LockBit ransomware (Virus Removal Instructions) - Updated Guide
LockBit virus Removal Guide
What is LockBit ransomware?
LockBit ransomware – malicious program that encrypts and leaks corporate data to public
LockBit ransomware – a virus that is borrowing tricks from other threats like REvil and Maze, so it can take ransomware attacks to the next level. Cybercriminals behind the malware use double extortion techniques to make victims pay the ransom. First, the attackers breach the company's network and begin gathering private corporate data, such as company plans, employee/customer details, private contacts, etc. Only then do the attackers deploy the LockBit virus on the network. According to reports,[1] malware is mostly striking targets in the US, the UK, France, Germany, Ukraine, China, India, and Indonesia.
Initially stemming from LockerGoga family, ransomware has also some similarities to ABCD ransomware. First spotted in October 2019, malware is still active and has already delivered several variants – some using .abcd file extension, while others – .lockbit. It locks documents, databases, pictures, videos, and other files with the help of a combination of AES and RSA ciphers, which makes it extremely difficult to recover data when no backups are available.
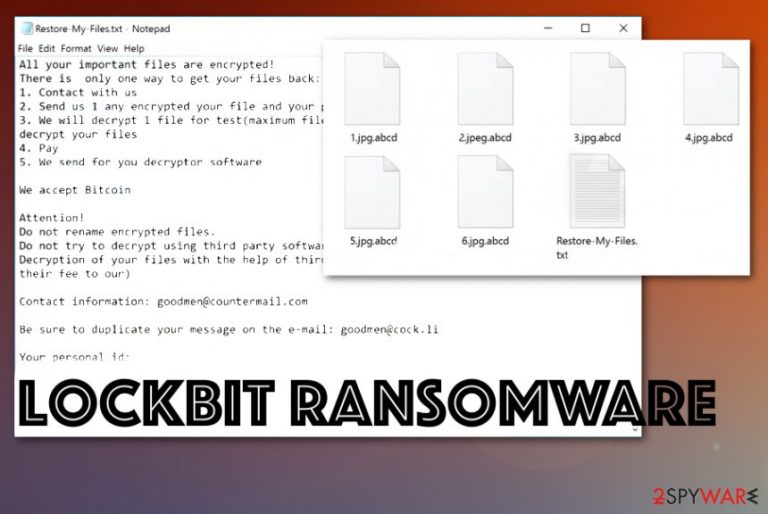
After the data locking process, LockBit ransomware also delivers a message from the attackers – it is compiled into a Restore-My-Files.txt file. Inside, it is explained that victims have to contact actors via goodmen@countermail.com, supportpc@cock.li, recoverymanager@cock.li, or another email to negotiate the price of the LockBit ransomware decryptor (in some variants, users are directed to a Tor website such as lockbitks2tvnmwk.onion instead).
| Name | LockBit ransomware |
|---|---|
| Malware family | LockerGoga/MegaCortex |
| File marker | Initial released used .abcd file extension, while later hackers started using .lockbit as well (hence the malware name) |
| Ransom note | Restore-My-Files.txt is delivered upon successful data encryption – it includes information about the infection and what victims should do to recover access to files. It also includes contact information of developers |
| Contact emails | goodmen@countermail.com, goodmen@cock.li, goodsupport@cock.li, abcd-help@countermail.com, supportpc@cock.li, pcabcd@countermail.com, recoverymanager@cock.li, etc. |
| Main symptoms | The virus infiltrates the machine and starts file-locking immediately. Once the chosen data gets encrypted and marked using the file appendix, photos, documents, archives, and videos or audio files become inaccessible. The ransom note delivered after that displays the options for file recovery, including paying the ransom |
| Distribution | Several methods can be used for malware delivery, including unprotected RDP connections, phishing emails, exploits, malicious installers, software cracks, etc. |
| Elimination | LockBit ransomware removal should be performed using a reputable anti-malware program because tools designed to detect and remove malware can find all components of the cryptovirus |
| Tips for system repair | In some cases, malware such as ransomware can negatively affect the Windows system during the infection process. As a result, an affected computer may start crashing, lagging, and suffer from other issues. To revert this damage, FortectIntego or similar repair software can be used |
| Detection names | Ransomware samples are detected by different AVs under different names, including TR/Downloader.Gen, Gen:Heur.Ransom.Imps.3, UDS:DangerousObject.Multi.Generic, Trojan.DelShad.kt, Trojan.Encoder.29662, Trojan.Ransom.Imps.3, etc. |
LockBit is known to employ a tactic called Big Game Hunting, which is used by many ransomware families. Just as LockerGoga, it's main targets include cities, high-profile corporations, as well as small businesses. The technique is so effective because larger organizations are more likely to pay a ransom without suffering major losses. Besides, the sums that are asked are adequately increased – the bigger the company, the more money the attackers can ask for.
