Dharma ransomware. 40 Variants listed for 2021
Dharma virus Removal Guide
What is Dharma ransomware virus?
Dharma ransomware is the threat that on average demands $57,000 in cryptocurrency payments
Dharma is a crypto-virus that first struck the world in 2016 and has been resurfacing with new versions regularly during recent years. From the first quarter of 2019 up till now, the virus comes back with new versions. The malware uses a complex extension consisting of user ID, contact email, and an extension, for example – .DEX, .YOUF, .SWP, .Cvc, or .World. Since its release, the AES or DES + RSA encryption algorithms have been used to encrypt data; ransom note titles and contents might vary slightly, although they are typically called either Info.hta and FILES ENCRYPTED.txt.
These documents are asking to contact developers via the provided email address and pay for the decryption service. As long as the virus keeps presenting new file extensions, be careful with unknown emails from suspicious senders since the virus still relies on spam when spreading around. Small businesses and bigger organizations should also be cautious – at the end of March 2019, the malware hit a system of the parking lot in Canada.[1] Previously, Dharma ransomware infected Texas hospitals [2] and some other organizations.
Although the newer samples of this cryptovirus show it is distributed via spam email, they deliver different files in particular campaigns. Researchers revealed new information that malicious actors use download links. When the user clicks on such a hyperlink, the password listed in the email itself can be used to get the particular file.
Once the self-extracting defender.exe file is opened, it drops a malicious file on the system. It appears to be an old version of ESET AV Remover and connects with the virus. During the fake AV tool installation, the malicious code is executed, resulting in computer infection and, later, file encryption.
During the first months of functioning, Dharma ransomware was spreading as an alternative for Crysis ransomware. However, now these viruses are considered to be of a different kind as the most of traits do not match. The ransomware caught attention back in November 2016[3] and was compared with Locky virus.[4] Dharma (.cezar family) and some other versions (Adobe ransomware, Combo ransomware, Java ransomware, Bip ransomware) have proven that the virus is ready for anything.
| Name | Dharma virus |
|---|---|
| Type | Ransomware |
| Danger level | High. Makes system changes and encrypts files |
| Release date | 2016 |
| Ransom note | Info.hta, FILES ENCRYPTED.txt |
| Encryption method | Malware uses AES or a combination of DES + RSA to lock files, depending on the version |
| Distribution | It is mainly delivered via infected email attachments, although other techniques, such as software cracks or fake updates, can be used as well |
| Data recovery | Some versions of the virus can be decrypted with a free RakhniDecryptor |
| Malware elimination | To remove ransomware from your system, you should scan the device with powerful anti-malware software |
| System fix | Malware can cause significant issues after it is deleted from the system (lag, crashes, errors, etc.). In case you experience problems after virus elimination, attempt to fix system damage with FortectIntego |
Since 2016, researchers have revealed over hundred different Dharma ransomware versions, all of which share many similar features and the main difference is the file extension appended. As time passed, experts have been updating the decryption tool which was launched soon after the first appearance of the virus.[5] However, it seems that victims are not capable of decrypting files encrypted by the latest versions.
Even though this crypto-malware has been silent for several months now, it seems to be back with several new versions in 2019, including .USA, .xwx, .best .NWA, .ETH, and .com file extensions. If you think that you are infected, don't waste your time because the more time you give to the virus, the more files it can encrypt. Make sure you disconnect your computer from the Internet and scan it with anti-virus software. Additionally, try Dharma ransomware decryptor (called RakhniDecryptor tool).
Since the end of spring 2020, cybersecurity researcher Jacub Kroustek has started warning people that the Dharma virus keeps evolving with its new variants. In June, criminals released over ten new ransomware variants, the most prominent of which are .base, .R3f5s, .bad, .HCK, .hlpp, .FRM, .WCH, .club, .PGP, .well, .space, .BOMBO.
The virus activity does not seem to end in July. Since the middle of the month, criminals have already released some noteworthy variants that manifest with the following extensions: .data, .smpl, .felix, .null, .gns, .bmtf, .nhlp, .prnds, .dtbc, .BOOT, .GYGA, and others. All these variants are identical, except the email addresses owned by criminals.
On the day of its appearance, security experts didn't know much about Dharma in general and believed it to be one of the new-generation viruses.[6] It seems that the virus developers were trying to keep it as obscure as possible and didn't follow the typical patterns other ransomware creators do.
For instance, the virus did not drop ransom notes or any other additional documents that would let you know about the virus hiding in the system. Also, on the day of virus discovery, November 2016, antivirus utilities did not seem to detect its malicious components, which complicated Dharma ransomware removal significantly. If you think that you are dealing with virus damage caused by this malware, use FortectIntego to double-check the system.
