Scarab ransomware / virus (Virus Removal Guide) - Jun 2020 update
Scarab virus Removal Guide
What is Scarab ransomware virus?
Scarab ransomware is a dangerous file-locking virus that releases versions since 2017

Scarab is ransomware that employs sophisticated AES-256 and RSA-2048 algorithms to lock personal data on the targeted computer. As soon as it locks files, it marks them with a specific extension, such as .scarab, .langolier, and, later on, email-based appendixes like .btchelp@xmpp.jp or .Ssimpotashka@gmail.com. However, you can also become a victim of Scarab-Recovery, Scarab-Turkish, Scarab-Barracuda, .anonimus.mr@yahoo.com, and numerous other versions.
After the data locking process, the virus drops a ransom note demanding from $300 to $500 in exchange for the key that can unlock encrypted data. The name of dropped ransom notes also varies depending on the version – HOW TO RECOVER ENCRYPTED FILES.TXT, IF YOU WANT TO GET ALL YOUR FILES BACK, PLEASE READ THIS.TXT, and a few others, were used.
Crypto malware was spotted for the first time in June 2017 and had been reappearing with new versions since then. According to the latest research, it could be hailing from Animus ransomware developers, as it has been using the same email address for quite some time now. Sadly, only versions released prior to June 2018 can be decrypted, as new variants use an improved RSA encryption method.
According to ransomware researchers, ransomware is actively creating a collection of Scarab 2020. Since the beginning of this year, .rbs, .ncov, .DecSec, .worcservice@protonmail.ch, .inc_evilsi@protonmail.chand, .cov19, .bomba versions already emerged. The last one has been spotted in the middle of May leveraging the COVID-19 theme as a marker extension for encrypted files. At the moment, criminals are using the FushenKingdee@protonmail.com, madeinussr@protonmail.com, inc_evilsi@protonmail.ch, decoding_service@aol.com, worcservice@protonmail.ch, decoding_service@protonmail.com, logiteam@protonmail.com emails. Unfortunately, none of these versions can be decrypted. As pointed before, the available decryptor is capable of cracking variants launched before June 2018.
| SUMMARY | |
|---|---|
| Name | Scarab |
| Type | Ransomware |
| might be related to | Animu Locker |
| Versions | Scorpio, Scarab-Amnesia, Scarab-Crypto, Scarab-Please, Scarab-Decrypts, Scarab-Horsia, Scarab-Walker, Scarab-Osk, DiskDoktor, Fastrecovery@airmail.cc ransomware, Scarab-Leen ransomware, Scarab-Bomber, Scarab-Good, Oneway, Danger, BtcKING, Recme, JungleSec, Dan ransomware, Deep ransomware, Scarab-Recovery, Scarab-Turkish, Scarab-Barracuda, Scarab-Anonimus, Scarab-zzzzzzzz, Scarab-Saved |
| Danger level | High. At the moment, the virus is especially active and keeps appearing with new versions |
| Cryptography | AES-256; RSA-2048 |
| File extensions | .scarab, [email].scarab, [email].scorpio, [suupport@protonmail.com].scarab, .amnesia, .crypto, .please, .decrypts@airmail.cc, .red, .DD, .decryptsairmail.cc, .horsia@airmail.cc, .JohnnieWalker, .osk, .infovip@airmail.cc, .DiskDoctor, .fastrecovery@airmail.cc, .leen, .bomber, .recme, .oneway, .good., .deep, .BD.Recovery, .enter, .fast, .key, .[Firmabilgileri@bk.ru], .BARRACUDA, .anonimus.mr@yahoo.com, .zzzzzzzz, .{Help557@cock.li}.exe, .btchelp@xmpp.jp, .Ssimpotashka@gmail.com, .rbs, .ncov, .cov19, .DecSec, .worcservice @ protonmail.ch, .inc_evilsi @ protonmail.ch, .inchin, .bomba, .saved, .save |
| Related files |
IF_YOU_WANT_TO_GET_ALL_YOUR_FILES_BACK_ PLEASE_READ_THIS.txt; HOW TO RECOVER ENCRYPTED FILES.TXT; TO RECOVER ENCRYPTED FILES-decrypts@airmail.cc.TXT; HOW TO DECRYPT WALKER INFO.txt; HOW TO RECOVER ENCRYPTED FILES-infovip@airmail.cc.TXT; HOW TO RECOVER ENCRYPTED FILES-fastrecovery@airmail.cc.TXT; Recover files-xmail@cock.li.TXT; INSTRUCTIONS FOR RESTORING FILES.TXT, HOW TO RECOVER – btchelp@xmpp.jp ENCRYPTED FILES.TXT, TO RECOVER.TXT |
| Language translated | English, Russian, Turkish |
| Distribution | Necurs botnet, malicious email attachments, fake Java or Adobe Flash Player updates, corrupted remote desktop apps |
| Decryption | Dr. Web announced that some of the files encrypted by the virus can be decrypted. Users should send an email to emte@adc-soft.com with few examples of affected data together with the ransom note |
| ElIMINATION | Manual removal is not possible. To get rid of ransomware and its variants, download a reputable anti-malware and run a full system scan |
| System fix | Ransomware is a complex computer infection, and it can negatively impact its performance even after it is eliminated. As a result, users might experience crashes, lags, and other stability issues. To remediate Windows and avoid its reinstallation, run a scan with repair software FortectIntego |
This ransomware[1] is not an ordinary crypto-virus – it was found to use Necurs botnet[2] to spread around. Having in mind that it is the largest spam botnet, the possibility to get infected with Scarab increases greatly. Luckily, the notorious botnet was majorly disrupted in March 2020, reducing malware infections worldwide. In addition, some variants are spread via fake Flash Player and use exploit kits to get into the affected machines all over the world.
Right after the infiltration, the virus encrypts video, music, picture, document, and similar personal data by using symmetric and asymmetric encryption algorithms. You can find files encrypted by ransomware by looking at the appendix of your files. If they have .scarab file extension, .scorpio, .zzzzzzzz, and similar suffixes, they are encrypted and you won't be capable of using them.
