Medusabtc ransomware (virus) - Free Instructions
Medusabtc virus Removal Guide
What is Medusabtc ransomware?
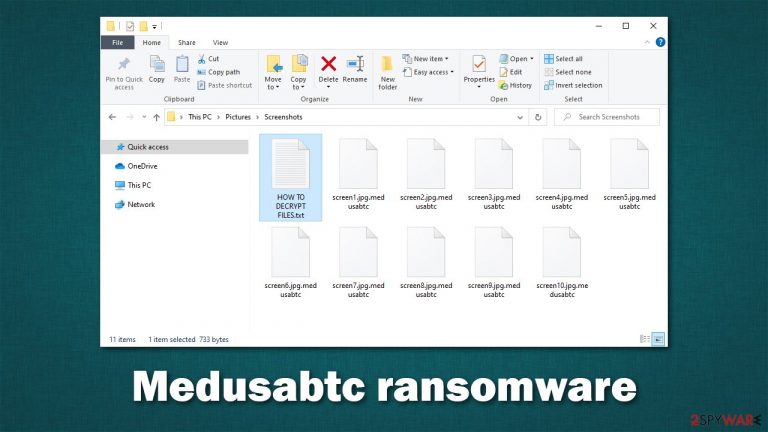
Medusabtc ransomware is a file-locking virus that delivers its ransom note in Portuguese
Ransomware is a devastating type of malware: it locks all pictures, videos, documents, and various kinds of other most common files and then asks victims to pay money for their return. The surge of ransomware infections has been drastic in the past years, and the number of attacks against home users and corporations is growing every year. Security experts have observed new strains emerging almost daily, while already established ones deliver new versions regularly.
Medusabtc virus comes from the family of Xorist, a ransomware family that was first introduced as early as 2012. Since then, we have seen multiple new variants emerging over time, including Dulgtv, Locks, Mcafee, ZaLtOn, and many others. It is evident that the attackers won't stop any time soon, and users should be aware of that.
Once installed on Windows, the malware uses a strong encryption algorithm such as TEA[1] to lock all personal files. During this process, they are stripped of their default icons and the extension .Medusabtc is appended. Victims then have to face reality and realize that their data is no longer usable. It is important to note that the files are not corrupted but locked behind a complex password generated to each user individually.
Of course, the attackers are unwilling to provide the decryption key for free and ask to pay up using Bitcoin. While it is unclear how much cybercriminals want, malware's previous versions are known to ask for approximately $600, although this can greatly vary from victim to victim. Regardless of this, they won't provide a decryptor for free.
Also, attackers provide contact emails for communication purposes – medusabtc@protonmail.com and btcpaynow@protonmail.com, which are meant to be used in order to negotiate the precise price. This information can be found in a ransom note HOW TO DECRYPT FILES.txt, generated on the dewhenoon as the encryption process is finished. Also, a pop-up message titled “Error” immediately appears on the desktop to grab users' attention.
Both messages are written in Portuguese, which brings to the conclusion that this malware variant is likely to be targeted at users living in countries that use the language. However, since malware can use distribution techniques that could reach random targets, users who can't speak Portuguese might also be affected.
| Name | Medusabtc virus |
|---|---|
| Type | Ransomware, data locking malware, cryptovirus |
| Malware family | Xorist |
| File extension | .medusabtc is appended to each of the personal files |
| Ransom note | HOW TO DECRYPT FILES.txt and “Error” titled pop-up |
| Contact | medusabtc@protonmail.com or btcpaynow@protonmail.com |
| Ransom demand | Not provided, although the attackers have a set date that victims are encouraged to contact them for a decryptor |
| File Recovery | If no backups are available, recovering data is almost impossible. We recommend you try alternative methods, which we list below |
| ransomware removal | Before you attempt file recovery, you should remove malware with the help of powerful security software, such as SpyHunter 5Combo Cleaner |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with the FortectIntego repair tool |
The ransom note explained
There are many types of malware, each of which operates differently. For example, stealthier parasites such as backdoors or data-stealers are known to be particularly sneaky, as their main goal is to run in the background and perform whatever actions they were programmed for as long as possible without being noticed by the user.
