Cerber Ransomware virus. 14 variants listed. Removal guide for 2021
Cerber virus Removal Guide
What is Cerber virus?
Cerber ransomware is a threat that has many versions with different functionalities and excluded countries
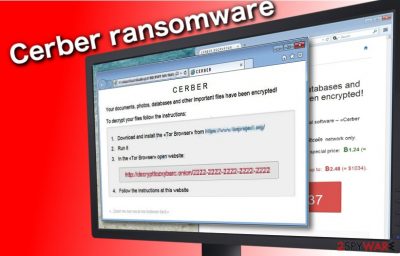
Cerber ransomware is a file locking virus that was first spotted in the wild in March 2016. Operating Ransomware-as-a-service scheme, the malware became a diverse and high profile threat that targets regular users, as well as organizations and businesses, although it avoids infecting victims from the Commonwealth of Independent States (CIS). Security researchers believe that this ransomware was developed in Russia,[1] as it is very prominent on Russian underground forums.
During years of its operation, the ransomware was split into five major variants, although sub-variants are being released on a regular basis, and mostly spread via malicious Word documents sent out to thousands of users via spam emails, although other methods, like Rig and Magnitude, exploit kits were also used.
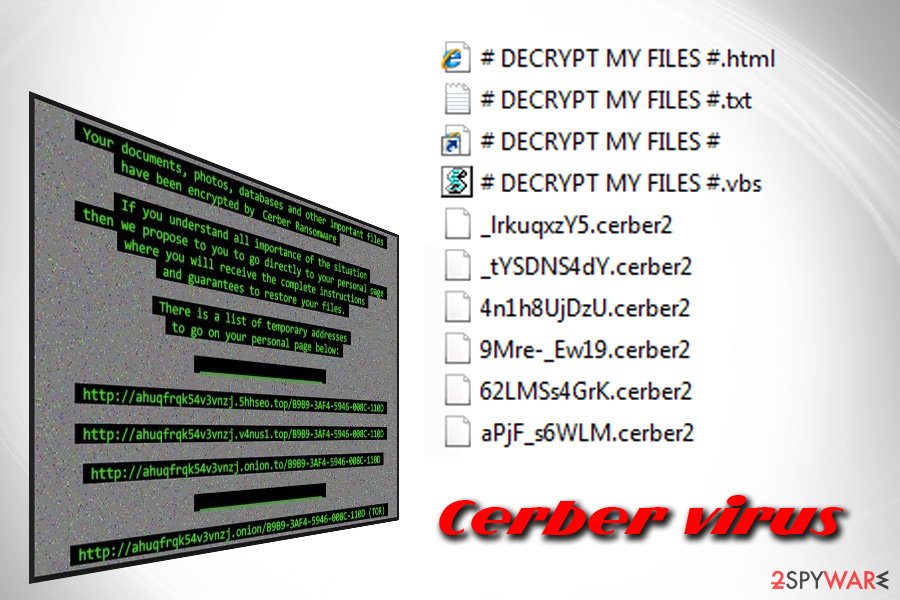
Once inside, the malware applies AES-256[2] or RC4 encryption algorithm to lock up all personal data and mark it with .cerber, .cerber2, .cerber3, .af47, .a48f, .[random characters] or another extension, and changes the desktop wallpaper, which notifies victims about the Cerber virus intrusion. Additionally, hackers also drop a ransom note which comes in various formats (.txt, .vbs, and .html) and asks users to pay a ransom of 1.24 BTC or more, depending on the malware version.
| SUMMARY | |
| Name | Cerber Ransomware |
| Type | Cryptomalware, file locking virus |
| Operated scheme | The malware uses RaaS (ransomware-as-a-service) scheme – the developers of malware keep 40% and the distributing parties retain 60% of the profits earned from ransom payments |
| Encryption algorithm | Ransomware will encrypt all personal files using AES-256 or RC4, and render the computer system unstable |
| Size of ransom | The ransom size varies greatly and can reach 1.24 BTC |
| Extension | cerber, .cerber2, .cerber3, .af47, .a48f, .[random characters], .ba99, .beef |
| Ransom notes | # DECRYPT MY FILES #.txt, # DECRYPT MY FILES #.html, # HELP DECRYPT#.html, _READ_THIS_FILE.hta, *HELP_HELP_HELP[random characters]*.hta, _R_E_A_D___T_H_I_S___[random]_.txt or _R_E_A_D___T_H_I_S___[random]_.hta, README.hta |
| Assocaited files | Acotyledon.exe, Straightness.exe, Parameter.exe, Giobertite.exe |
| Distribution | Exploit kits (Rig, Neutrino, Magnitude), spam emails, malicious sites |
| Decryptable? | There are limited options when it comes to data decryption, although some variants can be decrypted with the help of Trend Micro decryption tool |
| Elimination | In some cases, virus may disable the installed anti-virus software in order to operate without interruptions. To bypass this feature, you should access Safe Mode with Networking and perform a scan with reliable security software, such as SpyHunter 5Combo Cleaner or Malwarebytes |
| System fix | Malware often renders the system unstable as it also affects some system files. To avoid reinstallation of the Windows operating system, you can apply its fix using FortectIntego repair software |
Cerber ransomware virus has been changing the name of its ransom note repeatedly. So far, the crypto-malware versions use the following names for ransom notes: # DECRYPT MY FILES #.txt, # DECRYPT MY FILES #.html, # HELP DECRYPT#.html, _READ_THIS_FILE.hta, *HELP_HELP_HELP[random characters]*.hta, _R_E_A_D___T_H_I_S___[random]_.txt or _R_E_A_D___T_H_I_S___[random]_.hta, README.hta.
Like any other file-encrypting virus, the virus can infiltrate the system via malicious spam emails carrying deceptive .ZIP, .DOCM, .PDF, or .JS file attachments. An interesting detail about the ransomware is that it will not attack your computer if you live in one of these countries:
- Azerbaijan;
- Armenia;
- Georgia;
- Belarus;
- Kyrgyzstan;
- Kazakhstan;
- Moldova;
- Turkmenistan;
- Tajikistan;
- Russia;
- Uzbekistan;
- Ukraine.
Unfortunately, if none of these is your country of current residence, this virus may potentially hit your computer.
Cerber ransomware sets itself to run automatically on the next computer startup. Once the computer becomes active, ransomware starts sending random error messages and then reboots your computer into Safe Mode with Networking. Unfortunately, the virus then restarts your computer again, this time in a normal regime, and starts the encryption process. The latest version has received a huge update – now it uses red color for the ransom note used to warn the victim about the encrypted data.