Almost 200 Dharma versions used to infect home users and companies
In 2019, the most widespread ransomware version is known to use .eth, .bip, .cezar and .cesar file extensions. However, new versions keep evolving in 2020 and the criminals keep coming up with new names for the extensions, e.g., .$love and .LOL. Nonetheless, it seems like criminals keep reusing some of the previously-known names, such as LOL Dharma, which was first spotted in 2017.
Before that, the virus used the AES encryption algorithm[7] to encrypt all personal data on the device. It also deletes shadow volume copies on each Windows operating system it infects. Having in mind that the malware has already infected medical organizations and huge companies, encrypted data can be vital, and its recovery can be related to saved or lost lives.
In fact, there are hundreds of versions that come from the Dharma virus family. While some of the versions are extremely prevalent, others manage to merely infect a few victims. Regardless, the impact of the infection is tremendous. Users affected by this malware family can expect to see their files appended with one of the following extensions:
|
|
|
|
|
Once the malware encrypts the victim's files, it drops the brief ransom note on the infected computer, such as this one. As we have already mentioned, the Dharma ransomware virus failed to do that at the beginning of its distribution.
ATTENTION!
At the moment, your system is not protected.
We can fix it and restore files.
To restore the system write to this address:
bitcoin143@india.com
Victims have also reported about seeing this ransom note:
hallo, our dear friend!
looks like you have some troubles with your security
all your files are now encrypted
using third-party recovering software will corrupt your data
you have only one way to get them back safety – using our decryption tool
to get original decryption tool contact us with email is subject like write your ID which your can find
in name of every encrypted file, also attach to email 3 crypted files.
lavandos@dr.com
It is your interest to respond as soon as possible to ensure the restoration of your files because we won’t keep your decryption keys at our servers more than 72 hours in interest of our security
PS. only in case you don’t receive a response from the first email address within 24 hours, please use this alternative email address lavandos@india.com
As you can see, users are asked to contact the criminals via an email address provided in the note and inquire about the ransom needed to recover the affected files. Apart from the email, you will also see .dharma file extension or similar appendix pinned at the very end of the string. For instance, if your file is labeled as picture.jpg, the affected version of the file will be picture.jpg[email_address].dharma or picture.jpg[files.restore@aol.com].bip.
The email address depends on the particular version, so you can be asked to use bitcoin143@india.com, files.restore@aol.com, worm01@india.com (this virus drops worm.exe file on the system), btc2017@india.com, oron@india.com, or another @india.com, beamsell@qq.com, sindragosa@bigmir.net email address. A full list of email addresses:
|
|
|
However, we strongly suggest not to do that. You have absolutely no way of knowing what to expect from this bunch of extortionists and how contacting them might end. It is more reasonable to remove Dharma ransomware and use a free decryptor by Kaspersky. If you continue using your machine with ransomware running on the system, you can put yourself at risk of finding more encrypted data after rebooting the system.
Important information. Speaking of data recovery methods, you can restore your files encrypted by this malware. However, not all versions of the virus have been included in the decryptor's database. Nevertheless, try Rakhni decryptor or ESET Crysis Decryptor to see how it helps. Besides, according to one of the 2-Spyware visitors, he restored his data by using the 7-Zip program as a Dharma ransomware decrypt tool. For more information, see the data recovery methods described below the article.

Dharma ransomware versions described
Oron@india.com ransomware
Oron@india.com ransomware was released as an updated version of the threat which was named according to the file extension it uses. Just like any other dangerous ransomware-type infection,[8] it aims to encrypt important files on the targeted computer to gain illegal profits. The easiest way to recognize the ransomware is to check the file extension — documents encoded by this version are appended with [oron@india.com].dharma extension. It consists of two sections: an actual extension and the email address.
An indication of the email is an attempt to urge you to contact the crooks for the decryption tool. However, if you reach them out via oron@india.com, there is a high risk that they will make you pay without giving the decryption key. Thus, we do not recommend following the rules of the attackers. Luckily, you can restore your files using Dharma Decrypter.
Zzzzz ransomware
Zzzzz ransomware is one of the versions sharing identical extensions with the infamous Locky virus. It is not clear whether virus developers took Locky's idea or they decided to use the same extensions to indicate encrypted files is a sheer coincidence. Despite the odds, these viruses are not related and are based on different codes. Nevertheless, this does not make zzzzz files virus any less dangerous than the nasty Locky virus.
The virus is still encrypting files and making them inaccessible. The reason for doing that – making the user pay the ransom payment for the access key. You may use the Dharma decryptor to attempt zzzzz file recovery, but the most important thing is that you remove the virus from your computer to prevent further damage.