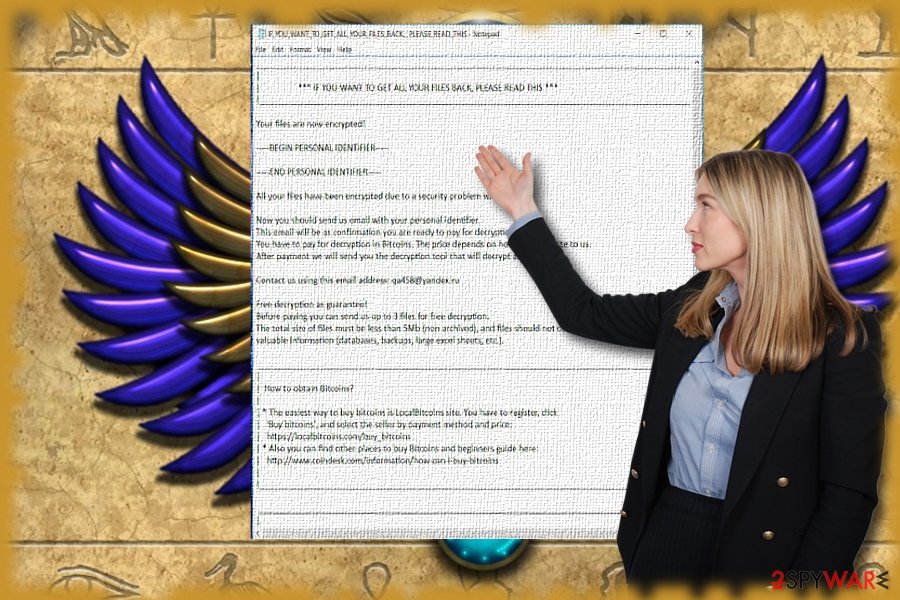
Scarab locks files and demands a ransom in exchange for the key
Originally, the ransom note of this virus is using the Russian language, but its latest versions are using the note translated into English. Typically, it reads:
*** IF YOU WANT TO GET ALL YOUR FILES BACK, PLEASE READ THIS ***
Your files are now encrypted!—– BEGING PERSONAL IDENTIFIER ————-
—– END PERSONAL IDENTIFIER ——————
All your files have been encrypted due to a security problem with your PC.
Now you should send us email with your personal identifier.
This email will be as confirmation you are ready to pay for decryption key.
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.Contact us using this email address: [email address]
Free decryption as guarantee!
Before paying you can send us up to 3 files for free decryption.
The total size of files must be less than 10Mb (non archived), and files should not contain
valuable information (databases, backups, large excel sheets, etc.).[……]
To gain users' trust, the developers are offering free decryption of three files up to 1 MB in size. However, felons do not indicate the sum of the ransom but rather urge affected users to contact them as soon as possible since the deadline for the ransom payment ends after 72 hours.
Following these orders is not recommended. Cybercriminals cannot be trusted in any way, so after paying the ransom you may be left without both money and files. Security experts recommend victims remove the virus ransomware instead of using a professional anti-malware tool, like SpyHunter 5Combo Cleaner or Malwarebytes.
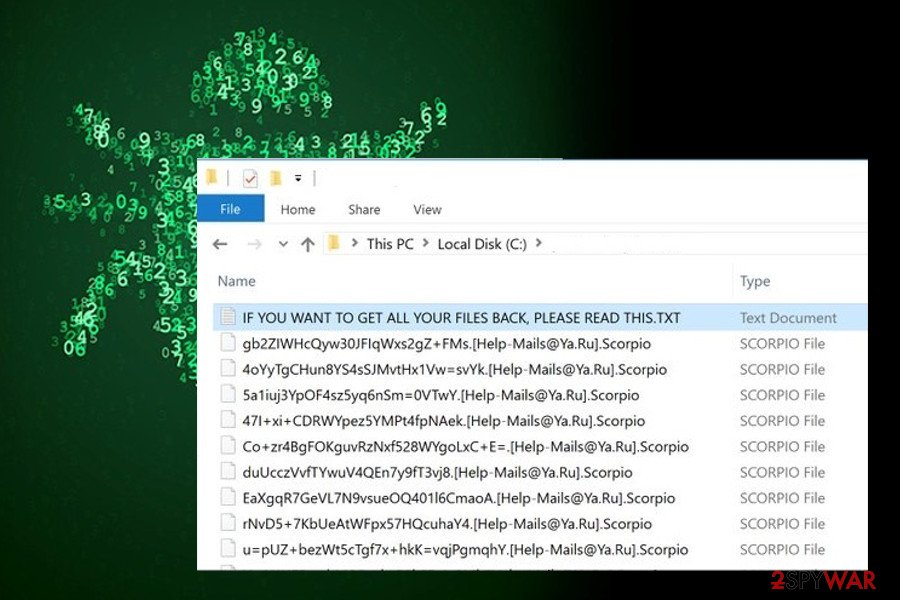
Once you complete the proper virus removal, you will be able to recover the biggest or even all of the encrypted files using third-party data recovery tools. You can find a comprehensive decryption tutorial at the end of this article. Alternatively, you can email a few encrypted files to Dr.Web (emte@adc-soft.com) and see if security experts can decrypt files for you.