Once the encryption process is finished, threat drops ransom notes in each folder that stores infected files. These notes are named as DECRYPT MY FILES. The file extension may vary, it can be a .html, .txt, or .vbs file. The .vbs file will also play a sound message, which says:
Hi, I'am CERBER RANSOMWARE 😉
—–
Y0UR D0CUMENTS, PHOTOS, DATABASES AND OTHER IMPORTANT FILES HAVE BEEN ENCRYPTED!
—–
The only way to decrypt your files is to receive the private key and decryption program.
To receive the private key and decryption program go to any decrypted folder,
inside there is the special file (*_R_E_A_D___T_H_I_S_*) with complete instructions
how to decrypt your files.
If you cannot find any (*_R_E_A_D___T_H_I_S_*) file at your PC, follow the instructions below:
—–
1. Download “Tor Browser” from [link] and install it.
2. In the “Tor Browser” open your personal page here:
[link]
Note! This page is available via “Tor Browser” only.
—–
Also you can use temporary addresses on your personal page without using “Tor Browser”.—–
1. [link]
—–
Note! These are temporary addresses! They will be available for a limited amount of time!
—–
The ransom note explains what happened to your computer and provides instructions on how to retrieve your files. Shortly said, virus developers, ask you to download Tor browser[3] to access the website where you can pay the ransom anonymously. It demands the victim to pay 1.25 BitCoins, which is approximately $512 USD.
It also threatens that the ransom will be doubled if the victim does not pay within seven days. If the ransom is paid, this ransomware should supposedly provide a unique download link to get a Cerber ransomware virus decryption tool. Otherwise, there is no way to decrypt files for free. Please, do NOT fall for these lies and get rid of ransomware to stop the encryption of another portion of your files.
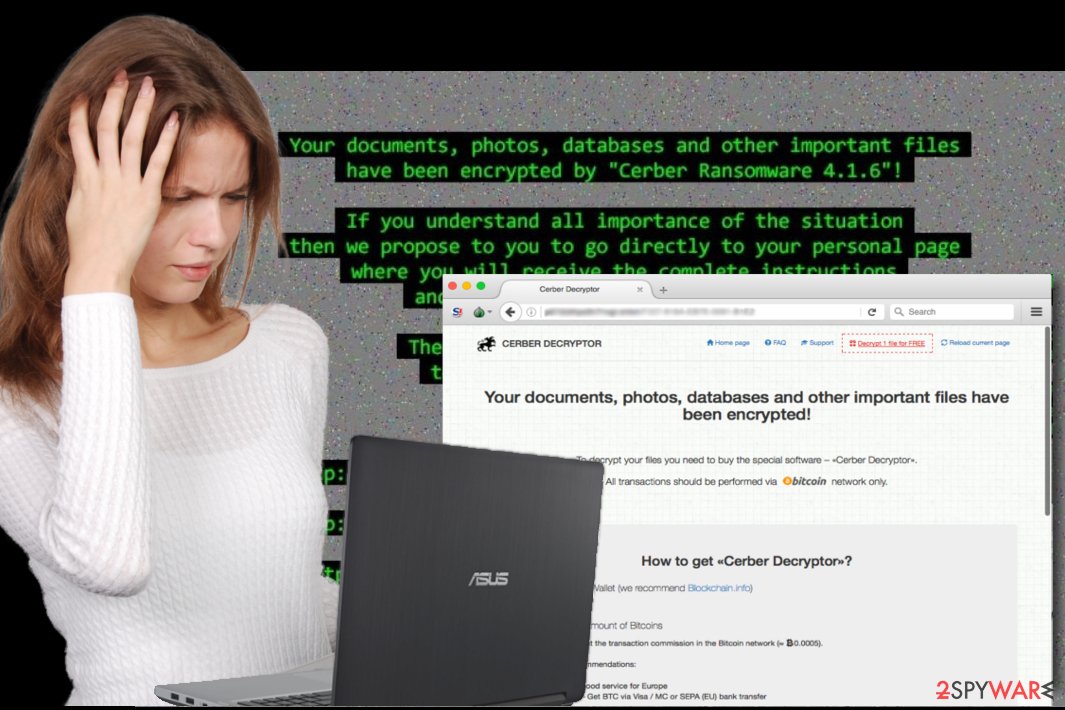
Next to money extortion, Cerber ransomware is capable of stealing crypto wallet data
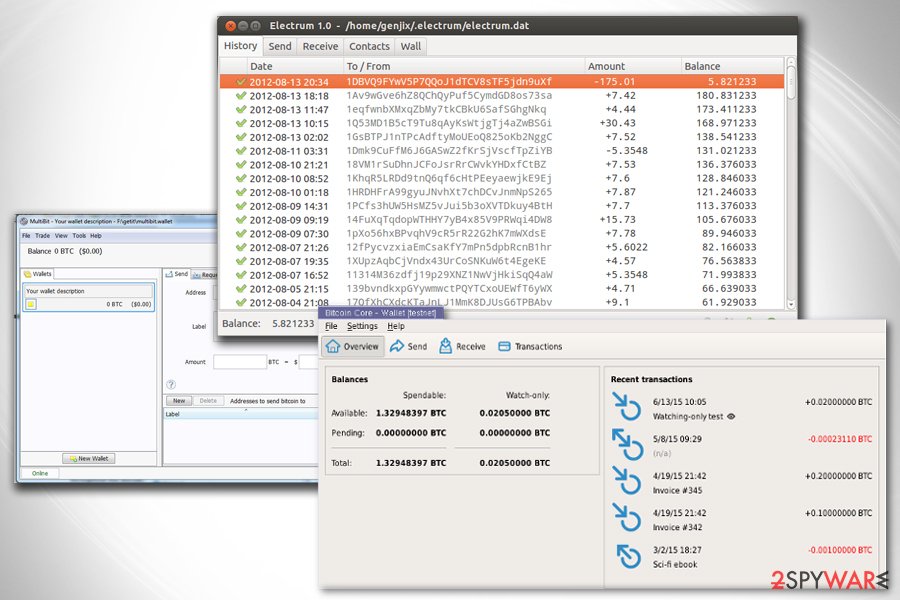
In order to boost their income, developers of ransomware have recently launched a new variant that is capable of stealing Bitcoin wallet data.[4] After the infiltration, it steals passwords stored in the Internet Explorer, Google Chrome, and Mozilla Firefox web browsers. Once it’s done, it becomes easier to obtain information from Bitcoin wallets.
The virus looks up for free files that belong to the different Bitcoin wallet apps:
- wallet.dat used by Bitcoin Core wallet;
- *.wallet used by Multibit wallet app;
- electrum.dat used by Electrum wallet app.
