CoolADSBlockSearch browser hijacker (Free Guide)
CoolADSBlockSearch browser hijacker Removal Guide
What is CoolADSBlockSearch browser hijacker?
CoolADSBlockSearch is a potentially unwanted browser extension that takes over your browsing sessions
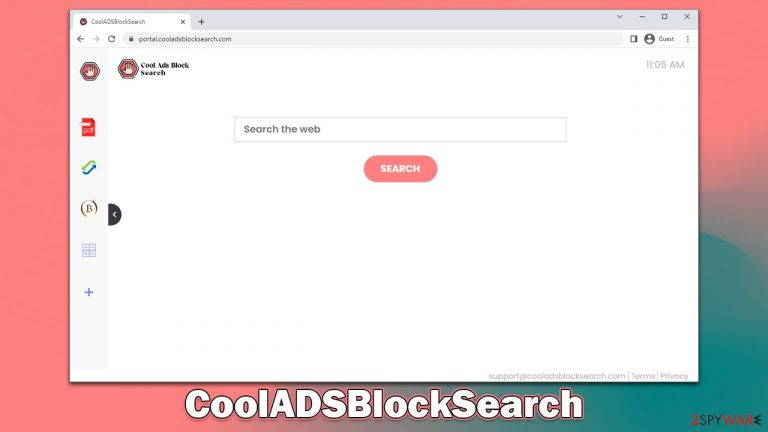
CoolADSBlockSearch is a browser-hijacking application that implies blocking ads, but there's nothing true about this statement. Not only does the app not provide any of its advertised features, but it also purposefully changes default preferences upon installation, which result in a negative user experience.
For example, it is often installed without users' knowledge when they download freeware[1] from less-than-reputable sources. It may also be promoted via fake updates and other misleading ads, which trick people into installing it.
Once the CoolADSBlockSearch browser hijacker enters the system, it immediately takes over Google Chrome or another used browser – it changes the homepage/new tab to cooladsblocksearch.com and starts redirecting to alternative search providers (Yahoo, Bing, searchlee.com, or nearbyme.io, which depends on your location). The top of the results is always filled with ads, which serve as the main monetization method for app creators.
If you have found that a potentially unwanted browser extension has hijacked your browser, take your time to properly get rid of it to secure your privacy and computer security. Below we provide all the details needed for that.
| Name | CoolADSBlockSearch |
| Type | Browser hijacker, potentially unwanted browser extension |
| Distribution | Bundled software, third-party websites, fake ads |
| Symptoms |
|
| Risks | Data tracking from various third parties, exposure to malicious ads, redirects to phishing sites |
| Removal | To remove the unwanted browser extension, you should access your browser's settings. Checking the system with SpyHunter 5Combo Cleaner security software can also ensure that there is no adware or malware running in the background |
| Other tips | After removing all potentially unwanted applications, we recommend you employ the FortectIntego utility to clean your web browsers and repair any damaged system files |
How hijackers spread
Some people don't install CoolADSBlockSearch on purpose, and they may even believe it just appeared out of nowhere. This is not the case, however, because browser hijackers are frequently installed by users without them intending to do so. PUPs do not spread in a manner as malware (such as ransomware[2] or trojans) does and are always installed by users, even though they are usually tricked into doing so.
Software bundling allows websites to deliver multiple applications at once, often without the user's knowledge or consent. This is a common practice among third-party websites as it brings in money from pay-per-install[3] schemes. However, this can result in users having unwanted and potentially harmful programs on their systems.
To avoid being victims of this rather unfair tactic, we recommend being extremely careful when installing new apps from third-party sources. For example, you should always make sure you select Advanced settings instead of Recommended within the installation window, remove all the ticks from pre-ticked boxes, and watch out for misplaced buttons and fine print – these techniques are commonly used to fool people, especially those who are in a rush to get over with.
CoolADSBlockSearch hijacker family
The app stems from a broader family of browser hijackers, which is known for versions like UltraCouponSearch, YouPDFSearch, StreamTopSearch, and many others. In fact, all of these are practically identical and, despite their names, they do not differ in functionality, which means that an app with the name “coupon search” would not actually help you find coupons. Beyond a simple search box, there's nothing innovative or useful to be had, thanks to the hijacker.
Most browser hijackers are relatively useless when it comes to some type of improvement within the search function. They often claim that they can “speed up” or “improve” searches, which couldn't be further from the truth. The alleged improvements are nothing more than ads that are inserted at the top of the search results, some of which may also lead people to websites that advertise other potentially unwanted programs.
Effective hijacker removal
We strongly advise you to scan your system with SpyHunter 5Combo Cleaner or Malwarebytes for malware before continuing with the removal instructions below. If you're not sure why the app is on your system or if you don't remember installing it, this is especially important. Browsing dangerous websites – like those that host illegal software or unlicensed streaming video – can expose your computer to malware without your knowledge.
As for the elimination of the extension, it does not differ from any other add-on installed on your browser. If you need help with the process, please check the instructions below:
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

MS Edge
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

MS Edge (legacy)
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Internet Explorer
- Open Internet Explorer, click on the Gear icon (IE menu) on the top-right corner of the browser
- Pick Manage Add-ons.
- You will see a Manage Add-ons window. Here, look for suspicious plugins. Click on these entries and select Disable.
You can protect your online privacy by regularly cleansing your browser caches, which is especially important after removing any potentially unwanted programs such as CoolADSBlockSearch. You can follow the directions below or use reliable optimization software FortectIntego that will not only clean your browser caches but also fix any damage caused by computer infections.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

MS Edge (legacy)
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Internet Explorer
- Press on the Gear icon and select Internet Options.
- Under Browsing history, click Delete…
- Select relevant fields and press Delete.
How to prevent from getting browser hijacker
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ What Is Freeware?. Lifewire. Tech News, Reviews, Help & How-Tos.
- ^ Ransomware. Imperva. Application and data protection.
- ^ What is Pay-Per-Install?. Codefuel. Monetization solutions for websites, apps, extensions and search engines.
