Mole ransomware / virus (Virus Removal Guide) - updated Jul 2017
Mole virus Removal Guide
What is Mole ransomware virus?
Evolution of Mole ransomware
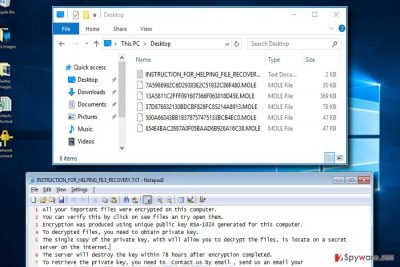
Mole virus functions as a ransomware which spreads via malicious spam emails disguised as USPS delivery problems.[1] The virus adds .mole file extensions to files it corrupts and drops INSTRUCTION_FOR_HELPING_FILE_RECOVERY.TXT, which is the ransom note. So far, the criminals have released three versions of this virus – Mole, Mole00, Mole01, Mole02 and Mole03 ransomware.
Researchers found connections with CryptoShield virus, and believe that it’s another piece of malware belonging to the CryptoMix family.
The malware is programmed to encrypt files using an RSA-1024 encryption key, appending .mole file extension and demanding to pay the ransom. Indeed, its behavior barely differs from other file-encrypting viruses. This cyber infection is known to eliminate Shadow Volume Copies; so it prevents victims from recovering data using these data copies.
However, there is some good news – victims of the initial ransomware version can now decrypt files encoded by Mole crypto-malware. You can find its download link in the data recovery instructions provided below the article. In case you got attacked by an updated version of the crypto-malware[2], you can use data backups[3].
If the virus has already inflicted damage, do not consider paying the ransom as there are few chances of recovery. Though the decrypter was finally released, IT experts have found a new version which appends .mole00 file extension to the files.
Furthermore, it disguises under Oren Music Panel executable. It is suspected that the malware might be distributed via several distribution channels, including exploit kits and spam emails. Mole removal might be a better decision. Attempts to obtain decryption software from the cyber criminals might end up with money loss and further cyber infections[4] Thus, we recommend employing FortectIntego or Malwarebytes.
The virus starts its malicious task as soon as a person clicks on a link provided in the infected email. After clicking on it, people are redirected to the fraudulent MS Word Online site which informs that document cannot be opened in the browser and users need to download and install the latest plugin.
Probably, you can get a feeling that this button installs a payload on the system. According to the research, Mole virus is executed either from pluginoffice.exe or plugin-office.exe file from doc-14-8g-docs.googleusercontent.com. When malware executable is dropped and activated on the system, it shows a fake Display Color Calibration alert that informs about an inability to turn off Windows calibration management.
The purpose of this fake error message is to force victims to click on “OK” button. This button is designed to start ransomware execution processes. Then, the virus starts data encryption procedure, and once it's over the virus drops INSTRUCTION_FOR_HELPING_FILE_RECOVERY.TXT file on the desktop and each folder that includes crypted files.
This file is a ransom note where victims are informed that they have 78 hours to contact cyber criminals and learn how to obtain the decryption key. However, sending the unique ID number to oceanm@engineer.com and oceanm@india.com emails is not recommended.
We can assure that crooks will demand to transfer few Bitcoins, but you may not be satisfied with this purchase. You may never receive a decryptor, or it might be not working properly, or it might be infected. It’s important to remove Mole from the device if you want to continue using your computer safely. Hopefully, alternative data recovery methods will help you to recover at least some of the corrupted files until the official decryptor is released.
Update June 2017: Victims whose computers were affected by this notorious ransomware virus no longer need to sorrow for lost data because if you haven't deleted the corrupted files, you can decrypt them now for free. Researchers from CERT Polska[5] reveal that they decided to take a look at a sample of this crypto-ransomware after one of the victims contacted them.
It turns out, they succeeded to perform a thorough analysis of the ransomware and also initiated a reverse-malware process. As a consequence, Mole decryptor was created. So if you were wondering whether to pay or not to pay the ransom, you can stop hesitating already and download the decryption tool to restore corrupted files.
We already mentioned this, but the ransomware removal must be performed before attempting to use a decryptor. You can find the link to download the decrypter in data recovery section below.
