Corona-lock ransomware (Virus Removal Guide) - Bonus: Decryption Steps
Corona-lock virus Removal Guide
What is Corona-lock ransomware?
Corona-lock is yet another ransomware campaign using the disease as a lure

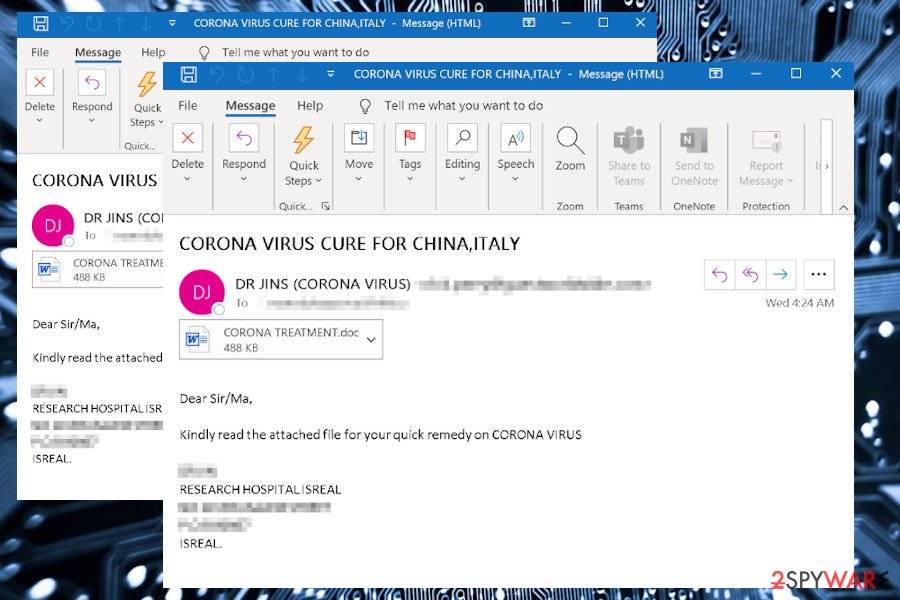
Corona-lock ransomware is a cryptovirus that misuses the COVID-19 pandemic to trick people into opening malicious ransomware payload and lock personal people's files. It has been found spreading via spam emails[1] called “Corona virus cure for China, Italy.” The email contains a CORONA TREATMENT.doc file, which is infected with the malicious ransomware payload.
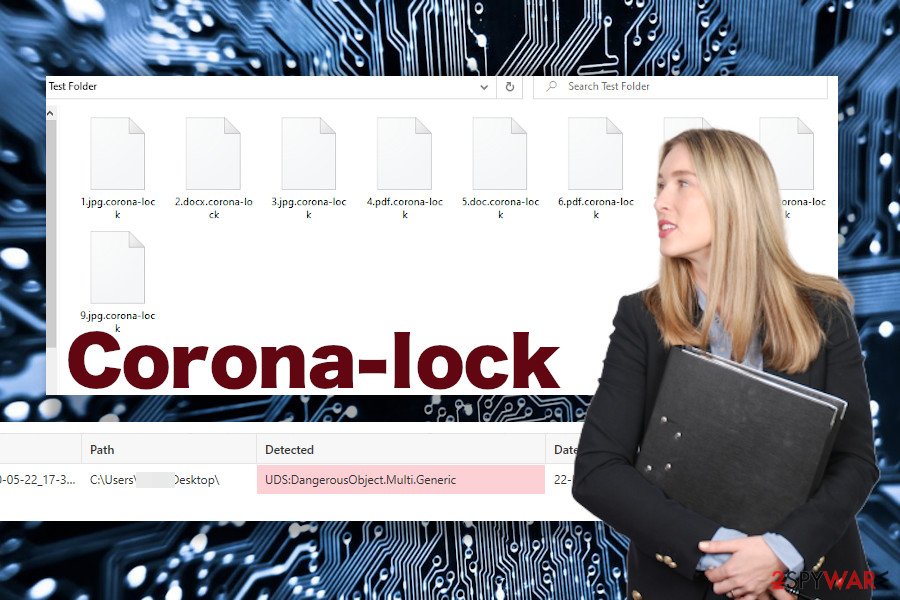
Upon the infiltration, the virus roots into the OS by changing Windows Registry entries and injecting malicious executables among boot up files. After that, the system is forced to restart leading to a complete lock of personal files. All non-system data gets encrypted by the .corona-lock! file extension. Usually, victims cannot fully understand what happened until the README_LOCK.txt note gets placed on the desktop and other folders.
