Black Claw ransomware (Virus Removal Guide) - Recovery Instructions Included
Black Claw virus Removal Guide
What is Black Claw ransomware?
Black Claw ransomware is encryption-based malware that locks personal and some system files for blackmailing victims
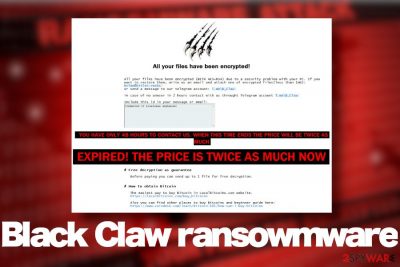
Black Claw ransomware, otherwise known as BlackClaw or .bclaw file extension virus, is one of the latest crypto-malware revealed ar the end of May 2020. First spotted by a ransomware researcher Amigo-A[1] it turns out as a separate ransomware variant geologically not bound to any of previously known viruses of its type. According to the researcher, it uses a combination of AES and RSA encryption algorithms to lock data on a host machine. A successful encryption process is followed by a ransom note RECOVER YOUR FILES.hta, which commands victims to email criminals via bclaw@hitler.rocks email address or T.me\B_Claw telegram.
The main distinctive marker of this ransomware is the .bclaw file extension, which appears as a suffix of each video, photo, Microsoft Office document, file archive, etc. encrypted. Typically, the extension is preceded either by the ID number, which can also be seen on the ransom note or ten randomly generated lower case letters in square brackets. Unfortunately, there is no Black Claw decryption software for unlocking files for free.
Victims of the bclaw file virus have two options, i.e. they can either contact criminals within 48 hours and pay the ransom after negotiations or run a full system scan after that attack while Windows is in Safe Mode[2] and remove all malicious entries that belong to this ransomware. We strongly advise victims not to pay the ransom because messing up with criminals can lead to privacy violations. Besides, no one can guarantee that crooks will send you a functional Black Claw decryption key.
| Name | Black Claw |
| Also known as | BlackClaw or .bclaw file extension virus |
| Geneology | This ransomware is not attributed to any ransomware family. It's a standalone encryption-based ransomware |
| Detection date | The virus has been spotted by ransomware researcher on May 26, 2020 |
| File marker | .[].bclaw or .[XXXXXXXXXX].bclaw The XXX part typically consists of 10 random lower letters |
| Ransom note | RECOVER YOUR FILES.hta |
| Encryption model | Combination of AES and RSA ciphers |
| Contacts | bclaw@hitler.rocks Telegram: T.me\B_Claw |
| Symptoms | Personal files cannot be opened because of a malicious file extension appended to each of them. Ransom note file created in every folder that contains encrypted data. Systems performance is slower than it used to be. The system restarts randomly, etc. |
| Danger | The ransomware encrypts personal data and not paying the ransom can lead to permanent data loss. Besides, this virus initiates aggressive changes within the Windows registry, startup processes, and other components, thus diminishing the system's vulnerability. The ransomware can download other malicious programs, such as Remcos trojan or NjRat. |
| Elimination | It is not possible to remove bclaw file virus without a professional anti-malware suit. Manually identifying malicious encryption-based files is not possible even for IT-savvy people. |
| Data recovery | No free encryption software is available for now. However, upon ransomware removal, you can try using alternative third-party data recovery tools. A full guide on how to recover encrypted files is provided at the end of this article. |
| System recovery | Take advantage of the FortectIntego repair utility to restore damaged Windows registry entries, removed system files, or disabled core processes. |
BlackClaw ransomware virus is not reminiscent of any viruses of its type. Starting from the extension and ending with the design of the ransom note. However, just like other crypt-viruses, for example, the infamous Djvu, Phobos, RagnarLocker, Zeronine, and others, it exhibits similar traits:
- spreads via trojans, open RDPs, malicious spam email attachments, etc.
- initiates multiple system's changes in the background before encrypting files;
- uses a popular encryption model (combines AES and RSA);
- generates a .hta file as a ransom note;
- demands victims to contact and pay the redemption;
- disguises malicious processes to increase prevalence;
- removes Volume Shadow Copies of encrypted files, etc.
It's extremely important to remove BlackClaw ransomware virus from the system as soon as its marker is noticed on files. In many cases, this type of virus carries additional virus payloads. Consequently, the longer you keep this virus installed, the higher is the risk of getting infected with malicious spyware or RAT.
Right after installing the bclaw virus file marker is not immediately disclosed. The virus is initiating a multiplicity of changes within Windows registries, injects malicious files on Desktop, User_folders, and % TEMP% directories. This way it ensures itself a smooth load among Windows boot.
Upon successful unravel, the Black Claw file-encrypting virus launches its encryption scanner and adds the file marker to each encrypted file. Consequently, the victim can no longer open or modify the files that belong to him or her. At this point, criminals shatter the victim's confinement by presenting a RECOVER YOUR FILES.hta ransom file.
The criminals behind .bclaw file extension virus demand their victims not to exceed time limit, which is 48 hours for establishing contact. Otherwise, the ransom size (not specified yet) gets doubled. The email address provided for info is bclaw@hitler.rocks, though alternatively, people can contact crooks via the Telegram account T.me \ B_Claw. The original text on the ransom note says:
All your files have been encrypted!
All your files have been encrypted (WITH AES+RSA) due to a security problem with your PC. If you want to restore them, write us an email and attach one of encrypted
files(less than 1mb): bclaw@hitler.rocks
or send a message to our telegram account: T.me\B_Clawin case of no anwser in 2 hours contact with us throught Telegram account T.me\B_Claw
Include this id in your message or email:
YOU HAVE ONLY 48 HOURS TO CONTACT US. WHEN THIS TIME ENDS THE PRICE WILL BE TWICE AS MUCH
# Free decryption as guarantee
Before paying you can send up to 1 file for free decryption.
