Android virus. Versions provided. The list of infected apps for 2021
Android virus Removal Guide
What is Android virus?
Android virus is the group of numerous malware infections that exclusively target devices running this OS
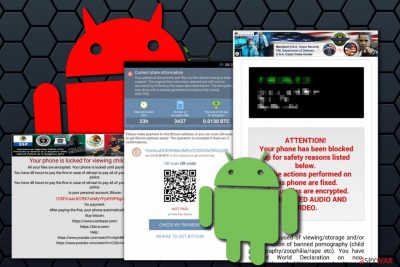
Android virus is a term used to describe a group of malicious applications targeting Android smartphones and tablets. While the mild types of infections might display intrusive ads or redirect to suspicious sites, the more severe threats like trojans, info-stealers, and DNS hijackers can take over the device completely, gain root access, download other malware and prevent its removal altogether. Keeping in mind how the infection rate keeps growing (researchers recorded 116.5 million infections in 2019 alone), how to remove adware from Android is becoming an important topic.[1]
The biggest issue is that hackers can still misuse the official stores to hide fraudulent apps inside them and infect users. Besides the regular smartphone viruses created by malicious actors, Google Play store has been used to spread potentially unwanted programs like Xender, Amber Weather Widget, Touchpal, Kitty Play, Z Camera, ES file explorer, etc.
Additionally, users are sometimes facing challenges when trying to get rid of ads that do not correlate with the application name. One such example is the Opt-Out ads, which can be related to a variety of different shady apps, typically downloaded from third-party sources.
In some cases, Android virus removal is as simple as cleaning devices' cache on Google Chrome or other installed browsers. Another more drastic option would be performing a full system reset, which would, unfortunately, delete all personal files like photos, music, videos, and other data located on the phone or tablet.
However, there is an easier way how to remove adware from Android, and it is security software. While some malware is so persistent that it gets rooted into the device and is impossible to terminate, most of the widespread threats can be shut down by anti-malware tools.
| SUMMARY | |
| Name | Android virus |
| Types of malware | Ransomware, Screen locker, Spyware, Adware, Trojan, Rootkit, Rogue apps |
| Danger level | High. Most of the virus versions are capable of locking the screen, stealing personal data, and causing money loss |
| Symptoms | Locked screen, pushy ads, encrypted files, unusual system's behavior, significant slowdown, increased telephone bill |
| Distribution method | Trojanized apps, text messages, Google Play store apps, file-sharing websites, malicious links |
| Malware list | Com.google.provision, Com.android.system.ui, Com.android.gesture.builder, Lastacloud virus, NotCompatiblev virus, Mazar malware, Smart cars-hacking Android malware, Gooligan malware, Ghost Push virus, HummingWhale virus, HummingBad virus, e, GhostCtrl virus, Invisible Man, LokiBot virus, Marcher Android Trojan, Tizi Android virus, Android Police Virus, Android ransomware, Android ransomware, Lockdroid ransomware, LeakerLocker ransomware, DoubleLocker ransomware, Matcher Trojan, Tizi spyware, vGhostCtrl, ExoBot, Xavier, 10001_1.jar, Rabbitfiles, Funnwebs.com, JavaTcmdHelper, Android ads on Lock Screen, Fake Virus Warning Android, Opt Out virus |
Ransomware can also penetrate Androids, and one of the best examples is AnubisCrypt ransomware. Not only does it lock all personal files and demands a ransom for their return, but it also locks up the screen of the phone, making it impossible to access.
There are two ways of how smartphone malware could be programmed to behave:
- trick users into granting the app elevated permissions (for example, “Display over other apps,” which could be a major cause of interstitial ads that interrupt you regularly);
- exploit vulnerabilities that are already present on an Android device (system and app updates are the primary way of repelling these invisible attacks).
Regardless of which approach is utilized by malicious actors, the ones who suffer the consequences of the virus infection are the users. There are several ways how you could stop malware from accessing your mobile device – keep in mind that your phone stores the most sensitive details about you, as you buy products from Amazon or eBay, access your online banking, and log in to social media using your credentials.
If you are careless, hackers can use this information for a variety of malicious purposes, so you should do everything to prevent the article's culprit from accessing your device. This article will explain the mobile malware's modus operandi and ways you could ensure your device stays out of cybercriminals' reach.
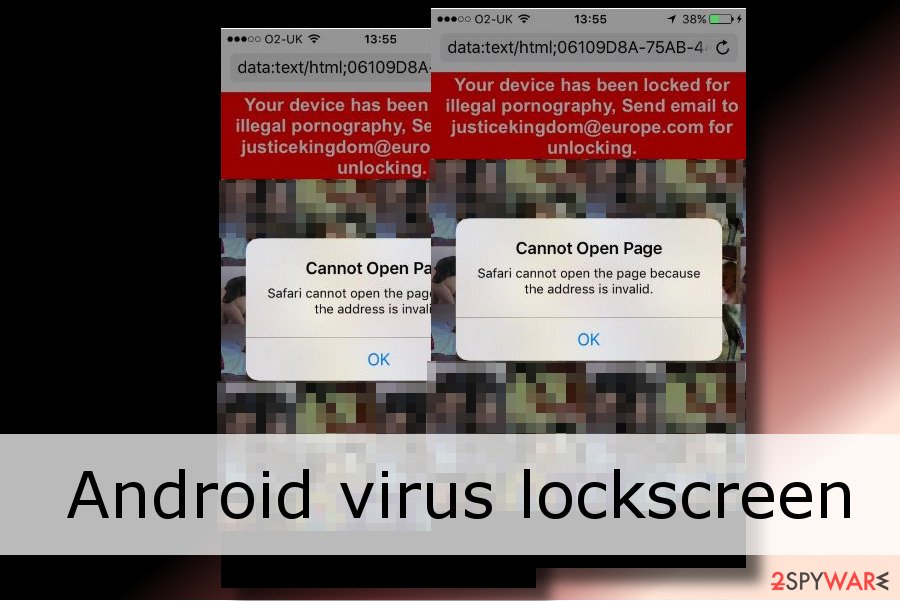
Android virus infection symptoms
Getting infected with malware is undoubtedly a frustrating experience. Pushy ads signal that there's something wrong with your Android device. Security researchers highly recommend avoiding lottery-themed and similar ads that can start interrupting you once you start using your device.
You should always be attentive when operating your phone or tablet – most malware displays little to no symptoms if not enough attention is paid to the device's operation. For example, one of the signs of infection could be that the app's icon simply dissipated after installing it.
Besides, you should pay attention to such signs as constant freezes and increased battery drain. If your phone or other Android-based device has started freezing up and stopping from functioning while you are browsing the Internet, you should install Android antivirus to check it for malware.
Possibly the most common virus infection sign is ads – and you see them everywhere, even on lockscreen. Of course, you should not confuse site-embedded ads with those that are initiated by an app (although the difference is pretty significant).