The ransom note of the virus is typically instructing the victim to provide the personal identifier and contact the felons via the provided email address. Updated variants of the Scarab virus have been using different email addresses for communication with victims. Some of the used emails are:
- qa458@yandex.ru;
- resque@plague.desi;
- Help-Mails@Ya.Ru;
- suupport@protonmail.com;
- unlocking.guarantee@aol.com;
- westlan@protonmail.ch;
- anticrypto@protonmail.com;
- decry1@cock.li;
- decry2@cock.li;
- decrypts@airmail.cc;
- translatos@protonmail.com;
- infovip@airmail.cc;
- DiskDoctor@protonmail.com
- fastrecovery@airmail.cc
- xmail@cock.li
- mr.leen@protonmail.com
- bd.recovery@aol.com
- firmabilgileri@bk.ru
- barracuda@airmail.cc
- ProjectJoke@aol.com
- projectjoke@india.com
- FushenKingdee@protonmail.com
- madeinussr@protonmail.com
- decoding_service@aol.com
- decoding_service@protonmail.com
- inc_evilsi@protonmail.ch
- worcservice@protonmail.ch
- logiteam@protonmail.com
Note that the Scarab ransomware decryptor has not been yet created, so it is quite difficult to retrieve files back. However, in April 2018, Doctor Web announced[3] that some cases of ransomware can be decrypted. For that, victims should send the ransom note HOW TO RECOVER ENCRYPTED FILES – decrypts@airmail.cc.TXT and 3-4 encrypted files to the email emte@adc-soft.com. If infected with any of these versions, try this method for files' decryption. If it does not work for you, jump to the end of this post to use other methods for data recovery. However, make sure you remove the ransomware before this procedure.
The list of variants
Scarab ransomware has been appearing with new versions since last year. Recently, it came to researchers' attention as the malware that receives updates pretty much each month. At the moment, there are twenty different members of this money extortionist family that are listed below.
Scorpio ransomware
Scorpio ransomware is believed to be the first new update to the original variant of Scarab ransomware. The most noticeable features of this virus are its ability to crack the computer in multiple different stages.
Firstly, it settles on the computer with the help of bogus scripts executed via Command Prompt Admin. The next phase encompasses data encryption. Scorpio ransomware scans the system for targeted files, applies AES cipher to lock them, and eventually appends .[Help-Mails@Ya.ru].scorpio file extension to distinguish them from the others.
The final phase is informative. Scorpio virus generates a ransom note named IF YOU WANT TO GET ALL YOUR FILES BACK, PLEASE READ THIS.txt. The file contains a unique victim's ID, and contact information, including email address (Help-Mails@Ya.Ru and alexous@bk.ru).
Crypto ransomware
Scarab-Crypto is the name of the next ransomware version detected in the second half of March 2018. Just like its ancestors, it uses AES cryptography and targets the most popular file types. Its distinctive feature is a .crypto file extension and HOW TO RECOVER ENCRYPTED FILES.TXT file. It instructs the victim to email Scarab-Crypto ransomware developers via anticrypto@protonmail.com and indicate a personal identification number.
Extortionists should subsequently unlock two files encrypted by the threat for free to claim their trustworthiness. The sum of the payment is not revealed in the note, but the victim is demanded to initiate a transaction via Bitcoin wallet asap to get a decryptor.
Amnesia
Spotted at the end of March 2018, this new version spreads via Necurs botnet and executed its payload when the potential victim extracts a 7Zip email attachment. Likewise other versions, it uses AEX-256 encryption algorithm. However, it can easily be distinguished from the rest of Scarab versions by an .amnesia file extension added to locked files. The list of targeted files:
.Png, .psd, .pspimage, .tga, .thm, .tif, .tiff, .yuv, .ai, .eps, .ps, .svg, .indd, .pct, .pdf, .xlr, .xls, .xlsx, .accdb, .db, .dbf, .mdb, .pdb, .sql, .apk, .app, .bat, .cgi, .com, .exe, .gadget, .jar, .pif, .wsf, .dem, .gam, .nes, .rom, .sav, .dwg, .dxf, .gpx, .kml, .kmz, .asp, .aspx, .cer, .cfm, .csr, .css, .htm, .html, .js, .jsp, .php, .rss, .xhtml, .doc, .docx, .log, .msg, .odt, .pages, .rtf, .tex, .txt, .wpd, .wps, .csv, .dat, .ged, .key, .keychain, .pps, .ppt, .pptx, .ini, .prf, .hqx, .mim, .uue, .7z, .cbr, .deb, .gz, .pkg, .rar, .rpm, .sitx, .tar.gz, .zip, .zipx, .bin, .cue, .dmg, .iso, .mdf, .toast, .vcd, .sdf, .tar, .tax2014, .tax2015, .vcf, .xml, .aif, .iff, .m3u, .m4a, .mid, .mp3, .mpa, .wav, .wma, .3g2, .3gp, .asf, .avi, .flv, .m4v, .mov, .mp4, .mpg, .rm, .srt, .swf, .vob, .wmv, .3d, .3dm, .3ds, .max, .obj, .r.bmp, .dds, .gif, .jpg, .crx, .plugin, .fnt, .fon, .otf, .ttf, .cab, .cpl, .cur, .deskthemepack, .dll, .dmp, .drv, .icns, .ico, .lnk, .sys, .cfg.
Scarab-Amnesia ransomware informs its victims about the current situation and the steps he or she has to take to decrypt files on a HOW TO RECOVER ENCRYPTED FILES.TXT file. Typically, it is stored on the desktop, but can also be found on random folders that contain files with .amnesia file extensions.
Please ransomware
At the end of March 2018, security experts discovered Please ransomware that is using AES encryption to modify targeted files. It is appending .please file extension to target data and dropping a ransom note “HOW TO RECOVER ENCRYPTED FILES.TXT” on a desktop. This message informs the victim to use an email called decry1@cock.li or decry2@cock.li to contact its developers and get further instructions needed for the recovery of affected files. Cybercriminals are also claiming that the victim can test the decryption procedure to ensure that it is possible. However, we do not recommend contacting hackers. Ransomware also can make changes to Windows registry key so this is better be deleted soon.
Decrypts ransomware
It is yet another version of ransomware. It's more or less similar to its ancestors, though exhibits different file extensions and the ransom note. Written on Delphi, it takes advantage of the AES-256 cipher to attack victim's files and render them useless by altering their file extension.
