WannaCry ransomware / virus (Free Guide) - Bonus: Decryption Steps
WannaCry virus Removal Guide
What is WannaCry ransomware virus?
WannaCry ransomware is a significant threat to users' files, even after years of operation
WannaCry is the notorious ransomware virus that crippled more than 200,000 computers around the world back in 2017 and caused millions of dollars of damages o multiple organizations and governmental institutions. People believed that the virus was finally defeated when researchers announced patches for the exploits used to deploy malware, although practice showed that malware is not going anywhere any time soon.
It uses EternalBlue exploit[1] that was leaked by Shadow Brokers, the hacker group which published a series of leaks that disclosed secret hacking tools used by the NSA. The strain was eventually tied to the North-Korean Lazarus group, responsible for the cyberattack on Sony in 2014 and Bangladesh bank robbery in 2016.
Modified versions of this ransomware appear to be still affecting numerous users and businesses all over the world. It was inactive for a while, but up to 12,480 variants with original code, were reportedly discovered. Although the kill switch was released and infections stopped, some of those ransomware samples were updated, and thousands of primary versions remain active in the wild. In August 2019, researchers detected and blocked more than 4.3 million attempts to infect computers and spread versions of the virus.
Windows update patches were released to defer the spread of WannaCry ransomware, but not everyone patched their software. The rise of this ransomware means that machines whose owners haven't patched the OS in the past two years are vulnerable to this malware to this day. Also, malware might evolve further, as different groups might be undertaking its development.
| Summary | |
|---|---|
| Name | WannaCry |
| Alternative names | WannaCrypt0r, Wana Decrypt0r |
| Type | Ransomware |
| Versions | .wcry file extension virus; .wncry file extension virus |
| Danger level | High. Makes system changes, encrypts files. Malware can damage files without the possibility of decrypting them |
| Release date | 12 May 2017 |
| Ransom amount | Demands can go up to hundreds or thousands, but there is no point in paying the ransom because virus developers are not keeping track of transfers and not sending decryption tools to anyone |
| Cryptography | RSA encryption method |
| Appended file extensions | .wcry, .wncryt, .wncry, can also use different file markers or none at all |
| Ransom note | @Please_Read_Me@.txt, Please Read Me!.txt |
| Targeted OS | Main targets are Windows XP and Windows 7, although newer OS versions could also be affected |
| Distribution methods | EternalBlue exploit kit and DoublePulsar backdoor and other Windows OS vulnerabilities get used to obtaining access to particular systems and spread the ransomware further |
| File decryption | No decryption tool is currently available, although there are a few alternative methods that could help some victims to recover the locked files |
| Malware removal | Install a powerful anti-malware software and perform a full system scan |
| System fix | After you get rid of the infection, Windows might begin crashing or returning errors due to damaged system files. To prevent such disturbances, scan your system with FortectIntego |
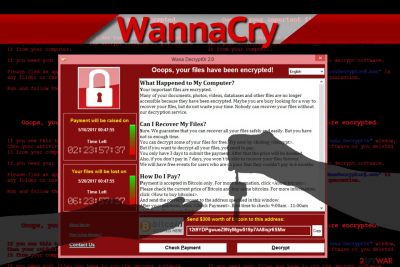
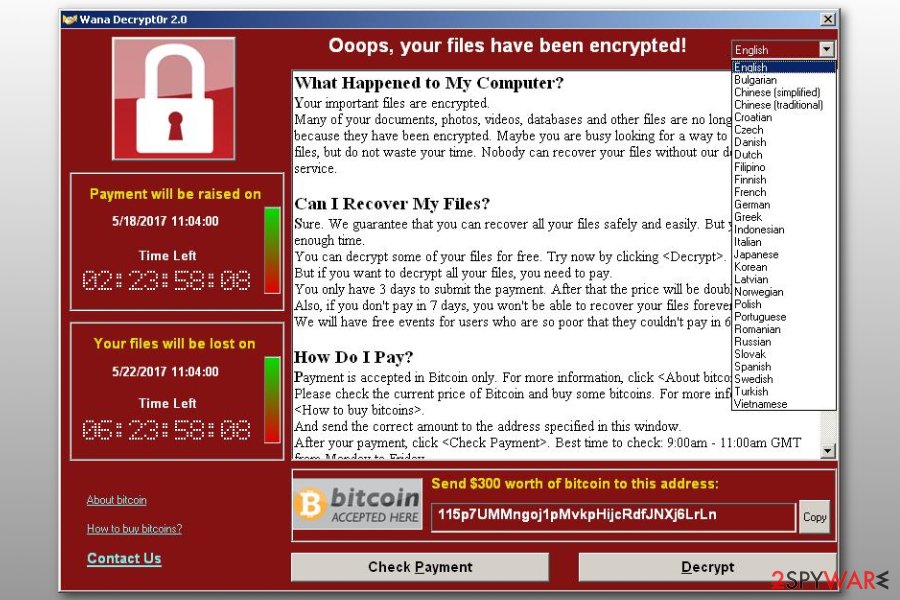
The virus encrypts data on the victimized computer using RSA algorithm and appends .wncry, .wncryt, or .wcry extensions at the end of the corrupted file-names. Victims are asked to pay $300 for the decryptor, which later doubles if the amount is not paid within three days.
