Cov19 ransomware (Virus Removal Guide) - Bonus: Decryption Steps
Cov19 virus Removal Guide
What is Cov19 ransomware?
Cov19 ransomware is a dangerous threat that can lock personal files and cause its victims significant financial losses

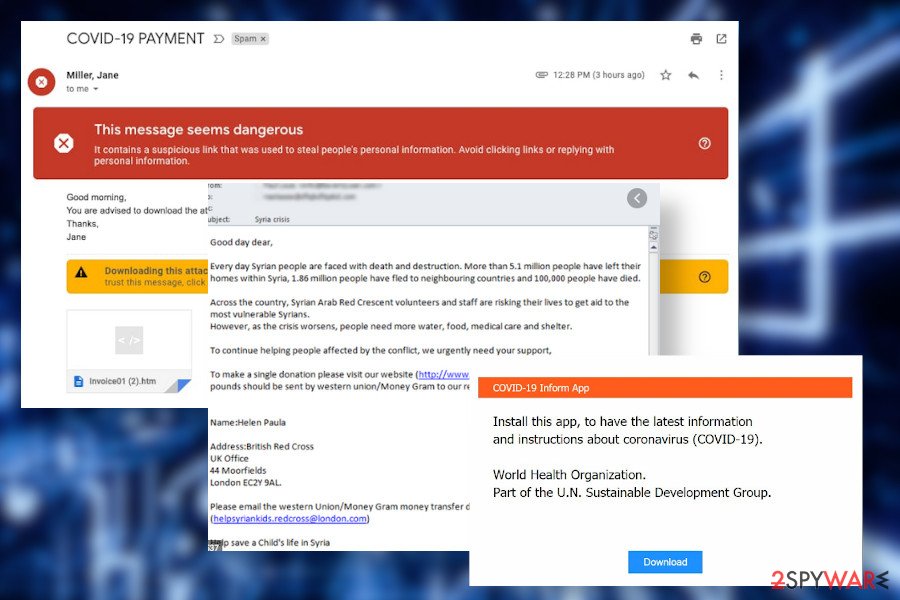
Cov19 ransomware is a dangerous file-encrypting cyber infection that is currently under an active contagion phase. Its developers misuse the name of the COVID-19 pandemic[1] that has resonated around the world in early 2020. The attackers trick people into downloading a malicious svchoster.exe file that serves as a downloader of the virus by with the help of phishing emails allegedly coming from WHO (World Health Organization) or CDC (Centers for Disease Control and Prevention), the COVID-19 Pandemic email and The Red Cross email.
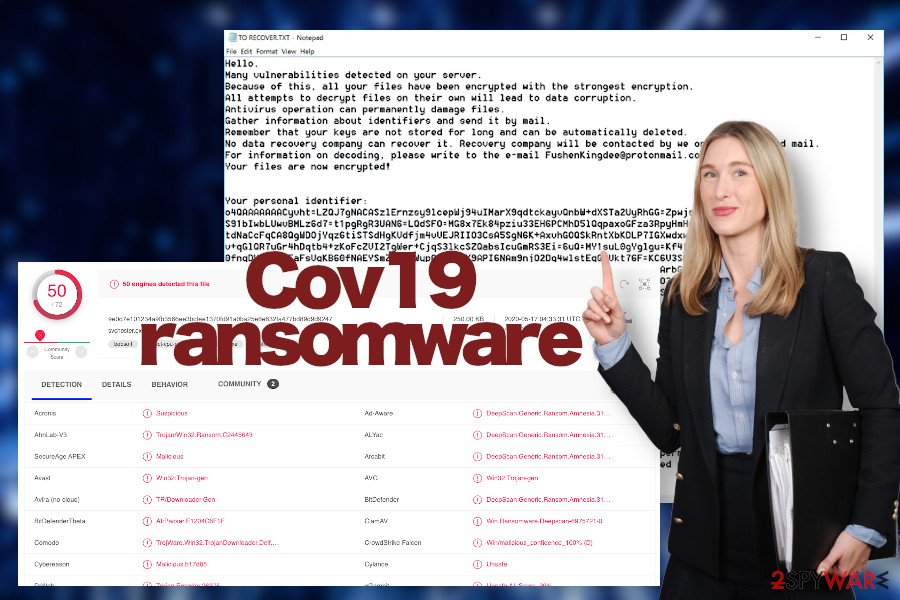
This encryption-based virus stems from the infamous Scarab ransomware family, which is very rich in the number of its members. The ransomware seeks to gain financial profit by encrypting the most popular file types (images, videos, photos, Microsoft Office documents, etc.) with a sophisticated encryption algorithm. The most obvious symptoms of this encryption-based malware are .cov19 extension appended to corrupted files and the TO RECOVER.TXT note positioned on Windows desktop.