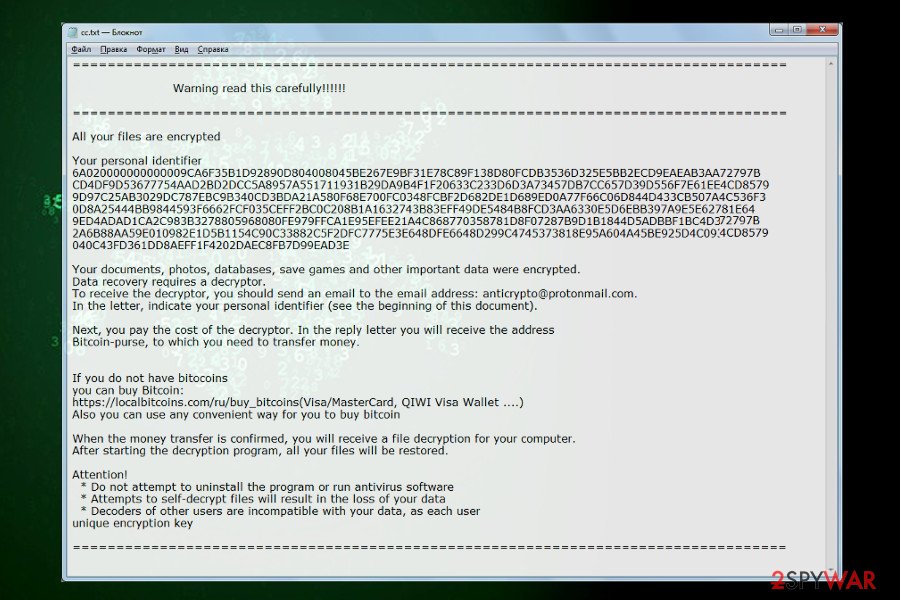
Following the encryption phase, each locked file gets either .decrypts @ airmail.cc or .decryptsairmail.cc file extension. Consequently, the owner cannot dispose of them in any way. The Scarab-Decrypts ransomware provides its victims with a ransom note called HOW TO RECOVER ENCRYPTED FILES-decrypts@airmail.cc.TXT. It does not say much, except that the files have been encrypted and provides an email address which asks the victim to contact to decrypts@airmail.cc and provide a unique identification number for further instructions. You can see an example of the Scarab-Decrypts ransom note below.
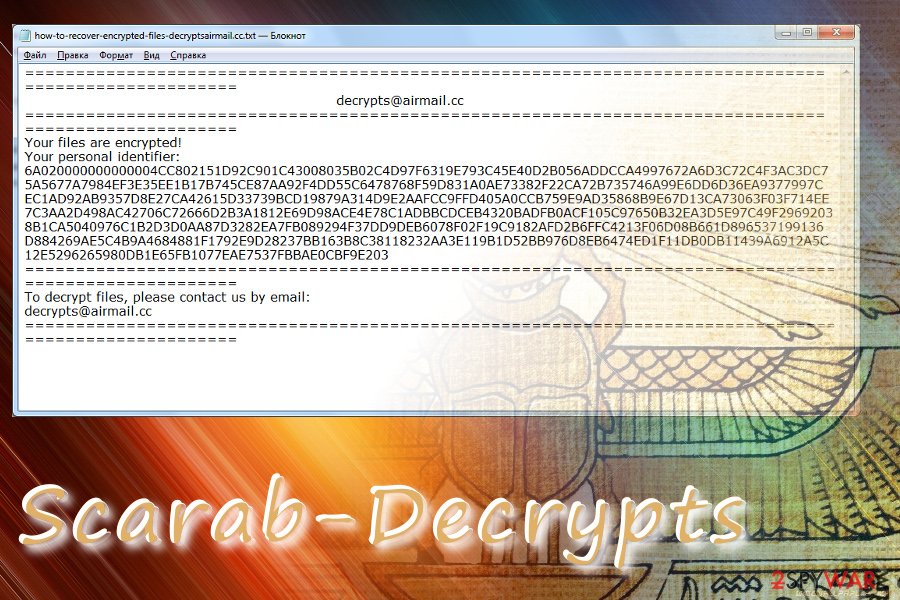
Horsia
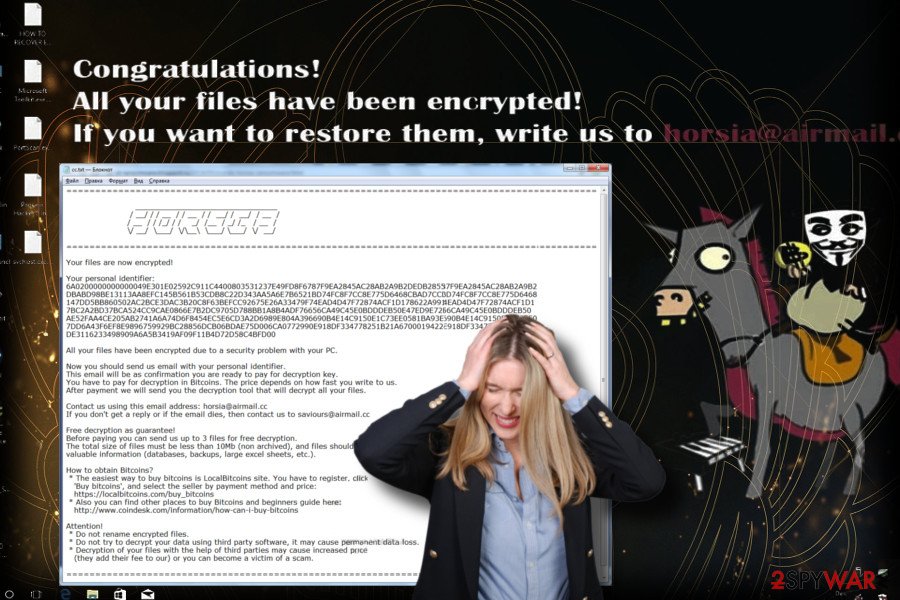
Horsia ransomware version was spotted at the beginning of May 2018. Disguised under 7Zip and otherwise named email attachments, the ransomware targets English-speaking PC users. Once it's installed, malicious processes start running in the background to protect the Horsia ransomware from removal.
Encrypted files are easy to notice as they get .horsia@airmail.cc file extension, which cannot be modified manually. Besides, each folder, including the desktop, contains a HOW TO RECOVER ENCRYPTED FILES.TXT file explaining the current situation, including payment and contact information. The full ransom note reads as follows:
Walker
This version of the dangerous cyberthreat and was spotted by security experts shortly after the Horsia variant came out. Just as all previous versions, Walker ransomware users AES cryptography to encrypt files. It changes all media, video, text and other personal files and makes them unusable by adding .JohnnieWalker extension.