While it is considered to be an old threat and Windows patched the vulnerability back in May 2017, the malware is still active with 74,621 infections in Q3 2018, as shows the research conducted by Kaspersky Labs researchers.[2]
As evident, WannaCry is not going away, despite its initial outbreak being over for a while now. Since its first infection, the malware has hit 4,826,682 computers worldwide and counting.[3] At the time of the writing, there are around 1.7 million vulnerable machines connected to the internet what could be victimized by the malware.
The virus originally emerged on Friday, 12 May 2017[4] and affected more than 230,000 computers in over 150 countries within a few days.[5] However, cyber attacks continued the next year as well. In March, ransomware hit the world's largest aerospace company Boeing and keeps doing the same.
The success of the attack hides in the distribution technique that aimed at outdated and unpatched Windows computers. Wanna Cry virus took advantage of EternalBlue exploit kit and hit various companies and organizations. However, the healthcare sector suffered the most[6].
According to reports, the first big companies affected by this ransomware were Telefonica, Gas Natural and Iberdrola. Some of the victims had data backups, while others had to face tragic consequences. Without exception, all victims are advised to carry out malware removal as soon as possible as it can help to prevent ransomware from spreading further.
Ransomware acts like a worm[7] because, as soon as it gets into the target PC, it starts looking for other computers to infect. It uses a security loophole in Windows OS and rapidly spreads using file sharing tools (such as Dropbox or shared drives) without asking for victim’s permission to do so.
There are three elements installed:
- Encryption/decryption tool;
- Tor browser;
- Files storing encryption keys.
The purpose of the virus is to collect ransoms in Bitcoins. After data encryption, the malware displays a ransom note where victims are urged to pay a ransom ranging from $300 to $600 in Bitcoins. Hackers try to scare people into paying the money by telling that their files will be deleted if they fail to pay within 7 days deadline.
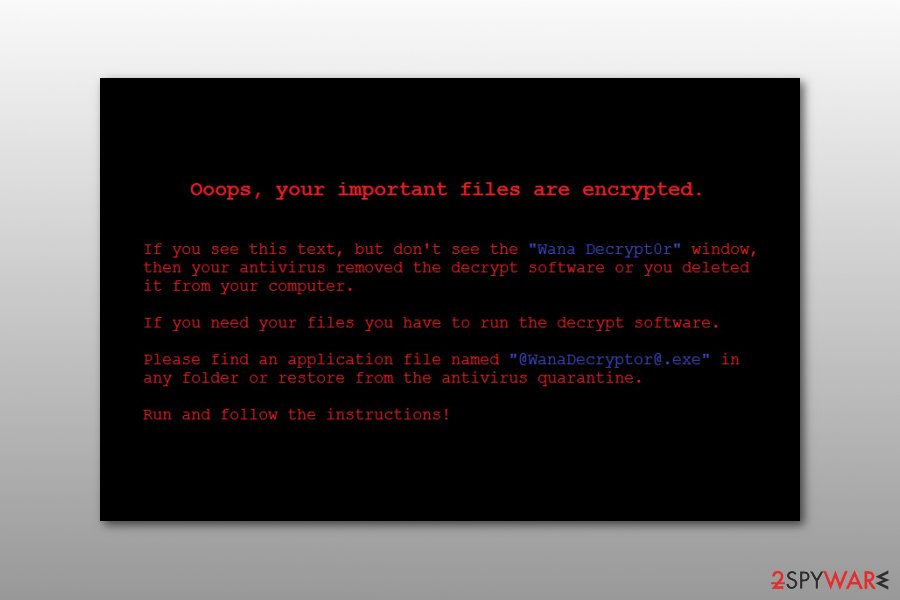
However, security specialists urge to remove WannaCry from the affected systems instead of paying the ransom. There are several decrypters, Wannakey and Wanakiwi, presented by security experts that you can download from the Internet for free. Additionally, if you have backups, you can recover data after cleaning the device with anti-malware software. Keep in mind that Windows system files could also be damaged, and security software might not be capable of restoring them, resulting in a full OS reinstallation.
Do not pay the ransom
Ransomware infections put the affected users into a rather tough spot: either pay the ransom within the provided timeframe or never regain access to your files. While malicious actors initially asked for a $300 ransom to be paid in bitcoin cryptocurrency (which is considered relatively low by today's standards), there was never any proof that the decryption tool was provided to victims, and they successfully regained access to the data.
According to Kaspersky security researchers, the coding used for ransomware was flawed. Once the ransom was paid, the attackers had no way to connect the targeted computer to the payment, hence no personalized key could be delivered for successful decryption. As a result, many users or companies who paid lost not only files but also the paid money.
