Google virus. The latest versions revealed (recovery guide for 2019)
Google virus Removal Guide
What is Google virus?
Google virus – a term used to describe a variety of cyber infections and scams related to the name of the tech giant

Google virus is a set of computer infections and scams that use Google's name in order to steal personal user data, trick into installing malicious software, or spend money on useless programs. Of course, the malicious actors have nothing to do with Google, which probably the best-known company in the world, employing almost 100k employees.[1] Nevertheless, the massive corporation sometimes slips too by failing to block phishing links or letting in malicious apps into Chrome store or Google Play.[2]
| Name | Google virus |
| Type | Trojan horse/backdoor/malware/potentially unwanted program/survey scam/tech support scam |
| Infection means | Software bundling, third-party sites, spam emails, fake updates, misleading pop-ups, etc. |
| Symptoms | Symptoms of Google virus may vary:
|
| Main dangers | Malware infections, installation of potentially unwanted programs, sensitive information disclosure to cybercriminals |
| Examples | |
| Termination | You can delete some of the infections manually, although most serious threats should be terminated with anti-malware software |
| Optimization | To fix virus damage, we highly recommend scanning the device with FortectIntego |
Google virus is not tight to one browser or a type of the operating system and can affect Windows, Mac, iOS, and Android users. The broad term also includes a variety of computer infections and, while some, like browser hijackers and adware, are less harmful, threats like trojans, backdoors, ransomware[3] or rootkits can result in serious consequences, such money loss, personal file destruction, or even identity theft.
Besides, many crooks rely on Google's name to make their Google virus scams believable, claiming that the system is infected with viruses, or that users' personal information is at risk. Additionally, survey scams might promise expensive gifts, but in reality, seek users' payment details or make them subscribe for useless services.
All in all, Google virus should be underestimated, and, if you are affected, you should take adequate measures to protect your computer from damage, as well as yourself from hackers who might abuse your sensitive information for evil deeds.
Propagation techniques used by Google virus
Malware can be transmitted in a variety of methods, as hackers behind it are usually sophisticated and look to multiple ways that are less noticeable. Additionally, malware can use a variety of evasion techniques, making Google virus removal complicated in some cases. Nevertheless, there is always the way to remediate infected machine and get rid of the threat for good.
Malware authors that spread Google virus might use the following propagation techniques:
- Malicious spam email attachments or hyperlinks
- Software bundles
- Unprotected Remote Desktop connections[4]
- Exploits[5]
- Fake updates
- Pirated or cracked software, etc.
Nevertheless, most of Google virus variants are mostly cases of adware infections, which are far less threatening. To find out if your machine is infected with malware or a potentially unwanted program, it would be best to scan your computer with security software to detect and terminate most of the viruses.
Some Google viruses might alter the way Windows OS operates, changing its registry[6] or altering the boot sequence. To revert these changes and fix infected system files, scan your device with FortectIntego.
It is not safe to use your machine until you remove Google virus, as some infections, such as trojans, might be able to steal your personal information that you enter into certain fields (for example, credit card details) or record all your keystrokes.
Alternatively, adware might lead you to phishing and scam sites that either will prompt you to install bogus software and then pay for its licensed version or deceptively subscribe you for some kind of service you do not want or need. On the other hand, threats like The HoeflerText font wasn’t found are using a simple trick to install such threats like Locky ransomware, Spora ransomware, or Zeus banking trojan.
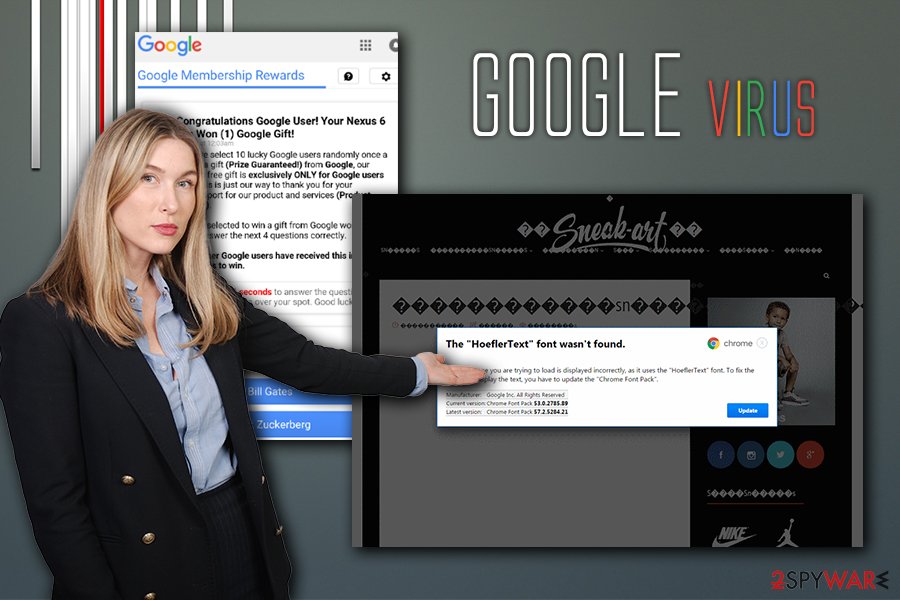
Google virus variants
There are many types of infections that might refer to the Google virus term. In this section, we will describe some of the versions you might encounter in the wild.
Google redirect
Google redirect virus is probably one of the most common Google virus variants, and it usually indicates adware, or other potentially unwanted program infection. PUPs often travel within software bundles or are downloaded from third-party sites intentionally, without knowing that the program is potentially dangerous.
