Apple virus (guide) - 2021 update
Apple virus Removal Guide
What is Apple virus?
Apple virus is a type of Mac infection that delivers fake notifications via the web browser or other methods
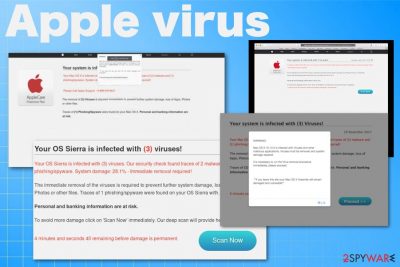
Apple virus is a term that includes various technical support scams, adware-type threats, and other malware designed to infiltrate Mac devices. Various support scams and phishing campaigns[1] target this ever-growing operating system to get valuable information or money directly from the victim.[2] Mac malware became a real cybersecurity issue in recent years, although people still believe that macOS and iOS machines are safe from viruses and cyber infections in general. This misconception leads to malware attacks or scam campaigns during which your personal information, data, or money, are at risk.
Fake alerts are typically delivered via Safari, Google Chrome, or another web browser that is installed on the system. These scams falsely claim that a virus has been found and that immediate action needs to be taken in order to fix everything – from allegedly stolen passwords to the elimination of the said virus. Keep in mind that these pop-up messages are fake, and you need to ignore them at all costs.
| Name | Apple virus |
|---|---|
| Type | Malware |
| Symptoms | Fake messages with warnings, system alerts, false malware detections |
| Distribution | Deceptive techniques like bundling, other programs, spam email campaigns |
| Versions |
|
| Main tactics | Scare people into calling the provided number or installing suspicious software |
| Elimination | Reliable anti-malware tools and full system scan can help remove the virus |
| system fix | Employ supplementary tools such as FortectIntego to ensure the operation of your Mac has been recovered fully |
Mac malware can be set to generate many functions and affect different parts of the targeted device. The primary goal and tactics depend on the scammer behind the threat. However, social engineering is the primary technique that all these attacks are based on.[3]
You can tell that your device infected when you experience one of several of the following symptoms:
- the device starts behaving erratically and crashes or freezes unexpectedly;
- the machine starts running slow;
- advertisements, banners, and redirects fill up the screen;
- applications, tool, or browser content, appears out of nowhere.
Unfortunately, people believe that the Mac infections are not the real threat and keep browsing various questionable websites where malicious material can be spread. This is the main technique used to deliver various cyber threats, especially the ones that involve scamming people with fake system alerts and messages about malware. This is the reason these notifications appear out of nowhere.
The main target of malware – unaware PC users
Apple virus affects computers, iPads, iPhones, and other devices that run the Mac operating systems. People can fall for the scam when the message resembling official providers appear on the browser, especially when the screen is locked and the only notification is the one stating about malware or system damage issues. In this case, they are urged to dial the given number to contact allegedly legitimate technical support.
When the alert stating about issues related to the machine or possible risks appears to you out of nowhere, there is no surprise that you can be tricked into dialing the number in the alert. However, be aware that the tech giant is not the company that shows messages like this with phone numbers or direct promotional content and eliminate the infection from the computer. You will be connected to fraudsters seeking to trick you into:
- paying for useless services
- downloading fake software
- revealing your personal information
Suspicious notifications removal requires more than leaving the browser tab because such messages result from infection running on your device already. In most cases, the message appears once, and you can exit the browser to end the process. However, clicking on any part of the lock screen and pop-ups can lead to rogue tool installations or continuous messages with fake warnings.
Don't interact with these fake messages and make sure you remove the virus causing them from the system. We highly recommend running a full system scan with your anti-virus software (FortectIntego or similar) to be sure that the virus is completely gone.
Avoiding online scams can prevent serious consequences
Adware is another problem that has been plaguing Mac systems for a while now and remains one of the most eminent threats in the wild. While the infection methods can vary, most users usually install adware unintentionally when establishing shareware or freeware. Another (a relatively large) portion of Apple virus category comes from intentional installation – that often happens when users are unaware that the suggested application is actually adware and will start serving intrusive ads after the installation.