Also, pay attention to your telephone bill and track the numbers. If you have started receiving a high telephone bill, you should double-check a month's report. There is a chance that you could have been signed up for a premium service without your consent. To save money, you have to take care of virus removal on your device.
To prevent such threats, you should think about antivirus software.[2] However, some experts claim that preventing such malware does not require security apps because Android is safer than other operating systems. Still, they also agree that you need to think about prevention techniques to save yourself from such viruses.[3]
Calendar virus – a problem that has been annoying not only iPhone users
The so-called Calendar virus is a well-known scam that targets users of various calendars. While this activity was first spotted on iOS devices, Android users soon also noticed that their Calendar apps are showing suspicious activity on their devices.
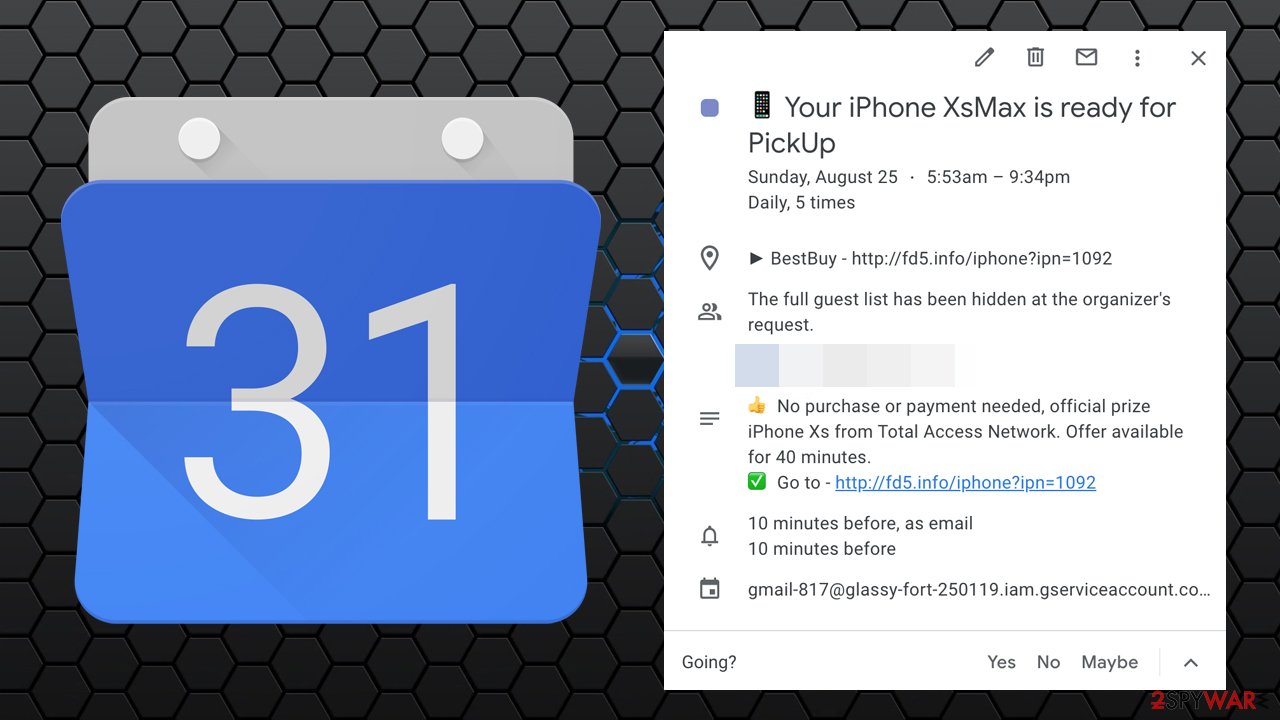
The calendar virus operation principle is intricate, as it does not need to infect the phone in order to function directly. Crooks abuse the built-in calendars, such as Google Calendar, to show users popup notifications at regular intervals. They include the deals, offers, sales, promotions, fake updates, and other types of scams that urge users to click on a provided link that comes from a predetermined set of domains. The most common URLs where victims of the Android Calendar scam are asked to click on include:
- Alert-booster.club
- Notice-iphone.club
- Important-notices.com
- Notice-cellphone.club, and many others.
Once users click on a promoted link, they are redirected to an insecure site, where users might be asked to purchase various goods, fill in their sensitive information, or install malicious programs. In other words, the Calendar virus seeks to extort money from users one way or another (stolen data can also be sold on the dark web to cybercriminals).
To avoid the Calendar virus from accessing your device, you should check for malicious emails that would include calendar invitations. Do not decline them bit simply delete the email from your inbox. Additionally, you could have also injected a malicious calendar event when clicking links on random websites. In such a case, you should eliminate the malicious calendar via Google settings.
Android virus has already infected millions of devices
Android malware has been spreading around since 2015, but it seems that they won't stop doing that in 2019 and further. Two of the most widespread members of this group showed up in November 2017. They are known as Matcher Trojan[4] and Tizi spyware[5]. The latter was found in 2015 and has been used to steal personal information from social media apps.
Among other recently discovered cyber threats, there is also DoubleLocker ransomware that emerged in October.[6] It not only encrypts files on the targeted device but changes the phone’s PIN. What is more, malware might also steal money from the victim's bank or PayPal account.
Beware that Android adware and other types of viruses can now bypass Google's security and pretend to be a helpful app in the Play Store. That was revealed when one of its variants, LeakerLocker, was spotted spreading using this technique. Other versions, such as vGhostCtrl[7], can open the system's backdoor and allow attackers to record the victim's audio/video files or steal crucial data. You should also beware of the Invisible Man app, which is used to steal banking app data and other sensitive data.

There is no doubt that Android users should pay attention to the security of their devices. In fact, almost all viruses are interested in getting personally identifiable information about the victim. Most often, this information includes credit card details, logins, and passwords.
Some variants, however, are focused on different things, such as:
- sharing victim’s contact list;
- recording conversations;
- delivering unwanted pop-up ads;
- initiating redirects to various websites;
- infecting the device with other malware.
According to cybersecurity research related to Android virus, which was held at the beginning of 2019, numerous apps distributed on Google Play Store can be infected with intrusive ads, which can be used for spreading more severe infections.
It would be best if you were also careful with the ES file explorer app, which claims to boost the phone's battery life. Instead of being functional, this application may lock the screen and display disruptive ads that refuse to go away. As a result, you will be forced to reset your device to its factory settings to remove adware from the phone.
Besides, if you noticed that your tablet or phone is behaving oddly, you should not ignore these symptoms of the possible infection. If you have been dealing with slowdowns, suspicious alerts, redirects, or received an increased telephone bill, you should check your device for malware because they are the main signs showing that you are infected.[8] To remove Android virus, you can use the mobile antivirus. You can find the best free tools in Fossbytes review.
