TeslaCrypt virus (Removal Instructions) - 2021 update
TeslaCrypt virus Removal Guide
What is TeslaCrypt virus?
TeslaCrypt ransomware is an infection that gets updates and keeps encoding users files
TeslaCrypt is a dangerous ransomware-type infection that was first discovered in February 2015 and employed AES, RSA, and ECHD algorithms. Currently, the most notorious versions of this crypto-malware are TeslaCrypt 2.0, TeslaCrypt 3.0, TeslaCrypt 4.0 , and TeslaCrypt 4.1b. However, it continues to be updated and the newest variant of this cyber threat is Teslacrypt 2.x.
Files encrypted by the ransowmare contain .xxx, .vvv, .ccc, .ttt, .micro, .ecc, and other extensions. Criminals leave HELP_RESTORE.HTML, RECOVER[5 random symbols].html, and howto_recover_file.txt ransom notes to inform about the ransomware attack. Even though earlier the contrivers of the malware have released a free decryptor, it might not be suitable for the newest variant. Thus, users are advised to stay cautious.
Similar to its predecessors Cryptowall, Cryptolocker, Simplelocker, and Threat Finder, the ransomware arrives at the system with the help of spam. Once it drops its files onto the target computer, the file virus checks it for sensitive information, such as the following:
- specific files;
- business documents;
- videos;
- pictures;
- etc.
| Name | TeslaCrypt |
|---|---|
| Type | Ransomware |
| Danger level | High |
| First discovered | February 2015 |
| Extensions | .ccc, .xxx, .vvv, .ttt, .micro, .ecc or no extension used at all |
| Ransom notes | HELP_RESTORE.HTML; RECOVER[5 random symbols].html; howto_recover_file.txt |
| Cryptography | RSA; AES; ECHD |
| Distribution | It can infiltrate the system via infected spam email |
| Decryptable | You can find a free decryption tool at the end of this article |
| Removal | Before proceeding to data recovery, you must uninstall the ransomware. For that, download the anti-malware program and clear all the detected pieces |
| Repair | The system can get recovered after the infection with tools like FortectIntego |
Beware that the virus can also try to encrypt your games and their files. It is known that it has already affected PC users who were playing the following computer games:
- World of Tanks;
- World of Warcraft;
- StarCraft;
- Minecraft;
- Dragon Age;
- RPG Maker;
- Steam.
For disabling its victims from the use of their data, TeslaCrypt ransomware uses a strong algorithm known as AES encryption[1]. As a result, all extensions of affected files are changed to .vvv, .ccc, .ecc, and similar suffixes. However, experts detected that this is not the only algorithm used by ransomware. Additionally, it has employed RSA and ECHD ciphers for data encryption.
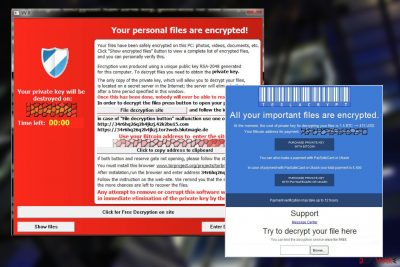
You know that you have infected with this ransomware when you find a file called howto_recover_file.txt on your computer's desktop. After clicking it, you should see such a warning message but it might differ depending on the version of this virus:
Your files have been safely encrypted on this PC: photos, videos, documents, etc. Click “Show encrypted files” Button to view a complete list of encrypted files, and you can personally verify this.
Encryption was produced using a unique public key RSA-2048 generated for this computer. To decrypt files you need to obtain the private key.
The only copy of the private key, which allow you to decrypt your files, is located on a secret server in the Internet; the server will eliminate the key after a time period specified in this window.
Once this has been done, nobody will ever be able to restore files…At the time of research, the TeslaCrypt virus distribution method was unknown, however, following successful infiltration on computer systems, the software scans all drives and encrypts certain file types using AES encryption. Encrypted files will have the .ecc extension applied to the filename.
As you can see, this ransom note by this virus claims that the user has to pay a fine of $500 or even $1000[2] in exchange for TeslaCrypt decryption key that is needed to unblock the affected information. This payment should be sent via PayPal My Cash cards using the TOR browser.
That's how the developers of the virus that are still unknown to governmental authorities are trying to hide. Victims can pay their ransoms in a form of Bitcoins and PayPal transactions. However, for those who are using this payment system, the ransom is increased twice to recover files encrypted by ransomware.