Similarities with its predecessors do not end there, however. Before executing the infection, LockBit ransomware checks the keyboard language, and exists without causing any harm if the computer owner comes from CIS countries,[2] including:
- Russia
- Moldova
- Armenia
- Belarus
- Tajikistan
- Ukraine
- Georgia, and others.
Since the LockBit virus stems from an already established malware family, it uses a variety of techniques in order to access the system. For example, a known malware executable sh1.exe had a valid certificate, which also allowed it to bypass built-in Windows UAC (Windows Account Control) protection. Additionally, LockBit ransomware also deletes Shadow Volume Copies, disables the startup repair function, and performs other Windows changes in order to cause maximum damage, increasing the chances of victims paying the ransom.
According to information provided by VirusTotal,[3] LockBit ransomware's infectious executables can be detected by many anti-virus engines. Nevertheless, because malware has multiple variants, new releases might not initially be stoppable, even with the most recent version of security software. As a result, LockBit ransomware can access machines even with security programs enabled, so extreme caution should be practiced when dealing with unsolicited emails, establishing a Remote Desktop connection, etc.
LockBit ransomware supposedly includes another module that allows scanning the entire system for new files to encrypt once in a while (for example, every half an hour). This way the cyber threat ensures that no valuable data has been left free from encryption and increases its luck in receiving ransom payments. This is one of the main reasons why LockBit ransomware removal is so important.
After encrypting data, LockBit ransomware will intensively ask for a ransom via a text message placed on the system. Criminals claim that, by using recovery tools, users may permanently damage the locked data and the only way to recover it is by paying the ransom:
All your important files are encrypted!
There is only one way to get your files back:
1. Contact with us
2. Send us 1 any encrypted your file and your personal key
3. We will decrypt 1 file for test(maximum file size – 1 MB), its guarantee what we can decrypt your files
4. Pay
5. We send for you decryptor softwareWe accept Bitcoin
Attention!
Do not rename encrypted files.
Do not try to decrypt using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price(they add their fee to our)Contact information: goodmen@countermail.com
Be sure to duplicate your message on the e-mail: goodmen@cock.li
Your personal id:
–
LockBit ransomware supposedly keeps both encryption and decryption keys safely hidden on remote servers that are reachable only for the criminals themselves. This way, hackers decrease the victims' chances of recovering their data. However, we still do not recommend fulfilling the ransom demands, as LockBit virus developers might simply ignore requests after the payment is completed.
Besides encrypting data and providing ransom demands, LockBit ransomware might be capable of delivering other malware to the Windows computer system. It is not surprising for this to happen as malware sometimes comes in packages. For example, the notorious Djvu ransomware was known to be bundled with AZORult banking trojan.
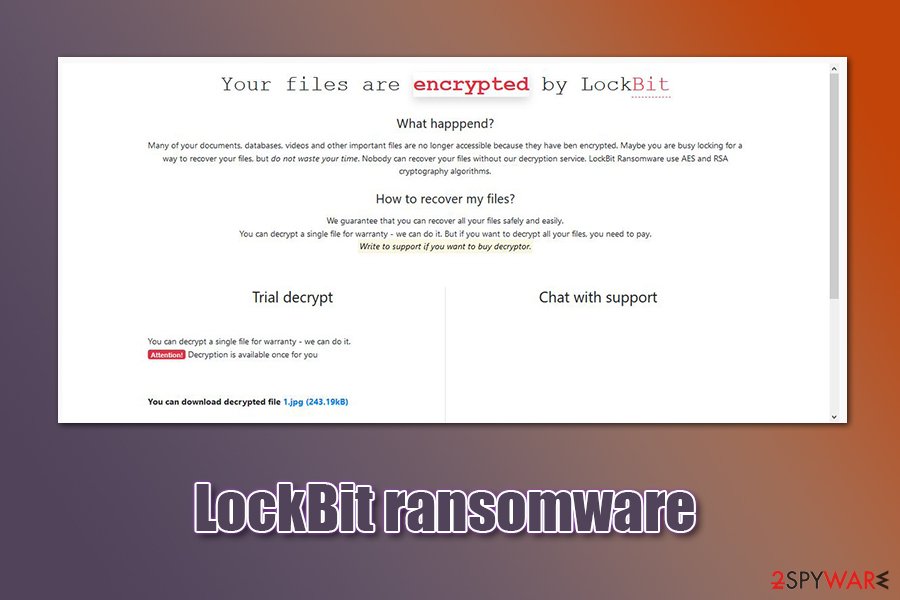
LockBit ransomware removal is the best way to avoid the risk of additional infections. You should scan your computer system with reliable anti-malware software and get rid of the threat. Afterward, if you have found some damaged components on your system, try repairing them with a tool such as FortectIntego.