# How to obtain Bitcoin
The easiest way to buy Bitcoin in Localbitcoins.com website.
https://localbitcoins.com/buy_bitcoinsAlso you can find other places to buy Bitcoins and beginner guide here:
https://www.coindesk.com/learn/bitcoin-101/how-can-i-buy-bitcoins# ATTENTION !!!
DO NOT RENAME THE FILES.
BLACK CLAW RANSOMWARE
Do not fall for intimidations that the ransomware will permanently delete bclaw virus files if you attempt to rename them or use security software. That's usually a scare tactic that criminals use to increase the prevalence of the virus and restrict people from using AV tools.
 Black Claw ransomware is a dangerous crypto-malware that renders files useless and demands victims to pay a redemption for a decryption key
Black Claw ransomware is a dangerous crypto-malware that renders files useless and demands victims to pay a redemption for a decryption key
If you have been attacked by this malicious virus, we strongly recommend you to restart the system into Safe Mode (a guide below the article explains how to to that) and run a scan with a reputable anti-virus to remove Black Claw virus from your machine. To ensure the elimination of each malicious entry that belongs to this threat, use tools like Malwarebytes or SpyHunter 5Combo Cleaner.
BlackClaw ransomware infection can be devastating for the overall system's performance. The compromised files and processes can severely diminish its performance and, thus one the backdoor for subsequent infections. To revert the damage that the bclaw file virus triggered, use recovery software to scan the system after virus elimination.
Keep the system protected while the exact itinerary of the ransomware is unknown
It would not be correct to say that ransomware distribution methods are not known. As for this particular ransomware virus, it's not yet clear what methods its developers use for the dissemination. Therefore, as long as researchers are working to find out how it spreads, what are its potentials, and how to decrypt its files, we recommend arming the machine with all possible security tools, including antivirus solution (full pack), enable reliable ad-blocker, and use real-time protection for scanning email attachments.
There are loads of methods that hackers take advantage of to find security loopholes on the targeted machines. Although the methods are more or less similar for all malware, ransomware developers use more aggressive scripting and exploit to short-circuit machine's protection. The following ways of encryption-based malware distribution techniques are the most common:
- Malicious email spam attachments. According to IBM[3], 59 percent of ransomware infects PC via obfuscated ZIP, PDW, EXE, and similar files that render Macros.
- Malvertising. Hackers find ways to abuse legal channels of the ads injecting malicious codes inside popups and banners positioned on shady websites.
- Exploit kits. Exploit kits, such as Rig exploit kit allow criminals to gain full control over the host machine without its owner's knowledge and subsequently initiate malicious redirects to malicious servers.
- Torrenting websites. The content shared on peer-to-peer networks is not controlled by anyone. Thus, hackers can impersonate regular users and distribute files, such as software cracks or keygens with an additional ransomware payload.
 Black Claw ransomware virus can trigger permanent data loss
Black Claw ransomware virus can trigger permanent data loss
Learn how to remove Black Claw ransomware in the right way
Usually, people get shocked after finding the .bclaw file extension virus on their data. Not only files get compromised but the entire system may run in an abnormal way. Not to mention a threatening ransom note that shouts out loud “pay me the money.” However, security experts from dieviren.de[4] recommend people to calm down and do not rush paying the ransom.
The best solution in this unpleasant situation is a full bclaw file virus removal. Before that, use a USB flash drive to copy all affected files to prevent permanent file loss. After that restart Windows in Safe Mode with Networking as explained below then run a thorough scan with an antivirus tool that you have on your machine. If you don't have one, we recommend downloading SpyHunter 5Combo Cleaner or Malwarebytes tools as they are great programs for eliminating malware and protecting the machine for subsequent cyber-attacks.
Note that manual Black Claw ransomware removal is not possible under any circumstances. This pest roots deeply into the operating system and can misuse legitimate processes to disguise its own malicious procedures. Thus, the only way to repair your machine is to use an automated security program for ransomware elimination and then recover it to the previous state with the help of FortectIntego repair solution.
Getting rid of Black Claw virus. Follow these steps
Manual removal using Safe Mode
If you are dealing with a ransomware virus for the first time, you may need help in launching a security program. The only way to remove Black Claw ransowmare virus is to restart Windows OS into Safe Mode as shown below and activate AV scanner.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Black Claw using System Restore
You can also try to recover your machine with the help of the inbuilt System Restore feature:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Black Claw. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Black Claw from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Files encrypted by .bclaw extension cannot be recovered for free. Unfortunately, a free decryptor is not available, at least for now. Nevertheless, you can try third-party data recovery programs to get at least some of your files back.
If your files are encrypted by Black Claw, you can use several methods to restore them:
Data Recovery Pro software might be helpful
As soon as you delete the ransomware, download Data Recovery Pro and set it to scan your machine.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Black Claw ransomware;
- Restore them.
ShadowExplorer can help to retrieve some of the files
Upon Black Claw removal find the most valuable files and try to retrieve them with the help of Volume Shadow Copies. In case the virus have deleted them, this method will not work.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Experts are working on to develop ShadowExplorer decryptor. Currently, it's not available.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Black Claw and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Amigo-A profile. Twitter. Social media network.
- ^ How do computer viruses work?. Kaspersky. Anti-virus software developers.
- ^ Nihad A. Hassan. Ransomware Distribution Methods. Spring link. Over 10 million scientific documents.
- ^ SICHERHEIT- UND SPYWARE-NEUIGKEITEN. Dieviren. Virus and spyware news.





