While adware is mostly considered to be a nuisance rather than a real threat, adware, just one type of Mac malware, has been documented much more by security researchers recently. It is true that most adware is quite harmless (although annoying), but some of the ad-supported software crosses the link and heavily modifies the system to perform its ad-serving activities.
The main danger in adware is that users are often linked to phishing or scam sites that prompt download of fake optimization software or attempt to convince users that they need to call a tech support number in order to “fix the malware infection,” which could result in hundreds of dollars in losses.
Therefore, you should not underestimate malware – take care of your computer, and it will save you a lot of stress in the future.
Main types of Apple virus
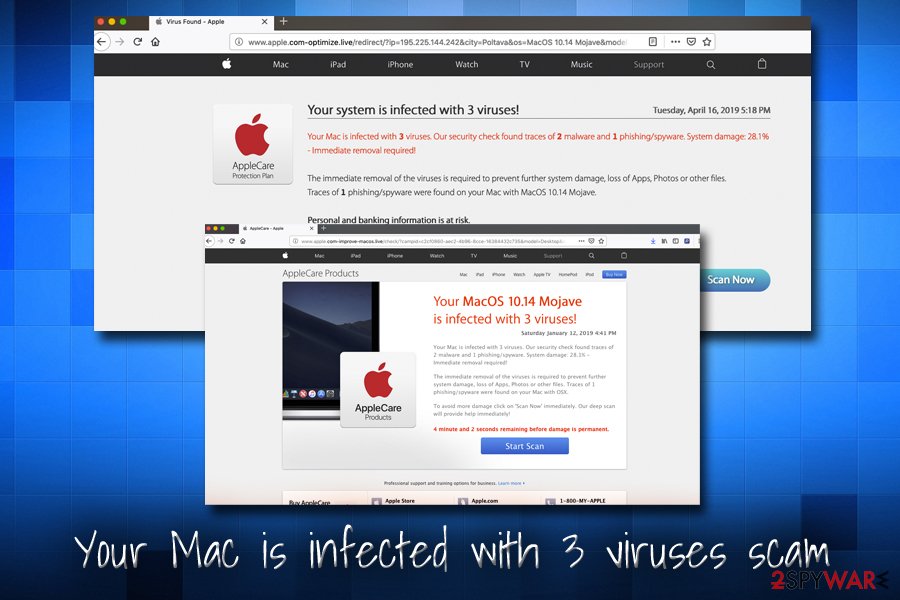
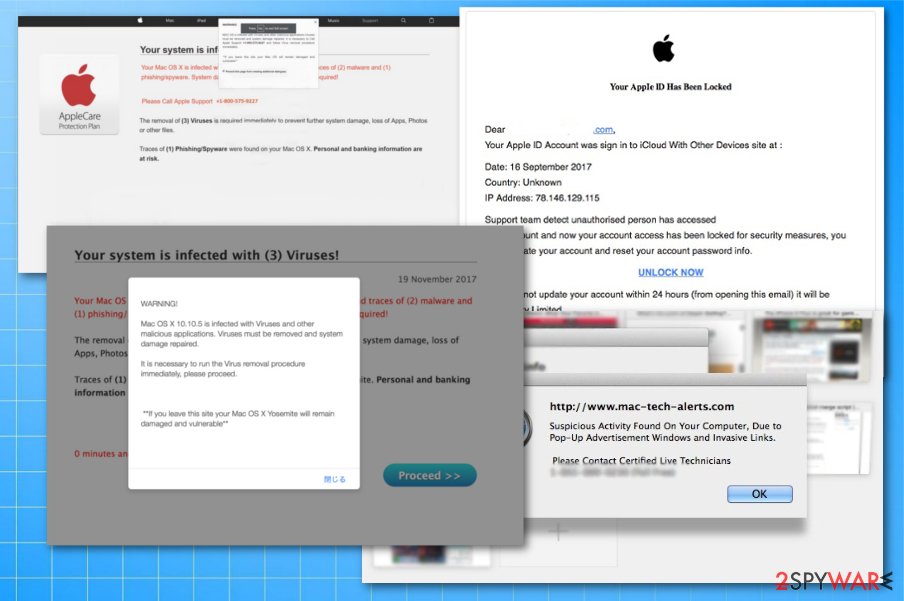
Your Mac is infected with 3 viruses
Your Mac is infected with 3 viruses is one of the most notorious scams out there. Users typically land on the phishing site either accidentally (they get redirected from a malicious site) or if their devices are infected with an adware. While most of the ad-supported programs are installed via software bundles, be aware they might also be found on official sources, so make sure you check some reviews online before installing anything.