This ransomware is also known as the CovidWorldCry virus. Both variants are not decryptable. At least not yet. The criminals behind this threat programmed this threat to run a combination of ChaCha and AES encryption algorithm, which is a tough nut to crack for cybersecurity experts.
| Name of the virus | Corona-lock |
| Also known as | CovidWorldCry ransomware, CoronaLock ransomware, BigLock ransomware |
| Ransom note | README_LOCK.txt or !!!READ_ME!!!.TXT |
| Encryption model | ChaCha + AES |
| Contacts | Criminals provide the support@covidworldcry.com email |
| Payload | Usually, people are represented with malicious spam emails that contain CORONA TREATMENT.doc file with a hidden 2020-05-22_17-36-19.exe payload |
| File marker | .corona-lock or .biglock file markers |
| Distribution | The virus was spread via Coronavirus-related spam email messages. Rig exploit kit, rogue software installers, and cracks can also be used for its distribution |
| Removal | If ransomware infected the machine, the only way to delete it is to restart the machine into Safe Mode with Networking (a guide below explains how to to that) and then run a full system scan with a professional AV engine. |
| Data recovery | There's no official decryptor for this threat. However, it's advisable to backup encrypted files and send the samples to cybersecurity experts for analysis. |
| Windows recovery | Upon ransomware elimination, recover the system using FortectIntego repair tool |
The malware is a new strain that does not seem to be connected to previous malware campaigns. It can only can be attributed to the COVID-19 campaign viruses[2] alongside Cov19, Coronavirus ransomware, Dharma, Maze, REvil, CovidLock, and many others. Although it's one of the ransomware-type viruses that take advantage of the Rig exploit kits, the most victims are caught on the hook by reliable-looking spam emails that contain the CORONA TREATMENT.doc file.
This CORONA TREATMENT.doc spam attachment disguises the malicious 2020-05-22_17-36-19.exe file, which is a unique ransomware payload. Once launched, the creates the following entries:
- %APPDATA%\key.file
- %HOMEPATH%\desktop\readme_lock.txt
- D:\install.log.corona-lock
- :\000814251_video_01.avi.corona-lock
- and others.
Moreover, the the virus creates malicious processes under names %WINDIR%\syswow64\vssadmin.exe, \conhost.exe, \dllhost.exe, \vssvc.exe, and %WINDIR%\syswow64\wbem\wmic.exe, which lock AV engines and increase ransomware persistence.