Therefore, security experts advise avoiding ransom payments at all costs, especially to criminals that are known not to deliver a working decryptor. Even if the tool would work, it only proves cybercriminals that their business model works and that all they have to do is infect more victims with WannaCry or another crypto-malware. Essentially, by paying criminals, users indirectly fund their illegal activities, and they continue the cycle of infection and extortion.
Instead, several alternative methods could be used to recover data. Since malware is known to be faulty, it might not perform its functions correctly in some cases. Here are the options that are available to the infected users:
- Using working backups
- Employing third-party recovery software
- Trying built-in Windows resources.
As evident, the only secure way of recovering ransomware-encrypted files is by using backups. If you are interested in alternative methods, please check our recovery section below.
Transmission methods explained
Even though there are multiple ways how this virus can enter your system, the most widely used one is targeting Windows CVE-2017-0145[8] vulnerability in Server Message Block (SMB) protocol. An infamous Shadow Brokers hacker group has stolen EternalBlue exploit kit which was designed by US National Security Agency (NSA) and published it online.

The vulnerability is already patched, suggests Microsoft’s security bulletin MS17-010 (released on 14 May 2017). The exploit code used by perpetrators was meant to infect outdated Windows 7 and Windows Server 2008 systems, and reportedly users of Windows 10 cannot be affected by the virus. The malware typically arrives as a dropper Trojan that contains the exploit kit and the ransomware itself.
However, experts still recommend users to be extremely cautious. In fact, people are advised to take precautionary measures as downloading and running CrowdStrike Falcon — antivirus which offers endpoint protection and incorporates behavioural analysis to detect indicators of attack (IOAs).
Furthermore, the latest malware variants are distributed via girlfriendbeautiful[.]ga/hotgirljapan.jpg?i=1 in APAC region. After gaining access to the target computer, the virus creates a folder in the C:\ProgramData and entitles it with a set of random chars. The new folder contains tasksche.exe executable file.
The ransomware can also save its components into C:\Windows directory, dropping two files – mssecsvc.exe and tasksche.exe. The virus executes Icacls . /grant Everyone:F /T /C /Q command to get access to all of victim's files. The virus is set to connect to a non-existing domain and if it fails to open, the ransomware infects the system. One of such domains was purchased by a security researcher MalwareTech, therefore viruses that used to connect to that domain failed to infect computer systems.
What is more, cybercriminals attempted to DDoS that domain to continue the activity of the ransomware, however, unsuccessfully. Sadly, attackers understood their mistake and shortly released updated variants of the malware that connect to different domains, so from now on it won't be easy to fight against this malicious program.
The ransomware can affect anyone who lacks knowledge about ransomware distribution, therefore we suggest reading this Wanna Cry ransomware prevention guide that our experts prepared:
- Install MS17-010 system security update that Microsoft recently released. It addresses this particular vulnerability that the ransomware addresses. The updates were exceptionally released even for old OS such as Windows XP or Windows 2003.
- Keep the rest of computer programs up-to-date.
- Install a reputable anti-malware software to defend your computer against illegal attempts to infect your computer with malicious programs.
- Never open emails that come from strangers or companies that you have no business with.
- Disable SMBv1 using instructions provided by Microsoft. If these instructions seem confusing, try the method provided in the next step.
- Apply a quick fix – install WannaSmile tool, which was developed by a developer Hrishikesh Barman. This tool automatically disables SMB, edits host file to add Google's IP to the “kill-switch” (online fix) and creates a lightweight local web server and add localhost to “kill-switch” (offline fix).
- Look for more tips in this guide on how to survive WannaCry attack.
September 2019: versions of ransomware contain bypass for the kill switch
Sophos researchers revealed in their new report that the virus is not dead. Also, it is more alive than ever because the kill switch that got many people to believe the end of this ransomware can be bypassed. Analyzing the recent activity of malware, researchers discovered how many people the threat got affected;
- At least 12,000 ransomware variants found in the wild. Even two years after the supposed killing of the virus.
- More than 5,000 attempts of attacks against unpatched devices got blocked. This is only in the last three months of 2018.
- Most of the computers targeted run Windows 7 without needed patches. So Windows XP is not forgotten.
- The original non-updated version was sent only 40 times.
- Paying the ransom is suggested but gives no results. Some of the victims have paid, but criminals aren't monitoring those payments and decryption tools or keys are not provided.
May 2019 update: the state of malware two years on
Possibly one of the main reasons why WannaCry became one of the most prolific threats of the decade was due to its ability to spread over the network to all the other unpatched computers by abusing the EternalBlue exploit.
After a significant amount of struggles that rail stations, hospitals, and other vital sectors had to go through, the kill switch was activated by a security researcher Marcus Hutchins (also known as MalwareTech), who was later charged with the unrelated cyber crimes.