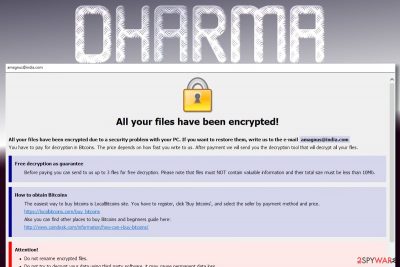
Wallet ransomware
Wallet ransomware is appending .wallet file extension to the encrypted files. Ransomware victims are also urged to contact criminals via the given email address amagnus@india.com and these are the only specific details upfront. The virus makes sure the victims are acquainted with the data recovery conditions by replacing the infected computer's desktop with an image of a ransom note.
Besides, extortionists set a 72-hour limit to pay the ransom and claim that, if victims fail to pay in time, the decryption key will be destroyed and they will lose access to their files forever. Of course, there are always alternatives and you don't have to succumb to the criminals' demands. Just scroll down to the end of this article and check our data recovery options for Dharma ransomware virus.
Onion file virus
.onion file virus was spotted in April 2017. The virus has been spreading via malicious email attachments. Once the victim clicks on an infected attachment, malware sneaks inside the system. On the affected device, ransomware starts a system scan and looks for the targeted file types. For data encryption, it has been using a sophisticated algorithm that prevents users from accessing their files.
The ransomware appends the .onion file extension to the encoded documents, PDFs, video, audio, image files, databases, and other popular file types. Nevertheless, the authors of the Dharma ransomware virus claim that purchasing decryption software from them is the only option to get back access to your data. However, you should not rely on their words. After the attack, you should focus on malware removal and later look for data recovery possibilities.
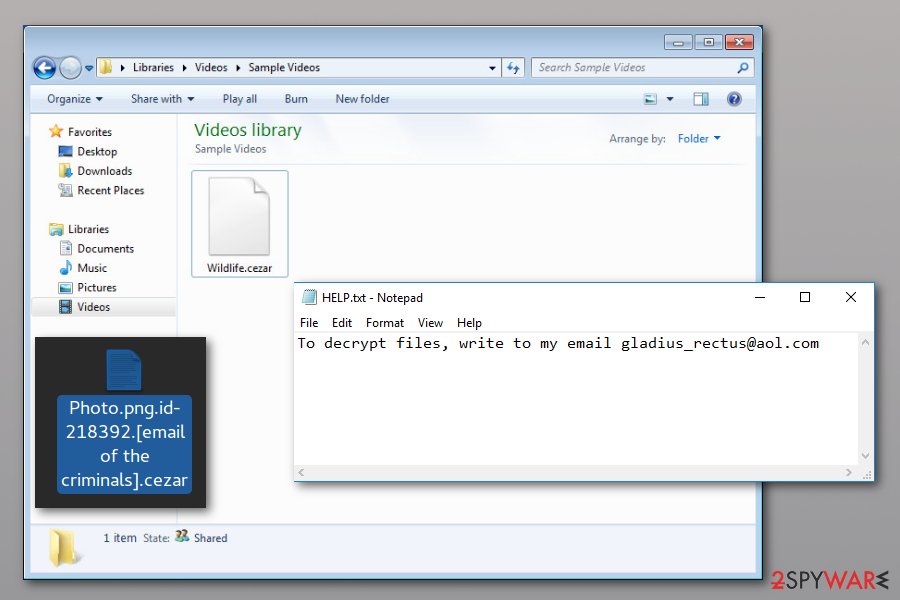
Cezar ransomware
Cezar ransomware emerged in the middle of August 2017. It is also known as Cesar ransomware due to a slightly different extension appended to the target data, respectively .cezar or .cesar. The virus suggests writing to btc2017@india.com for instructions on how to recover encrypted files, so it works as a typical Dharma ransomware version.
The aim of the virus is to force the victim to get in touch with cybercriminals and start negotiations regarding data recovery. The criminals will ask you to pay an enormous ransom in Bitcoins and promise you to provide a Dharma decryption key afterward. Unfortunately, criminals cannot be trusted, so we do not recommend you to put too much effort into trying to make them restore your files. Chances are, they might never will.
Combo ransomware
Combo ransomware was discovered only days after the discovery of other threats. This one is different from others because it uses the same email used by the previously known ransomware – Bip. File extensions are called [Broodmother@cock.li].combo or .[combo@tutanota.de].combo which also includes email addresses that are provided for letting victims know how to reach Dharma virus developers.
The email appears in typical ransom notes Info.hta and FILES ENCRYPTED.txt. However, as we always note, contacting criminals via Broodmother@cock.li or Combo@tutanota.de is not recommended since it may lead to permanent data loss or infiltration of more severe malware.