As soon as Google redirect virus settles, it takes over the browser and starts displaying alternative search results, which usually come in the form of sponsored links that are located and the top. In such cases, users are often misled by this behavior and click on sponsored links – not genuine Google results, but the links that adware or other PUP is promoting.
This might not only prevent users from finding relevant information but also increase traffic to unknown websites, as well as artificially inflate their rankings. Additionally, not all of the links are secure, and users might end up on malware-compromised sites resulting in Google virus infiltration.
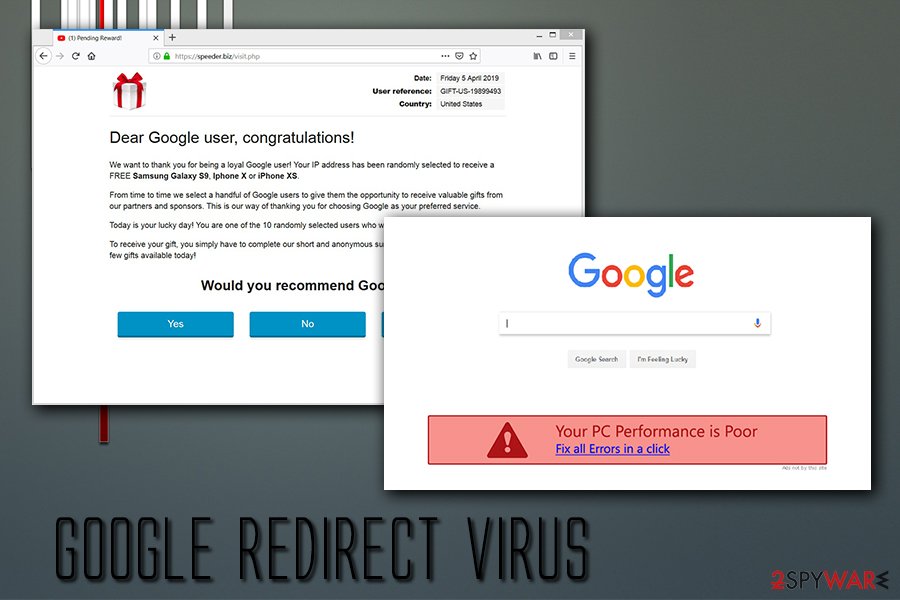
Google redirect virus can also be extremely annoying to deal with, as it can add a layer of pop-ups, deals, banners, offers, and other ads into all sites that users visit. Clicking on such advertisements is not recommended as ad space can be bought by cybercriminals that insert malicious code into the website.
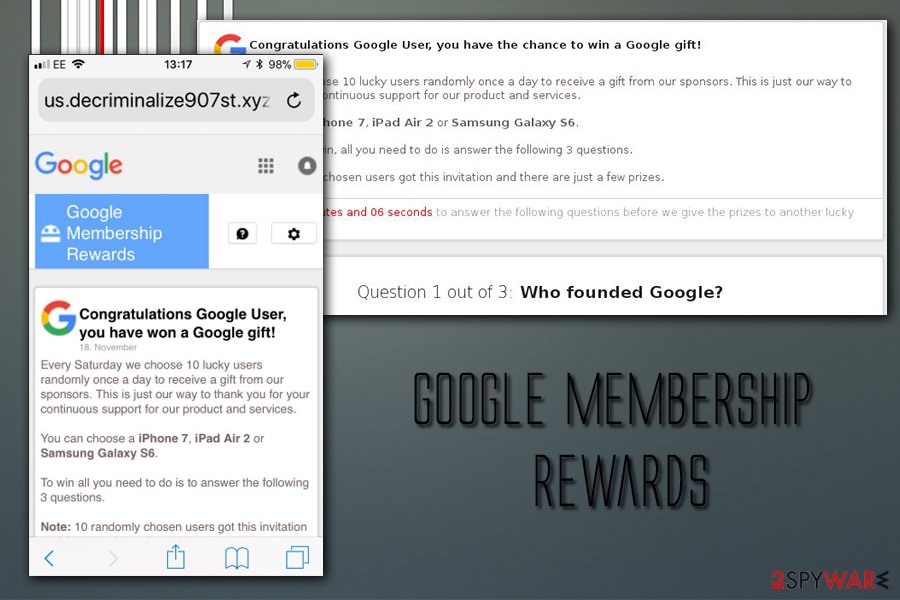
Google Membership Reward
Google Membership Reward belongs to survey scam category. While it has many similarities with technical support scams,[7] it uses different techniques to make users either disclose their personal information, such as credit card data or make them subscribe to a service they did not intend to. Nevertheless, both categories use deception and social engineering to work.
Most usually, users land on the Google Membership Reward accidentally when they visit a suspicious website or are redirected due to adware or PUP infection. There, users are informed that they are selected few among other Google users (which is a lie – the message is shown to every visitor), and are eligible to valuable prizes for free – all they have to do is allegedly answer very primitive questions in a survey. The offered gifts vary, but some examples include:
- $1000 Walmart Giftcard,
- iPhone X 256 G
- Samsung Galaxy S8
- PlayStation 4
What is more, users are also informed that they only have a mere few minutes to take the survey, as the prize will allegedly be given to somebody else. This tactic is often used by tech support scams too, providing a fake timer that creates an “immediate action” situation where users simply do not have time to think whether or not the claims are true.
However, there is no gift, and all the promises are fake. Do not trust Google Membership Reward if you encounter it, as nobody is trying to give you $1,000 or similar expensive gift for free.
Google Lead Services
Google Lead Services, which is also known as GoogleLeadService.com, is a fraudulent website that promotes its advertising services, such as Zip Code Lookup. Nevertheless, this shady site has nothing to do with the original company, as it only uses the name of it in the hopes of providing a sense of legitimacy.
Thankfully, the developers of the servers are at least decent enough to describe what they actually are, as the fine print reads:
We are not affiliated with or related to Google Lead Services™ in any way. The term “Google” is used as a synonym for “Search”
The service itself offers to display banners and another type of ads, that might range from regular size to full page ones. In most cases, these pop-ups, banners, deals, etc., are delivered with the help of adware application that is secretly infiltrated during freeware installation.
Thus, to remove Google Lead Services ads from their browsers, they need to locate and delete adware that is installed on their devices. As usual, we suggest scanning the device with security software or delete the application manually with the help of our instructions.
Google Chrome 1111 virus
Google Chrome 1111 virus is possibly one of the strangest Google virus variants. Once infected, the web browsers start displaying strange pop-ups with nothing by “111” or “1111” in them. While the dialogue can be closed, it can often return and spam the web browser.
Nevertheless, this is not the only activity that Google Chrome 1111 virus does. Allegedly, it can also spawn pop-ups that advertise a variety of services or display fake online job offerings, promising earnings of $20,000. However, please do not get lured by these advertisements, as they are all fake or might even be dangerous.
To stop the annoying behavior which constantly disturbs web browsing sessions, you will have to determine what type of malware is installed on your device and terminate it. The best way to do it is by using reputable security software.
To stay away from malware, use extra caution