After you remove LockBit ransomware from your machine, you can start thinking about possible data recovery solutions. Since malware targets corporations, ransom demands can be exceptionally high (for example, PwndLocker authors asked as much as $660,000 from one of the affected companies). Scroll to the end of the page where you will find some file restoring possibilities which might be helpful in your case.
LockBit ransomware gang: attackers merely take 5 minutes to encrypt the corporate network
Security researchers said that LockBit actors were actively collaborating with the Maze gang, which has been recently shut down.[4] It was reported that Maze's leak site was initially used to publish sensitive corporate data stolen by criminals, although, in September 2020, a separate website was created for the purpose.
Security researchers from Sophos[5] analyzed eight incidents connected to this malware strain and discovered that the infection routine is quite sophisticated and very fast. Unlike many other high-profile actors, LockBit uses automated tools in order to break into the targeted networks, although targets are carefully chosen by criminals themselves.
It was reported that cybercriminals use techniques that provide very little forensic information for investigators, as the malicious data resides in memory rather than physical drive. LockBit virus also attempts to bypass Windows 10 built-in anti-malware by applying patches to it via computer memory. Once malware breaks in, it can self-spread across the network and encrypt the most important company information. According to the report, the whole process only takes 5 minutes.
Ransomware infection methods being polished over time
As long as ransomware[6] has been spread, these malicious parasites are distributed by using the same techniques, although they are also improved with new innovations. According to security specialists from NoVirus.uk,[7] criminals use email spam as a way to distribute malware. The virus is often hidden in a hyperlink or attachment that comes looking like an ordinary shipping message from a reliable company such as DHL or FedEx.
The most important part about managing your received email is checking the sender, his/her email address, and searching the written texts for possible grammar mistakes. If the message comes from an unidentifiable deliverer or includes a lot of mistakes, you should delete it right away without even considering to open it. Also, scan all received attachments with reliable antimalware software in case the clipped document appears to be malware-laden.
Additionally, ransomware infections can get delivered via other sources such as p2p networks[8] (The Pirate Bay, eMule) that include a lot of software cracks. Also, malware camouflages as fake software updates (JavaScript, Flash Player), so better get all required program upgrades only from their official websites. Last but not least, vulnerable RDPs that do not include passwords or include weak ones are also targets of cybercriminals. 
LockBit ransomware removal guidelines
LockBit ransomware removal should be carried out only with anti-malware software, otherwise, big damage can be brought to your computer system or you might skip some crucial steps. However, you should disable malicious processes first so that the malware does not interrupt your elimination process.
You can disable LockBit ransomware processes by booting your computer system in Safe Mode with Networking or activating the System Restore feature. If you do not know how to accomplish such tasks, scroll to the end of this article and take a look at the steps provided there.
When you are ready to remove LockBit ransomware from your Windows system, make sure to check the entire machine for malicious strings. You can do that by running a full checkup with SpyHunter 5Combo Cleaner or Malwarebytes. If these antivirus programs find some corrupted components, try fixing the damage with FortectIntego software.
Getting rid of LockBit virus. Follow these steps
Manual removal using Safe Mode
To stop malicious processes on your Windows machine, apply the following guiding steps, and activate Safe Mode with Networking.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove LockBit using System Restore
To diminish malicious activity on your computer, you should enable System Restore. Apply the following steps to turn this feature on.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of LockBit. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove LockBit from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by LockBit, you can use several methods to restore them:
Use Data Recovery Pro to restore some locked data.
Try employing this software for file repair after a ransomware attack.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by LockBit ransomware;
- Restore them.
Windows Previous Versions feature might help with file restore.
Apply this feature to corrupted/locked data and you might have a chance of recovering it.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Try Shadow Explorer and restore some files.
If the ransomware virus did not touch Shadow Copies of your data, try employing this software for file recovery.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Currently, no official decryption tool has been released.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from LockBit and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Dan Goodin. LockBit, the new ransomware for hire: A sad and cautionary tale. Arstechnica. Technology and security news.
- ^ Commonwealth of Independent States. Wikipedia. The free encyclopedia.
- ^ b02d57f1c4f7f233044a56fdc57c89b6cc3661479dccc3b4cfa1f6f9d20cd893. Virus Total. File information.
- ^ Zack Whittaker. Maze, a notorious ransomware group, says it’s shutting down. Tech Crunch. Startup and Technology News.
- ^ LockBit uses automated attack tools to identify tasty targets. Sophos. Security research blog.
- ^ Ransomware. Malwarebytes Labs. Technology.
- ^ NoVirus.uk. NoVirus. Security and spyware news.
- ^ P2P. Tech Terms. Definitions.