Another proof that Cerber virus continues growing and expanding is a recent collaboration with developers of Kovter Trojan. This cyber infection is known since 2013 as click-fraud malware. Both malicious programs were noticed spreading with spam emails that delivered fake notifications from parcel delivery services, such as FedEx, USPS, and UPS.[5]
Therefore, once victims are tricked into opening an obfuscated file, they download two viruses instead of one cyber infection. As a result, victims can not only get their files encrypted but also lose personal information, such as login details. To make sure you are not infected, double check your system with SpyHunter 5Combo Cleaner, Malwarebytes. It will also help you remove Cerber ransomware with each of its files and will also fix damaged files and similar components on your computer.
Good news: some Cerber ransomware versions fail to remove Shadow Volume Copies
The new year has already brought us new changes in Cerber ransomware. After making the latest researches on this malware, experts discovered that it turned red. In fact, red color has shown up in the ransom note of this ransomware that warns its victims about the encryption of their files and a need to pay the ransom in exchange for the malicious decryptor. Besides, this crypto-virus tends to use .ba99 file extension which is appended to every victim's file. Four random characters can also be appended.
Fortunately, this malware fails to remove Shadow Volume Copies of these files that it encrypts, which should help users recover their data with the help of Shadow Explorer and similar tools. This version has already been named as Red Cerber. Of course, after discovering such concerning news, we predict that this virus will stay at its peak this year just like it did the last year.
What is more, cybercriminals have just started with new distribution tricks. Although they are still delivering massive loads of the virus's examples via email, now they appear to be using IP addresses that belong to Amazon Web Services, or shortly Amazonaws.
These malicious emails reportedly contain no subject line and no message, simply an attachment. The attachment is a ZIP file with a Word document in it, which contains a Macros script that downloads the ransomware as soon as the victim enables Macros function in Word. Zip archives, as well as Word documents, are named with a random set of digits. Here are some of the malicious email addresses that criminals are using to deliver ransomware to target systems:
- vroak[@]otmail.it;
- clayton.lively[@]cogentpowerinc.com;
- kasserer[@]villingevand.dk;
- rbrown[@]rsu13.org.
Cerber ransomware versions. 2020 guide
Cerber Decryptor
Cerber Decryptor tool has been offered by Cerber ransomware virus authors since its appearance. They have been advertising it as a program that is supposedly the only one capable of recovering encrypted data for the victim. This might not be true because you can never rely on cybercriminals. This piece of malware can be bought in Bitcoins, but there is no information whether it decrypts files or not.
Even if it does, remember that criminals can send it to you in a bundle with malicious files or Trojans, which can cause further security problems to you. Malware researchers have always been suggesting not to rely on cyber criminals and decryption services that they offer. Besides, paying the ransom would fund their further projects, so you may want to think twice before you reach out for your credit card. The wisest solution is to initiate the ransomware removal right after it shows up on the system. This procedure can save some part of your files from encryption.
Cerber2 Ransomware
Cerber2 ransomware is the second version of Cyber virus. It was released in August 2016, and it seems to be distributed via drive-by downloads, malvertising, and malicious email campaigns. This virus locks the data using a nearly unbreakable encryption algorithm and adds .cerber2 file extension to them.
Once encrypted, files cannot be accessed in any way without having the decryption key. Of course, you can get the decryption key, but crooks ask to pay money for it, in other words, you need to pay a ransom to get your files back. It is strongly recommended not to pay the ransom as Cerber2 decryption tool might have flaws and not decrypt the data entirely. Just like other ransomware decryptors offered by authors, this one can be supplemented with harmful additional files as well. Security experts recommend removing v2 as soon as the victim notices that the computer has been compromised by it and retrieve lost data from backups.
Cerber3 ransomware
Cerber3 is yet another version of crypto-virus that has clear improvements in its code. This new version of this ransomware has also been considered to be more malicious and destructive as the hackers had plenty of time to fix the bugs found in the previous two versions. The second version of this ransomware was found by security researchers in the middle of September 2017. After appending .cerber3 file extension to the encrypted data, it drops the ransom note called # HELP DECRYPT #.html.
The virus was actively spread via Ammyy Admin web page[6] which was infected with the malicious file for several days, approximately from the 13th to 15th of September. The binary, which was entitled as an encrypted.exe, was placed in AA_v3.exe. Previously, this domain was assaulted by other highly damaging malware in the future. At the moment, the website is fully restored and safe for public use.
Cerber 4.0
Cerber 4.0 is yet another vicious version of ransomware. This virus does not use previously-used extensions anymore. It has improved its encryption algorithm and now displays extensions consisting of a jumble of different numbers instead. Besides, according to the virus creators, this new version of the virus is much more resistant to antivirus detection and manages to disguise its activity on the computer until all of the files are encrypted.
Talking about files, it has been found that Cerber v4.0 is now capable of encrypting even more file types which only proves that ransomware developers are not hanging around and are ready to exploit as many users as possible. For this purpose, they have also released the RaaS version of malware which can be obtained on the dark web. Currently, experts count three main distributors of this malware, but it is very likely that more cyber crime enthusiasts will join in.
Cerber 4.1.0 ransomware
Cerber 4.1.0 ransomware differs from the previous versions mainly due to appended extension. While previously, .cerber2 and .cerber3 extensions were the trademark signs of the versions, now the virus leaves 4-digit extension or adds no extension at all.
Another major improvement lies in the distribution. PseudoDarkleech Rig exploits kit helps transfer the malware. On the other hand, such discovery will help the virus researchers to publish the decryption key and issue prevention measures sooner. The improved version also sends the request of a specific HTTP. It results in retrieving JSON file which contains payment instructions. It links to 17gd1msp5FnMcEMF1MitTNSsYs7w7AQyCt bitcoin address. Though there are more technical details revealed, it still makes Cerber ransomware virus a terrifying cyber infection.
Cerber 4.1.1 version
Cerber 4.1.1 version comes in the “bonus” package along with 4.1.0 version. Since it is little known about the exceptional features of this edition, there are many speculations about its capabilities. It is likely to spread via the same exploit kit as 4.1.0 version. Virus researchers have noticed that ransomware has changed its IP address again. Such strategic move makes the tracking of the infection source more complex.
In order to generate 4-digit code, the ransomware employs a complicated registry segment called “MachineGun”. It is an integral part of the entire HKLM\Software\Microsoft\Cryptography key. Taking into account, these peculiarities complicate the elimination of the threat. That is why a proper security application is a necessity.
Similar infections await for victims in file-sharing networks or other questionable domains. It is unwise to consider remitting the payment as several versions of the malware have already gained millions of dollar profit and the developers are unlikely to send the decrypter.