Arena ransomware
Arena ransomware is yet another addition to Dharma malware family. The virus was spotted by security researcher Michael Gillespie on August 23rd, 2017. The new ransomware variants appends traditional extension – .id-[ID].[criminal's email address].arena. The virus then outputs some text in a FILES ENCRYPTED.txt file (known as a ransom note).
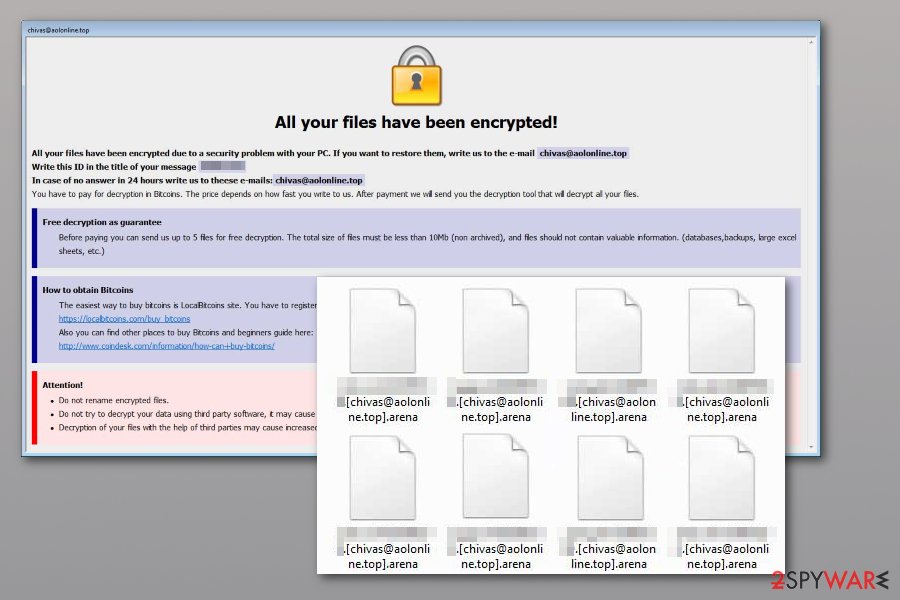
This version of the Dharma ransomware virus has been suggesting contacting the criminals via sindragosa@bigmir.net email address, leaving no hints about the price of the decryption key. Unfortunately, currently, the only tool that could help you restore your files is a data backup. Remove Arena ransomware before trying to plug it into your computer, otherwise, the virus will encrypt files stored on it.
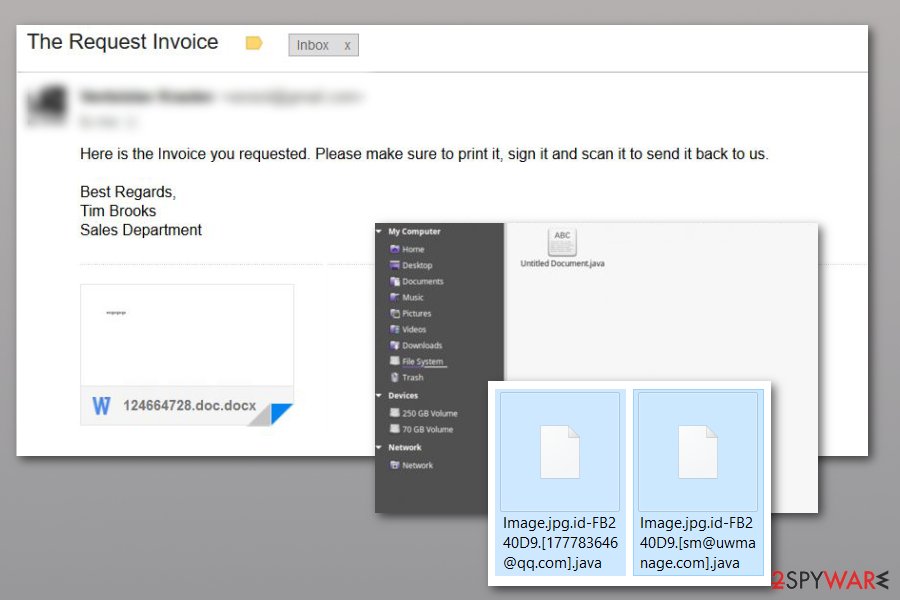
Java ransomware virus
.Java files virus was spreading around the Internet via spam using the subject line “The Request Invoice.” Security experts have been reporting about several new versions attaching these extensions:
- .id-8-characters.[1778357646@gg.com].java[9]
- .[decrypthelp@qq.com].java
- .id-8-characters.[sm@uwmanage.com].java
- id-8-characters.[pain@onefinedstay.com].java (the variant released in July 2020)
It is believed that there are more than three versions of this Java ransomware spreading on the Internet, so be careful while searching the web and ignore the following message:
Here is the Invoice you requested. Please make sure to print it, sign it and scan it to send it back to us.