ExoBot was titled one of the most dangerous Android viruses of 2020
Marcher Android Trojan, also known as ExoBot, is a banking malware that is known at least since 2013. Researchers reported about virus comeback in 2018 and 2019. The updated version uses three hazardous components in one campaign: malware, credential phishing, and banking data theft. Security experts warn that this version of malware is more complicated and difficult.[9]
Previously, Marcher malware was spread via SMS or MMS messages.[10] However, crooks changed the distribution method and sent a shortened link to a phishing site via email in order to avoid detection. The recent campaign has been targeting customers of Austrian banks.
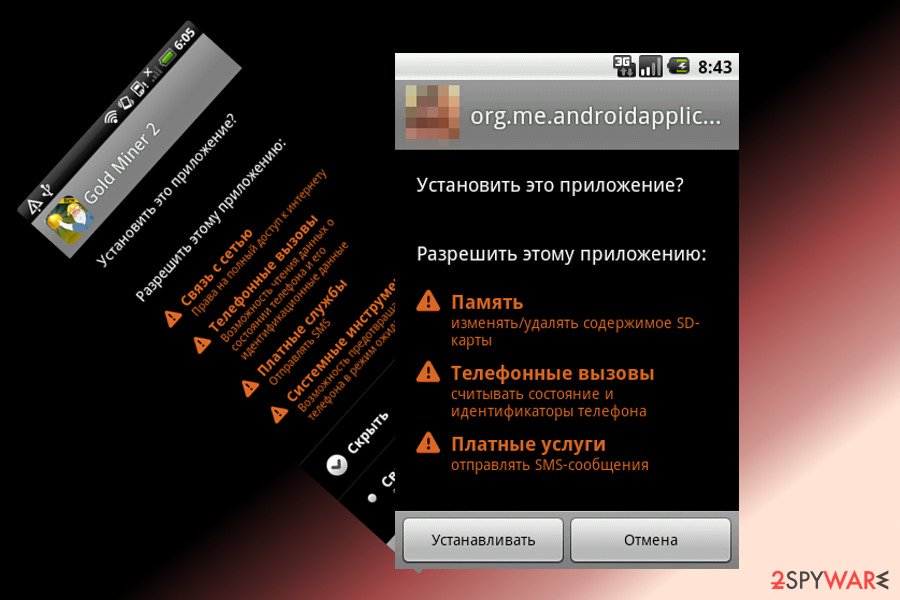
The malicious email includes a link to a fake Bank Austria website where users have to log in and enter their email address and phone number. Then attackers send a victim a warning that he or she does not have the “Bank Austria Security App” installed on the phone and asks to download it from the provided link.
However, the installation of the malicious app requires altering security settings to download it from an unauthorized source. The malware requires lots of permissions that get attackers full access to the smartphone.
Once installed, a malicious app creates a legit-looking icon on the home screen that looks similar to Bank Austria. After installing the Marcher virus, victims are asked to enter their credit card information or other personally identifiable details whenever they open any applications.
According to research, about 20,000 Android users may have suffered from this scam and installed ExoBot on their devices.
2019: Google's security firewall can still be bypassed
Most of the Android viruses can be downloaded from the Google Play store, together with safely-looking apps. No matter how much effort Google puts while protecting users and preventing these malicious apps from bypassing their security, viruses find a way to this store.
In February 2016, one of the variants was noticed spreading via text messages.[11] Once inside the system, it enabled illegal connections. In 2017, security experts reported a list of over 75 applications infected with Xavier Android virus found on the Google Play Store. However, it’s not the only way how this virus can infect the device.
In 2018, security experts reported several variants of this malware using sophisticated social engineering techniques to infiltrate the device via trojanized apps. Therefore, you should be careful when installing third-party apps because they can be infected with the 10001_1.jar virus.
You can also get Rabbitfiles virus or similar malware from third-party or file-sharing websites. Besides, Whatsapp ads and similar notifications can also result in problems related to your phone. It's clear that 2019 means a new era for Android viruses. If in 2018 one in ten apps was infected, after several years, this number continues growing.
The list of infected Android apps (malware list)
JavaTcmdHelper virus
JavaTcmdHelper virus is one of the applications that cause issues on Android phones and can often be detected as dangerous by antivirus programs.
This application doesn't show up on the phone or even in the Settings or Application sections. However, users have reported system messages stating that Javatcmdhelper is possibly dangerous. The message may also state about the app that behaves unusually or has privacy risks.
Java tcmd helper virus can be detected by your anti-malware tool or security app. Still, the name depends on a particular virus database and may differ from program to program.
The most common heuristic name is Artemis!7123f6c80769 or Artemis!f580cadc3dc1. Because of this, it gets called Artemis/JavaTcmdHelper virus by various users.
Funnwebs.com
Funnwebs.com is yet another adware-type program that targets Android phone users. This intruder lures people using social engineering tactics to subscribe for notifications this website delivers to your screen.
Unfortunately, like many other adware-type programs, this threat also creates tons of commercial content that fills up the screen of your phone. It also redirects to commercial sites, affiliated pages or delivers your traffic to links like reward3977.xzprize43.life.
Various notifications about the possible threat can be caused by this website or related programs that expose the user to possibly malicious content.
Com.google.provision
Com.google.provision virus operates as the malicious script which downloads and installs unknown applications into Android system. Unfortunately, the infection does not target smartphone users but has its variations occupying PC and tablet devices.
Since the introduction of the Device Administration tool on Android 2.2, this malware has more chances to rampage on the system. It is tough to detect it on your own, so we don't recommend that.
At the moment, the only trustworthy method to delete the virus is to install a mobile version of the malware elimination tool and eradicate it. Unfortunately, factory settings reset does not help terminate infection, but you can try.
Com.android.system.ui
Com.android.system.ui malware is another version of Android virus that seeks to mislead users into visiting insecure websites and shady applications. Most usually, it manifests a tendency to install unwanted software into a device as well. Scan the device with a malware elimination tool and check the list of system apps.
Com.android.gesture.builder
Com.android.gesture.builder virus is also programmed to install potentially malicious apps on the systems. Be wary of the content and apps you download other than the Google Play store. On the other hand, past incidents reveal that it is not safe to download apps even from the mentioned store. Therefore, having a malware elimination tool becomes more relevant than ever before.
NotCompatible virus
NotCompatible virus is a dangerous Android virus that acts as a proxy. As soon as it gets into its target system, it connects to its server and waits for specific commands. There have been many speculations that this malware can connect affected devices into a botnet and then turn them into spam machines.
Some security experts have warned that NotCompatible malware can easily be used to steal personal information from the phone or similar device. To protect yourself from these issues, we highly recommend you download mobile antivirus. It will help you to prevent the infiltration of such and similar threats.