As usual, after data encryption, Scarab-Walker virus drops a ransom note in the .txt format, explaining the situation to the user. Hackers demand payment in Bitcoins. Soon after the ransom is paid, users are prompted to e-mail JohnnieWalker@firemail.cc and include their personal ID. Additionally, cybercrooks offer to unlock one file to prove that data is decryptable.

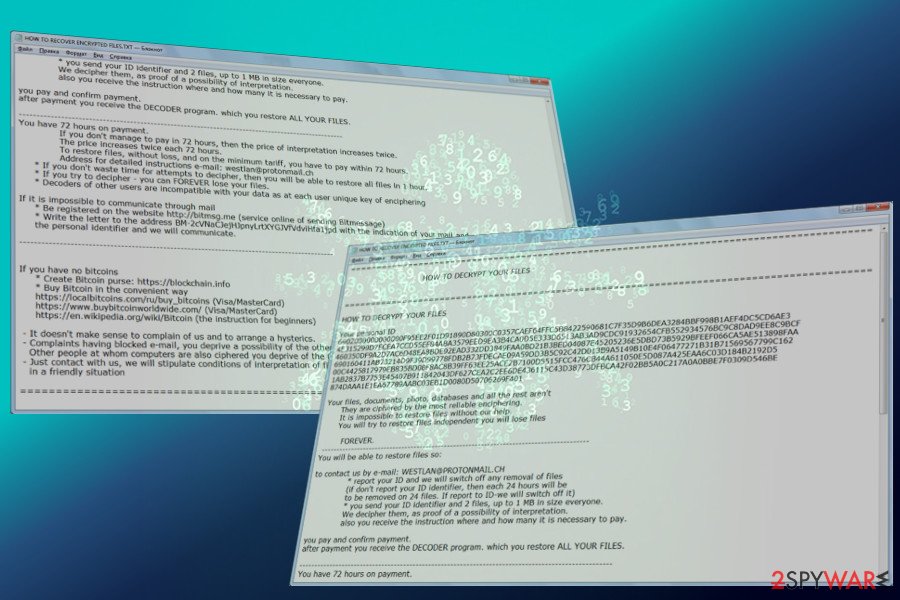
Fastrecovery@airmail.cc
Additionally, the malware reappeared in June 2018 with the .fastrecovery@airmail.cc file extension to mark each of the affected files. The virus drops a ransom note HOW TO RECOVER ENCRYPTED FILES-fastrecovery@airmail.cc.TXT into each folder which explains about files' encryption using RSA-2048 cipher. The only way to recover locks files is said to be a special decryprion key that is stored by criminals on a remote server.
Osk
Scarab-Osk is encrypting data by using AES cipher. It is using .osk extension to mark every affected file. Hackers ask for 0.013 Bitcoin in HOW TO RECOVER ENCRYPTED FILES.txt message to be paid and then email sent to translatos@protonmail.com for further instructions and the decryptor. As usual, we advise refraining yourself from contacting cybercrooks and restore all encoded data using a backup.
DiskDoctor ransomware
DiskDoctor ransomware is still encrypting files with the same AES-256 encryption algorithm. Differently from previous variants, this one appends .DiskDoctor file extension to the targeted files. But it still displays data recovery instructions in the text file called “HOW_TO_RECOVER_ENCRYPTED_FILES.txt.”
In the ransom note, crooks demand to contact them via DiskDoctor@protonmail.com email address in order to learn about data recovery possibilities. However, we do not recommend trying to get back your files in this way. Crooks will demand to transfer a few hundreds of dollars in Bitcoins in order to get a decryption tool. However, once you make a transaction, they might disappear and never give you a needed tool. Hence, you should remove DiskDoctor from the computer ASAP.
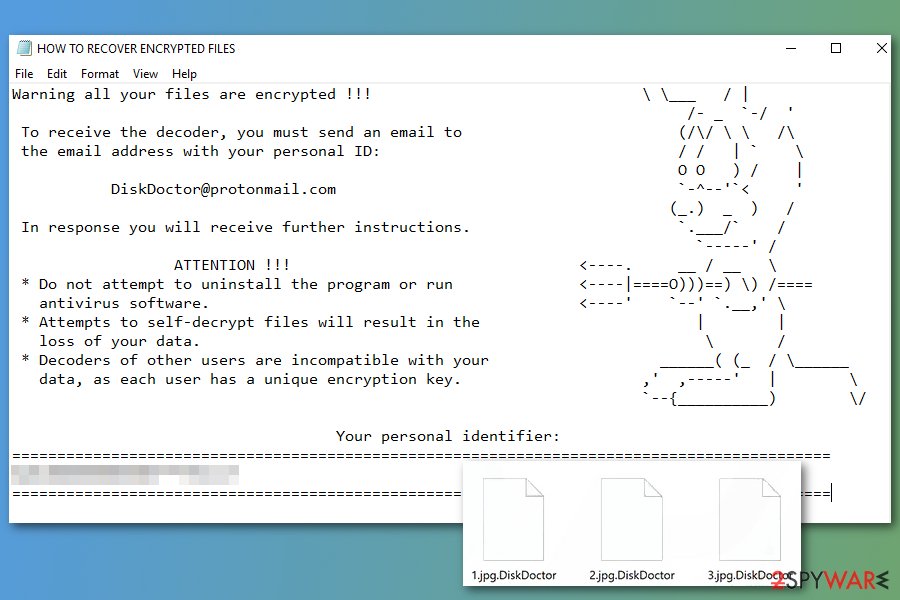
Good ransomware
In June 2018, researchers detected a few version of Scarab and this one is decryptable with Dr. Web. “.good” is a file extension that virus adds to modified files and “filedecryption@prorotnmail.com” is the contact email address. As typical for the family, the ransom note is placed in file “HOW_TO_RECOVER_ENCRYPTED_FILES.txt.”. This contains information about encryption and what to do but no specifics about the ransom or decryption. This virus version came to the light alongside other ones.
