Crypt0L0cker virus (Removal Instructions) - 2017 update
Crypt0L0cker virus Removal Guide
What is Crypt0L0cker virus?
The activity of Crypt0L0cker virus
Crypt0L0cker ransomware is an infamous crypto malware [1], which can be found mentioned in various sources as Crypt0L0cker virus. Computer users should be aware of this virus and its distribution methods, because once it infects the computer, it is nearly impossible to repair the damage that it does to it. It is an updated version of TorrentLocker ransomware, and it hides under the name of one of the most dangerous computer viruses in the world – CryptoLocker. The difference is that the virus that we discuss about today has O’s replaced with zeros in its name [2]. It spreads as a Trojan horse [3] via email: its malicious executive file usually reaches computer users disguised as a secure document, for example, speeding ticket or invoice. The sole purpose of this PC threat is to infiltrate victim’s computer system and encrypt files stored in it. Crypt0L0cker malware scans all system folders and locates relevant data including music files, videos, photos, documents, and other types of files, and then encrypts them using a sophisticated encryption algorithm. Once the files are encrypted, the user cannot access them anymore.
The further activity of the virus
After the encryption process is done, this ransom virus drops DECRYPT_INSTRUCTIONS file on the computer, in .html and .txt formats. This file informs the user that files were encrypted by a virus and that the only way to get Cryptolocker decryption tool is to pay a ransom to cyber criminals. These crooks demand 2.2 Bitcoin, which is equal to approximately 983.27 USD. Unfortunately, we do not think that cyber criminals provide the key after users pay the ransom since users are looking for Crypt0L0cker file recovery solutions on various forums online. Therefore, we do not suggest paying the ransom, because you might lose a considerable amount of money alongside your files. Although computer experts are doing their best trying to find Crypt0L0cker decryptor, unfortunately, any specific tool hasn’t been discovered yet. We recommend you to remove this virus from your system without a hesitation since there is hardly any hope to recover your files (unless you have a backup). You can remove Crypt0L0cker with FortectIntego anti-spyware software.
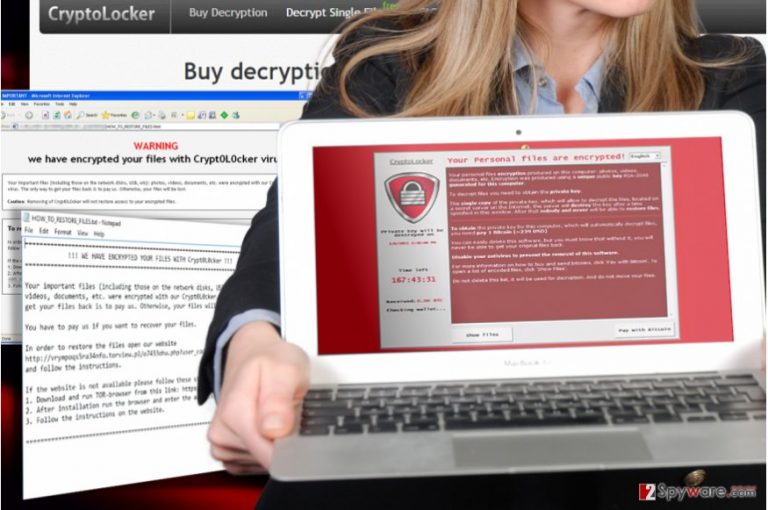
New version of Crypt0l0cker released in August 2016. How does it differ from the previous version?
A new variant of this Crypt0L0cker ransom virus has been spotted spreading on the world wide web, and this one seems to be targeting Italian-speaking computer users [4]. This version also encrypts victim’s data and demands a ransom; besides, it appends .enc file extension to encrypted record. Hence, a file which is named image.jpg will be renamed to image.jpg.enc. What is more, this new ransomware, unlike other viruses of its kind, leaves a ransom note that is named randomly (the name of the ransom note is individual for each victim). As a result, it might become a little complicated to identify the virus, since TrueCrypter and .CryptoHasYou viruses also append same file extensions to encrypted data. When it comes to this virus’ distribution methods, it is distributed via spam email campaigns. It appears that cybercriminals pretend to be employees of Italian energy organization named Enel, and send letters to victims with such attachment: ENEL_BOLLETA.ZIP. This name translates as Enel bill and includes a JS file Enel_Bolleta.js. If the victim extracts the archive and runs this JavaScript file, the ransomware starts the decryption process immediately.