However, ransomware is not the one to hide, at least not after it has done its deed and encrypted the files. It is true that people might get infected via malicious emails or software vulnerabilities, which result in stealthy infiltration. After malware does its job, it usually makes sure that the victims find out about the infection as soon as possible in order to increase the chances of ransom payment.
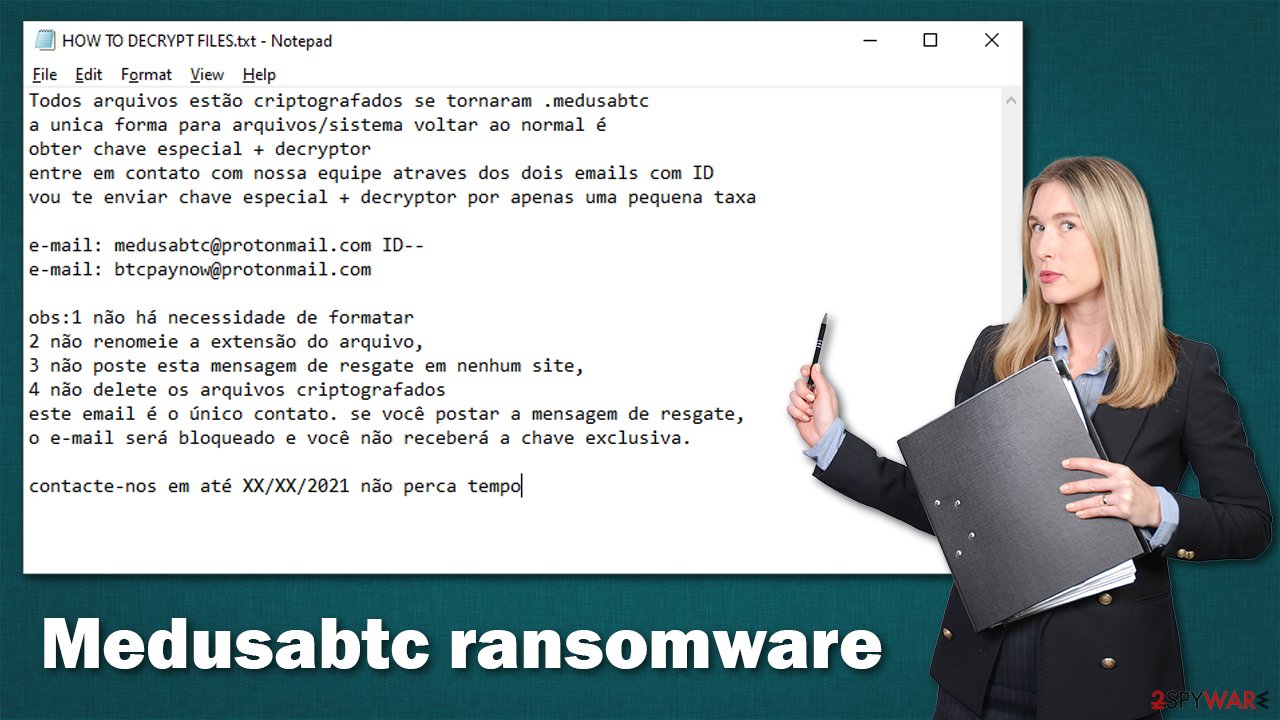
For that reason, the Medusabtc virus generates a ransom note and places it on the desktop, as well as into all the directories of locked files. As mentioned, the note is written in Portuguese:
Todos arquivos estão criptografados se tornaram .medusabtc
a unica forma para arquivos/sistema voltar ao normal é
obter chave especial + decryptor
entre em contato com nossa equipe atraves dos dois emails com ID
vou te enviar chave especial + decryptor por apenas uma pequena taxae-mail: medusabtc@protonmail.com ID–
e-mail: btcpaynow@protonmail.comobs:1 não há necessidade de formatar
2 não renomeie a extensão do arquivo,
3 não poste esta mensagem de resgate em nenhum site,
4 não delete os arquivos criptografados
este email é o único contato. se você postar a mensagem de resgate,
o e-mail será bloqueado e você não receberá a chave exclusiva.contacte-nos em até XX/XX/2021 não perca tempo
In short, the attackers say that none of the encrypted files should be modified and provide emails that should be used for contact. They also say that the message shouldn't be posted anywhere on the internet, as then the crooks would delete the decryption key and file recovery would be impossible. They also provide a date before the decryption key would allegedly be deleted permanently.