Leen ransomware
Just like its name suggests, Leen ransomware is using “.leen” to each of the files that become modified. As soon as that is complete, a ransom note is placed in every folder. “INSTRUCTIONS FOR RESTORING FILES.TXT.” contains information about this certain attack:
Contact us using this email address: mr.leen@protonmail.com
Free decryption as guarantee!
Before paying you can send us up to 3 files for free decryption.
The total size of files must be less than 10Mb (non archived), and files should not contain
valuable information (databases, backups, large excel sheets, etc.).
Cybercriminals demand unspecified payment in Bitcoins and suggest victims contact them via email “mr.leen@protonmail.com.” in order to get a key or more information.
Danger ransomware
Danger ransomware is decryptable with Dr. Web, but it is different from the most of the members in the family because this version uses RSA-2048 encryption algorithm. “.fastrecovery@xmpp.jp” is a file extension that this virus adds after the modification is complete. Typical “HOW_TO_RECOVER_ENCRYPTED_FILES.txt.” ransom message placed on pretty much every folder on the PC. Information about changing contacts and encryption method is the main useful things in the note. No specific ransom amount just email address “fastrecovery@xmpp.jp” that changes after three days.
Oneway ransomware
Difficult weeks in the cyber-security world while Scarab develops new variants each week. This version is targeting Russian-speakers because while this adds “.oneway” file extension the ransom note called “Расшифровать файлы oneway.TXT.” Email address “bm15@horsefucker.org” is provided in the message and the note contains more information about test decryption and the attack itself.
BtcKING ransomware
BtcKING ransomware came with more similar patterns. Encryption is done in a similar way and “.BtcKING” file extension looks like other previous versions. Also, this variant places a ransom message called ” How To Decode Files.txt” on every existing folder on the system and desktop. This ransomware also came in June 2018 alongside other dangerous versions.
Bomber ransomware
Another ransomware targeting Russian victims. This ransomware appends photo, video, text and other files with “.bomber” file extension so it is easily detected which ones are modified. After this encryption process is completed virus creates a ransom note “HOW recover encrypted FAYLY.TXT” and you can have more details about the attack. This is placed on your desktop and in every folder where you can find modified files. This version displays soft2018@tutanota.com; soft2018@mail.ee; newsoft2018@yandex.by as possible contact emails.
JungleSec ransomware
JungleSec version of Scarab has more specific details. Encryption is done while appending “.jungle@anonymousspechcom” extension to modified files. And after that ransom note, “ENCRYPTED.md” is placed in multiple places on the system. In this file, you can discover that virus developers demand a certain 0.3 in Bitcoin and state their contact email as “junglesec@anonymousspeech.com” which you are suggested to contact after the payment is done. This version has no decryption option.
Recme ransomware
Recme ransomware is one of the newest variants discovered in late June of 2018, with classical Scarab encryption patterns. After the encryption process, during which “.recme” file extension is placed on your photos, videos, text, or archive files, this ransomware creates a ransom message called “HOW_TO_RECOVER_ENCRYPTED_FILES.txt.”. In this message, you can find more details about the cyber attack.
Dan ransomware
This version of Scarab ransomware came alongside the previous five is the one that adds “.dan@cock.email” file extension to targeted files. These can be anything from images, photos, or videos to text files or even archives. After this modification is complete you can find ransom note file “HOW TO RECOVER ENCRYPTED FILES-dan@cock.emai.TXT”. This is a ransom message that often contains various information about the initial attack and instructions for the victim.
Recovery ransomware
Scarab-Recovery came out in early July 2018. The virus is written in the Delphi programming language and uses AES to lock up data. The crypto-virus adds .BD.Recovery extension to each of the affected file and drops ransom note “HOW TO RECOVER FILES.TXT” which states that victims should email crooks via bd.recovery@aol.com or bd.recovery@india.com. However, hackers should never be contacted as it can result in a loss of money.
Turkish ransomware
As the name suggests, this version of Scarab focuses on Turkish PC users. However, all the Turkish characters were replaced by English letters, making it impossible to understand. The virus uses AES to encrypt data and ads [Firmabilgileri@bk.ru] appendix to each of the affected files, which is also a contact email of cybercriminals. As usual, we suggest you ignore cybercrooks and remove Scarab-Turkish from your machine ASAP.
Barracuda ransomware
The latest variant of crypto-virus is dubbed Scarab-Barracuda because it encrypts files and adds .BARRACUDA file extension. The virus is closely related to Scarab-Rebus and can be decrypted. Therefore, do not waste your money and do not pay cybercrooks. Merely contact security experts who can help to decode data. Unlike many other versions, Barracuda ransomware drops a ransom note which includes its name in it – BARRACUDA RECOVERY INFORMATION.TXT. Cybercriminals are trying their best to scare users with the following:
Attention!
Do not attempt to remove a program or run the anti-virus tools
Attempts to decrypt the files will lead to loss of Your data
Decoders other users is incompatible with Your data, as each user unique encryption key
zzzzzzzz ransomware
In 2019, the owners of Scarab ransomware returned with a new file extension used to block victims' files and convince them to pay the ransom. At the moment, the virus is appending .zzzzzzzz file extension after using an encryption algorithm to scramble the code of separate files. Keys are required to unlock encrypted files and saved them in external servers which can be reached only by cybercriminals.
According to the ransom note, victims have 5 days to unlock files by paying a ransom. The payment should be made either in Bitcoin or Dash cryptocurrency. Zzzzzzzz ransomware is not decryptable yet, just like numerous other versions of Scarab. If infected, use third-party tools to unlock your files.

Ssimpotashka@gmail.com ransomware
Ssimpotashka@gmail.com ransomware is one of the variants that resurfaced after its initial release in July 2018. Almost two years later, users started reporting infections of this Scarab version once again. Since the malware is using an improved RSA algorithm to lock files, it cannot be decrypted with previously working methods, unless working backups are retained.