After the kill-switch was activated, the amount of infections went down by a significant margin. Nevertheless, according to Microsoft researcher Nate Warfield,[9] there are still around 1.7 million machines that are vulnerable to EternalBlue SMB exploit, and that is not counting the devices that could be connected to these via the servers.
Since its initial outbreak, it hit 4.8 million machines worldwide, with the top countries hit being:
| WannaCry infections by country since its initial launch | |
| India | 727,883 |
| Indonesia | 561,381 |
| USA | 430,643 |
| Russia | 356,146 |
| Malaysia | 335,814 |
Many security researchers are voicing their disappointment about the situation, as the threat can be easily avoided by merely patching the vulnerable systems. Unfortunately, cybesecurity is mostly overlooked until it manages to cause a significant amount of damage.

November 2018 update: the virus is still active in Q3 2018
Security experts from Kaspersky Lab published a report detailing a global threat actor activity. They noted that the total amount of blocked threats in Q3 2018 was 947,027,517 across 203 countries. While ransomware attacks were considered to be in decline this year, a total amount of infections grew from 186,283 to 259,867 in a year, which indicates the overall growth of file-locking malware.[10]
According to research, the overall infections of the virus increased by 2/3 in comparison to the same period in 2017. They were especially concerned about the strain's prevalence, accounting for a total of 28% of all infections:
It is concerning to see that WannaCry attacks have grown by almost two thirds compared to the third quarter of last year. This is yet another reminder that epidemics don’t cease as rapidly as they begin – the consequences of these attacks are unavoidably long-lasting. Cyber-attacks of this type can be so severe that it’s necessary for companies to take adequate preventive measures before a cyber-criminal acts – rather than focus on recovery
It once again proves that, although the EternalBlue was patched over a year ago, users and organizations still tend not to patch their systems on time, resulting in thousands in recovery costs. Researchers push users to invest in preventing the attack rather than dealing with its consequences.
March 2018 Update: the notorious ransomware has infected the servers of Boeing
On March 28, experts had reported about the recent WannaCry ransomware attack. Apparently, Mike Vanderwelm, chief engineer at Boeing detected a cyber threat on the company's servers.
Cybersecurity researchers thought that the ransomware will deteriorate the firm's production and even software. Luckily, it hasn't caused that much damage as everyone has expected[11]. Later on, the head of Boeing communications ensured that malware affected only a few devices. However, the problem is under control, and no issues were detected on production lines.
November 2017 Update: imposters aim to infect computers in Russia and Portugal
In November, Russian-speaking users reported being hit by a fake Wanna Cry versions which is called WannaDie. Some people also recognized it by WanaDie name and .wndie extension at the end of the compromised filenames. Even though it does demand to pay the ransom in order to receive Wanna Die Decrypt0r, experts report that it does not encode information on the infected computers.
The same situation is with a fake Portuguese variant.[12] This malicious program also is unable to decrypt files yet. However, it is ready to start swindling 0.0060 Bitcoins from threatened computer users. But affected files can be recovered by using the 7HAR2NTX-YC8APT4B-4H7H62JP-A2QLWNHU-ZWYX5J4J-W29P6M9W-KS3LKAP4-BML5WTS2 unlock key.
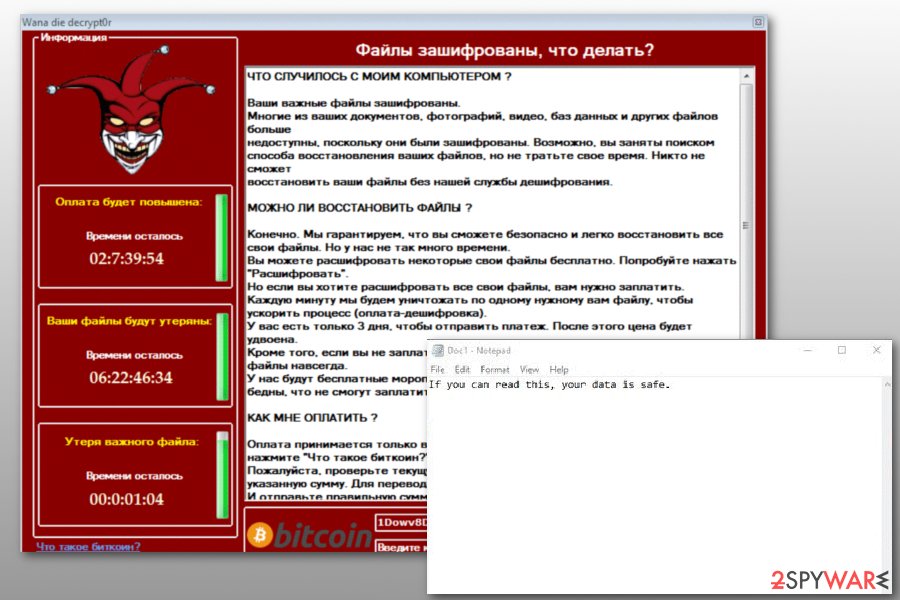
Both fake variants use a similar design of the ransom note as the original variant. Victims are also asked to pay the ransom within 3 days; otherwise, the size of the ransom will increase, and after 7 days, the decryption key will be destroyed.
