ZestyPeak mac virus (Free Instructions)
ZestyPeak mac virus Removal Guide
What is ZestyPeak mac virus?
ZestyPeak is a virus designed to specifically infect Mac systems unnoticed
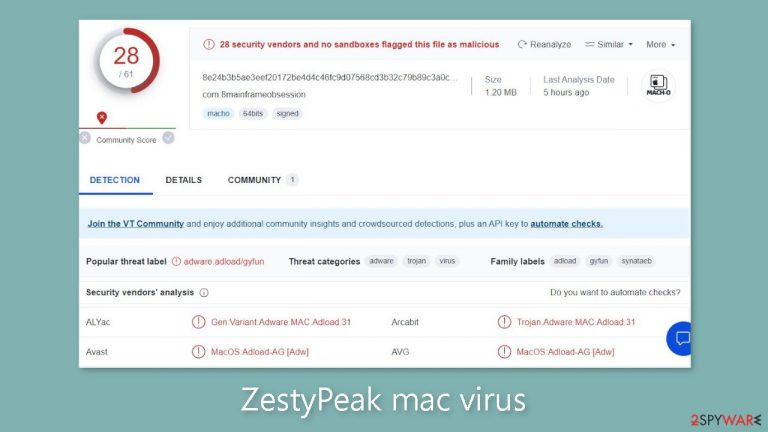
ZestyPeak appears as a macOS virus with adware[1] capability and the ability to take over Macs. When it infiltrates a system, it changes browser settings such as the homepage, new tab address, and search engine. As a result, it begins to generate promotional material such as pop-ups, banners, and redirections.
Nonetheless, the virus's harmful nature exceeds initial expectations. Without the user's knowledge, it automatically activates hazardous URLs and installs potentially unwanted programs (PUPs) as well as malware. This adware is more aggressive than adware geared at Windows platforms, and it is classified as part of the Adload malware family.
It is capable of evading Apple's security mechanism, XProtect,[2] leaving users ignorant of its presence until its impact becomes apparent. Navigating to the “Applications” directory will allow you to detect the harmful application within the system. All viruses in the Adload family have a similar appearance, with a magnifying glass symbol surrounded by a green, teal, or grey circular design.
| NAME | ZestyPeak |
| TYPE | Adware, browser hijacker, mac virus |
| MALWARE FAMILY | Adload |
| SYMPTOMS | Changed homepage and new tab address, a different search engine; redirects to shady websites, increased amount of commercial content |
| DISTRIBUTION | Fake software updates, deceptive ads, software installations from peer-to-peer file-sharing platforms |
| DANGERS | Altered search results can lead to dangerous websites; pop-up ads might be promoting scams; the virus can install other PUPs or even malware in the background |
| ELIMINATION | Eliminating this Mac virus manually can be complicated if you do not have experience. The most effective way to remove it is with a professional security tool that can scan your system to delete every related file |
| FURTHER STEPS | FortectIntego should be used to completely wipe out any data left and fix the remaining damage |
We've already investigated a number of programs, including PathwaySpan, UrbanClassic, FeedWild, and many others. The creators of these infections are constantly refining their techniques to avoid detection by security systems. Although many Mac users believed that they were immune to infection, this concept has been disproven for quite some time.
By removing just one element, the Adload developers were able to make their code undetected by XProtect. Furthermore, they use other evasion techniques, such as dispersing program-related files throughout the entire system, making them far more difficult for the typical user to detect.
Uninstalling the program isn't as simple as dragging it to the bin because it quickly reinstalls itself. The virus also leverages many components, such as Login Items and Daemons, to prevent users from removing the extension and the application that has been installed at the system level.

How to avoid Adload?
Because of the serious threat posed by the prolonged presence of this dangerous application within your system, it is critical to avoid it as much as possible. Unfortunately, many Mac users' sense of invincibility often leads them to overlook the simple and essential recommendations provided by security specialists. Unsafe browsing habits, such as accessing questionable websites and clicking on random links, exacerbate the problem.
It is best to avoid websites that engage in unlawful activity, such as illegal streaming platforms, torrent sites,[3] and peer-to-peer file-sharing networks. Such sites, which operate outside of governmental scrutiny, are rife with deceptive adverts and hidden redirects, encouraging the spread of harmful apps using manipulative social engineering strategies.
Adload is frequently distributed through fraudulent Flash Player updates. Users are routinely confronted with webpages claiming the outdated status of their Flash Player version, coercing them to install the supposedly most recent edition in order to play back media such as films and web-based games seamlessly. However, it's important to note that Flash Player was discontinued in 2020, and HTML5 took its place, making supplemental software obsolete for online media consumption. Modern websites already include built-in functionality for this purpose. As a result, any message pushing a Flash Player upgrade is simply false.
Another common method of adware distribution is software bundling. The ZestyPeak macOS virus may have entered your system during the installation of another program, which is frequently accomplished via freeware distribution websites. These platforms covertly embed supplemental software components within their installers, a practice that is typically not disclosed on their websites.
Remove the ZestyPeak mac virus
Manual removal can turn into a race against time. Battling launch agents, daemons, and cronjobs might require multiple attempts, as some components could rewrite themselves after deletion. It's wise not to attempt this unless you're well-versed in identifying and eliminating specific files. Some files might bear a .plist extension, indicating a standard settings file utilized by macOS applications to store configuration data.
The application employs diverse persistence techniques, scattering files across the system. This complexity complicates the removal of browser extensions and applications.
For peace of mind, it's advised to rely on professional anti-malware tools, such as SpyHunter 5Combo Cleaner or Malwarebytes, capable of detecting and eliminating unwanted programs. This approach is especially crucial as the virus might have introduced additional malicious programs, ensuring a thorough system cleanup.
If you still want to try and delete it manually, proceed with these steps:
- Open Applications folder
- Select Utilities
- Double-click Activity Monitor
- Here, look for suspicious processes related to adware and use Force Quit command to shut them down
- Go back to the Applications folder
- Find ZestyPeak in the list and move it to Trash
If you are unable to shut down the related processes or can't move the app to Trash, you should look for malicious profiles and login items:
- Go to Preferences and select Accounts
- Click Login items and delete everything suspicious
- Next, pick System Preferences > Users & Groups
- Find Profiles and remove unwanted profiles from the list
There are likely to be more .plist files hiding in the following locations – delete them all:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any suspicious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

The manual elimination process might not always result in total virus removal. Therefore, we still strongly suggest you perform a scan with security software.
Remove the browser extension
ZestyPeak adds an extension to your browser, initiating undesirable tasks. It potentially gathers sensitive data, transmitting it to tracking servers. This data could include your IP address, username, macOS version, browser specifics, computer ID, “Applications” folder contents, and a roster of agents, daemons, and system configuration profiles.
Following the removal of hazardous files from your system, it's crucial to promptly uninstall the extension. Utilize FortectIntego to automatically clear cookies and cache. This tool can also rectify damaged files and system errors, leading to enhanced machine performance.
If you prefer doing this yourself without additional help, here are the instructions. You will find guides for Google Chrome and Mozilla Firefox at the bottom of this article:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Cookies and website data:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
The simplest and quickest solution to this is completely resetting Safari:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in the menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

Getting rid of ZestyPeak mac virus. Follow these steps
Remove from Mozilla Firefox (FF)
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Remove from Google Chrome
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

How to prevent from getting adware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Taina Teravainen. Adware. TechTarget. SearchSecurity. Definitions.
- ^ Protecting against malware in macOS. Apple. Platform Security.
- ^ Brad Haddin. 4 risks of using torrents. Creative. Apps, Gadgets, Opinion, Tech.