Your Mac is infected with 3 viruses scam claims that the computer is compromised and that the personal information like banking details are at risk of exposure. This is a clever trick used by malware creators to scare inexperienced computer users, as they do not understand that malware detection can be only performed by dedicated anti-virus scanners.
If users perform a fake scan, they will be prompted to install bogus software, such as system optimizers like Advanced Mac Cleaner, Driver Tonic or Mac Auto Fixer. In other cases, victims might be asked to call a fake tech support number in order to scam them and pay for the bogus services.
Recently, multiple domains names were created in order to push Mac is infected with 3 viruses scam, which include:
- Apple.com-fasting.live
- Apple.com-faster.live
- Apple.com-fast.live
- Apple.com-monitor.live
- Apple.com-clear.live
- Apple.com-optimize.live
- Apple.com-scan.live
- Apple.com-fixing.live
- Apple.com-speed-macos.live
- Apple.com-improve-macos.live
- Apple.com-scan-macbook.live
- Apple.com-clean-os.live
- Apple.com-repair-os.live
There is no doubt that all these sites are fraudulent, and always claim virus infections (such as e.tre456_ worm_osx, which is fake), as well as the fact that personal information is in danger. The fake site does not only uses a legitimate name but also includes the logo, system version, date, and similar information to deceive the victims and make them believe that these fake warnings are coming from a legitimate company.
However, cybercriminals behind these sites and the scam have nothing to do with the tech giant Apple. Do not be surprised if you encounter Your Mac is infected with 3 viruses messages on other sites as well, however.
In order to stop Your Mac is infected with 3 viruses redirects, you need to terminate the virus from the computer – either scan your device with anti-malware software to get rid of PUPs automatically or delete all the entries manually. Additionally, if you want to make sure your device is running well and all the virus damage is fixed, use FortectIntego.
Warning Virus Detected
Apple Warning Virus Detected is especially prevalent in iOS devices like iPhone or iPad, although desktop users also have seen plenty of similar examples. The pop-up message shows up on Google Chrome, Safari, Mozilla Firefox, Opera, or another browser at any time during the web browsing activities and shows various fake notifications in order to make users call a fake tech support number.
There are many different versions of “Apple Warning Virus Detected” scam in the wild – here is one of the pop-up messages users might encounter:
System Warning!
Apple iPhone is infected with virus and immediate action is required.
Continue and follow the instructions to fix your Apple iPhone. Do not close this window.
**Exit at your own risk**
Other fake messages claim that porn virus has been found or the system has crashed and needs immediate remediation. As usual, all these messages are fake, and you should not pay to any of them, and hurry up and delete the adware infection from your device.
Virus alert from Apple
Virus alert from Apple is another scam that tries to impersonate legitimate technical support by displaying fake messages to users. Before trusting such claims, users should realize that browsers cannot perform any type of system scan, and only dedicated security software can troubleshoot issues and detect malware on the device. Therefore, if you saw any kind of claims that your computer is infected and you need to take immediate action – it is a scam and should be ignored.
The notification might claim that there are several viruses detected on your Mac or iPhone, and also include the IP address, system version, and other details. Unlike virus infections, such information can be scanned simply because your device is connected to the internet – that does not mean that the claims are legitimate.