Lastacloud virus
Lastacloud virus is a trojan horse also known as Android.Lastacloud. It has been actively spread as updates for WhatsApp and Android Browser that present themselves as Updatecom.whatsapp.update and com.androidbrowser.update. Once inside the device, this threat seeks to steal personal information, such as contact lists, accounts that are accessed through the device by the victim, internal and external storage, and similar data.
It can also try to infect the system with other cyber threats. Almost each of the reputable antivirus programs can help you to remove Lastacloud virus from the system. Please, do NOT postpone its removal because this virus can lead you to severe problems.
Android Police virus
Android Police Virus is a newly-designed version of FBI virus, which is capable of infecting smartphones. Today, it is the most dangerous example of this OS malware because it can block the entire system and encrypt each of the installed files.
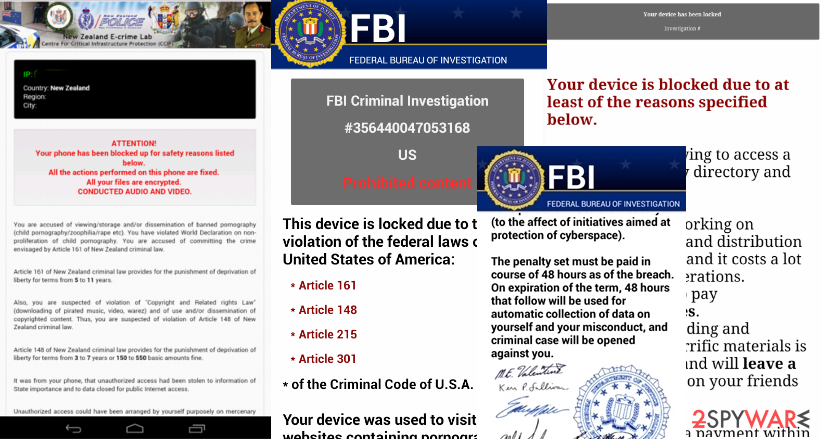
Also, it can cause warning messages and redirects to malicious websites seeking to make people pay the ransom for its developers. It is hard not to notice the infiltration of this virus. If you are infected, you should avoid visiting websites that require adding your logins and passwords. Of course, you need to remove Android malware ASAP.
Android ransomware
Android ransomware is a malicious mobile phone threat that uses a clickjacking technique to get admin rights on the victimized device. However, it can also infiltrate the device through malicious apps, such as Porn ‘O’ Mania. To avoid infected apps, you should use only official stores, such as Google Play and Appstore.
Once the ransomware infects the system, it encrypts the victim's files and locks them down. It also threatens the user and claims to share the victim's data and browsing history with the people on the contacts list. You must remove this virus immediately.
Svpeng virus
Svpeng virus is Android ransomware that was introduced in 2014. However, it seems that it is still active – in 2018, smartphone users are still stuck on this virus which can cause severe problems on their phones and tablets. What does this malware cause?
It is a typical “lockscreen” parasite that blocks the phone's screen with a fake warning message from the FBI. In reality, people who are working behind Svpeng ransomware do not have any connections to the FBI. They are seeking just to trick their victims into paying the fake ransom. Please, do NOT fall for these claims. You need to remove Svpeng from the system by resetting your device to factory settings.
Mazar malware
Mazar malware is not a traditional version of an Android virus. This threat spreads via text messages that are filled with infected links. Once the victim clicks such a seemingly legitimate link, the OS gets infected with the malicious software that starts running dangerous activities behind your back.
Typically, it starts monitoring the phone or tablet, changes its settings according to its needs, sends SMS to premium numbers, and initiates illegal connections via the Internet. Those who are connected to it are granted administrator rights, so they can do whatever they want. There is no doubt that you must remove Mazar virus from your device. Otherwise, you can lose your banking data and similar information.
Smart cars-hacking Android malware
Smart cars-hacking malware was introduced by virus researchers at the end of November 2016. According to the company, which is known as Promon, it was used by them to hack into the official application of Tesla that allows finding the car, opening its doors, and starting the engine.[12]
To perform these commands, Android malware modifies the source code of the official Tesla app at first. Then, it shares the victim's username and password with the attackers and helps them steal the car. However, the virus, which Promon researchers tested, does not rely on any security vulnerabilities of the Tesla app. According to the company, it has to be installed manually with the help of social engineering and similar techniques.
However, the virus, which Promon researchers tested, does not rely on any security vulnerabilities of the Tesla app. According to the company, it has to be installed manually with the help of social engineering and similar techniques.
Ghost Push virus
Ghost Push virus is a notorious malware capable of infecting all Android devices using versions below Nougat (V7). The malicious actor functions as a rootkit – it is capable of performing various malicious activities without users' permission. For example, the most prevalent symptom of the infection is downloading and installing other malicious applications and spamming ads non-stop. The advertisement gains revenue for hackers, and it is believed that they earn around $4.05 million a day.[13]
Unfortunately, getting rid of Ghost Push is almost impossible. Even factory reset does not do the job, and reflashing firmware would be the only choice for users. However, the good news is that those who are using Nougat, Oreo, and Pie should feel relatively safe, as those versions of the OS are protected from this type of malware. Nevertheless, it does not mean that hackers will not create new variants that would defeat protection measures in the latest versions of Android.
Gooligan malware
Gooligan malware has corrupted over 86 applications, such as Youtube Downloader, Kiss Browser, Memory booster, Demo, Perfect Cleaner, Battery Monitor, System Booster, etc.[14] It seems that all system performance and browser-related programs and gaming, as well as pornographic applications, risk becoming the carriers of Gooligan. Over 74% of all Android phones might be vulnerable to this new version of the virus.
After the infection process is complete, the malware roots the device and enables full access to install more malicious elements. Such activity is done for the sole purpose of stealing your personal information, such as login data to banking accounts.
Interestingly, Ghost Push virus, which hit the stage last year, provided a foundation for the current malware. Needless to say, the improved version is much more treacherous.
HummingWhale virus
HummingWhale virus – this malicious virus is an updated copy of HummingBad malware which is known for its massive attacks against smartphone users. Back in 2016[15], this virus managed to wreak havoc on approximately 10 million Android devices. Recently, HummingBad appeared in a new form and a new name, and this time it is dubbed HummingWhale malware.
HummingWhale malware was apparently available on Google Play Store for a while in the form of 20 various applications, most of them being called [random word] Camera. Examples include Rainbow Camera, Whale Camera, Ice Camera, Hot Camera, and similar applications.
The malware used to set up a virtual machine on the infected device, stealthily install extra applications on the device and serve annoying advertisements for the user. Once the user closed an ad, the malware uploaded already installed the shady program to the virtual machine to create a fake referrer ID used to generate revenue.