Cerber 4.1.4 virus
Cerber 4.1.4 virus showed up right after the appearance of 4.1.1 version, and these viruses are very similar. They both encrypt files using the same methods, corrupt the original filename and append a customized four-character extension instead of the original one. Ransomware roots deeply into the system, adds registry keys, alters values, drops its components to the %TEMP% folder and other locations across the entire computer system to make it harder to remove.
Each component is extremely dangerous, and it is a must to remove them all at once to ensure a successful Cerber 4.1.4 removal. This virus strongly encrypts personal data without any shame and demands a ransom in exchange for Decryptor. No matter how hard malware analysts try, they cannot break this virus' obfuscation layers and find out what algorithm is used to generate unique encryption/decryption keys for the victim. Sadly, files encrypted by this version cannot be recovered with any decryption tools.
Cerber 4.1.5 ransomware
Cerber 4.1.5 ransomware appeared at the beginning of November 2016, and successfully infected hundreds of computers already. This version copies techniques used in the past and hardly differs from previous versions. Encrypted files become unrecognizable because virus scrambles their filenames; however, the virus creates a unique file extension for each victim and appends it to encrypted records. It leaves a ransom-demanding message in README.hta file, which points to personal payment websites.
The victim is asked to pay 0.6967 BTC, which equals to $500, or more if he/she fails to pay up in the given term. Cerber 4.1.5 reportedly spreads with the help of notorious Neutrino and RIG exploit kits, malvertising, and of course malware-laden emails. You can protect your PC from this ransomware by stockpiling data backups and installing trustworthy anti-malware software.
Cerber 4.1.6 ransomware
Cerber 4.1.6 ransomware emerged at the end of November 2016, more or less after a month after the appearance of the 5th edition of the fourth ransomware version. This modification of the virus has no outstanding improvements and functions just like its former versions do. The virus merges RSA and RC4 encryption algorithms to create an uncrackable cipher that renders personal files, documents, databases, and other important files useless.
The ransom price is 501$, and criminals command the victim to transmit this sum of money via Bitcoin system within five days; otherwise, they increase the ransom price. This sequel to the infamous project is just as dangerous as its predecessors, and it also connects every compromised PC into a botnet to carry out DDoS attacks. Victims of the 4.1.6 version should remove the virus as soon as possible and perform several system scans to thoroughly analyze the computer and remove all malicious files and ransomware remains.
Cerber 5.0 ransomware
First spotted in late December 2016 to March 2017, Cerber 5.0 ransomware, was another version released by developers in the hopes of snatching more money from virus victims. This variant of the family was spread with the help of malicious executables falsely signed by legitimate companies that provide certifications.
Once inside the system, the virus will check if there is one of the following anti-virus installed on the system: ArcaBit, ArcaVir, Avast, Bitdefender, Bullguard, CA, Emsisoft, ESET, eScan, eTrust, F-Secure, G Data, Kaspersky, Lavasoft, or TrustPort. If one of these apps is present, the ransomware will not initiate the infection procedure.
In case the opposite is true, Cerber 5.0 ransomware will disable the Windows startup repair function, delete Shadow Volume Copies, and terminate the following processes:
- excel.exe;
- infopath.exe;
- msaccess.exe;
- mspub.exe;
- onenote.exe;
- outlook.exe;
- steam.exe, and a few others.
After that, ransomware will encrypt all personal files located on the computer, although it will skip most of the viral system files, such as boot.ini, .desktop.ini, .iconcache.db, .ntuser.dat, etc. Just as its predecessors, this variant will drop a ransom note (although named differently – README.hta), where crooks will ask users to click on a provided link that would direct them to a personal payment/contact page. As usual, users should not give in to crooks' demands, as they might lose the money, along with encrypted files.
Cerber 5.0.1 ransomware
Cerber 5.0.1 ransomware was quickly launched to back up the previous infections. It keeps encrypting files with RSA-2048 and AES-256 algorithms. That is why users, entrapped by Cerber ransomware, might comply with the hackers' demands to retrieve the files. Needless to say, it is not recommended to transmit the money as there are few guarantees of getting it back. This version has been spreading as a fake email warning with huge billing sums.
The virus urges a victim to open the attachment which would activate a VBA script. Afterward, it will execute the .exe file which downloads the main file of the infection. It also disguises its processes in Task Manager to lower the risk for users to spot ominous commands. Do not waste and eliminate the threat before it causes more severe outcomes.
Red Cerber ransomware
Red Cerber ransomware. This version has been detected on the eve of 2017. In comparison to previous variations, the gearheads introduce several changes in the overall design and operation peculiarities. One of the key modifications was the disabled command to delete shadow volume copies. Likewise, it gives hope for its victims to recover the encrypted files.
What is more, it employs additional tools for delivering a blow to a virtual community. Along with spam emails, RIG and Nemucod exploit kit are also employed to increase the number of victimized systems. Compromised and corrupted domains also serve for spreading this virus.
Keep in mind that the corrupted version of Adobe Flash Player also might disguise Red Cerber malware. There are also a few modifications concerning encryptable file formats. Its developers add 50 file extensions which the virus aims to encode. However, a few, mainly system executable files, such as .exe and .bat, were excluded from the list.
Help_help_help ransomware virus
Help_help_help ransomware virus. After taking a short break during the holidays, the cyber villains introduced the modified version of Red Cerber. The key changes include the introduction of the demands in the *help_help_help[random characters]*.hta file. The version which is found by TrendMicro as RANSOM_CERBER.F117AK[7] avoids firewalls, antivirus software or antispyware products.
The penetrators also added an improved Nemucod exploit kit. Needless to say that such improvements only elaborated the infection even more. The key astonishing feature of malware lies in the execution process. Nemucod exploit kit delivers cer.jpg file into your system. After it sets foot on the operating system, it performs a metamorphosis: the file changes into .exe file.
Consequently, it becomes only a matter of seconds when help_help_help virus completes its hijack. After encrypting target files, the virud drops a ransom note called _R_E_A_D___T_H_I_S___[random]_.txt or _R_E_A_D___T_H_I_S___[random]_.hta. The ransom note starts with a different line than the rest of Cerber ransomware virus ransom notes – it says “Hi, I'am CERBER RANSOMWARE 😉.” The virus asks for half a Bitcoin (around $1195) and increases this price to 1 BTC in 5 days.
Cerber 6 ransomware virus
Cerber 6 ransomware virus. While a while has passed since the last version of Cerber, the developers used this time to improve and craft this crypto-malware to a new level. The latest version, the 6th installment, presents improved anti-sandboxing and anti-VM features. In other words, it is able to avoid detection in virtual machines which complicates the developing counterattack strategies. It is also known to use SFX files, i.e. self-extracting files.
