthieves to intensify their attacks and provide funds to develop more advanced ransomware.
The best way to stop cybercriminals from distributing their malicious software is by not paying them. So the greatest choice that a victim can make is to remove ransomware from all infected devices, no matter how small the ransom amount may seem.
If you had an anti-malware tool, but the cyber infection bypassed its security filters, that could mean one of two things, either its virus database was out of date, or it's too weak to catch the latest infections. We recommend using trustworthy apps such as SpyHunter 5Combo Cleaner or Malwarebytes for Wbxd ransomware removal.
We're afraid that's not all. To ensure that the virus is completely eliminated, the system files and settings are fixed, and there's no chance of infection renewal. We recommend performing an entire system scan with powerful system repair apps like the FortectIntego. Then you can try to recover those files safely. If you skip these removal steps, you might suffer from secondary ransomware encryption.
The more advanced encryption processes, the fewer .wbxd file recovery options
Djvu ransomware family that its threat belongs to recently managed to alter and improve the encryption procedures and employed a more advanced RSA algorithm started to use online keys exceptionally. Offline keys and victim IDs were also used before 2019, but such methods allowed researchers to recover victims' files entirely.
Developers of this malware now rely on online keys that get uniquely formed for each victim. It is impossible to obtain decryption keys needed for separate devices that get encrypted, so researchers cannot help Wbxd file virus victims as they were with earlier variants in the family.
Options for file recovery are limited, but it is possible to restore at least some of your files. In such instances, users understand the importance of backing your files on separate devices or cloud databases. If you have copies of those files, you can easily replace the affected data with safe copies after the thorough system removal.
Remember to clear the machine from any malware pieces before entering the different device to your computer. You can store some of the encoded files and other malware-related files on the external drive and hope for the future's official decryption tool. However, if you want to use the device right away – anti-malware tools and proper Wbxd ransomware termination are crucial.
Refrain from using file-sharing platforms to avoid Djvu ransomware family infections
It's a renowned fact within the cybersecurity community that the Djvu family spreads its viruses mostly (but not exclusively) through file-sharing platforms, such as popular torrent sites and similar. Until people decide to stop downloading pirated programs, and other illegal software, that won't change.
It's one of the easiest infection payload file delivery methods because the threat actors don't have to hack any websites or devices. Cybercriminals have to think of a catchy name, for example, a crash for the latest, most anticipated game, and upload their creations.
Since there are no security protocols that check every uploaded file, their developed ransomware can easily spread around the world without them doing much. To avoid getting your devices, please don't use torrent sites to download any illegal activation toolkits, unlocked commercial applications, or other pirated software.
Remove ransomware virus with our simple instructions
As we've pointed out in the first chapter of this article, paying the ransom only motivates cybercriminals to infect more innocent people with their created malware, so if you were unlucky enough to get your device infected, the only right thing to do is to remove Wbxd ransomware.
But before doing that, victims should consider either using free Emisoft decryption software or copying all their encrypted files into an external, offline storage device. If their free decryptor isn't working, there's always hope that the necessary tool will be created sooner or later.
After either of those options is done, it's time to take on ransomware removal. Manual elimination is possible, but it isn't a walk in the park, so first try using SpyHunter 5Combo Cleaner or Malwarebytes anti-malware software. If the virus is persistent and can't be deleted normally, you'd have to do it in Safe Mode with Networking. A detailed guide for that is provided just below this chapter.
When you get rid of the cyber infection from your device, you have to perform a system repair because viruses from this lineage are known to insert themselves into various system settings and files, such as the Windows Registry, host files, and so on.
This way, they prevent anti-malware software from detecting them, making cybersecurity webpages inaccessible to the victims, and other system irregularities. That's why experts[3] recommend downloading the FortectIntego system repair tool and performing a full system scan with it to restore any changes that virus could have caused to the system so you would encounter any abnormal device behavior, such as cyber threat renewal, crashing, severe lag, etc.
Getting rid of Wbxd virus. Follow these steps
Manual removal using Safe Mode
If the cyber infection can't be deleted in normal Windows mode, reboot your computer and start it in Safe Mode with Networking
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Wbxd using System Restore
Cryptoviruses can also be eliminated with the help of System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Wbxd. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Wbxd from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Wbxd, you can use several methods to restore them:
Using Data Recovery Pro to retrieve encrypted files
Data Recovery Pro might be able to restore .wbxd extension files:
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Wbxd ransomware;
- Restore them.
Individual file recovery can be made with Windows Previous Version feature
This Windows function might let the victims recover .wbxd extension files to their previous versions:
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Shadow Explorer – a powerful file recovery app
Most cryptoviruses delete Shadow Volume Copies, which Shadow Explorer uses to recover data. If they weren't encrypted or removed, then this app might help you to retrieve your files.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Possible Wbxd ransomware decryption methods
A company called Emisoft is trying to help ransomware victims by creating free decryption tools. This software might not help to recover your files now, as this cryptovirus is brand new, but you can still download it and give it a try.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Wbxd and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Ransomware statistics for 2020: Q3 report. Emisoft. Security blog.
- ^ Juliana De Groot. A History of Ransomware Attacks: The Biggest and Worst Ransomware Attacks of All Time. Digitalguardian. The digital guardian blog.
- ^ Lesvirus. Lesvirus. Spyware and security news.