However, if these variants would ever start encrypting files, paying the ransom should not be considered. It is most likely to lead to money loss.
August 2017 Update: South Korean self-service kiosks are under attack
The ransomware has appeared on LG self-service kiosks[13] in South Korea on Wednesday. Users reported that they have received the ransom note[14] on the computers. However, despite the fact that the message looks extremely similar to the original one, further analysis is required to assure that this is WannaCry ransomware.
The original malware succeeded in wreaking global chaos since multiple companies worldwide failed to update their Windows operating system. Specifically, the malware targetted weak SMB protocols in Windows 7 version. South Korea was also one of the most affected countries. Thus, LG company failed to update their kiosk systems raised a surprise if not suspicions.
FBI arrested MalwareTech for developing and selling malware
MalwareTech is the online name of Marcus Hutchins, who has managed to temporarily stop the ransomware distribution. Once the researcher has detected the bogus domain and registered it, the global file-encrypting virus spread has significantly slowed down for some time.
However, on the 2nd of August, it was reported that FBI arrested 24-year old, UK-based malware researcher.[15] The US authorities pressed the charges for creating and selling a banking Trojan Kronos.
According to the official document,[16] Hutchins created the virus in July 2014 and later tried to sell it for $3,300. At the beginning of 2015, he has updated Kronos malware and advertised in dark web forums. Finally, he is suspected of selling the malicious program for about $2,000.
Hackers behind the ransomware generated $143,000 from the attacks
Event though this ransomware is one of the most dangerous ones, only 338 victims have been convinced to pay the ransom for the decryption software[14]. It seems that the developers of the malicious program should improve their social engineering tactics to make more profit.
On August 3, it was noticed that collected ransoms were drained from three Bitcoin wallets used by cyber criminals. The virtual currency has been transferred to nine other Bitcoin accounts.[17] However, it’s not clear the money has been sent and what purposes hackers have.
There’s no doubt that these transactions are being monitored. Europol and the U.S. Department o Justice are working on this cyber attack. However, any official statements haven’t been released yet.
The list of ransomware virus versions
.wcry file extension virus
.wcry file extension virus. Experts categorize this version of the virus to be the first. Once it appeared in the cyberspace on February 2017, no one believed that it would become as dangerous as CryptXXX, Cerber, or CryptoLocker viruses.
The virus uses AES-128 cryptography cipher to lock files securely, adds .wcry file extensions to their filenames and asks to transfer 0.1 Bitcoin to a provided virtual wallet. The malware was initially distributed via email spam; however, this particular virus did not bring a lot of income for its developers. Although files encrypted by this ransomware appeared to be unrecoverable without having the decryption key, developers of it decided to upgrade the malicious program.
.WNCRY file extension virus
.WNCRY file extension virus. The ransomware version that belongs to the described malware category emerged in 2017 and has been entitled due to its ability to append .wncry file extension to every encrypted file. You can use a free decryption tool that will restore files marked with these file extensions for you.
The ransomware is currently under analysis, so victims are advised to remove the ransomware and keep the encrypted data because, in the future, researchers might find a way to restore corrupted files. Just like the rest of the crypto-ransomware family members, virus demands a ransom in Bitcoins that's worth $300-$600.
WCrypt ransomware
WCrypt ransomware virus. WCrypt virus is an alternative name to the main ransomware. The ransomware has devastated files all over the globe, and new versions keep showing up.
Researchers have noticed that certain variants of this ransomware append .wcryt or .wncrypt extension to files, which gives an idea where the alternative name of the ransomware comes from. If your antivirus detects an infection called WCrypt, eliminate such virus and everything related to it ASAP!
WannaCryptor ransomware
WannaCryptor is also an alternative name of the ransomware, which is used by several anti-spyware and antivirus programs. If your security software blocked a Trojan, you should know that the infamous ransomware has just attempted to step into your system.
If it succeeded to do so, it would have encrypted all of your files and asked for $300-$600 as a ransom. This name is used according to Wanna Decryptor 1.0, which the malware opens after encrypting all files. Victims reported that this ransomware adds .wcry file extensions to corrupted records.
WanaCrypt0r ransomware
WanaCrypt0r ransomware virus. It is yet another name for the updated version of the ransomware. The new version chooses Windows vulnerabilities as its primary attack vector and encrypts all files stored on the system in seconds.
Affected files can be recognized from extensions added to the filename right after the original file extension – .wncry, wncryt, or .wcry. There is no way to restore corrupted data without having a backup or the private key created during the data encryption process. The virus typically demands $300, although it raises the ransom price to $600 if the victim fails to pay up within three days.
WanaCrypt0r 2.0
WanaCrypt0r 2.0 ransomware virus. It is the name of an updated WannaCryptor variant, which launches Wana Decrypt0r 2.0 after encrypting user's files. This malicious program was used to attack computer users worldwide during the cyber attack launched on May 12, 2017.