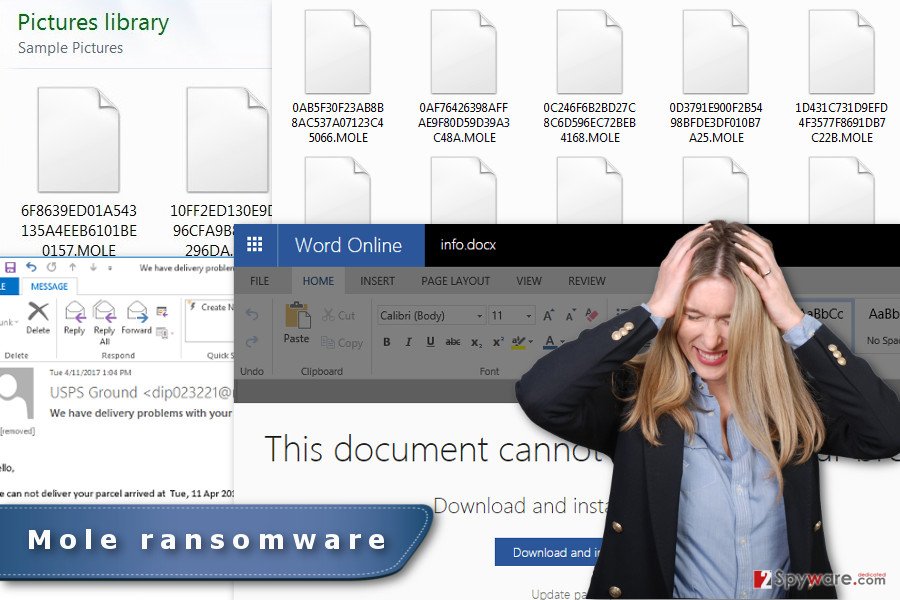
Versions of Mole ransomware
Mole00 ransomware virus. On July 4th, 2017, a new variant of Mole emerges. This time, the virus uses .MOLE00 extension to mark the encrypted files. After encrypting the data, the malicious program creates _HELP_INSTRUCTION.TXT file and saves it to every computer location that contains at least some corrupted files. The ransom note doesn't provide a particular ransom price but suggests visiting Mole00-02 payment website that asks paying 1 BTC to receive a data recovery software.
The ransomware was mainly distributed via email – scammers used USPS-themed spam campaign to trick unsuspecting victims into installing a malicious plug-in to view the attached message's content. The ransomware is highly dangerous, and so far there are no tools that could recover Mole00 file extension files for free.
Mole01 ransomware virus. Mole01 ransomware emerged for a short period but was quickly replaced by Mole02 ransomware version. The 01 version used _HELP_INSTRUCTION.TXT to provide instructions for victims. It also points to a dark web site accessible via Tor browser and also demands 1 BTC as a ransom.
Unfortunately, ransomware decryptors available today are not powerful enough to decrypt .mole01 file extension files. To restore encrypted files, we suggest using data backup or any data copies stored in email, online data storage accounts, and other places. Before you attempt to recover some files, remove Mole01 virus first.
Mole02 ransomware virus. MOLE02 version emerged on July 08, 2017. The virus completely corrupts the original file name and adds .MOLE02 file extension to it. The virus scans the entire computer system and corrupts all of the files with extensions from its target list. Following that, the virus creates and saves the _HELP_INSTRUCTION.TXT file as a ransom note.
The ransom note holds instructions on how to access the secret website with instructions on how to recover victim's data. The payment website suggests buying the “private key” for one Bitcoin. The victim has to enter one's victim ID and personal email address after transferring the ransom to criminals' Bitcoin address. However, a decrypter for MOLE02 is available, so we ask you not to pay the ransom!
Mole03 ransomware virus. Mole03 ransomware emerges on July 23. Reportedly, actors behind EiTest campaign distribute the virus via “The “HoeflerText” wasn't found” pop-ups. In other words, ransomware authors compromise legitimate websites and make them display the malicious pop-up.
Once the victim visits an infected site, the malicious script checks if the victim is using Google Chrome. If yes, it suggests installing a font pack that contains malware. If the victim uses Internet Explorer, the website automatically redirects the victim to a tech support scam site.
MOLE03 virus also uses _HELP_INSTRUCTION.TXT to send a message to the victim. It also points to the same payment website that demands 1 BTC.
There is no decryptor for Mole03 ransomware available. Therefore, if it locked your files, you will need to use alternative data recovery methods. Ideally, use a data backup. In case you never created it, try data recovery solutions listed below the article.
Techniques used to distribute the virus
Online security researcher Brad Duncan noted that Mole hijack occurs via malicious spam emails, which alert netizens about problems with package delivery. The subject line might include these names:
- Delivery problem, parcel USPS #number;
- New status of your USPS delivery code: #number;
- Our USPS courier can not contact you parcel # number;
- Please recheck your delivery address USPS parcel #number;
- Status of your USPS delivery ID: #number;
- We have delivery problems with your parcel # number.
However, there might be other email campaigns that distribute a malicious payload. Though, it is important to be careful and not to click on the links provided in the email that informs about delivery issues; especially, if you do not expect to receive any parcel. As we mentioned earlier, these emails have a link that leads to the fake Microsoft Office Online page which informs about a necessity to download a plugin to open the content.