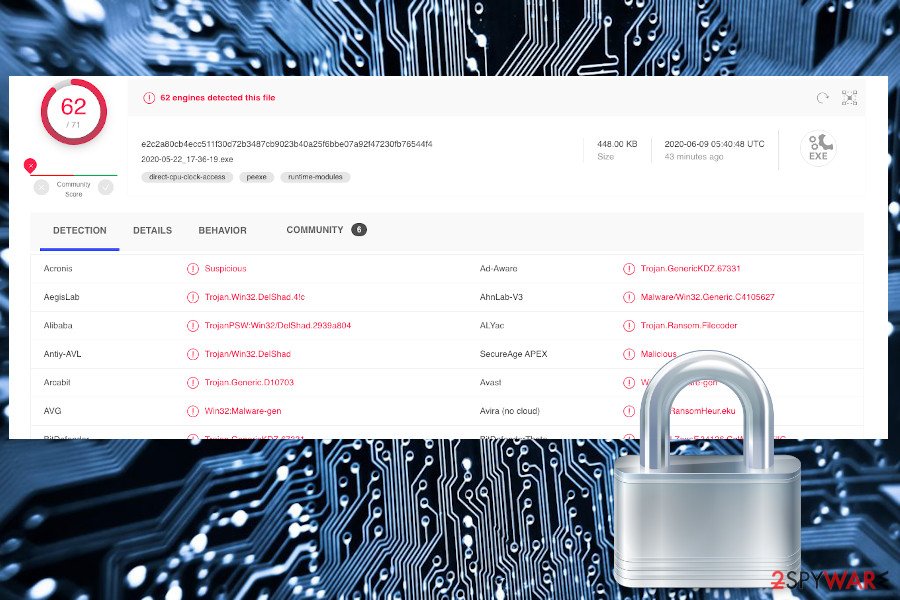
According to the VirusTotal analysis[3], the virus' executable can be detected and quarantined by 61 security tools out of 71. The most common detections are the following:
- Ransom:Win32/Coronalock.DEA!MTB (Windows Defender)
- Win32:Malware-gen (AVG)
- Trojan.GenericKDZ.67331 (BitDefender)
- Trojan.TR/AD.RansomHeur.eku (F-Secure)
- Trojan.Win32.DelShad.dfc (Kaspersky)
- Win32:Malware-gen (Avast)
- A Variant Of Win32/Kryptik.HDOJ (ESET-NOD32), etc.
All activities initiated by ransomware are extremely malicious. It roots into the OS, compromises %AppData%, %Temp%, and entries in other directories, eliminates Shadow Volume copies, terminates core processes, and starts alternative ones, etc. All performance leads to one goal – complete restriction from personal files.
Once the files are encoded by .corona-lock file extension, the ransomware generates a note README_LOCK.txt or !!!READ_ME!!!.TXT, which contains a unique ID number, which is bound to a personal file decryption key stored by criminals. to get the key, victims have to write an email to support@covidworldcry.com and pay the criminals a ransom payment.
YOUR FILES WERE ENCRYPTED
AND MARKED BY EXTENSION .corona-lock—
DON'T WORRY! YOUR FILES ARE SAFE! ONLY MODIFIED :: ChaCha + AES
WE STRONGLY RECOMMEND you NOT to use any Decryption Tools.
These tools can damage your data, making recover IMPOSSIBLE.
Also we recommend you not to contact data recovery companies.
They will just contact us, buy the key and sell it to you at a higher price.
If you want to decrypt your files, you have to get RSA private key.
—
To get RSA private key you have to contact us via email to:
—————————->> support@covidworldcry.com <<
and send us your id: >> 2374052812 <<
—
HOW to understand that we are NOT scammers?
You can ask SUPPORT for the TEST-decryption for ONE file!
—LIST OF ENCRYPTED FILES
If you are currently seeing such a message, we strongly recommend you to backup the encrypted files to alternative storage (hard drive, USB flash drive, cloud storage, etc.) and then restart the machine into Safe Mode with Networking. The safe mode disables malicious processes and allows launching the security software. To remove Corona-lock ransomware virus from the system thoroughly, we recommend using Malwarebytes, SpyHunter 5Combo Cleaner, or similar security software.
Upon successful malware removal, it's must to recover the Windows directories that the virus might have compromised. Distorted Windows Registries, disabled processes, and written/deleted files, modified attributes, and other performances can trigger Windows malfunctions and crashes. For this purpose, you can take advantage of the FortectIntego tool.
Encrypted file recovery options
Do not get confused by false claims on some unreliable sources that the removal of Coronal-lock ransomware using an anti-virus tool will recover personal files. Ransomware removal means that the AV engine quarantines the malicious ransomware processes and files.
