ArchiveOperation Mac virus (Free Guide)
ArchiveOperation Mac virus Removal Guide
What is ArchiveOperation Mac virus?
ArchiveOperation is a Mac virus that can endanger your online privacy
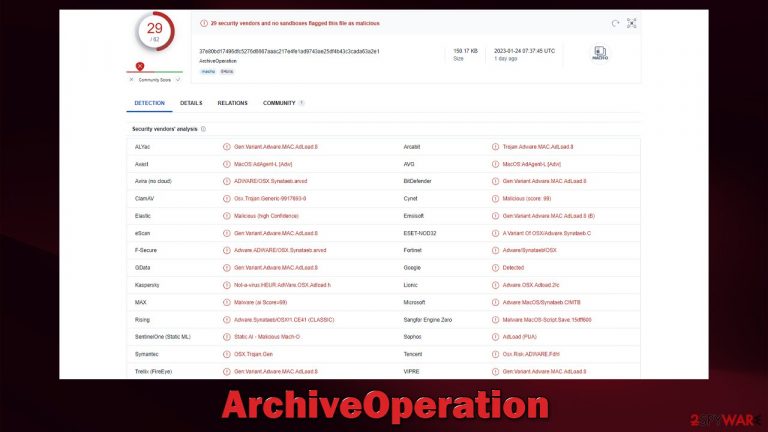
ArchiveOperation is a type of malware that stems from a specific strain of adware known as Adload, which is specifically designed to target Mac computers. It is known to spread through a variety of methods, including fake Flash Player updates and the installation of illegal software.
Once the malware is installed on a device, it can display unwanted ads, change browser settings such as the homepage, redirect the browser to unwanted websites, slow down the device's performance, and steal personal information, including login credentials, financial information, and browsing history. It can install additional versions of itself, which makes it harder to remove. It also installs special profile and other items on the system, which make its removal even more difficult.
In this article, we will explain more about how the ArchiveOperation virus operates, how to avoid its infiltration and how to remove it properly to avoid dangerous consequences of malware infections on a Mac machine.
| Name | ArchiveOperation |
| Type | Mac virus, adware, browser hijacker |
| Malware family | Adload |
| Distribution | Pirated software installers, fake Flash Player updates, misleading ads |
| Symptoms | A suspicious browser extension installed on the web browser; search and browsing settings altered to another provider; new profiles and other elements created on the accounts; increased number of ads and redirects |
| Removal | The easiest way to remove Mac malware is to perform a full system scan with SpyHunter 5Combo Cleaner security software. We also provide a manual guide below |
| System optimization | After you terminate the infection with all its associated components, we recommend you also scan your machine with FortectIntego for the best results |
More about the Adload malware family
It is not surprising that Mac malware is on the rise as more people are purchasing Apple products. However, many Mac users still believe that their devices are not vulnerable to malware, despite evidence to the contrary. Security researchers have consistently shown that macOS is also a target for cybercriminals, and users should be aware of this.
Adload is one example of a Mac malware strain that emerged in 2017, and since then, many variations have been released by the unknown cybercriminals behind it. These versions of the virus often spread through pirated software installers, and fake Flash Player updates are also a common method of distribution.
According to security research, this virus strain is distributed in a similar way to other prominent Mac malware, such as the Shlayer Trojan or Bundlore. A few of the most recent versions of Adload include ExpandedList, LifeProxy, and WebAge.
To reduce the risk of infection, it is recommended to avoid illegal software distribution websites. Additionally, it's important to note that Adobe has discontinued Flash player, so any requests to install it are fake and likely to result in malware infection.

ArchiveOperation virus removal
Adload variants are much trickier to erase than traditional applications, thanks to their uncomplicated yet effective techniques. For example, they might be disabled in the browser and impossible to remove without additional methods. The virus abuses AppleScript's integrated feature so that Gatekeeper – Mac's native security system – can't delete it.
Therefore, users may try to delete ArchiveOperation from their devices but will soon see it reappear again. To end this cycle of reinstallation and reinfection, a complete removal needs to be done – either with the help of security software or through an in-depth manual method which is given below. We highly suggest using SpyHunter 5Combo Cleaner or Malwarebytes instead of going for the manual option, as there could be files remaining after elimination that can cause malware returns.
Regardless of which removal option you choose, we strongly advise you to check the browser cleaning section, as it is vital to ensure one's privacy.
Eliminate the main app and its components
To shut down any malware-related processes, the first step is to open up your Activity Monitor. From there, you can easily terminate them as outlined below:
- Open Applications folder
- Select Utilities
- Double-click Activity Monitor
- Here, look for suspicious processes related to adware and use the Force Quit command to shut them down
- Go back to the Applications folder
- Find the malicious app in the list and move it to Trash.
Upon infiltrating your system, the virus may set up new User profiles and Login items to remain persistent. This could be why you can't seem to rid yourself of the app or extension despite attempts.
- Go to Preferences and select Accounts
- Click Login items and delete everything suspicious
- Next, pick System Preferences > Users & Groups
- Find Profiles and remove unwanted profiles from the list.
Finally, it is important to eliminate any remaining files from the malware. PLIST files, also known as “property list” files, are small configuration files that contain user settings and information about specific applications. To fully remove the virus, it is necessary to locate the associated PLIST files and delete them.
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Get rid of the extension and clear web browsers from trackers
Adload versions are a severe breach of privacy, as they manipulate the system permissions to enable a malicious extension to collect large amounts of personal information and display intrusive ads. In addition, it can cause unwanted redirects, which can be extremely frustrating to deal with.
To ensure that the ArchiveOperation virus is eliminated, it is vital to remove everything related to it on the browser, starting with the extension:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Passive data tracking can also be performed with the help of cookies and other trackers, which are stored locally. Therefore, we recommend cleaning web browsers promptly after malware is terminated. You can either use the manual steps or employ the FortectIntego cleaning tool for this purpose.
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

In some cases, resetting the browser is the best choice once all adware is deleted from the device:
- Click Safari > Preferences…
- Go to the Advanced tab.
- Tick the Show Develop menu in the menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

If you are using Google Chrome or Mozilla Firefox, you will find the step-by-step instructions below.
Getting rid of ArchiveOperation Mac virus. Follow these steps
Remove from Google Chrome
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Remove from Mozilla Firefox (FF)
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Delete from macOS
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