HummingBad virus
HummingBad virus. First discovered in February 2016, malware has already infected more than 10 million Android users. The malware had been spreading via “drive-by download attacks, ” and users got infected after visiting particular malicious websites. In January 2017, the malware was spotted actively spreading again on the Google Play store as HummingWhale application.
After infiltration, the malware gets access to the core of the smartphone’s operating system. Then, it starts delivering misleading ads and displaying alerts about necessary system updates. When users click on these advertisements, developers of the application generate revenue. However, it’s not the main problem.
Malware also gets full access to the infected device and can steal users’ private information, such as contacts, logins, credit card, or banking information. For this reason, it’s crucial to remove HummingBad as soon as it shows up on the device.
Lockdroid ransomware
Lockdroid ransomware, also known as Android.Lockdroid.E spreads as a pornography app “Porn ‘O’ Mania”. The virus uses social engineering techniques to get the admin rights of the infected device. It aims to achieve this goal by using a fake package installation. As soon as the installation is completed, Lockdroid virus gets full access to the device and encrypts data.
What is more, it can change the PIN and lock the device. In this way, malware elimination might become difficult. It uses the clickjacking technique and attacks smartphones and tablets with Android 5.0 or newer OS versions. According to Google[16], this malicious app cannot be downloaded from the Google Play Store.
GhostCtrl virus
GhostCtrl virus exploits a vulnerability to help its owners to get control over the device. It showed up in the middle of 2017 when it was found attacking Israeli hospitals, but it is not considered a new virus. However, according to some of the security experts, malware is not going to stop – soon, it can become a ransomware-type threat as this virus has also been found to have some locking capability as well.
It spreads, presenting itself as a legitimate app, such as WhatsApp and Pokemon Go. Once inside the system, GhostCtrl malware drops a malicious Android application package (APK) and opens the backdoor of the system to provide full access to the victim's personal information, videos and audios. It can also reset passwords and call or send texts to the victim's contacts.
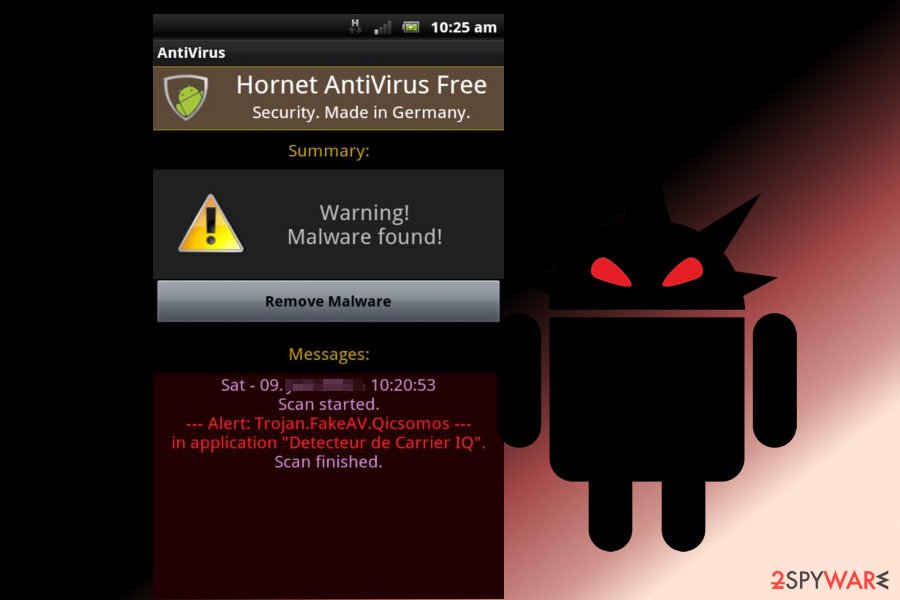
Invisible Man
In July 2017, security experts discovered an updated and improved variant of Svpeng attacking banking app users in 23 countries and dubbed it Invisible Man.[17] The virus spreads as a fake Flash Player app in suspicious and insecure download websites. Fortunately, malware hasn't made it to the Google Play Store.
However, when users install this malicious app, they give administrator rights to the device. As a result, cybercriminals can control it via the Command and Control server.
The malicious program works as a key-logger and collects credentials when a user logs in to the bank via a mobile app. Besides, Invisible Man malware can send and read messages, make and listen to phone calls, open phishing URLs, and collect various information. It also prevents victims from removing its administrative rights, so its removal becomes complicated.
LeakerLocker ransomware virus
LeakerLocker ransomware virus. In the middle of August 2017, malware researchers discovered LeakerLocker spreading via two apps available on Google Play Store. The malicious application was hiding under Wallpapers Blur HD” and “Booster & Cleaner Pro” apps.
One user's installed one of these programs, the malware locks the device's screen with a threatening message. According to it, this version of Android malware gained access to sensitive data. If the victim does not pay the ransom within 72 hours, all the information will be leaked.
However, security experts doubt that malware can cause such damage and recommend eliminating LeakerLocker from the device with security software.
DoubleLocker ransomware virus
DoubleLocker ransomware virus. In September 2017, malware researchers spotted a new version of mobile malware. It spreads as a fake Adobe Flash update. After the attack, it locks the device by replacing the PIN. Then it launches data encryption and demands to pay 0.0130 Bitcoins to unlock the device and recover files.
Additionally, malware might also steal money from PayPal and banking accounts. Therefore, the removal of the virus should be performed ASAP. However, non-routed device owners might need to factory-reset infected phones to unlock them. Routed device users can use the Android Debug Bridge (ADB) tool. Further, DoubleLocker removal has to be completed with security software.
LokiBot virus
Infostealer.Lokibot is a malicious application designed for Android smartphones. Once it gets on the victim's device, it becomes capable of sending SMS messages and replying to them, use mobile browsers, address particular URLs and install the SOCKS5 proxy.
As a result, the victim's outgoing traffic can be redirected. The virus can also compose and display fake notifications for the user, prompting the victim to open a bank account. As soon as the victim does so, the virus loads a fake overlay of the login page and collects all login details that the victim enters into the provided fields.
The extent of this Trojan virus is growing rapidly because it is being sold on dark web forums for approximately $2000, meaning that any wannabe criminal can buy it and distribute it.
In October 2017, LokiBot malware became capable of becoming a ransomware virus. However, this feature becomes active only in case the victim detects Infostealer.LokiBot and attempts to delete it. The malicious app fails to apply encryption on the victim's files but displays a screen-locking message anyway. The “Go_Crypt” function doesn't encrypt data but renames it anyway.
The screen-locking message says, “Your phone is locked for viewing child p0rnography,” and demands a payment of $100 within 48 hours. Otherwise, according to the virus, the case “will be handed over to the police.”
Marcher Android Trojan
Alternatively known as ExoBot, the virus is known since 2013. However, in November 2017, researchers reported on a massive campaign that started in January of the same year. The virus aims at Bank Austria users and tricks them into installing fake “Bank Austria Security App.” The recent version of the Marcher virus uses clever social engineering techniques to steal sensitive users' information, including banking credentials, date of birth, name, and other personally identifiable information.