Soon after the infiltration, the Ssimpotashka@gmail.com virus begins performing the necessary changes to make the machine ready for data encryption. Malware targets hundreds of file types, although it skips the system and some executable files for the computer to be functional after the infection (the goal of ransomware is not to destroy Windows per se – hackers seek to retrieve money from ransom payments instead).
After the encryption, each of the affected files receives a marking .Ssimpotashka@gmail.com, and can no longer be accessed. For data recovery, users need to email the attackers and then pay a ransom (typically in bitcoin cryptocurrency) to retrieve a decryption tool with a unique key. The information about the infection and further actions can be found in a ransom note HOW TO RECOVER ENCRYPTED FILES.txt file, which is dropped in several places on victims' computers.
.rbs file extension virus
The first renewed Scarab version that surfaced in 2020 is dubbed as .rbs file extension virus. According to its founders, the ransomware is spread via spam emails that contain malicious .exe or .zip attachments. It is using a sophisticated RSA encryption algorithm to lock files and mark each of them with the .rbs appendix.
Upon successful encryption of the victim's data, it drops a ransom note TO HOW DECRYPT files.txt, which demands to pay 0.1 BTC on Bitcoin Wallet 1GPUVdXsW6T57aUAJuQ2sWx4X2M76MAQmr 2. Once the payment is transferred, the victim is supposed to contact criminals via a madeinussr@protonmail.com email address.
Criminals promise to react to the payment within 24 hours. In case no response is received, criminals ask the victim to download a Bitmessage[4] and send a message to the BM-2cWQjc8pWXmMMrRh26ADg1XXMbtZ4UpdbA member.
.ncov ransomware
Spotted on February 25, 2020, the .ncov file extension virus turned out to be another family member of the infamous Scarab. The ransomware has been reported by several cybersecurity community members who have fallen victims to this malicious virus.
Just like its predecessors, it uses a complicated RSA cipher to lock files and then generates a ransom note Note: Data Decryption Guide.TXT on the desktop and multiple system's folders. The .ncom ransomware virus seems to be targeting Russian-speaking countries predominantly as its ransom note is written in Russian and has no translation into English or other languages. The victim attacked by the .ncov ransomware is expected to contact crooks via ncov@cock.li and transfer the ransomware payment within 24 hours. After that, the payment doubles and gets fixed after 72 hours period.
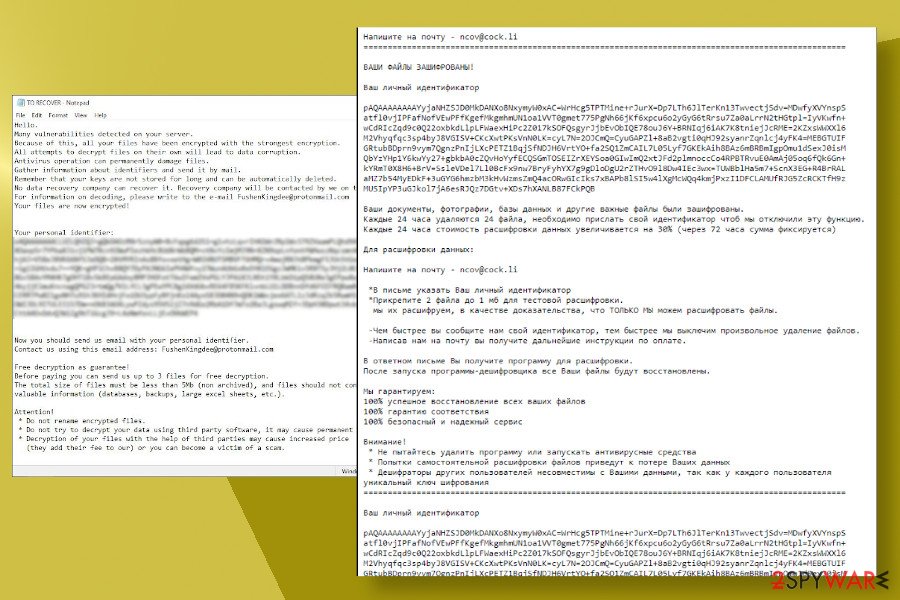
Cov19 ransomware virus
Cov19 ransomware is the latest member of the Scarab family. As soon as the Coronavirus pandemic gathered momentum, cybercriminals started leveraging the COVID-19 theme as a name for new cyber infections. Apart from thousands of Covid-19 spams, criminals use Coronavirus references for ransomware too. Crooks behind Scarab are not exceptional.
The Scarab Cov19 ransomware virus has resurfaced in the middle of May 2020. The basic features of the virus are reminiscent of the original, except for the .cov19 file extension and a new name for the ransom note, which is TO RECOVER.TXT. The note:
Hello,
Many vulnerabilities detected on your server.
Because of this, all your files have been encrypted with the strongest encryption.
All attempts to decrypt files on their own will lead to data corruption.
Antivirus operation can permanently damage the files.
Gather information about identifiers and sent it by mail.
Remember that your keys are not stored for long and can be automatically deleted.
No data recovery company can recover it. Recovery company will be contacted by we on the indicated mail.
For information on decoding, please write to the email FushenKingdee@protonmail.com
Your files are now encrypted!
Please do not pay the ransomware. Experts are currently under investigation if the files encrypted by .cov19 extension can be decrypted for free. We recommend removing the ransomware asap and contact reputable vendors for help.
Bomba ransomware
Bomba ransomware is the summer 2020 edition of the Scarab ransomware virus. It has been detected at the beginning of June disguised under malicious .ZIP email attachments. The emails carrying this virus tend to imitate order confirmations, though the senders and content vary.
Once the payload is launched, the virus starts the changes within system's settings and unravels the cipher (AES + RSA), which locks files using the .bomba file extension. Subsequently, all pictures, photos, docs, music files, etc. can't be opened or renamed.
Also dubbed as .bomba file extension virus, this ransomware cannot be decrypted for free. Therefore, if you don't have backups, you have two options – either write an email to the logiteam@protonmail.com with a unique identifier (a long string of letters and numbers provided on the ransom note) and pay the redemption for criminal or backup locked files on the external hard drive, inform cybersecurity experts (.e.g Dr. Web who are already capable of decrypting some of the ransomware versions) and wait for the decryption software.