Talking about infections in retrospect, we could say that it was primarily aimed at small businesses and online companies; However, home computer users had to deal with this file-locking malware as well. As we have already mentioned, the ransomware was updated a few times, and the improvements were made to its distribution[3] strategies as well.
As a result, the virus managed to increase its distribution rate from 200 to almost 2000 infected PC systems per day. Unsurprisingly, security experts have already labeled TeslaCrypt as one of the most dangerous viruses of 2016, despite the fact that the hackers have ended this project in May 2016[4]. IT security company ESET immediately created the decryption tool and started helping victims of the ransomware to rescue their files.
Although, keep in mind that you must remove the ransomware before you head to the data recovery. Experts note that there is no need to agree to pay the ransom, as you can easily get back your data with the free TeslaCrypt decryption software.
You can get SpyHunter 5Combo Cleaner or Malwarebytes to help you with malware removal. Ransomware-type infections are hard to detect and eliminate. Thus, professionals security tools come in hand when novice computer users are struggling with the procedure. Just download the antivirus and run a full system scan. It may take up to several minutes before your PC is clean once again.
A new ransomware version has been recently spotted in the cyberspace
Recently, cybersecurity experts have discovered a new version of this ransomware. The new crypto-malware is named as TeslaCrypt 2.x as it is similar to the previous variants of the file-encrypting virus. Currently, the cyber threat is relatively new. So, there is not much information about its peculiarities.
However, 2.x ransomware version is based on the same source code as its predecessor. Likewise, files are encrypted using one of the following algorithms as before:
- AES;
- RSA;
- ECHD.
Luckily, not many victims have been infected with this version just yet. However, experts recommend you to stay cautious as files encrypted by TeslaCrypt 2.x ransomware might or might not be recovered with the official decryption tool. Unfortunately, updated crypto-viruses include more sophisticated attack methods. So, it might be difficult to get back the compromised data.
Despite that, if you notice that your PC is infected, you must remove the ransomware immediately. For that, use one of our recommended and certified security tools to ensure that none of the ransomware-related components are left on the system.
Spam emails remain the most common malware distribution technique
Similar to other ransomware-type infections, this virus spreads with the help of malicious spam emails[5]. Usually, they come to the inbox as innocent-looking letters to trick users into opening them.
Experts discovered that the virus spreads as an invoice_2h04qd.js email attachment. However, this is merely an attempt to lure you into downloading the payload of the malware.
The subject line claims 'Required your attention'. Please, do NOT open such a message and do NOT download this attachment to your computer. No matter how tempting it looks, all that it seeks is to infect your computer with TeslaCrypt.
Of course, there is no guarantee that you won't run into other campaigns used for distributing this ransomware. That's why you should always check the sender and, if you don't know it well, remove such email messages from your inbox.
The evolution of Tesla Crypt ransomware virus
TeslaCrypt 2.0 is ransomware that uses the ECHD algorithm to encrypt the most widely used files on the infected system. The compromised data is appended with a .vvv file extension and becomes inaccessible. Victims are demanded to pay $500 in order to get back access to the encoded information. Unfortunately, experts warn that you might be scammed by the attackers. So, the wisest decision is to remove the ransomware and use official decryption software.
- .vvv File Extension virus. After infecting the system and encrypting useful files, it changes their extensions to .vvv and drops HOW_RECOVER.HTML, HELP_RESTORE.HTML, HOW_RECOVER.TXT, or HELP_RESTORE.TXT document on the desktop. According to it, the victim has to pay the ransom for getting the ability to use his/her files again. Please, do NOT pay it because you can lose your money.
The initial and the second version of the file-locker use the same key to encrypt and also to decrypt the files, and after the decryption process, these viruses leave specific traces that can help the user to find the decryption key. Besides, using the flaw in the program code of these viruses, some security experts have already invented some decryption tools that can help you to decrypt your files.
TeslaCrypt 3.0 version has its flaw patched and after the virus encrypts the files, it deletes the decryption key from the computer. As a result, it becomes much harder to recover the lost data. The third edition demands more than 400 USD dollars in exchange for a decryption key.
- .ccc File Extension virus is also known as a seriously dangerous application that seeks to disable its victim from opening his/her files. It does that by encrypting them with advanced encryption technology. As a result, all extensions of important files are turned into .ccc. If you can't open your files and you can see such extensions, there is a huge possibility that you are infected with .ccc File Extension ransomware. In this case, you should remove infected files of .ccc File Extension virus to prevent the further loss of your files.