While the internet has become much safer in the past 20 years, it does not mean that it is entirely secure. Nevertheless, some users are simply unaware of that or do not care about the consequences of a cyber infection, thinking that it will not affect them in any way.
While it is true that most potentially unwanted applications will not cause major harm as long as they are deleted on time, other viruses, such as trojans, ransomware or info stealers might result in permanent file/money loss or even identity theft. Besides, careless usage of the computer while infected with an adware might result in exact same consequences.
Staying away from potentially unwanted programs is relatively simple – you need to make sure you look at the installation instructions of shareware carefully and always opt for Advanced/Custom settings. This will allow you to terminate browser add-ons, system optimizers, uninstallers, driver updaters, and similar crapware.
On the other hand, to protect yourself from more sophisticated threats, you need also to do the following, as advised by experts:[8]
- Install anti-malware software and keep it updated;
- Patch your operating system as soon as updates become available (do not postpone);
- Enable Firewall;
- Only use Remote Desktop services with VPN enabled and select a secure port for it;[9]
- Make sure you use strong passwords for all your accounts and enable two-factor authentication where possible;
- Do now download pirated software or its cracks;
- Make sure all your software updates are set to automatic setting;
- Use ad-blocker;
- Be careful with spam emails, as malicious attachments or hyperlinks might result in malware infections.
Delete Google virus from your computer to ensure its safe operation
Depending on the type of infection, Google virus removal will vary. In most cases, simple browser hijackers, adware and other PUPs can be uninstalled via the installed application list manually. If you are not sure how to do that, you can check our instructions below. Nevertheless, problems might arise even with unwanted programs, as it might not instantly be clear which program is the culprit of redirects and persistent ads.
However, if you downloaded some executable files or installed fake updates, you will have to use reputable security software to remove Google virus from your device altogether. Make sure you perform a full system scan with tools like FortectIntego, SpyHunter 5Combo Cleaner or similar.
Once you delete Google virus, you should also reset each of the installed browsers, as traces might still be present, and redirects might not stop right away.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of Google virus. Follow these steps
Uninstall from Windows
To terminate Google virus from Windows manually, please follow these instructions:
Instructions for Windows 10/8 machines:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