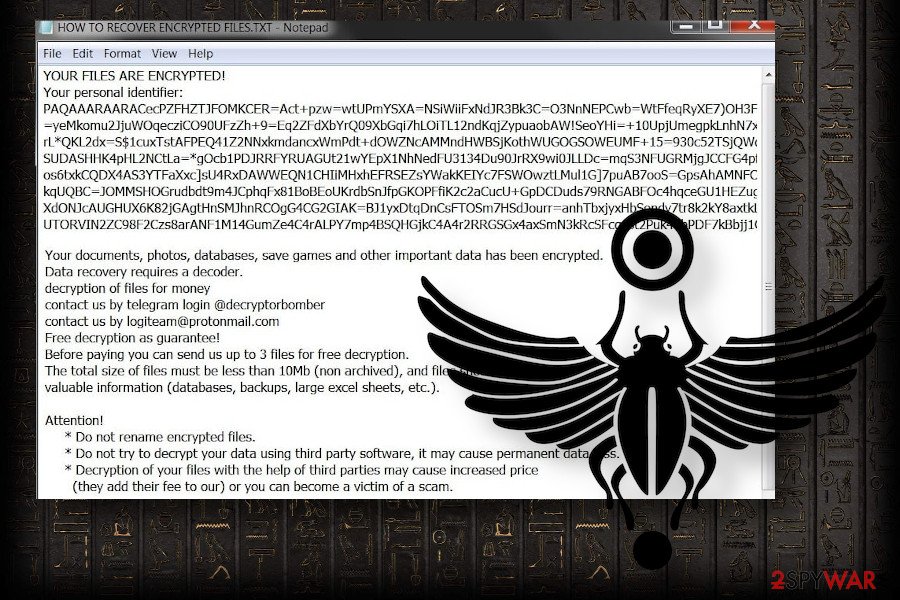
By the way, criminals behind the Bomba virus provide their victims with a privilege – they allow sending 3 files (up to 10mb) for free decryption. That's test decryption to prove to the potential payers that the Scarab decryption key that they have is fully functional.
Anyway, Bomba ransomware removal is a must since ransomware can also be used for the backdoor of banking trojans, spyware, or other malicious entries. Use a professional security program to delete the malicious ransomware files altogether and then recover the machine with FortectIntego repair tool.
The notorious trojan botnet used to spread the ransomware around
Necurs botnet is infamous for the distribution of different ransomware-type infections. In November, cybersecurity experts have also detected it spreading the Scarab virus[5]. Criminals are aiming to affect computers located in[6]:
- Australia;
- Germany;
- United Kingdom;
- France.
At the moment of writing, the botnet already sent about 12.5 million emails with a malicious 7Zip archive with the Visual Basic script that downloads and executes the third version of the virus.
The subject line of these emails is made by this scheme: “Scanned from [printer/scanner company name].” Currently, the most popular versions of titles are:
- Scanned from Lexmark;
- Scanned from Canon;
- Scanned from HP;
- Scanned from Epson.
The infected archive itself is named image2017-11-23-4360760.7z. However, the name of this file might change based on the distribution data. Therefore, users are advised to be careful and watch out for emails sent from copier@[your email address or company’s domain].
Spam emails is yet another method used to spread Scarab
The authors of this crypto-malware continue to distribute the virus in the old-school way which relies on malicious spam emails[7]. Cybersecurity experts have detected an enormous wave of malicious emails distributed with the help of Necurs botnet in late 2017. The content of the letter included VBS scripts disguised as innocent scanned documents in 7Zip archive.
Therefore, users should be aware of potential dangers that might be sent straight to the inbox. Keep in mind that if you do not retain rational thinking and cautiousness, no anti-virus will be able to save you from the hijack or another malware infiltration. In addition, note that some hackers still use old trickery: visiting a corrupted site, you may notice a fake alert prompting to update your Java or Adobe Flash Player.
The only way to get rid of Scarab ransomware is a reliable malware removal tool
Our security experts understand how threatening it might seem to lose encrypted data by trying to remove Scarab ransomware. Although, the only way to decrypt files without paying the ransom is to get rid of this cyber threat with a robust antivirus. We suggest using FortectIntego, SpyHunter 5Combo Cleaner. or Malwarebytes. Afterward, you will be able to try alternative data recovery methods presented below.
In case you cannot launch your security software, take a look at the bottom instructions. They should help you launch it and overcome this issue. However, note that the cybersecurity application does not decode files and can help you only for Scarab ransomware removal.
Getting rid of Scarab virus. Follow these steps
Scan your system with anti-malware
If you are a victim of ransomware, you should employ anti-malware software for its removal. Some ransomware can self-destruct after the file encryption process is finished. Even in such cases, malware might leave various data-stealing modules or could operate in conjunction with other malicious programs on your device.
SpyHunter 5Combo Cleaner or Malwarebytes can detect and eliminate all ransomware-related files, additional modules, along with other viruses that could be hiding on your system. The security software is really easy to use and does not require any prior IT knowledge to succeed in the malware removal process.
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Scarab and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Kelly Bissell. Don’t Be Held For Ransomware. CFO. IT news and commentary.
- ^ Ben Gibney & Roland Dela Paz. Massive Email Campaign Spreads Scarab Ransomware. Forcepoint blogs. News, views and insights for security professionals to defend against cyber attacks and data theft.
- ^ Dr. Web anti-virus. Re.Web. Security researchers.
- ^ Daniel Cawrey. Bitmessage is the Bitcoin of online communication. Coin Desk. Media platform for investors in cryptocurrency.
- ^ Necurs’ Business Is Booming In A New Partnership With Scarab Ransomware. F-Secure Labs. Security blog.
- ^ Die Viren. Die Viren. Cyber security news and malware database.
- ^ Catalin Cimpanu. Google Says Gmail Now Blocks 99.9% of Spam and Phishing Emails. BleepingComputer. News, reviews and tech support.


