Marcher distribution campaign is complicated. It brings malware to the smartphone, tries phishing credentials and stealing banking information, and finally emptying the victim's bank account. The biggest trick is that attackers use the original Bank Austria design and interface. Users are advised to stay away from suspicious emails or SMS messages from this bank and check necessary information directly from the bank's website without clicking provided links in the phishing email.
Tizi Android virus
Google reported about Tizi Android virus in November 2017. The threat works as spyware and is designed to steal personal information from social media apps, including Facebook, LinkedIn, Skype, WhatsApp, etc. Malware might also record calls, access SMS, take pictures, and complete many other tasks that put user's privacy at risk.
Tizi virus might also get root access by exploiting system vulnerabilities or tricking a user into giving such permission during the installation of a malicious app. Some of the infected apps were available on the Google Play Store in 2015. However, the majority of them are spreading via third-party apps. At the moment, Google reports that about 1.300 smartphones were infected with this spyware.
Android ads on Lock Screen
Android ads on Lock Screen are something phone manufacturers or operating system developers never include in the package when you purchase your device. Additionally, Google bans[18] apps display ads on lock screens unless it is a lock screen replacement app.
Therefore, if ads on Lock Screen appear every time you enter it, it is the potentially unwanted application that is causing the issue. Therefore, if you installed lock screen replacements recently, make sure you uninstall them to remove Android ads on the lock screen.
Known applications that can cause ads on the lock screen include:
- UC Browser
- VideoShow video editor
- Photo Editor Pro
- Solo Launcher
- Z Camera
- HiFont
- Battery Doctor
- Xender, etc.
Unfortunately, it can sometimes not be obvious which app compromises your lock screen, especially if many of them are installed. To find out which application is causing the unwanted activity and remove adware from Android, check the download list, as well as a section in your system settings that displays what permissions are granted to which apps.
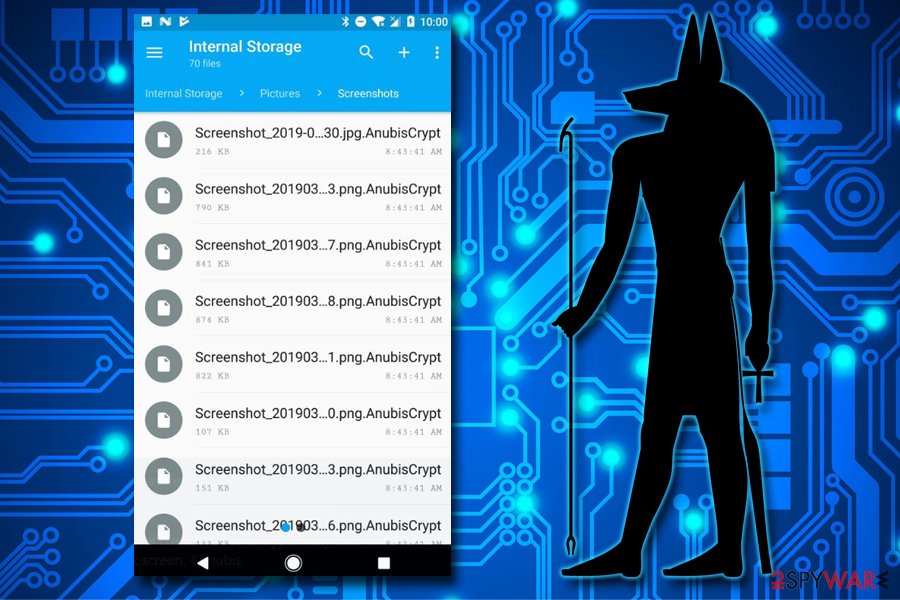
Anubiscrypt ransomware
Anubiscrypt ransomware first showed up in April 2019 when an ESET security researcher spotted the virus on Google Play.[19] The threat is not only capable of encrypting all pictures, videos, music, and other personal files but also permanently locking the phone screen, preventing its access.
Besides that, Anubis malware is also can perform the following on the host device:
- Steal victims' PayPal, eBay, Amazon, and other credentials;
- Intercept SMS;
- Log all keystrokes;
- Grant remote access to hackers.
If that would not be impressive enough, Anubiscrypt ransomware uses motion-based evasion techniques, making its detection and removal an extremely complicated task. Nevertheless, security software should be able to perform it without too many difficulties, as long as it is fully updated to its most recent version.
Agent Smith virus
Another version of the Android virus has reached the surface recently. This cyber threat was discovered at the start of July 2019. Experts found out that this new malware string aims to attack devices by planting fake copies of legal applications.[20] The main goal of this activity appears to be related to advertising campaigns.
The number of victims has already reached 25 million! Users are easily tricked by the legitimate-looking popular games and apps when the Agent Smith malicious component is truly hidden in them. This threat has good skills in hiding itself by appearance as a legal product from Google, e.g., Google Updater, and similar.