Best Regards,
Tim Brooks
Sales Department
This Dharma ransomware version also inflicts quite significant damage to the system. It disables system recovery and deletes shadow volume copies. Though it greatly reduces the number of alternative data recovery options, it is recommended to remove the Java virus immediately.
Write ransomware virus
.write file extension virus came out after several months of silence. Even though there are not many changes overall, they have switched to using different file extensions and contact email addresses for identity protection. The upgraded variant is appending .write or [files.restore@aol.com].write file extension after encrypting important data that is stored on the targeted system.
Once the victims receive the ransom-demanding message, they are urged to contact the criminals via files.restore@aol.com email address. However, have in mind that criminals will try to persuade you to make the transaction while you have no guarantees of getting Dharma decryptor.
It is important to know that .write file extension virus is currently undecryptable. Although, it doesn't mean that the only way to get back access to your file is to pay the ransom. There are ways how you can recover data without obeying the demands of the crooks. For that, we recommend checking the decryption steps at the end of this article.
Arrow ransomware
.arrow file extension virus was detected at the beginning of March 2018. Virus analysis points out to .cezar version to be its substruction. Although it's not clear the sum of the ransom demanded, it's clear that extortionists can be contacted via GuardBTC@cock.li, Blammo@cock.li or Bitcoin888@cock.li emails. Consequently, it might be referred to as .id-.[].arrow file extension virus and is a clear example that the developers of Crysis/Dharma ransomware are not going to stop.
Bip ransomware
Bip ransomware came out in the middle of March 2018. Alternatively, it has been known as [Beamsell@qq.com].bip file extension. To make data decryption nearly impossible, the virus has been deleting shadow volume copies and then displaying a ransom note on the victim's computer desktop. The encoded files can only be recovered with the help of extra copies of encrypted files (backups) or RakhniDecryptor tool which was developed by Kaspersky.
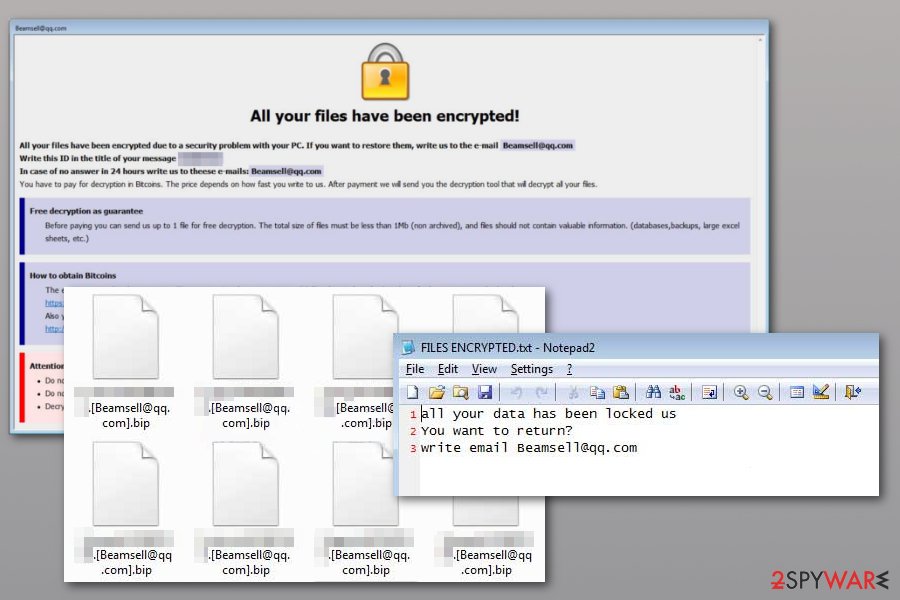
Following the encryption procedure, .bip files virus, in fact, drops two ransom notes in Info.hta and FILES ENCRYPTED.txt where victims of ransomware are asked to send an email to Beamsell@qq.comi to get data recovery instructions. It’s unknown how much money Dharma virus developers are asking to pay; however, it’s still not worth paying them. We recommend focusing on Bip removal instead.
Java2018@tutaio.arrow virus
.java2018@tuta io.arrow file extension virus emerged at the end of May 2018. It uses .[email].arrow file extension to the appended files. Immediately after the encryption, ransomware downloads a ransom note where victims are asked to contact crooks immediately. The faster they write, the less they need to pay, according to the ransom note.