What methods are used to distribute this virus?
Victims report that this ransomware spreads via misleading emails that present themselves as notifications from the government. As we have already mentioned, these emails can look like warnings for speeding and similar notifications [5]. We suggest you to inspect such letters carefully. If a message is full of typo or grammar mistakes, there is a huge possibility that it is fake. Also, you should always pay attention to the sender and, if you have any concerns and suspicions, do not open or download any files attached to such emails. Also, it is known that viruses like ransomware also spread via fake alerts. If a message has appeared on your computer out of nowhere and is filled with information that is too good to be true (for instance, “You have won an iPad,” or “You are the lucky visitor“), you should ignore it because clicking it can easily lead you to the infiltration of such virus like this one. Of course, it is hard to miss the fact that this threat has infiltrated your computer because it encrypts predetermined files in seconds.
If you have already received the threatening message from this virus stating that your files are encrypted, and if you cannot open your photos, music files or other relevant records and documents, it means that your computer was infected with this virus. We recommend you to initiate an immediate Crypt0L0cker removal without a delay. If you do not know how to do it, look at the guide given below.
The best way to remove Crypt0L0cker malware and decrypt your files:
There is only one anti Crypt0L0cker remedy – data backups. We strongly advise computer users to regularly create copies of important files and export them to an external storage device and keep such device unplugged from the computer. If you keep storing your files on such devices, you will be able to recover them in case a ransomware virus or another malicious computer threat slithers into your computer and damages them. In case you do not have backups, we recommend you to try these file recovery tools: R-Studio or Photorec, or you can give a try to this decryption tool. You can also look for a decryption solutions on this site.
Before you try to recover files that this malware has encrypted, you must exclude the malicious files related to this virus. You can use Crypt0L0cker removal instructions provided below, but we do not suggest trying to uninstall this virus manually unless you are a very experienced computer user. If you have never dealt with similar viruses before, we suggest you to assign this task to a powerful anti-malware software and remove Crypt0L0cker virus and related files automatically.
Getting rid of Crypt0L0cker virus. Follow these steps
Manual removal using Safe Mode
In case Crypt0L0cker attempts to block your antivirus from initiating the system scan and eliminating the infection from the computer, please be sure to follow the steps we provide in these virus decontamination instructions:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Crypt0L0cker using System Restore
Step-by-step instructions on how to decontaminate Crypt0L0cker and retrieve all your antivirus capacities are provided below. Make sure you follow them attentively and do not delete some important system files by accident.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Crypt0L0cker. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Crypt0L0cker from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Crypt0L0cker, you can use several methods to restore them:
Good news: you may be able to recover your files using Data Recovery Pro
Data Recovery Pro is a software that might help recover files encrypted by Crypt0L0cker if the decryption tools do not work. The instructions below will demonstrate how to use this tool to achieve best results.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Crypt0L0cker ransomware;
- Restore them.
Windows Previous Versions feature may be your answer to file recovery:
Windows Previous Versions feature only works if System Restore function has been enabled before Crypt0L0cker encrypted files on the computer. To use Windows Previous Versions recovery feature properly, make sure you follow the instructions here:
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Crypt0L0cker decrypter
You may try decrypting your files using the Crypt0L0cker decryption tool provided by Kaspersky.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Crypt0L0cker and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Cryptovirology. Wikipedia. The free encyclopedia.
- ^ Juan María Tellería. English and leetspeak. A step towards global nerdism. Repositori. Repositori Universitat Jaume I.
- ^ Robert Siciliano. What is a Trojan horse?. Mcafee. Antivirus blog .
- ^ Marco Ramilli. Recovering files from brand new Crypt0l0cker. MarcoRamilli. Hacking, malware evasions, penetration testing, targeted attacks, malware analysis and everything related to cyber security field..
- ^ Andra Zaharia. Analysis: How malware creators use spam to maximize their impact. Heimdal. Hemdal security blog.