The main thing that allows skipping app security measures is the Janus vulnerability[21] which Agent Smith misuses. Even though this threat is mostly used for ad distribution, it can relate to the swindle of personal information or banking credentials. Hence, users need to be extremely careful if they have spotted malware in their devices. The virus can be found in applications such as:
- com.whatsapp
- com.lenovo.anyshare.gps
- com.mxtech.videoplayer.ad
- com.jio.jioplay.tv
- com.jio.media.jiobeats
- com.jiochat.jiochatapp
- com.jio.join
- com.good.gamecollection
- com.opera.mini.native
- in.startv.hotstar
- com.meitu.beautyplusme
- com.domobile.applock
- com.touchtype.swiftkey
- com.flipkart.android
- cn.xender
- com.eterno
- com.truecaller
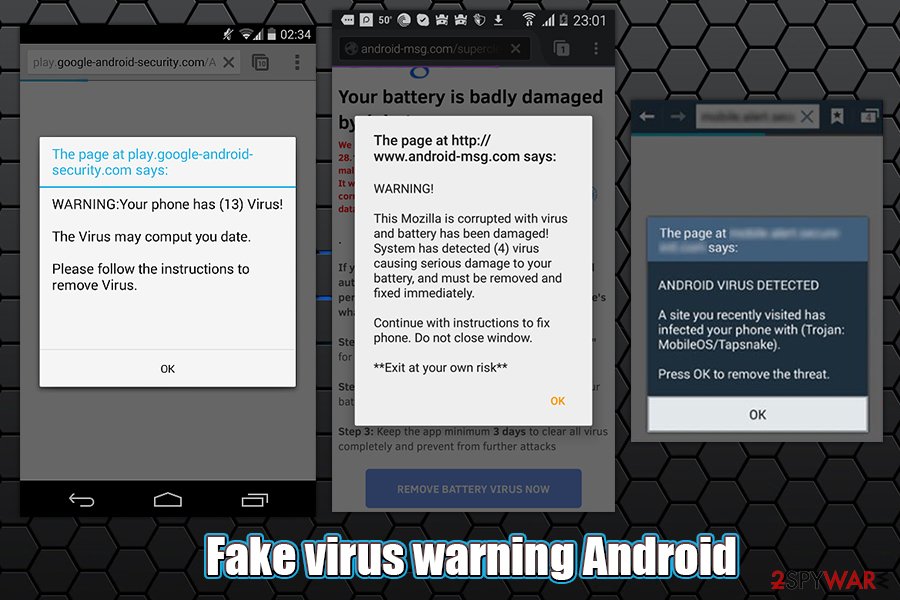
Fake virus warning Android
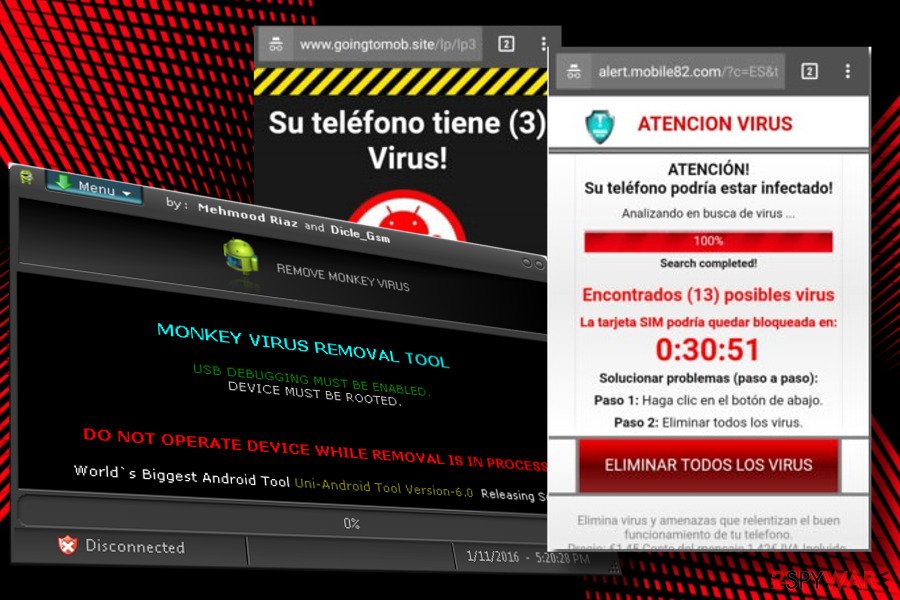
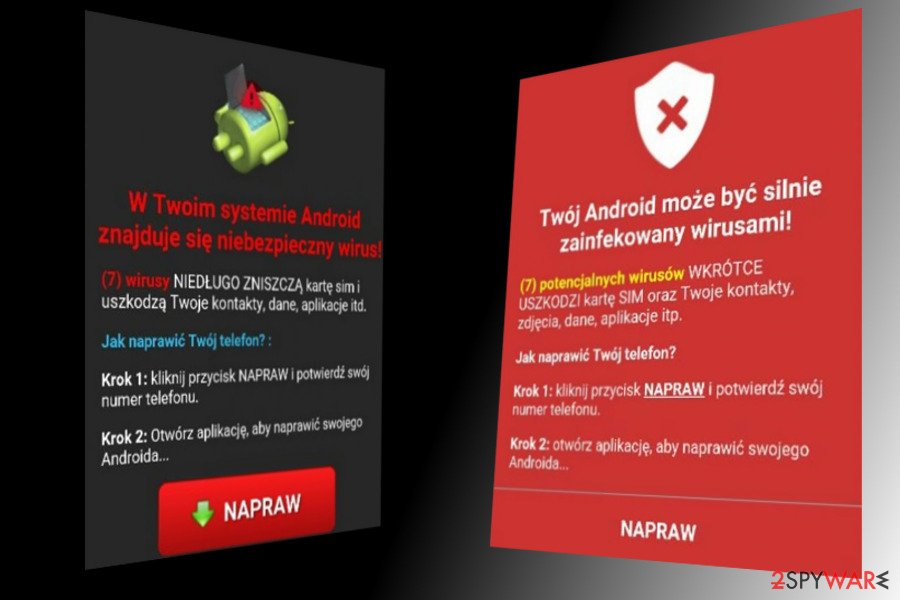
Fake virus warning Android is a rather generic term used to highlight a particular pop-up, alert, notification, or another type of ad which claims that the device is riddled with malware. While in some cases, users can encounter fake virus alerts on a malicious site by accident, Google Chrome, Mozilla Firefox, or another web browser redirects to such domains might indicate an infection or that notifications were enabled from a shady website.
To remove Fake virus warning, you should first check your phone or tablet for unwanted applications that you might have installed unintentionally. However, some apps might be relatively deceptive, and determining which one is the culprit is relatively complex, especially if you download them from unofficial sources. Therefore, malicious and unwanted apps can be easily detected by anti-malware software designed for Android devices, so we recommend performing a full system scan in such a case.
As mentioned previously, another reason for such messages might be the enabled notifications via a particular site. Even if you believe you never did, in some cases, these buttons can be disguised and, as soon as clicked, subscribe to a user to receive notifications. Since users are not familiar with the feature, they are unsure how to stop the pesky pop-ups. If you are using Google Chrome on your phone, follow these steps to remove fake virus warnings:
- At the top-right corner of the browser, tap on three vertical dots
- Select Settings
- Now go to Notifications
- At the bottom, you will find a list of websites that notifications are enabled for
- Deselect everything you do not recognize
- Unwanted notifications should be gone!
Keep in mind that you should never click on Fake virus warning Android alerts, as you might be tricked into downloading malicious software, disclosing your sensitive details, or subscribing for a useless service that you will be automatically charged for.
Opt Out virus
Opt out virus is one of those pesky infections that users simply can't get rid of, and some are even forced to perform a factory reset. Users reported that they started receiving pop-ups, interstitial, auto-play, and other annoying ads seemingly out of nowhere. To make matters worse, these notifications are often hindering the background of the display and show up over all other apps, as well as the user interface (UI) components such as a keyboard. If the marking is clicked, users are redirected to a rogue optout.tracker.ared.re/optout/mobile= URL, where they are asked to download another suspicious application. Please do not download anything that Opt out virus suggests, as you might infect your smartphone with more adware or even malware.
Mobile devices are intricate systems nowadays with thousands of different configuration settings, app permissions, and other peculiarities – it is very easy to get lost when dealing with such threats. To get rid of it, users should determine which app is causing suspicious ads, although sometimes it might be more complicated than it seems. In most cases, the culprit is coming from a third-party site, so in case you recently downloaded something from such sites, uninstall it immediately.