While some crooks tend to convince users with a somewhat friendly demeanor (for example, Djvu variants such as Vtua), plenty of malware authors use fear and panic as their main weapons – they try to intimidate people and make them avoid seeking help from experts.
However, you should avoid contacting the attackers, as you might never hear from them again, even if you pay the money. They might also ask you to pay more or send you a tool that does not work. Due to this, you might lose not only your files but also your money. Instead, please check below for the instructions you should follow.
Use security software to remove the infection
To prevent the ransomware from corrupting your data and remove the infection carefully, you should access Safe Mode and perform a full system scan with SpyHunter 5Combo Cleaner or Malwarebytes anti-malware. Before you do this, disconnect your computer from the internet – you can simply plug out the ethernet cable or disconnect your WiFi via a system tray.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.

Data recovery process
Most users who get infected with ransomware have never encountered it before, so they are not completely sure how it all works. Once people see that they are unable to open any files, they might straight out panic. While it is true that the encryption process is done securely, it does not mean that the files are corrupted.
At the same time, it is important to note that anti-malware would not restore the .medusabtc files into their previous state. This is because security software is simply not designed for that. There is a type of software that was made to recover lost files, although it might not always work for ransomware. Nonetheless, we recommend you try it.
1. Use recovery Software
Important: Before you proceed, make sure you make a backup of all the encrypted files, as they might get corrupted in the process
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

2. Find a decryptor
Free decryptors are also sometimes created by security researchers. For that to happen, there needs to be some type of flaw within malware's encryption method or the servers belonging to the attackers might be seized. There is no guarantee that a decryption tool for this virus version will be ever created but we recommend visiting the following websites:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors
Unfortunately, there is no way to confirm that alternative decryption solutions will work for you, as they depend on many factors.
Repair system files
Ransomware can negatively impact Windows system files, damaging them. New ransomware strains are more prone to bugs due to hackers' lack of inexperience, so it can mess up your computer really quickly. Unfortunately, security software cannot fix damaged system components, which might later result in system crashes, errors, and other issues. Therefore, we strongly recommend you run a PC repair software after the infection to remediate Windows and avoid the reinstallation of the OS.
- Download FortectIntego
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

Ways to avoid ransomware infections
Xorist ransomware has been around for many years, and that there have been different methods that it was distributed. Most of the time, cybercriminals rely on methods that are proven to be successful, although innovations, such as fileless infections that occur in the memory,[2] are also practiced in some cases.
Here are a few tips from security researchers[3] that should help you avoid being infected in the future and negate ransomware effects:
- Backup your personal files;
- Use SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable software at all times – make sure it is updated as necessary;
- Don't ignore warnings from security software and don't assume it's a false positive;
- Never download software cracks or pirated programs from illegal websites;
- Update all software, including your operating system, as soon as the updates are available;
- Use strong passwords for all your accounts and never reuse them;
- Use official sources to download software.
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Tiny Encryption Algorithm. Wikipedia. The free encyclopedia.
- ^ Fileless threats. Microsoft. Docs.
- ^ Dieviren. Dieviren. Cybersecurity news and malware insights.