This download button is infected and drops a malicious file on the system which generates another error message. Fake Display Color Calibration notification includes the “OK” button, which allows Mole ransomware to start damaging processes on the system as soon as it is clicked on.
Right after the project was launched, the developers of Mole malware decided to improve their distribution technique. The malware continues impersonating U.S. Postal Service emails. Besides disguising the malware in the attachment, now the developers have loaded more “malicious” content in the attached files.
They would hide Kovter (which now has its own crypto-malware – Kovter ransomware) and Miuref (alternatively known as Boaxxe) malware [6]. The entire malignant content is packaged into plugin.zip folder. Naturally, within this folder, plugin.js is placed as well.
In order for Mole crypto-malware to execute and paralyze the system, Nemucod trojan is also included. Interestingly, the gearheads also revived another malware – Nymaim ransomware [7]. It uses almost identical spam messages and includes the mentioned series of malware as well. On April 21, the crooks diverted from imitating USPS services to disguising under diverse lottery, parking notifications, and tax refund messages.
Remove Mole ransomware, get your files back
Having ransomware on the computer puts computer’s security and your privacy at risk, so remove Mole virus without a delay. This crypto-malware has already damaged your files; thus, you should not let it allow other viruses to enter the system and cause you more problems.[8] We suggest you eliminate
We suggest you eliminate virus from the system as soon as you find a ransom demanding message and find out that you cannot access your files. Elimination requires using professional antivirus software or malware removal tools. We suggest performing this task using FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes. We can assure that these programs can delete the virus entirely from the system.
However, Mole removal may not be smooth. File-encrypting viruses are often immune from security tools or prevent from installing them. However, you can disable the ransomware by rebooting the device to the Safe Mode with Networking.
This mode allows accessing, installing or updating security software and completing elimination. Once you remove the ransomware, try the decrypter created by CERT Polska.
Getting rid of Mole virus. Follow these steps
Manual removal using Safe Mode
If you cannot access antivirus program installed on your device or malware prevents you from installing it, please reboot your PC to the Safe Mode with Networking. Then you will be able to use security software and get rid of the virus.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Mole using System Restore
System Restore method also helps to disable the virus and access security software. We want to point out that you should scan the computer with updated malware removal program several times just to be sure that all malicious components are deleted from the system entirely.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Mole. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Mole from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.At the moment, data decryption tool is already available, although data backups can save your files, too. However, if you do not have it, try options presented below. One of the provided methods will restore your files.
If your files are encrypted by Mole, you can use several methods to restore them:
Data Recovery Pro – automatic solution to restore files encrypted by Mole
This professional tool is designed to restore deleted, corrupted and some of the encrypted files. Victims of the ransomware compliment this program for restoring a bunch of files. Though, we want to stress out that it's not a particular decryptor for this malware.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Mole ransomware;
- Restore them.
Try Windows Previous Versions feature to restoring individual files
If you need to recover few important documents, Windows Previous Versions feature might be helpful. It allows traveling back in computer's time and copying individual versions of the encrypted files. However, you can use this method under one condition – System Restore feature needed to be enabled before Mole virus attack.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Mole decryptor
Computer Emergency Response Team from Poland, known as CERT Polska, has reversed a sample of the malware and created a free decryptor that you can use. Download the Mole decryptor from their official page.
IMPORTANT. Victims of MOLE02 can decrypt their files using this decrypter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Mole and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Brad Duncan. Malspam on 2017-04-11 pushes yet another ransomware variant. Internet Storm Center. SANS ISC InfoSec Forums.
- ^ Matt Kingswood. Planning and practice can keep you prepared for a ransomware attack. ITProPortal. The latest business IT news, reviews, features and guides from around the world.
- ^ Backup the best defence for ransomware. IT-Online. Daily IT Industry News.
- ^ Peter Loshin. FBI ransomware alert: Don't pay; report, defend against attacks. TechTarget. The website includes tips, webcasts, and other advice in a variety of focused enterprise technology channels.
- ^ Jarosław Jedynak. Mole ransomware: analysis and decryptor. CERT Polska news. Malware Analysis, Results, Information Security News.
- ^ Bradley Barth. Mailmen and Mole-men: Spammers impersonated USPS, delivered Mole ransomware in evolving campaign. SCMedia. The cyber security source.
- ^ Brad Duncan . Mole Ransomware: How One Malicious Spam Campaign Quickly Increased Complexity and Changed Tactics. Paloalto Network. Next Generation Security Networks.
- ^ Mark Huffman. Why ransomware is about to get more dangerous. ConsumerAffairs. Consumer news, reviews, complaints, resources, safety recalls.





