Crooks behind this Dharma virus version are using two contact email addresses java2018@tuta.io or java2018@india.com. However, it's not recommended to discuss data recovery possibilities with developers of ransomware. This may not lead to any good. They will ask to pay the ransom, but there are no guarantees that they will let you decrypt files. Hence, it's better to eliminate ransomware from the system.
Brr ransomware
On the second week of September 2018, Brrr ransomware came to light. Files encrypted with .[paydecryption@qq.com].brrr pattern and same two ransom note files as most of the previous versions. Ransom note contains paydecryption@qq.com contact email and an offer to decrypt one file that is smaller than 1Mb. This move is definitely for manipulation and you shouldn't fall for this trick.
Gamma ransomware
Gamma ransomware was detected at the end of 2018 as yet another new version in Dharma/Crysis family. The virus has been relying on a similar pattern as other versions of this family: the virus fails to reveal a certain ransom amount, and actively offers to test the decryption for free. Other features of the Gamma version:
- The malware is using .id-%ID%.[bebenrowan@aol.com].gamma file extension;
- Ransomware drops a ransom note in files Info.hta and FILES ENCRYPTED.txt;
- The contact email that was given to the victim: bebenrowan@aol.com.
Bkp ransomware
In September 2018, Dharma ransomware owners presented yet another version of this malware called Bkp ransomware. As you can guess, files are marked with .bkp file extension and cannot be opened or used. This variant, similarly to other ones, has been delivering the same files for ransom notes with the names Info.hta and FILES ENCRYPTED.txt The contact email provided to the victim is bkp@cock.li, but it can be changed over the time. At the time of writing, there are about 10 known victims affected by this particular version which also remains not decryptable.
Boost ransomware
Boost ransomware came out only a month after the previous versions we spotted on the Internet. This time, a virus is encrypting data by using the AES algorithm and marking those files using a specific pattern – .[boston.crypt@tuta.io].boost. As usual for this ransomware family, FILES ENCRYPTED.txt file with the ransom message gets delivered to folders that contain encoded documents, photos, and other files.
Waifu ransomware
Yet another version from the Dharma family was discovered in October 2018 – Waifu ransomware. The malware encodes the user's files and marks them with an appendix that ends with .waifu. Also, contact email darknes@420blaze.it included in this file marker.
The ransomware developers are the ones who have been releasing new versions constantly. As a result, they haven't been changing these viruses much, so it is obvious why this variant is not very different from previously discovered.
BTC ransomware
BTC ransomware came out in October 2018, but this one has more features than other variants. First, the virus has been dropping BTC_DECRYPT_FILES.txt or IDR__BTC_DECRYPT_FILES.txt files as ransom notes that get delivered to the victim's screen right after the file-locking procedure is finished.
The encrypted data can be recovered by buying a Dharma decryptor which costs from 0.5 BTC to 1.5 Bitcoin. Since experts have already spotted several samples of this malware, it is normal that they have noticed several contact emails offered to use for contacting cybercriminals behind the virus: btc@fros.cc; zikr@protonmail.com; zikra@protonmail.com; zikr@usa.com.
FUNNY ransomware
FUNNY ransomware came out at the end of October 2018 as well. This time, only the program window named as the contact email appears on the screen after encryption. The information stated on the window include instructions on how to buy Bitcoins and pay the demanded ransom.
When you write WildMouse@cock. or unlock24@cock.li and ask for the opportunity to decrypt files, the ransom amount should be revealed. It possibly differs from victim to victim, based on the number of files or the valuable information ransomware possibly accessed.
Xxxxx virus
The year of 2018 was a busy year for the Dharma ransomware developers. Xxxxx ransomware was only one of many versions that got released this year. However, this version was the last discovered in October 2018. Not much new information got revealed with this version since it also not changed and resembles other 20+ variants.
Only features that make it different from previous Dharma versions:
- file marker .id-id.[syndicateXXX@aol.com].xxxxx
- contact email syndicateXXX@aol.com
Audit ransomware
Audit files virus appeared in November 2018 which came out after infecting several victims out of nowhere. It seems that crooks are still giving 24 hours for victims to reach them via contact email payransom@qq.com. This information alongside the victims' ID and places where you can buy cryptocurrency is delivered with the program window named with the particular contact email.
Tron ransomware
Tron ransomware is a version that was brought at the end of 2018. One of the distinct features belonging to this version of Dharma ransomware is the particular 0.05 BTC ransom amount. The sample that was analyzed revealed this information, but the amount still can differ from victim to victim. However, remember to avoid contacting these criminals and ignore the message with these emails supportjron@gmail.com; xtron@cock.li and follow up with virus removal.