In response to wider public awareness about the distribution of this malware, the felons look for ways how to execute the malware with minimal users' interference. The use of multiple and diverse hacking techniques explains why ransomware remains the biggest cyber issue.
Besides disguising in spam emails, it also employs exploit kits, trojans, and bugs in well-known program utilities to multiple its damage on the virtual community. At the moment, there is no decryption software released for this version. However, some of our recommended options at the end of the article might be effective.
Magniber ransomware virus
Magniber ransomware virus. This version of crypto-ransomware has been spotted by Michael Gillespie on October 14, 2017. It can be recognized from .ihsdj or kgpvwnr extensions which it adds to encrypted records. The virus was initially called My Decryptor ransomware. Later on, a group of security researchers spotted a massive malvertising attack closely related to Magnitude exploit kit which filters victims based on their geolocation and language used in the computer. The exploit kit targets CVE-2016-0189 vulnerability in Internet Explorer and if the target meets the requirements, infects the system with Magniber virus.
The name of the ransomware derives from Magnitude + Cerber. The malicious virus is surprisingly similar to the latest Cerber malware variants. However, technical similarities are not the only thing that makes security researchers wonder about the origins of Magniber. It appears that the ransomware activity has slowed down during October, which gives the base for thinking that cybercriminals were creating a new and possibly more dangerous ransomware variant.
The malicious software appears to be targeting people from South Korea only. Of course, this location-based ransomware variant can turn to other world countries at any time, so we strongly advise you to protect your computer and create a data backup. This ransomware encrypts files only to demand a ransom via My Decryptor page (accessible via Tor browser) and demands 0.2 Bitcoin ($1100). If the victim decides not to pay, the ransom price increases to 0.4 Bitcoin after 5 days.

Closer look at ransomware distribution
Reportedly, malware is currently trying to involve other cybercriminals to join its affiliate network and allows them to distribute this virus however they want. The original developers of Cerber ransomware virus take part of the profit and allow the affiliates to keep the rest of it.
Be aware that cybercriminals mostly distribute this virus via spam emails, so make sure you do not open any suspicious emails[8] that come from unknown senders. Even most of such malicious correspondence[9] goes to “Spam” catalog, there is no guarantee that a virus-carrying email will not slip to your regular Inbox as well.
So, you should be particularly careful about opening any attachments that come from unknown sources and are accompanied by suspicious emails. Often the cybercriminals will pose as representatives of governmental or law enforcement institutions, so it is recommended that you always check the legitimacy of such emails if you receive any. Cerber ransomware virus can also enter your computer with the help of Trojans[10].
Therefore, you should avoid untrustworthy download websites because you might download an infected file that has this malicious virus carrier attached to it. Needless to mention, you should avoid visiting high-risk web pages and interacting with the pop-ups and other notifications you may encounter there.
The latest ransomware distribution campaign targets vulnerabilities in legitimate software and uses them to push the ransomware into target computers. The only way to protect your PC from being infected is to keep anti-malware software running at all times.
According to PC experts, misleading emails pushing users to pay the ransoms to prevent the infiltration of Cerber have also been detected. Stay away from such email messages and do NOT even think about making these fines! You need to take care of your company's safety instead. Make sure you let your employers know about such attacks and install reliable security software.
Ransomware uses Magnitude and other exploit kits to increase its distribution rate
No need to say that, during all these years of distribution, Cerber ransomware has been expanding and looking for new monetization methods. During a massive attack in South Korea[11] and other Asian countries, cyber criminals who are hiding behind this ransomware used Magnitude exploit kit.
When a user visits a malicious website, the malware checks a few details about the virus in order to decide whether it is worth launching the attack or not. Those “gates” are known as “Magnigate”[12] and are used to check the user’s IP address, ISP, and information about the operating system or web browser. In this way, the virus can launch targeted attacks and avoid infiltrating random computers.
As a result, this crypto virus has been actively attacking companies and their computer networks. Interestingly enough, in addition to Cerber encryption, people hiding behind this virus threaten their victims to launch malicious DDoS attacks[13] that will supposedly disturb the company's network and its overall operation. Hackers start with the threat email which warns about the upcoming attack and demands to pay a set amount of ransom. After that, the amount of money is said to increase.
Donoff Trojan downloader is used to extract malicious Cerber's code
The virus is still actively distributed in December 2016. According to a report from Microsoft, Cerber ransomware is rapidly proliferating with the help of an email spam campaign, which delivers password-protected .zip archives. Typical email subject lines contain words like “Howdy,” “Hi” or “Hello,” and a very short message asking to view the contents of the attached file, and providing a password to the attachment. Once extracted, files inside this archive activate malicious macro scripts that download Donoff Trojan downloader, which downloads the ransomware to the computer system.
In addition, it is still actively distributed via the RIG exploit kit. The victim only needs to enter a site that hosts an exploit kit to allow it to exploit security vulnerabilities in the system and download the ransomware without the user's consent. The virus has also been noticed proliferating its copies via compromised websites that host the Nemucod virus. These sites can easily redirect the victim to Pseudo Darkleech, which strongly obfuscates the infection when Nemucod drops ransomware virus on the victim's computer system.
Speaking of the virus' code, we must point out that the virus has changed the font background color from bright green to red. On top of that, the latest version of the virus doesn't touch Volume Shadow copies[14], which basically are a door to data recovery. With tools like ShadowExplorer, you can restore at least part of the data encrypted by this ransomware virus!
Ransom.Cerber can also abuse Apache Struts 2 vulnerabilities
In April 2017, researchers identified new mutations in the distribution of this virus. This time, people behind Cerber project targeted vulnerabilities in Apache Struts 2 on Windows servers. To begin with, Apache Struts is a free and open-source framework for creating Java web applications.
It turns out that malware distributors have been attacking systems running programs created with Apache Struts and setting up backdoors, enrolling devices into DDoS bot networks, placing cryptocurrency miners, and of course, malicious viruses like ransomware on compromised machines.
The vulnerability in Apache Struts software allowed criminals to target servers instead of individual computers, providing them with chances to reach potential victims that surely have money and most likely are willing to pay up just to get the control of the data back.
The attackers used an exploit code that allowed them to run shell commands, launch the BITSAdmin utility, and finally download Cerber ransomware from a remote server. Now, researchers have discovered that this particular piece of ransomware modifies Windows Firewall rules and prevents communication from installed antivirus to the world, making it impossible to install antivirus updates or sending reports to the developer. According to researchers, the Bitcoin wallet address used by this version of the infamous ransomware remains the same.