| Summary | |
| Name | Cov19 |
| Geneology | This ransomware is a member of the infamous Scarab ransomware |
| International classification | Ransomware |
| Marker | .cov19 |
| Ransom note | TO RECOVER.TXT |
| Distribution | The primary source for this virus is malicious PDF, ZIP, DOC, DOCX, attachments of spam email messages impersonating organizations like WHO, RedCross, or Disease Control. Additionally, it may be disseminated via open RDPs, or launched as a secondary payload of trojans like Remcos, Orcus, or Gh0st. |
| Symptoms | Most of the non-system files corrupted. All icons get the homogenous shape and the file marked .cov19. The ransom note is presented on the desktop. Task Manager runs the svchoster.exe process. “Svchoster.exe application error” may pop-up randomly The system becomes sluggish, unresponsive, and may restart out of nowhere, etc. |
| Removal | A powerful AV tool is required. Windows Safe Mode with Networking has to be enabled for the scan |
| Damage | Missing Registry entries, files, and processes. Consequences – errors, BSODs, crashes, etc. Fix virus damage with the help of a repair tool. |
| Take advantage of the FortectIntego repair software. | |
Cov19 ransomware dropper is typically dispersed within malicious email spams that contain allegedly legitimate documents that are supposedly sent by the RedCross or governmental institutions providing instructions on how to behave during the Coronavirus pandemic to prevent infection. The obfuscated attachments are bundled with a malicious svchoster.exe file, which impersonates a legitimate Windows svchost.exe file. However, this file automatically downloads a ransomware payload and carries out activities (changes of the boot sequence, registry alterations, removal of core files, etc.) allowing a virus to root into the system.
According to researchers from NoVirus.uk[2], this mid-May 2020 Scarab ransomware campaign uses the .cov19 file marker and load the ransom note on the victim's Desktop. TO RECOVER.TXT file contains an overview of the attack, warnings related to the usage of security tools and recovery software, and asks victims to contact the specified e-mail address (FushenKingdee@protonmail.com).
Hello.
Many vulnerabilities detected on your server.
Because of this, all your files have been encrypted with the strongest encryption.
All attempts to decrypt files on their own will lead to data corruption.
Antivirus operation can permanently damage files.
Gather information about identifiers and send it by mail.
Remember that your keys are not stored for long and can be automatically deleted.
No data recovery company can recover it. Recovery company will be contacted by we on the indicated mail.
For information on decoding, please write to the e-mail FushenKingdee@protonmail.com
Your files are now encrypted!
The ransom message seems to be generated as a typical note used by its predecessors, so don't trust a word written on it and react immediately and remove Cov19 ransomware virus from your computer. Paying criminals is not a hundred-percent guarantee that the encrypted files will be restored. Even more, ransom payment definitely won't fix the damage that the virus initiated on the system. For this purpose, you will have to eradicate malicious entries with a reputable AV engine and then fully optimize the system with a repair tool like FortectIntego.
Anyway, before file recovery and system optimization processes, it's crucial to ensure a full Cov19 ransomware removal. In case of any malicious entries are left undelete, the virus may reappear and lock files again. According to the Virus Total[3] analysis, 50 AV programs out of 72 are capable of recognizing and decontamination the malicious files belonging to this ransomware. Typically, it is detected as:
- Trojan/Win32.Ransom.C2445643
- Win32:Trojan-gen
- TR/Downloader.Gen
- DeepScan:Generic.Ransom.Amnesia.318762
- Trojan.TR/Downloader.Gen
- HEUR:Trojan-Ransom.Win32.Generic
- DeepScan:Generic.Ransom.Amnesia.31876
- A Variant Of Win32/Filecoder.FS
- Ransom-Scarab!AA87BE1B17D8, etc.