According to the latest reports, the total of ransoms paid to Bitcoin wallets that belong to cybercriminals reached $60,000 already. The virus appends .WNCRY file extensions to encrypted files drops a ransom note called @Please_Read_Me@.txt. At the moment, malware researchers cannot provide any tools that could restore data that this malicious program corrupts.
Wana Decrypt0r ransomware
Wana Decrypt0r ransomware virus. This is the program that the virus launches after a successful infiltration to the target system. The researchers already noticed Wanna Decryptor 1.0 and Wanna Decryptor 2.0 versions approaching victims.
The malicious software displays a countdown clock showing how much time has left to pay the ransom until the price of it skyrockets, and also identical countdown clock that shows how much time has left until the virus deletes all data from the computer. This particular version shook the virtual community on 12 May 2017, although several days later it was stopped by a security researcher who goes by the name of MalwareTech.
Wana Decrypt0r 2.0 ransomware
Wana Decrypt0r 2.0 ransomware virus. This program has shocked hundreds of thousands of computer users worldwide because in May 2017 it managed to infect over 230k computers in more than 150 countries. The appearance of this program window indicates that the ransomware has already encrypted all of your files, so closing it won't save your data. This version of ransomware demands between 0.171 to 0.34 BTC to restore victim's files.
The described malware variant was analyzed and researchers discovered how it infects the system. Before attacking the files stored on the target computer, the program connects to a non-existing domain, and if it fails to connect, the encryption procedure starts. One security researcher discovered such ransomware kill switch and registered the domain, making the ransomware useless. However, since then, the virus has been updated.
WannaCry 2.0 ransomware virus
Since all the news sites rushed to post about the kill switch discovered by the malware researcher, authors of the ransomware pushed out a 2.0 ransomware version that evades the kill switch[18]. Luckily, the infection rate has slowed down, and although the ransomware is active, it still means something.
It is believed that the second version is not developed by original malware authors, which simply shows that criminals only need to modify the code a little to start attacking users again. According to reports, the malicious virus spreads via fake Excel documents, so if a stranger sends you one via email, do not open it!
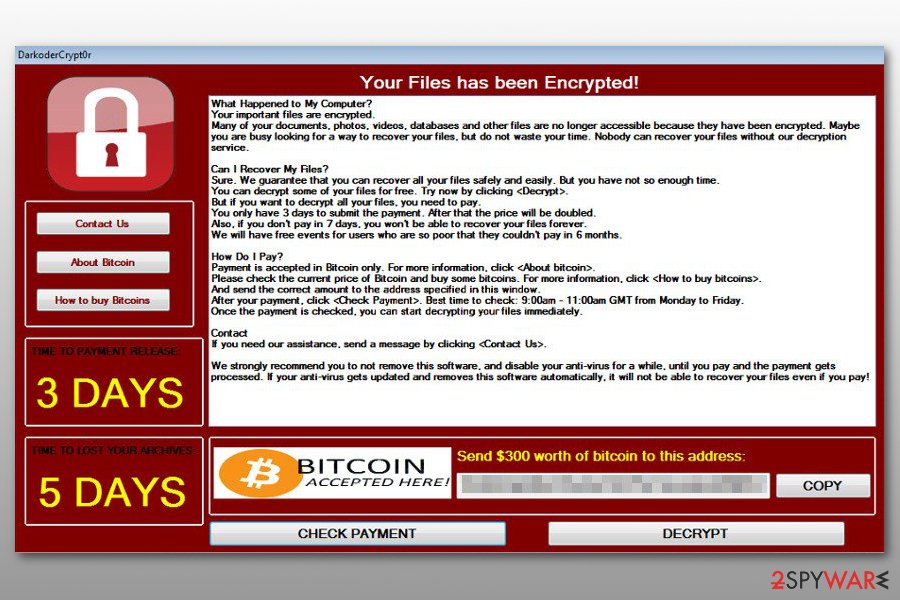
DarkoderCrypt0r ransomware
DarkoderCrypt0r ransomware virus. DarkoderCrypt0r virus is an imitation of the powerful ransomware that has recently hit the virtual community. It adds .DARKCRY extensions to corrupted files and launches a program that looks almost identically as Wana Decrypt0r 2.0.
Instead of displaying a countdown clock that shows how much time the victim has to pay the ransom until the ransom doubles, the virus displays “3 days.” It asks for the same sum of money as the real virus. This version does not have worm-like features, therefore it doesn't spread the same way as the original virus.
FakeCry ransomware
FakeCry ransomware virus. The FakeCry is another virus clone. It is one of those viruses that recently attacked Ukraine. According to Kaspersky, some MeDoc users were infected not only with ExPetya but with another ransomware that turned out to be a fake copy of the infamous WannaDecrypt0r 2.0 virus. The difference between the fake and the original is that the clone is developed in .NET, while the real one is written in C language.