The data that is encrypted using the ChaCha + AES encryption algorithm and exhibits the .corona-lock file extension will not be encrypted upon virus removal. Data encryption requires a specific decryption software that reverts the changes initiated by the cipher.
Virus creators offer their victims to buy the decryptor for a considerable amount of money and we are sure that a part of victims agree with the payment as they crave for unlocking important data. However, we do not recommend supporting criminals in any way.
Instead of that, experts from NoVirus.uk[4] advise to remove ransomware and then decrypt files using alternative methods. First of all, you can contact ransomware researchers and provide them with ransomware examples for testing. It's very likely that sooner or later they can develop a free decryptor.
While the decryptor is under development, you can try decrypting the files using third-party data recovery programs, System Restore, or Shadow Volume copies. You can find a comprehensive guide at the end of this article.
.biglock file extension indicates Coronalock virus infection
Corona-lock ransomware is also known as the CovidWorldCry virus. Both variants are equally dangerous. However, depending on the variant that infiltrated the machine, the diverse extension can be appended to personal files.
In many cases, people find their files encrypted by the .biglock file extension virus. Files that contain such a suffix cannot be opened, moved, deleted, or renamed. Unfortunately, automatically renamed personal files means only one thing – ransomware attack.
Beware that criminals seek to gain as much money as possible. Virus managers may demand you to pay a redemption that varies from $480 to $1500 depending on the amount of encrypted data.
As we have already pointed out, this ransomware cannot be decrypted for free. Thus, you can either pay the criminals or get rid of the virus from your machine and try data recovery methods provided by our security experts.
Coronavirus-themed email spam keeps flooding inboxes
During the worldwide Coronavirus pandemic, criminals launched thousands of disease-related spam campaigns, malware, and viruses. Unfortunately, millions of people were caught on the hook of intriguing news, disease prevention methods, charities, and other rogue email messages that were used by scammers to infect PCs with ransomware.
It's very important to raise people's consciousness, so we keep repeating that official and reliable organizations are sharing the information on the official website or other reliable sources. They are not sending emails with questionable attachments to random PC users unless they are registered or made their e-mails public.
However, the malspam campaign is not the only way to spread malware and ransomware viruses. Criminals can quite easily exploit software vulnerabilities, known as flaws. Hackers take advantage of the exploit kits to gain access to people's machines. This particular ransomware is known for exploiting Rig exploit kit, which allows hackers to inject the malicious payload to the targeted machines remotely. Therefore, it's crucial to update outdated software and patch reported vulnerabilities without a delay.
Therefore, people should be extremely careful with suspicious email attachments, avoid downloading pirated software, cracking software, visiting x-rated websites, or clicking on doubtful ads. Instead of that, take advantage of a reputable anti-virus suite, which features real-time protection and other additional security measures.
Corona-lock removal guide: learn how to eliminate the entire ransomware package thoroughly
Usually, people attempt to remove ransomware by simply launching the AV tool in a regular Windows mode. Unfortunately, such an attempt is usually unsuccessful because ransomware runs malicious processes that block security software.
If you are currently solving such a situation, you should perform Corona-lock removal while the machine is restarted into Safe Mode with Networking. You can find a full guide explaining how to do that down below.
Besides, it's very important to select a professional security software to eliminate the virus. Ransomware, in general, is an intricate piece of software, which may remain in the disguise of Windows system files and re-attack the machine upon elimination if a single malicious entry is left intact. Our recommended programs are SpyHunter 5Combo Cleaner and Malwarebytes, but if you have another preferable security tool, you are free to use it, except make sure it's fully up-to-date.
Getting rid of Corona-lock virus. Follow these steps
Important steps to take before you begin malware removal
File encryption and ransomware infection are two independent processes (although the latter would not be possible without the former). However, it is important to understand that malware performs various changes within a Windows operating system, fundamentally changing the way it works.
IMPORTANT for those without backups! →
If you attempt to use security or recovery software immediately, you might permanently damage your files, and even a working decryptor then would not be able to save them.