While the discussion about Cerber ransomware has tied down, users might have let their guard down convinced that the malware has faded into oblivion. Such thinking might be perilous, as the hackers are yet to strike again. Recently specialists have detected this menace hidden in Dropbox files. While in the case of ordinary spam messages, a user still needs to extract the attachment in order to activate the infection.
The developers found a workaround to this feature and spread this crypto-malware via self-extracting Dropbox files. Luckily, they still need to be “clicked” in order to inflict damage. There is another wave of this malware coming: TrendMicro virus report reveals multiple new versions of the threat: Ransom_Cerber.R000C0DD517, Ransom_Zerber.R08NH0CD317, etc.
The report also reveals that the latest version is also able to avoid machine learning detection by security applications[15]. Continuous re-loading of the executable files prevents detection. However, specialists reassure that multilayer security software is still a proper solution when dealing with ransomware virus.
Recovering locked data: free Cerber decryptor can help users infected with .cerber and .cerber2 versions
In August 2016, malware researchers managed to find some flaws in the ransomware project and launched a site that allowed victims to decrypt .cerber and .cerber2 files for free. Although the authors of this site do not provide any information on how did they manage to defeat the ransomware, some security experts had guessed that they have managed to find out what the Master Decryption Key is. It appears that this was not true, and most likely they have found a flaw in the virus C&C server. Reportedly, hundreds of victims who followed news about the virus managed to decrypt their precious files for free.
Sadly, organized criminals quickly found the flaw and patched it, so as a result, it is no longer possible to decrypt files using this decryption service anymore. What is more, Cerber's payment site has been improved by adding a Captcha system, which helps to avoid automated attempts to access the site.
It seems that this gang is well-organized and determined to keep this virus undefeatable, which is a horrifying fact. Therefore, computer users are advised to take precautions, create data backups and protect computers with proper anti-virus solutions to prevent a ransomware attack, because, at the moment, there is no way to recover encrypted data using decryption tools.
No way to recover other files locked by the infamous virus
Unfortunately, it is impossible to decrypt the files locked by Cerber ransomware without paying the ransom. However, it is not recommended to pay up[16] because:
- It only encourages cybercriminals to continue their fraudulent activities and create more computer viruses;
- Plus, bear in mind that there is NO guarantee cybercriminals are actually going to help you to recover your files;
- You may not receive the decryptor at all, even if you pay up.
- Also, this tool may be corrupted, bring other malware on your computer, and this way, damage it even more.
Therefore, you should not collaborate with cybercriminals on any level, because their main intention is to make money, and they will do their best to make their efforts pay off.
Deleting the virus from your computer will not help to eliminate the cipher from the files. Trying to recover your files using the hacker-suggested Cyber decryptor tool is not safe either. The best decision is to turn to some more reliable ways to recover your data. The quickest and safest way to achieve that is by importing your data from a backup device.
We strongly recommend you NOT to keep the copies of your data on online storage clouds, because some viruses can access them via your Internet connection and corrupt them, too. It is best to keep your files stored on some external drive and update it regularly[17]. But there are risks here too.
If the external drive is plugged into the computer at the time of the virus infiltration, the files in the storage will most likely be encrypted too. So, make sure that you unplug the external storage device from your computer every time you back up some files. If you do not have a backup, you might want to try these decryption tools – Photorec, Kaspersky virus-fighting utilities, or R-Studio.
Keep in mind that you must eliminate the Cerber virus from your device completely before you attempt to recover your files in either of the ways mentioned above. You can do that using anti-malware software like FortectIntego.
Cerber ransomware removal guide
There is no doubt that ransomware is one of the most dangerous computer viruses of today. Computer experts are still working to create a decryption tool to help its victims decrypt their files, but, at the time of writing, there is only one legitimate decrypter that should be tried to recover the encrypted files without paying the ransom.
It is provided in the “Recover your data” section. Besides, if you are infected and cannot open your files, we suggest you follow optional recovery solutions created by our tech experts to finish Cerber removal from the system.
However, before you try them, make sure you remove this ransomware as soon as possible. Don't forget that it is a dangerous and well-structured computer threat, so you should opt for a professional malware removal tool to eliminate the ransomware from a victimized computer fully. If the removal procedure did not go as smoothly as you expected, you can try the instructions provided below. Once you unblock your virus remover, try scanning your computer again.
Getting rid of Cerber virus. Follow these steps
Identify ransomware affecting your PC
Modern-day ransomware had its roots in the early 2010s when cybercriminals began to understand the potential it has for money extortion. Over the years, thousands of new ransomware strains have been developed and spread all over the world, infecting regular consumers, small businesses, and high-profile organizations.
Because of the lucrative nature of ransomware, cybercriminals are creating new ransomware versions in the hopes of establishing themselves in this illegal business. Ransomware often uses different extensions, ransom notes, and other attributes that it can be identified by. However, quite often, this information can overlap or simply not be available, so identifying the threat might be difficult.
In order to deal with ransomware infection effectively, you must first identify it. Here are a few examples of how to determine the precise ransomware you are dealing with:
File extension
Almost all modern ransomware viruses are using extensions that are appended at the end of the original filenames. However, this is not a rule, and in some cases, cybercriminals change the name by replacing it with randomly generated characters, add the marker before the file name, or do not visually change the name of the file at all.
Here you can see an example of a unique extension .hhmgzyl that belongs to the Snatch ransomware family:
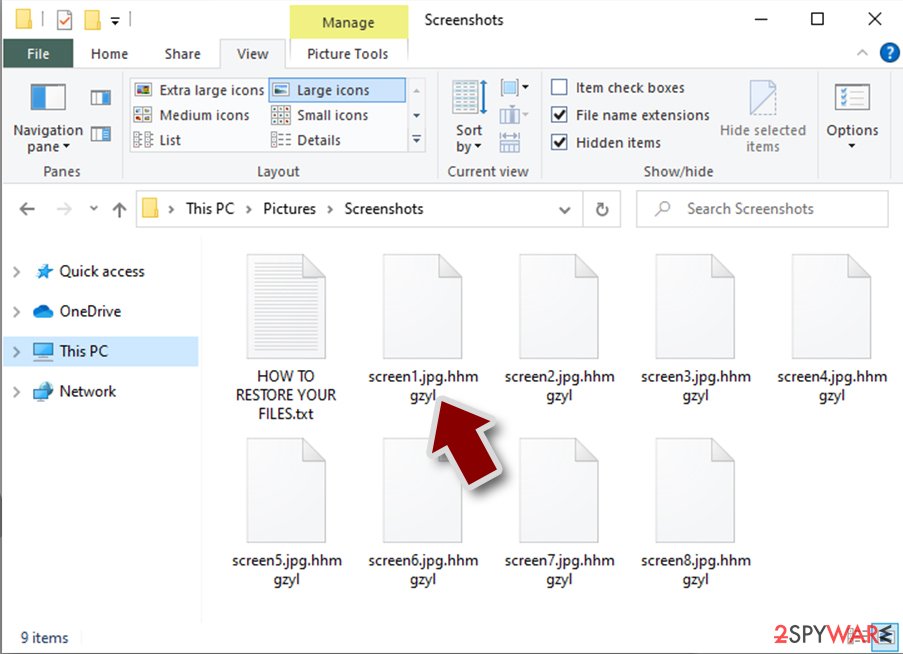
If your files are appended with .exe, .locked, .encrypted, or other broadly-used extensions that are difficult to identify, proceed with the next step.