Adobe ransomware
Adobe ransomware is a unique version that came out in November and December 2018. The virus developers have launched several different attacks leading victims to the lose of their files. The affected data is marked with the .adobe file extension, which has also been used by Djvu ransomware.
Possible contact emails used by this particular version:
- parambingobam@cock.li
- bufytufylala@tuta.io
- youneedfiles@india.com
- stopencrypt@qq.com
- btcdecripter@qq.com
Santa ransomware virus
Santa ransomware was released in December 2018. Not much changed as it supposed to be when dealing with this virus family. However, the ransom note that comes in a text file named FILES ENCRYPTED.txt reveals the contact email for the developers – Newsantaclaus@aol.com. A full file marker also includes this email. When documents or photos get encoded, .id-XXXXXXXX.[Newsantaclaus@aol.com].santa shows up at the end of the original name.
Wallet ransomware
Wallet ransomware was the first example spotted in 2019. This malware is using a mixture of AES and RSA encryption algorithms to encrypt data and make it unavailable for use. Files are marked with either .wallet or .wallet.lock appendixes. The ransom note is typical to Dharma file virus, and reveals that the amount of ransom equals from $500 to $1500 worth of cryptocurrency.
Heets ransomware
Heets ransomware showed up in January 2019. When the ransomware attack starts and files get locked, their names are changed to .id-[bestdecoding@cock.li].heets file marker. This way, the victim is informed that he or she is in huge trouble and needs to buy the Dharma decryptor. However, you should always think about whether it is worth spending almost $1000 on the affected data.
The full list of instructions is placed in an HTML window that appears on the desktop and shows possible steps and emails for contacting virus developers – bestdecoding@cock.li; heetsdecoding@cock.li – that should be used to reach out to cybercriminals.
Qwex ransomware
Qwex ransomware was reported by Jakub Kroustek The malware injects various files on the system besides FILES ENCRYPTED.txt ransom note or executable. This virus can change startup entries and add a program that disables the security features of the PC. To avoid any interaction with backdata@qq.com and dta@cock.li.
ETH ransomware
ETH ransomware has been affecting computer systems since the beginning of 2019. Our site has also encountered a few users who got victimized by this variant which is adding .ID-[random].[helpfilerestore@india.com].eth to encrypted files that get encoded and became useless as their code was completely scrambled. The ransom note stays the same and is called FILES ENCRYPTED.txt.
Unfortunately, ETH ransomware, just like numerous Dharma versions, is not decryptable. However, do not follow tips given in the ransom note and use helpfilerestore@india.com email address to contact virus developers. You need to avoid contacting people behind the malware and get rid of all the related programs with the anti-malware program since many of them can detect this virus.
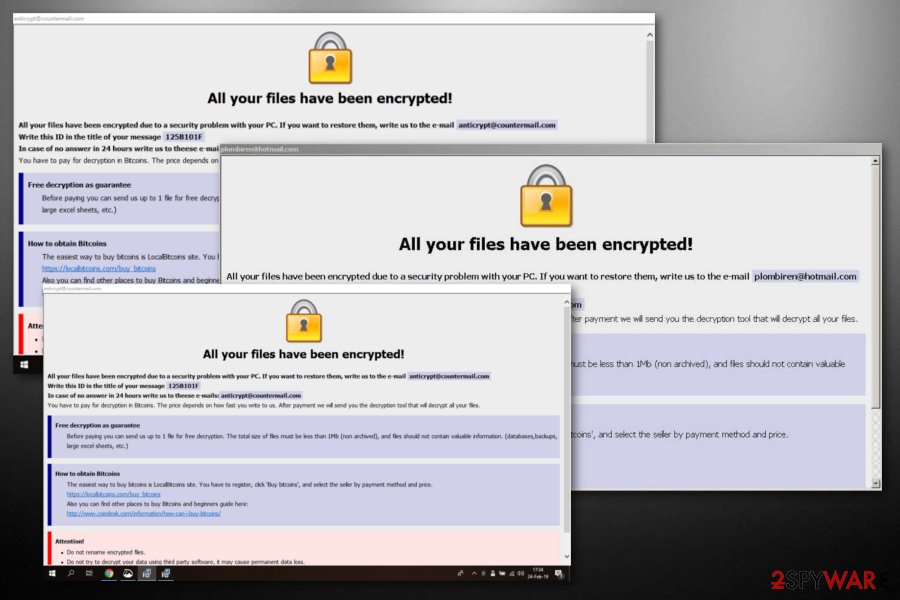
888 ransomware
888 ransomware is one of numerous Dharma variants that is using the name of the USA president in the contact email given to virus victims and mark their encrypted files. If you happen to find .[donald888@mail.fr].888 added to your files, it indicates that your files got encrypted and that you won't be able to use them anymore.