Before you proceed with the removal instructions below, you should copy the encrypted files onto a separate medium, such as USB flash drive or SSD, and then disconnect them from your computer. Encrypted data does not hold any malicious code, so it is safe to transfer to other devices.
The instructions below might initially seem overwhelming and complicated, but they are not difficult to understand as long as you follow each step in the appropriate order. This comprehensive free guide will help you to handle the malware removal and data recovery process correctly.
If you have any questions, comments, or are having troubles with following the instructions, please do not hesitate to contact us via the Ask Us section.
IMPORTANT! →
It is vital to eliminate malware infection from the computer fully before starting the data recovery process, otherwise ransomware might re-encrypt retrieved files from backups repeatedly.
Isolate the infected computer
Some ransomware strains aim to infect not only one computer but hijack the entire network. As soon as one of the machines is infected, malware can spread via network and encrypt files everywhere else, including Network Attached Storage (NAS) devices. If your computer is connected to a network, it is important to isolate it to prevent re-infection after ransomware removal is complete.
The easiest way to disconnect a PC from everything is simply to plug out the ethernet cable. However, in the corporate environment, this might be extremely difficult to do (also would take a long time). The method below will disconnect from all the networks, including local and the internet, isolating each of the machines involved.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet

- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
If you are using some type of cloud storage you are connected to, you should disconnect from it immediately. It is also advisable to disconnect all the external devices, such as USB flash sticks, external HDDs, etc. Once the malware elimination process is finished, you can connect your computers to the network and internet, as explained above, but by pressing Enable instead.
Scan your system with anti-malware
If you are a victim of ransomware, you should employ anti-malware software for its removal. Some ransomware can self-destruct after the file encryption process is finished. Even in such cases, malware might leave various data-stealing modules or could operate in conjunction with other malicious programs on your device.
SpyHunter 5Combo Cleaner or Malwarebytes can detect and eliminate all ransomware-related files, additional modules, along with other viruses that could be hiding on your system. The security software is really easy to use and does not require any prior IT knowledge to succeed in the malware removal process.
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Find a working decryptor for your files
File encryption is a process that is similar to applying a password to a particular file or folder. However, from a technical point of view, encryption is fundamentally different due to its complexity. By using encryption, threat actors use a unique set of alphanumeric characters as a password that can not easily be deciphered if the process is performed correctly.
There are several algorithms that can be used to lock data (whether for good or bad reasons); for example, AES uses the symmetric method of encryption, meaning that the key used to lock and unlock files is the same. Unfortunately, it is only accessible to the attackers who hold it on a remote server – they ask for a payment in exchange for it. This simple principle is what allows ransomware authors to prosper in this illegal business.
While many high-profile ransomware strains such as Djvu or Dharma use immaculate encryption methods, there are plenty of failures that can be observed within the code of some novice malware developers. For example, the keys could be stored locally, which would allow users to regain access to their files without paying. In some cases, ransomware does not even encrypt files due to bugs, although victims might believe the opposite due to the ransom note that shows up right after the infection and data encryption is completed.
Therefore, regardless of which crypto-malware affects your files, you should try to find the relevant decryptor if such exists. Security researchers are in a constant battle against cybercriminals. In some cases, they manage to create a working decryption tool that would allow victims to recover files for free.
Once you have identified which ransomware you are affected by, you should check the following links for a decryptor:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

If you can't find a decryptor that works for you, you should try the alternative methods we list below. Additionally, it is worth mentioning that it sometimes takes years for a working decryption tool to be developed, so there are always hopes for the future.
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Corona-lock and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Joe Tidy. Google blocking 18m coronavirus scam emails every day. BBC News. Broadcast news.
- ^ Cisomag. Coronavirus-themed Malware and Ransomware Ramp Up. CisoMag. Publication features news.
- ^ 2020-05-22_17-36-19.exe. Virus Total. Free URL and file scanner.
- ^ Security and spyware news. NoVirus. Virus and spyware news.