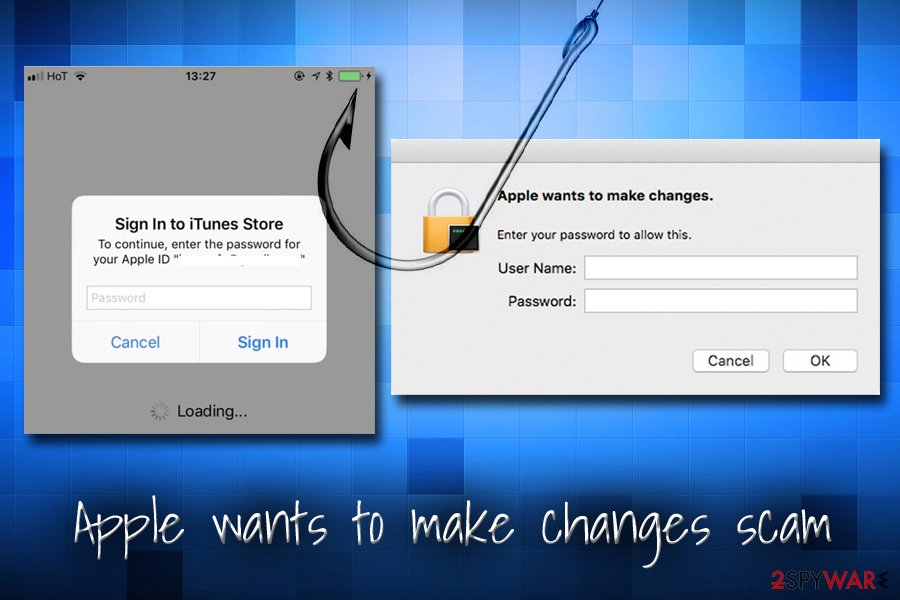
Apple wants to make changes
Apple wants to make changes is a fake pop-up message that might pop-up at any time during the computer operation. Unfortunately, the pop-up window looks identical to the original macOS system prompts, so this time, users might believe that the pop-up is legitimate and comes from Apple.
In reality, it is just another trick used by cybercrooks. It uses legitimately looking pop-up window that asks people to enter their login credentials. While most tech support scams try to make users install suspicious applications like fake optimization tools, this social engineering trick might disclose login details that can later be used to access Mac computer remotely.
In such a case, cybercriminals might access the system and install such threats as keyloggers or info-stealers. These infections can result in money loss or even identity theft. Therefore, never enter your credentials into fake pop-ups and use adware removal tools to stop these unwanted messages.
AppleCare And Warranty
AppleCare And Warranty can be encountered on Safari, Google Chrome, or other browsers. While it has many similarities with other scams that target Mac users, this fake website tries to imitate the original design, mimicking its official website. Crooks simply are trying to make users associate the scam with AppleCare program – extended Warranty for Apple products.
It implies that the system is infected with a virus, although the text is not very believable – most likely written by a non-English speaking person. The fake notification reads as follows:
AppleCare and warranty Internet Security Damaged !!! Call Help Desk at 1-888-621-0834
Suspicious activation detected on, your IP address due to harmful virus installed in your computer. This virus can also damage the firewall security which can result in data loss or hard drive crash. Call immediately on the number provided, to rectify the issue.
We have disabled your computer to stop further damages to your computer. Do not restart your computer or shutdown. It may result in data loss. Please call us immediately to fix your security and to update the service agents of your computer software.
Do not call the provided number, as cybercriminals might convince you to pay the fees for the face services, or ask you to provide remote access to the machine and install spyware to steal your banking or other sensitive details.
Apple Security Breach
Apple Security Breach is a scam message that popups on malicious websites. This technical support scam tries to make users believe that the security of the device was broken and pictures and other data is being transferred to unknown sources. The fake support number provided is 1-800-711-9001, although it might differ.
Additionally, users are also urged to install the alleged protection software:
Call 1-800-711-9001 immediately to connect with Apple Technical Support for installing the Protection Software.
This is another attempt to mimic the industry giant's tech support. However, be aware that the official messages would never prompt you to call anyone. If you need to contact the real tech support, there are several ways of doing so via the official web site. Thus, the URL address is often a quick giveaway when it comes to scam messages.