Ransom note
Ransomware family might sometimes be identified by the ransom note it uses. In most cases, cybercriminals create a simple .txt file and place it on users' desktops or other places that are easily reachable (typically, where the encrypted data is located). Other times, a pop-up window can also be used, which is launched as soon as the encryption is complete. In some cases, threat actors name the ransomware within this note:
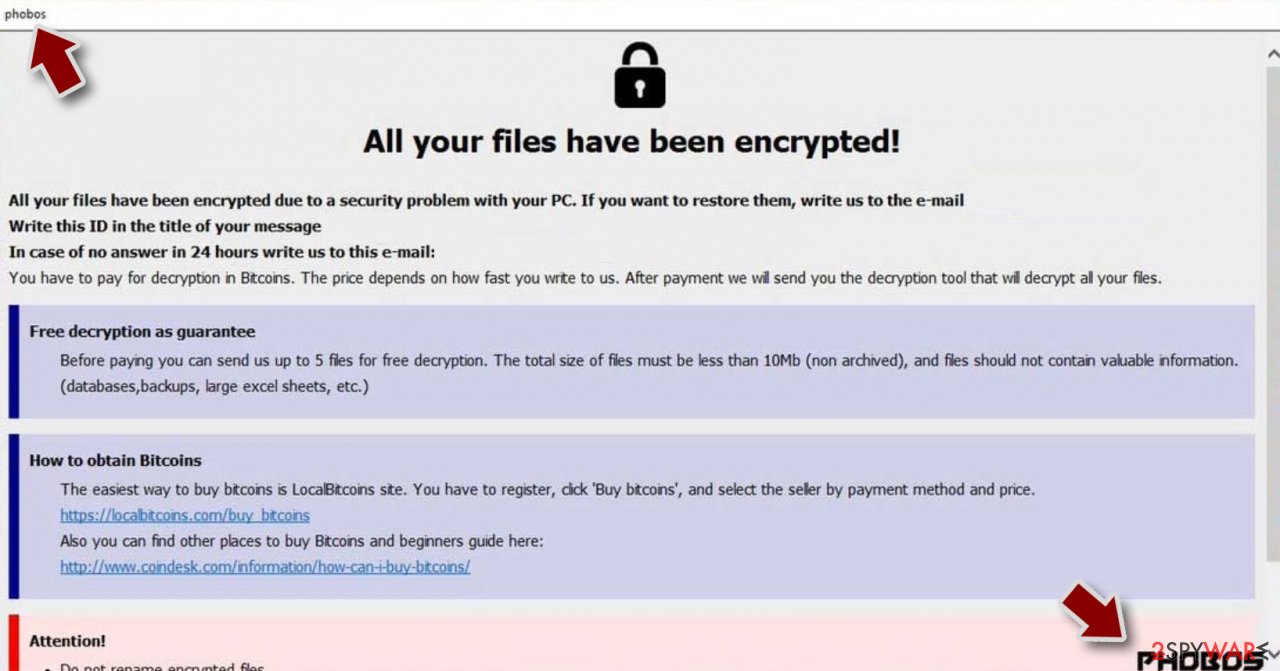
In some cases, it is possible to identify ransomware by its ransom note name, but they are typically very generic (e.g., FILES ENCRYPTED.txt, _readme.txt) and used by different cybercriminals groups.
Free ID Ransomware service
ID Ransomware is a free service that can easily let users identify the precise malware they are dealing with. All you have to do is upload the ransom note that can be found on the desktop and within folders where encrypted files are located and the sample of an encrypted file.
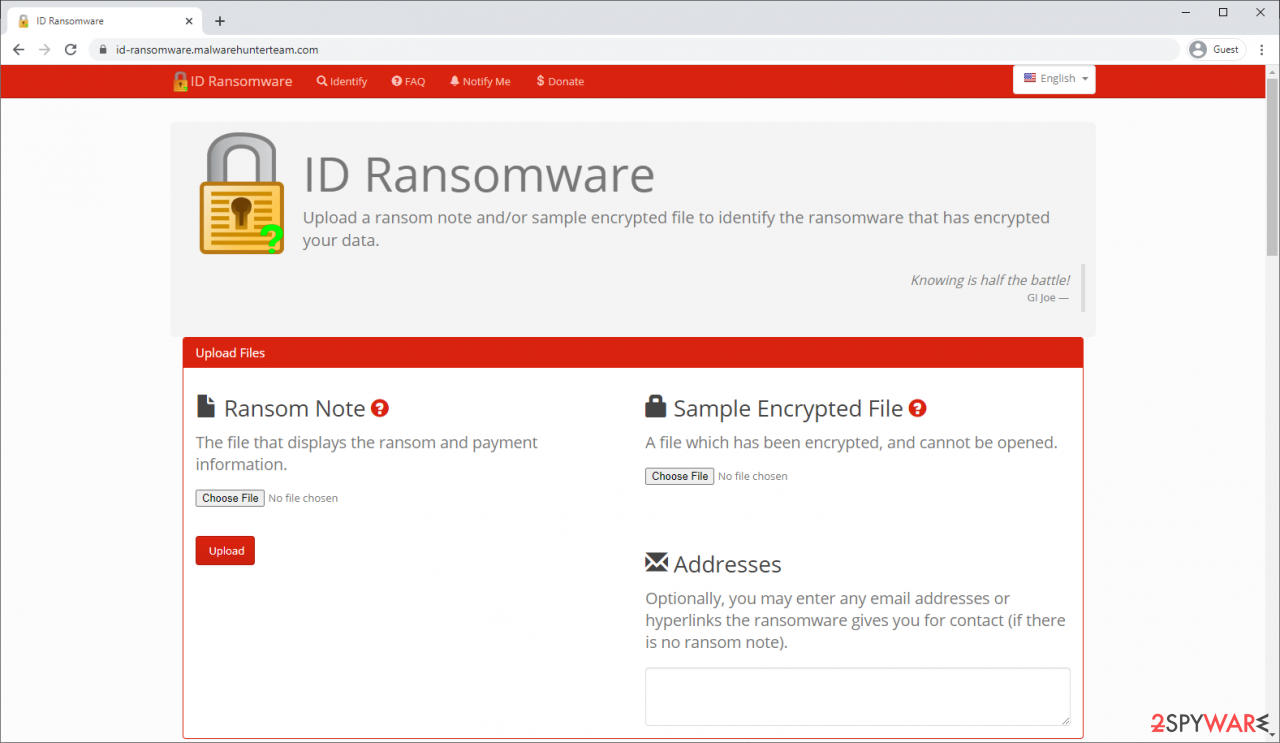
Soon after uploading the required files, you will be provided with all the relevant information, including what family ransomware belongs to and whether or not it is possible to decrypt files.