- .xxx File Extension virus – this version of TeslaCrypt 3 also makes victim's files inaccessible and embeds .xxx extension to the filenames of affected victim's records. If you see that these extensions were added to your files, it is a sign that you cannot access them anymore. The price for a .xxx File Extension virus decryption tool is around 400 dollars as well. Unfortunately, we do not recommend you to pay up because you might not receive the decryption tool at all.
- .ttt File Extension virus – the appearance of .ttt file extensions unexpectedly added to the filenames on your computer reveals the existence of the third version of the virus. Just like other variants of TeslaCrypt 3.0 (.xxx, .micro, .ccc file extension viruses), .ttt File Extension virus commands to pay for the decryption key. Unfortunately, there is no guarantee that cybercriminals will give you the decryption key if you pay up.
- .micro File Extension virus is a version of the third variant. After encrypting victim's files, it adds a .micro file extension to their filenames. The ransom demanded by cybercriminals is also equal to approximately 400 USD. It acts the same as any other variants.
TeslaCrypt 4.0 is regarded as the most advanced variant of that virus. This virus no longer adds additional file extensions to the filenames. It also uses a complex encryption algorithm – RSA-4096. TeslaCrypt 4.0 drops ransom notes titled as RECOVER[5 random symbols].html. Unfortunately, the encryption algorithm this malware uses is nearly unbreakable, so you must take precautions and secure your files in case your computer gets affected by this virus. You should read this article – Why do I need backup and what options do I have for that?
TeslaCrypt 4.1b is currently the latest version of the virus. The researchers are still finding out new features that have been added to this newest edition. So far, it seems that the encryption process and the amount of ransom demanded in exchange for the encrypted files has not undergone any changes. Yet, new gateways were added to the list of websites where the victims can issue payments for their files.
It was also found that this virus uses WMIC (Windows Management Instrumentation Command-line)[6] to delete the shadow copies of the files on the PC so that it would be impossible for the user to restore these files from the system backup. In general, the differences of this program in comparison to its predecessors are slight.
Protect your PC by uninstalling the virus
Victims rush to recover files encrypted by this dangerous cyber threat. Although, first you must remove the ransomware to protect your computer from further damage. Security researchers note that crypto-viruses are capable of infiltrating the systems with more cyber threats.
Likewise, the removal is urgent if you don't want to permanently damage your computer. The minute you notice that your system is infected, you must perform the following tasks to protect it:
- Disconnect your computer from the Internet;
- Run a full system scan with FortectIntego and remove infected files from your computer;
- UPDATE. TeslaCrypt project was shut down in May 2016. Cybercriminals have revealed a master key that allows victims to decrypt their files for free. If your files are encrypted by the ransomware, use this TeslaCrypt decryption tool to recover them.
We recommend performing the automatic removal on your computer right after finding out that you are infected. Scan your computer with an updated malware removal program, for example SpyHunter 5Combo Cleaner or Malwarebytes. If you cannot install or run a full system scan, follow the instructions below to get access to your computer and launch the anti-spyware program.
Manual virus removal is NOT recommended as it is a complicated process that requires professional, computer-related knowledge. If malware prevents you from launching your antivirus or anti-spyware program, reboot your computer to the Safe Mode with Networking or try System Restore. Each of these methods is explained below.
Getting rid of TeslaCrypt virus. Follow these steps
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove TeslaCrypt using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of TeslaCrypt. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove TeslaCrypt from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by TeslaCrypt, you can use several methods to restore them:
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from TeslaCrypt and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Advanced Encryption Standard. Wikipedia. The free encyclopedia.
- ^ Jonathan Keane. Teslacrypt Ransomware Grows As Victims Pay Up. Digital Trends. Technology News and Product Reviews.
- ^ Andra Zaharia. Security Alert: TeslaCrypt Infections Rise as Spam Campaign Hits Companies in Europe. Hemdal Security. The Heimdal Security blog.
- ^ Peter Stancik. ESET releases new decryptor for TeslaCrypt ransomware. We Live Security. News, views, and insight from the ESET security community.
- ^ Liam Tung. TeslaCrypt ransomware alert: watch out for bogus email invoices. CSO. The Resource for Data Security Executives.
- ^ Ethan Wilansky. WMIC - Take Command-line Control over WMI. Microsoft. Microsoft Developer Network.





