Additionally, you could also go to Settings > Apps > Advanced/three dots at the top-right of the screen > Special app access > Display over other apps, and check which apps have the permission to display over different applications and the US components.
Mobile viruses mainly spread via free third-party app stores
Android viruses have been actively spread via third-party apps that have to be installed on the phone manually. However, new methods used for distributing these threats have started spreading around, and today you can get infected with this malware by clicking on the malicious link as well.
In most cases, people download this threat to their devices in a bundle with unlicensed or experimental apps that are actively promoted on the Google Play store and similar locations.
To avoid this, we highly recommend you download your apps only from legitimate app stores that check every program before they start promoting it. Google Play Store, Amazon, and Samsung can be trusted in this case. Besides, even if you select any of these app stores, you should still double-check the app before downloading it to your device because you can never know what kind of malware is hiding in it.
If you are interested in cybersecurity, you must have already heard about hackers who managed to add their malicious app to the Google Play store and collected more than 10.000 downloads before it was revealed.[22] Also, it has been reported about affected websites that automatically download an infected app to your phone.[23]
To keep your device clean and ensure protection against malware, you should stop visiting suspicious/illegal sites and never click links that may show up for you while visiting them. Finally, we believe that it is time to think about mobile antivirus that could help people prevent the installation of malicious apps.
General Android virus removal guide
If your device is infected with a virus, you can run into these problems:
- The loss of sensitive information. Malicious apps that are used to infect smartphone OS can collect different kinds of data. Such information includes contacts, logins, e-mail addresses, and similar information that is important for attackers.
- Money loss. Most Android viruses are capable of sending messages to premium-rate numbers or subscribing users to premium services. This can lead you to money loss and similar issues.
- Infiltration of malware. The virus can try to take over your device and infect it with other malware. It can also cause annoying ads, pop-up alerts, and fake warning messages.
- Performance-related issues. When infected with such a threat, you may notice system instability problems, slowdowns, and similar problems.
If you think that your device is infected, we highly recommend you scan it with Android virus cleaner. There are plenty of security programs available on the Google Play store. It will help you detect malicious files and other fraudulent components on your device.
Sometimes viruses block security software in order to avoid their elimination. If that is the case, you should reboot your Android device into Safe Mode before launching your antivirus to disable third-party apps (and malware as well) from running:
- Find the power button and press it for a couple of seconds until you see a menu. Tap the Power off.
- Once you see a dialog window that offers you to reboot your phone to Safe Mode, select this option and OK.
If this failed to work for you, just turn off your device and then turn it on. Once it becomes active, try pressing and holding Menu, Volume Down, Volume Up, or Volume Down and Volume Up together to see Safe Mode. If that doesn't work, search the phrase “How to put into Safe mode” and add your phone's model. Then, follow the instructions.
You can also try to perform Android virus removal manually by uninstalling the malicious app yourself. However, you should be very careful when trying to do so because you may remove useful files and apps from your device. For manual removal, please follow these steps:
- Reboot your device into Safe Mode with the help of the steps that are given above.
- When in Safe Mode, go to Settings. Once there, click on Apps or Application manager (this may differ depending on your device).
- Here, look for the malicious app(s) and uninstall all of them.
We also recommend turning off the option that allows installing apps that belong to unknown sources. For that, go to Settings -> Security. Once there, turn off this option.
The factory reset might be needed to remove Android malware
If nothing helps you remove Android malware from your phone or tablet, you should reset it to its factory settings. For that, you need to perform these steps:
- Click the Settings icon on your device. You can find it among other apps.
- Select Privacy (or Personal) and Factory reset (you can also find it as Factory data reset, Backup & reset, etc.). We recommend selecting Back up my data to protect it from loss.
- Click Reset device to remove malware and other storage from your device.
How to prevent from getting malware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Anthony Spadafora. Mobile malware attacks double in 2018. Techradar. The source for tech buying advice.
- ^ Joe Hindy. 15 best antivirus Android apps and anti-malware Android apps. Android Authority blog.
- ^ Ryan Whitwam. Android antivirus apps are useless — here’s what to do instead. ExtremeTech. Answers to the unanswerable questions of technology.
- ^ Danny Palmer. Android security triple-whammy: New attack combines phishing, malware, and data theft. ZDNet. Breaking news, analysis, and research keeps business technology professionals in touch with the latest IT trends, issues and events.
- ^ Anthony Desnos, Megan Ruthven, Richard Neal, Clement Lecigne. Tizi: Detecting and blocking socially engineered spyware on Android. Google Security Blog. The latest news and insights from Google on security and safety on the Internet.
- ^ Swati Khandelwal. New Ransomware Not Just Encrypts Your Android But Also Changes PIN Lock. The Hacker News. Cyber Security and hacking news.
- ^ Danny Palmer. This scary Android malware can record audio, video and steal your data. Zdnet security.
- ^ 3 signs you have an Android virus. KimKomando. America's digital goddess.
- ^ Credential phishing and an Android banking Trojan combine in Austrian mobile attacks. Proofpoint. Advanced cyber security solutions.
- ^ Pham Duy Phuc, Niels Croese, Han Sahin. ExoBot (Marcher) - Android banking Trojan on the rise. CSD by SfyLabs. Android malware detection.
- ^ WARNING: If you have an Android smartphone, do NOT open THIS deadly text message. Express.co.uk.
- ^ Lars Lunde Birkeland. Tesla cars can be stolen by hacking the app. Promon blog.
- ^ Get Infected with Ghost Push? Don’t worry, here’s the fix!. CheetahMobile. Mobile internet compan.
- ^ More Than 1 Million Google Accounts Breached by Gooligan. Check Point Threat Research.
- ^ Oren Koriat. A Whale of a Tale: HummingBad Returns. Check Point. Threat Research Archives.
- ^ Google: No-one installed Lockdroid apps. IT PRO. IT Analysis and Business Insight..
- ^ Linas Kiguolis. “Invisible Man” Android banking malware spreads as Flash Player. 2-spyware. Latest news about spyware, malware and their removal.
- ^ Ryan Whitwam. Google finally bans apps that include shady lock screen ads from the Play Store. Android Police. Android news, reviews, apps, games, phones, tablets.
- ^ Lukas Stefanko. Crypto-Banking Ransomware found on Google Play. Twitter. Social network.
- ^ Natasha Christian. ‘Agent Smith’ infects 25 million Android devices globally through WhatsApp, Opera and SwiftKey clones. News. About nowadays technology.
- ^ New Android vulnerability allows attackers to modify apps without affecting their signatures. Guard Square. Mobile Protection Application.
- ^ John Zorabedian. Google takes down fake anti-virus app that duped 10,000 users on Play Store. Naked Security. Sophos blog.
- ^ Daniel Van Boom. 10 million Android devices reportedly infected with Chinese malware. Cnet Magazine.