The problem is that the malicious Cov19 virus downloader is not the only entry that has to be removed. This infection runs a whole package of malicious processes and is usually protected by helper objects. Not only they help the virus remain persistent but also block AV programs from running.
In this case, the Cov19 ransomware removal can become a tough nut to crack. To solve this problem, try restarting Windows into Safe Mode (if you don't know how to do that, please find instructions at the end of this post). Then initiate a deep system scan with reputable AV programs, for example, SpyHunter 5Combo Cleaner or Malwarebytes.
Sophisticated email messages with malicious attachments remain the main trickery used against unsuspecting users
Scamming campaigns are extremely actively used by hackers to initiate ransomware attacks. Legitimate looking email messages with subject lines about financial information, order confirmations, order tracking information, Coronavirus management methods, etc. spread with malicious attachments (macros) that drop ransomware downloader once opened.
Such and similar emails typically are well-crafted. Full content, e-mail signatures, subject line, reliable sender, in general, all reliable look makes thousands of people fall victims of file-encrypting viruses.
To protect your PC from being attacked by hackers, be very cautious when checking the email inbox. If you did not order anything, there's no need to open a message that claims to contain order confirmation or tracking number. In general, skip all emails that are not related to your activities, but if you see the need to check the received content, use a professional AV tool to scan the attachment.
Eliminate Cov19 ransomware using professional AV programs and ensure full system's repair afterward
Manual Cov19 ransomware removal is not possible due to many reasons. For example, it is not possible to know which processes running on the system are malicious because encryption-based viruses can replace legitimate system files and mimic their behavior. Besides, there may be tens of interconnected files and processes, which protect each other from removal.
To fully eliminate a virus such as Cov19 ransomware, it is important to understand the risks that it causes. Not only it can lead to permanent file loss, but it also causes a complete system's crash if it is not cured properly upon the removal of crypto-extortionist. A full recovery of Windows Registries is crucial and we strongly recommend taking advantage of the FortectIntego tool for that.
The best tool for you that we can recommend for Cov19 ransomware removal is a professional anti-malware software. In other words, a full package of the antivirus solution that exhibits a high detection rate. Unfortunately, removing the virus will not solve the problem with encrypted files. Thus, if you have fallen victim, here's what steps you should initiate:
- First of all, rely on tools like SpyHunter 5Combo Cleaner or Malwarebytes to get rid of the ransomware;
- Initiate a full scan with FortectIntego or similar tool to repair the needed parts of your PC;
- Use data backups of third-party data recovery software to encrypt files.
Getting rid of Cov19 virus. Follow these steps
Manual removal using Safe Mode
Reboot the machine in Safe Mode with Networking to get rid of Cov19 ransomware virus completely
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Cov19 using System Restore
System Restore is the feature that people can take advantage of after the system's crash or virus infection
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Cov19. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Cov19 from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Unfortunately, neither of Scarab ransomware versions can be decrypted. There's no official software for recovering files encrypted by .cov19 file extension, so victims can either use backups or try third-party data recovery programs.
If your files are encrypted by Cov19, you can use several methods to restore them:
Data Recovery Pro can help to retrieve a part of compromised files.
Make sure that the ransomware is fully removed before running a scan with it.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Cov19 ransomware;
- Restore them.
Windows Previous Version is useful in retrieving individual files
Although the recovery of all files damaged by Cov19 ransomware can be a tiresome process, it can be helpful in recovering the most valuable data.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer is the feature helpful for encoded files
Volume Shadow copies could be a perfect way out. However, most of the ransomware viruses enable a command that deletes these copies right after infiltration.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Unfortunately, there is no official Cov-19 decryption software
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Cov19 and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Adil Radoini. Cyber-crime during the COVID-19 Pandemic. Unicri. United Nations Interregional Crime and Justice Research Institute.
- ^ Security and Spyware news. NoVirus. Daily virus and spyware news.
- ^ svchoster.exe analysis. VirusTotal. Free file and URL scanner.