If none of the above helped you to identify which ransomware you are dealing with, you should use keywords (extension, contact email, ransom note contents, crypto-wallet address, etc.) to find the information on the internet.
Scan your system with anti-malware
If you are a victim of ransomware, you should employ anti-malware software for its removal. Some ransomware can self-destruct after the file encryption process is finished. Even in such cases, malware might leave various data-stealing modules or could operate in conjunction with other malicious programs on your device.
SpyHunter 5Combo Cleaner or Malwarebytes can detect and eliminate all ransomware-related files, additional modules, along with other viruses that could be hiding on your system. The security software is really easy to use and does not require any prior IT knowledge to succeed in the malware removal process.
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
Restore Windows "hosts" file to its original state
Some ransomware might modify Windows hosts file in order to prevent users from accessing certain websites online. For example, Djvu ransomware variants add dozens of entries containing URLs of security-related websites, such as 2-spyware.com. Each of the entries means that users will not be able to access the listed web addresses and will receive an error instead.
Here's an example of “hosts” file entries that were injected by ransomware:
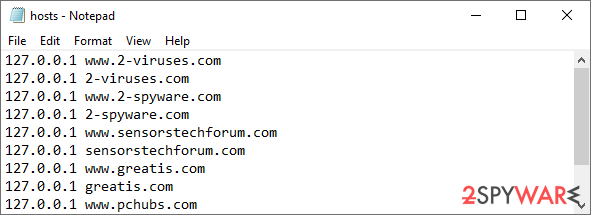
In order to restore your ability to access all websites without restrictions, you should either delete the file (Windows will automatically recreate it) or remove all the malware-created entries. If you have never touched the “hosts” file before, you should simply delete it by marking it and pressing Shift + Del on your keyboard. For that, navigate to the following location:
C:\\Windows\\System32\\drivers\\etc\\
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Find a working decryptor for your files
File encryption is a process that is similar to applying a password to a particular file or folder. However, from a technical point of view, encryption is fundamentally different due to its complexity. By using encryption, threat actors use a unique set of alphanumeric characters as a password that can not easily be deciphered if the process is performed correctly.
There are several algorithms that can be used to lock data (whether for good or bad reasons); for example, AES uses the symmetric method of encryption, meaning that the key used to lock and unlock files is the same. Unfortunately, it is only accessible to the attackers who hold it on a remote server – they ask for a payment in exchange for it. This simple principle is what allows ransomware authors to prosper in this illegal business.
While many high-profile ransomware strains such as Djvu or Dharma use immaculate encryption methods, there are plenty of failures that can be observed within the code of some novice malware developers. For example, the keys could be stored locally, which would allow users to regain access to their files without paying. In some cases, ransomware does not even encrypt files due to bugs, although victims might believe the opposite due to the ransom note that shows up right after the infection and data encryption is completed.
Therefore, regardless of which crypto-malware affects your files, you should try to find the relevant decryptor if such exists. Security researchers are in a constant battle against cybercriminals. In some cases, they manage to create a working decryption tool that would allow victims to recover files for free.
Once you have identified which ransomware you are affected by, you should check the following links for a decryptor:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

If you can't find a decryptor that works for you, you should try the alternative methods we list below. Additionally, it is worth mentioning that it sometimes takes years for a working decryption tool to be developed, so there are always hopes for the future.
Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Cerber and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ What is Cerber Ransomware? Everything You Need to Know. Avast. Security blog.
- ^ Margaret Rouse. Advanced Encryption Standard (AES). SearchSecurity. Information Security information, news and tips.
- ^ Stuart Dredge. What is Tor? A beginner's guide to the privacy tool. The Guardian. News portal.
- ^ David Bisson. Cerber Ransomware Now Capable of Stealing Bitcoin Wallet Files. Tripwire. IT Security News & Blog.
- ^ Nicholas Ramos. KOVTER and CERBER on a One-Two Punch using Fake Delivery Notification. Trustwave. Helps businesses fight cybercrime, protect data and reduce security risk.
- ^ Catalin Cimpanu. Ammyy Admin Website Compromised to Spread Cerber 3 Ransomware. Softpedia. Free downloads encyclopedia.
- ^ RANSOM_CERBER.F117AK. TrendMicro. Threat encyclopedia.
- ^ Maria Korolov. 93% of phishing emails are now ransomware. CSO. Security news, features and analysis about prevention, protection and business innovation.
- ^ Justin Luna. Microsoft warns holiday shoppers of phishing email carrying Cerber ransomware. Neowin. The website about technology industry news.
- ^ Margaret Rouse. Trojan horse. SearchSecurity. Information Security information, news and tips.
- ^ Jérôme Segura. Enemy at the gates: Reviewing the Magnitude exploit kit redirection chain. Malwarebytes Blog. The security blog.
- ^ Kafeine. Magnitude Actor Adds A Social Engineering Scheme For Windows 10. ProofPoint. Cybersecurity Solutions.
- ^ What is a DDoS Attack?. Digital Attack Map. Visual representation of DDoS attacks worldwide.
- ^ No slowdown in Cerber ransomware activity as 2016 draws to a close. TechNet - Microsoft. The home for all resources and tools designed to help IT professionals succeed with Microsoft products and technologies.
- ^ Ransomware Recap: Old Ransomware, New Features. TrendMicro. Cyber Security Solutions.
- ^ Cadie Thompson. Why you should never pay hackers if they take over your computer. Business Insider. Business and Investment news.
- ^ Sarah Mitroff. Back to basics: The three easiest ways to back up your files. CNET. Product reviews, how-tos, deals and the latest tech news.


