The ransomware asks for 0.1 BTC as a ransom. The ransomware, surprisingly, has a list of extensions in DEMO_EXTENSIONS. The list contains extensions of image files only, and the ransomware suggests decrypting these file types for free. To decrypt the rest of encrypted data, the virus demands ransom.
The ransomware is distributed in the same way as ExPetya/Petya and infects systems via a dropper that extracts two files on the system. The FakeCry ransomware launches graphical user interface and the encrypter. At the moment of writing this update, no decryption tools were available for this Wanna cry-lookalike.
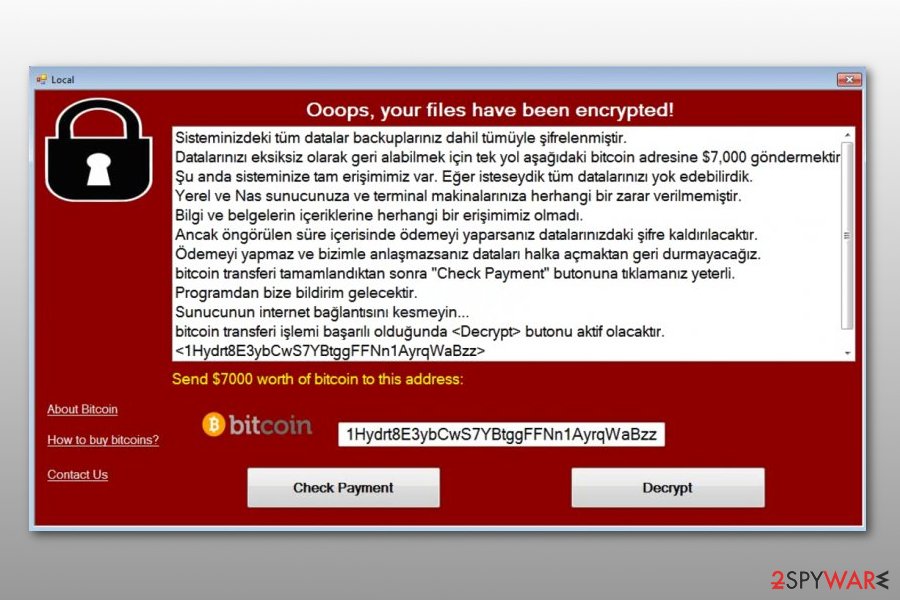
WannaCryOnClick ransomware
In July 2017, another bogus virus copy emerged. This time, it was dubbed as WannaCryOnClick ransomware because of its ability to send email messages to virus' developers as soon as the victim clicks on “Decrypt” or “Check Payment” buttons available in the ransom-demanding program.
The virus is also known as Fake Turkish version because the ransom note is written in this language. The criminals state that the victim has to pay $7000 in Bitcoin to retrieve data decryption key. However, people who fell victims to this ransomware should not waste their money because criminals most likely won't provide the decryption key even after paying the ransom.
WannaDie ransomware
WannaDie ransomware virus. WannaDie or WanaDie pretends to be a Russian version of the virus. The malicious program was discovered in November 2017. The virus corrupts files with .wndie file extension and demands to pay the ransom in order to recover files with Wanna die decrypt0r. However, the virus does not employ a real encryption algorithm, so paying the ransom is not needed.
Fake Portuguese WannaCry
On November 2017, cybercriminals presented another imposter that targets computer users n Portugal. Cybercriminals are known for communicating with victims via nkittybuggy8648@gmail.com email address. Even though the malicious program asks to pay 0.0060 Bitcoins for the data recovery, victims should not do that. All files can be unlocked with this code 7HAR2NTX-YC8APT4B-4H7H62JP-A2QLWNHU-ZWYX5J4J-W29P6M9W-KS3LKAP4-BML5WTS2. Once it’s done, malware removal with security software should be completed immediately.
.[recoverydata54@protonmail.com].WannaCry files virus
Victims affected by a questionable .[recoverydata54@protonmail.com].WannaCry ransomware that is linked with this virus and Phobos ransomware, but the particular relationship is not confirmed.
It is possible that this version of the virus emerged and is really related to recent activities that got renewed. However, this might be a poorly coded copy. Various researchers determined that this is easily decryptable and can be copying a few versions, but the ransomware name in the extension can be a legitimate indication.
This threat delivers a few files with ransom demands, one of them is info.txt and another version of the payment instructions get opened as a program window directly on the screen. The amount that virus developers want to get gos up to $1500 in Bitcoins.
Delete WannaCry ransomware to retrieve altered files
If you want to get back the access to the compromised files, you must remove the virus or it will repeat the encryption process. Since the ransomware is highly sophisticated and hides its components all across the computer, only professional removal software can help you eliminate it. For that, we suggest using SpyHunter 5Combo Cleaner, or Malwarebytes. To restore potentially damaged Windows system files, we recommend using FortectIntego – it can replace bad sectors with brand new ones automatically.