If you are Windows 7/XP user, proceed with the following instructions:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Delete from macOS
Macs are not immune to cyber infections – the myth has been debunked many times. Thus, if your browsers show strange behavior, delete the potentially unwanted app from your device as follows:
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Remove from Google Chrome
To make sure the virus does not return, Reset Google Chrome browser as explained below:
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Remove from Microsoft Edge
Delete unwanted extensions from MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Clear cookies and other browser data:
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Restore new tab and homepage settings:
- Click the menu icon and choose Settings.
- Then find On startup section.
- Click Disable if you found any suspicious domain.
Reset MS Edge if the above steps did not work:
- Press on Ctrl + Shift + Esc to open Task Manager.
- Click on More details arrow at the bottom of the window.
- Select Details tab.
- Now scroll down and locate every entry with Microsoft Edge name in it. Right-click on each of them and select End Task to stop MS Edge from running.

If this solution failed to help you, you need to use an advanced Edge reset method. Note that you need to backup your data before proceeding.
- Find the following folder on your computer: C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.
- Press Ctrl + A on your keyboard to select all folders.
- Right-click on them and pick Delete

- Now right-click on the Start button and pick Windows PowerShell (Admin).
- When the new window opens, copy and paste the following command, and then press Enter:
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” -Verbose

Instructions for Chromium-based Edge
Delete extensions from MS Edge (Chromium):
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Clear cache and site data:
- Click on Menu and go to Settings.
- Select Privacy, search and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Reset Chromium-based MS Edge:
- Click on Menu and select Settings.
- On the left side, pick Reset settings.
- Select Restore settings to their default values.
- Confirm with Reset.

Remove from Mozilla Firefox (FF)
Firefox is not immune to Google virus as the scam misusing its name can appear on this browser as well. Make sure you reset it if you were involved into this scam somehow.
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Delete from Safari
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

After uninstalling this potentially unwanted program (PUP) and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti-spyware. This will help you to get rid of Google registry traces and will also identify related parasites or possible malware infections on your computer. For that you can use our top-rated malware remover: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting malware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Google. Wikipedia. The free encyclopedia.
- ^ Liam Tung. Google: Malware in Google Play doubled in 2018 because of click-fraud apps. ZDNet. Technology News, Analysis, Comments and Product Reviews.
- ^ Tom Spring. ‘HoeflerText’ Popups Target Browsers With RAT and Locky Ransomware. Threat Post. The first stop for security news.
- ^ Ransomware attacks via RDP on the rise. Cyberon. Cyberon security.
- ^ Margaret Rouse. Computer exploit. SearchSecurity. Information Security information, news and tips.
- ^ Tim Fisher. What Is the Windows Registry?. Lifewire. Tech Untangled.
- ^ Protect yourself from tech support scams. Microsoft. Windows Security support.
- ^ Lesvirus. Lesvirus. Cybersecurity advise from France.
- ^ How To Secure Microsoft Remote Desktop Protocol (RDP) and Remote Desktop Services (RDS). TruGrid. Simplifies corporate-wide access to Enterprise Workspaces.