Apple Security Alert
Apple Security Alert is the scam that shows bogus warnings and aims to scare people with various error messages, including error codes or specific names of malware. The notification provides contact information and suggestions to write or call the technical support team for instructions on fixing the issue. Unfortunately, third-party program installations may lead to malware infections or even hacker attacks on your machine.
All these campaigns often end up in lost information, stolen credentials, or even money from your account. This happens when the victims get tricked into paying for the alleged help, and all those online banking details get captured by keystroke loggers or other malware.[4]
Apple Rewards Event
Apple Rewards Event is another hoax developed by cybercriminals in order to get valuable personal information out of unexpecting users. However, this is not a technical support scam but rather a survey scam – these fake alerts usually target a particular group of people and claim that they are eligible for an expensive gift, such as an iPhone, iPad, or a large sum of money.
Allegedly, all users need to do is answer simple questions in a short survey. Those who get tempted by gifts and proceed with answering the questions (the scam is programmed to work no matter if the answers are correct) eventually land on a page which asks for personal information, such as credit card details. In other cases, users are subscribed to a useless service and charged every month.
Thus, never trust this notification – there are no free prizes around that the company is willing to give away for free.
Apple Security Damaged
Apple Security Damaged is the scam that gets triggered and fake alerts stating that your machine can get damaged appears. Technical support scams like this one aim to make these alerts appear more realistic and this goal is achieved when they show notifications with the original logo or delivers pop-up on the browser resembling the system error messages. People fall for these scams when the message looks legitimate. Unfortunately, scammers get even more creative when it comes to such scam campaigns.[5]
Avoid infections on your device easily
These technical support scams and social engineering attacks are not the threat that affects your machine the most. This is merely a result of a potentially unwanted program or a different cyber threat running on the system already. Silent infiltration methods is the reason why you cannot see the program causing such behavior like redirects and false messages.
Potentially unwanted programs that come from deceptive commercial pop-ups or banners and via software bundling are the ones that cause these scammer attacks. If you want to avoid these infections, always keep paying attention to processes happening on the machine.
By choosing Advanced or Custom installation options instead of Recommended or Quick, you unpack the list of all the includes programs and can choose what to install on the device from the list. Freeware comes bundled with PUPs, and that's how computers get infected with adware and browser hijackers.
Eliminate adware and other malicious software from your device
You should be aware that macOS devices are not immune to cyber threats, although various sources may claim so. When such intruders affect the machine, it shows that your device is infected with the virus and can be damaged if you don't react as soon as possible
Remove the Apple virus as soon as you notice any suspicious message and scammer alerts, even though you exited the window. Staying away from these notifications can help avoid additional malware infiltrations but doesn't help with initial PUP termination.
You can quickly eliminate threats by installing the anti-malware tool and running a full scan on the machine. During such check of all the parts on the computer or device program indicates all errors and real issues with the system, including malicious programs and infected files or PUPs that cause these scary warning.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of Apple virus. Follow these steps
Delete from macOS
To get rid of the infection, clean the machine fully. It will help you spot all related PUPs or malware.
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Remove from Mozilla Firefox (FF)
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Remove from Google Chrome
Check if the browser is not infected with more viruses by using this guide:
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Delete from Safari
To delete unwanted or dangerous apps from Safari, get rid of malicious extensions and other in-browser content that is causing more issues with the browser and machine in general
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

After uninstalling this potentially unwanted program (PUP) and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti-spyware. This will help you to get rid of Apple registry traces and will also identify related parasites or possible malware infections on your computer. For that you can use our top-rated malware remover: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting mac viruses
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Phishing. Wikipedia. The free encyclopedia.
- ^ Rochelle Garner. 'Apple support' phishing scams are getting really good. Cnet. Latest tech news.
- ^ Margaret Rouse. Social engineering. Techtarget. Search security.
- ^ Violet Blue. Keyloggers: Beware this hidden threat. PCworld. News, tips and reviews.
- ^ Aaron Mamiit. New phishing scam targeting iPhone users looks like a real Apple Support call. Digitaltrends. Technology news.
• Polski
• Deutsch
• Français
• Italiana
• Português
• Español
• Svenska
• English (UK)