The sooner you will disable this virus, the better, so do not waste any more time. If you have data backups saved in other locations, do not rush to use them. Plug your external drive or use the cloud services only when you get rid of the threat. If the computer is still compromised, your data copies can be encrypted one more time. For best results, we suggest you follow these removal guidelines provided by 2-Spyware team.
Keep in mind that the prevention of WannaCry requires patching! Previously, the virus was Windows CVE-2017-0145 vulnerability. However, it is still unknown whether it is using the same hole and affecting unpatched users or has found yet another vulnerability to misuse for its attacks.
Getting rid of WannaCry virus. Follow these steps
Manual removal using Safe Mode
To delete the virus with Safe Mode, follow each of provided steps attentively and make sure you boot your PC into the right mode. This way, you will disable the virus and create the right environment for the launch of malware removal software.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove WannaCry using System Restore
To eliminate the malicious program with System Restore, we highly suggest using steps that are given below.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of WannaCry. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove WannaCry from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Unless you are willing to waste from $300 to $600 or have a data backup, there is no way to restore files encrypted by this fearsome virus. The malware analysts have been working hard and have already presented legitimate decryption tools. In addition, you can also try the following data recovery options:
If your files are encrypted by WannaCry, you can use several methods to restore them:
Install and run Data Recovery Pro
Data Recovery Pro might be the right tool if you want to restore part of encrypted files. Here's how to use it.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by WannaCry ransomware;
- Restore them.
Search for Volume Shadow Copies
Sometimes even the most sophisticated viruses can fail to complete all of the malicious tasks, therefore if you are lucky enough, the virus might leave Volume Shadow Copies in the system. To find them and use them for data recovery, install ShadowExplorer software.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Try decryption tools presented from GitHUb
If you didn't reboot your computer after infiltration of the virus, you can try Wannakey decrypter. If you have already reboot your machine, make sure you download WanaKiwi which is compatible with Windows XP, Windows 7, Windows Vista, Windows Server 2003 and 2008.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from WannaCry and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Ondrej Kubovič. One year later: EternalBlue exploit more popular now than during WannaCryptor outbreak. WeLiveSecurity. Eset security blog.
- ^ Victor Chebyshev, Fedor Sinitsyn, Denis Parinov, Oleg Kupreev, Evgeny Lopatin, Alexander Liskin. IT threat evolution Q3 2018. Statistics. SecureList. Kaspersky's blog.
- ^ Michael Hill. WannaCry Remains a Global Threat Two Years On. Info Security. Information Security & IT Security News.
- ^ Alex Hern, Samuel Gibbs. What is WanaCrypt0r ransomware and why is it attacking global computers?. The Guardian. News, Sport and Opinion.
- ^ Nandagopal Rajan. WannaCry: Here’s all you need to know about the biggest ransomware attack. The Indian Express. Latest News, Breaking News Live, Current Headlines.
- ^ Lily Hay Newman. The Ransomware Meltdown Experts Warned About Is Here. WIRED. In-Depth Coverage of Current and Future Trends in Technology.
- ^ WannaCrypt ransomware worm targets out-of-date systems. Microsoft TechNet. The new Microsoft Malware Protection Center Blog.
- ^ Microsoft Security Bulletin MS17-010 - Critical. Microsoft TechNet. Security TechCenter.
- ^ Nate Warfield. 2 years after WannaCry and there’s still 1.7M machines with SMB exposed to the Internet. Twitter. Social Network.
- ^ Roman Unuchek, Fedor Sinitsyn, Denis Parinov, Alexander Liskin. IT threat evolution Q3 2017. Statistics. SecureList. Kaspersky's blog.
- ^ Lucia Danes. A recent WannaCry attack on Boeing was not that devastating. 2-spyware. Cyber security and spyware news.
- ^ Karsten Hahn. Tweet about fake Portuguese WannaCry. Twitter. The social network.
- ^ Catalin Cimpanu. Ransomware Hits LG Self-Service Kiosks Across South Korea, Possibly WannaCry. BleepingComputer. News, reviews and tech support.
- ^ Mohit Kumar. Hackers Behind WannaCry Ransomware Withdraw $143,000 From Bitcoin Wallets. The Hacker News. Cyber Security, Hacking News.
- ^ Kate Irby. He stopped the WannaCry cyberattack. Now he’s been detained by the FBI, reports say. KansasCity. KC Breaking News, Sports, Weather & More.
- ^ The Indictment of Marcus Hutchins. United States District Court. Easter District of Wisconsin..
- ^ Selena Larson. Someone has emptied the ransom accounts from the WannaCry attack. CNN.Breaking News, Latest News and Videos.
- ^ Swati Khandelwal. WannaCry Kill-Switch(ed)? It’s Not Over! WannaCry 2.0 Ransomware Arrives. The Hacker News. Cyber Security, Hacking News.





