There is also a specific amount of ransom given to virus victims – this version is demanding $500 – $1500 in Bitcoin from its victims for files' recovery. Please, do not for their promises as the people you are dealing with are hackers!
Frend ransomware
Frend ransomware appeared in February 2019. When the infection gets into the system, it modifies the entire system with the help of AES or DES ciphers. Additionally, files receive the .frend file extension which changes files' names completely. Additionally, the virus saves FILES ENCRYPTED.txt text file on the computer's desktop that explains for the victims a need to contact hackers via undogdianact1986@aol.com or FobosAmerika@protonmail.ch email addresses. Please, ignore this request and use third-party tools to recover encrypted files.
KARLS ransomware
KARLS ransomware is another virus that was released a few days after previous versions, at the beginning of 2019. This particular threat employs the AES-256 algorithm for the file-locking process and makes data useless to have the reason for money extortion. When data gets .id-[random].karlosdecrypt@outlook.com.KARLS file marker, it can be recovered with the official Dharma ransomware virus decryption tool. However, you need to have a virus-free device before you start these procedures.
AYE ransomware virus
AYE ransomware came out in February 2019 as one of the numerous variants of the Crysis/Dharma ransomware family. The virus acts identically and drops a ransom message called FILES ENCRYPTED.txt right after encrypting files. The message reveals only the contact email and confirms the fact that the system got encrypted and can't be used anymore. Beware that this malware can disable some functions of your machine, so reboot the machine in Safe Mode before scanning it with an antivirus program. Additionally, start files' recovery.
NWA ransomware
The month of March 2019 was not the exception for Dharma activity. Slightly fewer variants than in previous months came out but cybercriminals still became active. NWA ransomware came out with a lengthy file extension ([filename].[original extension].id-[user ID].[dr.crypt@aol.com].NWA) that makes the user notice which files were encoded. The email address to discuss files' recovery is dr.crypt@aol.com.
Unfortunately, ransomware can also alter other files on the system and change the preferences of the programs running at the startup. It can also add the executable, called explorer.exe, with additional processes, and disables security programs to make the elimination more difficult.
Korea ransomware
Korea ransomware employs the typical symmetrical AES encryption algorithm and makes users' data useless. All this effort for the purpose of crypto-extortion because users want to get their files back.
Like most of the other versions, it adds a file extension to files that got affected in a pattern – .[omfg@420blaze.it].korea. Discovered almost at the same time as other variants hailing from this ransomware virus family, this threat automatically launches the HTML window with payment instructions. Additionally, it reveals places where you can buy Bitcoins which is the preferred cryptocurrency for ransomware threats.
Stun ransomware
Stun ransomware showed up just after April fools 2019. This Dharma version was discovered out of nowhere and was analyzed thanks to the samples provided by affected users. Investigations have revealed that this particular ransomware wipes some files and installs programs to various folders of the system.
Ransomware developers have also made additional changes that become clear if you compare two different viruses hailing from the same family. Files, typically marked with .id.[unlockdata@foxmail.com].stun extension, are not the only ones affected by this cryptovirus. For this reason, you need to get a reputable anti-malware program and scan the system fully.
Dec ransomware
This variant came to light in mid-April 2020 and was spotted by security researcher Jakub Kroustek.[10] Just as its predecessors, Dec ransomware uses a similar pattern for data encryption – it employs AES cipher to lock files and modifies their structure in the following way: .id-XXXXXXXX.[email].dec. An example of an encrypted file would look as follows – picture.jpg.id-1E857D00.[de_cryption@tuta.io].dec.
Once data is encrypted, the Dec file virus also delivers a ransom note called FILES ENCRYPTED.txt and a popup window, which holds information about what victims should do next. Allegedly, they are asked to contact criminals via e_cryption@tuta.io or decryption1@protonmail.com emails and then pay cybercriminals ransom for the decryptor. Text version of the note provides a brief description:
all your data has been locked us
You want to return?
write email de_cryption@tuta.io or decryption1@protonmail.com
Unfortunately, just like other newer Dharma variants, Dec ransomware is currently not decryptable, but you can employ third-party tools or use Windows built-in resources to attempt data recovery. Nonetheless, you need to make sure that you first remove Dec ransomware from your machine fully.
Love$ ransomware
Love$ ransomware variant has been detected by malware researcher Jacob Kroustek in April 2020. It does not deviate from its ancestors. It renders AES encryption and locks non-system files in a similar patter, i.e. it appends a unique ID number, email address, and .love$ extension to the locked file. Consequently, a file previously named as myfiles.doc would be turned to myfiles.doc.id-1E857D00.[im.online@aol.com].love$.
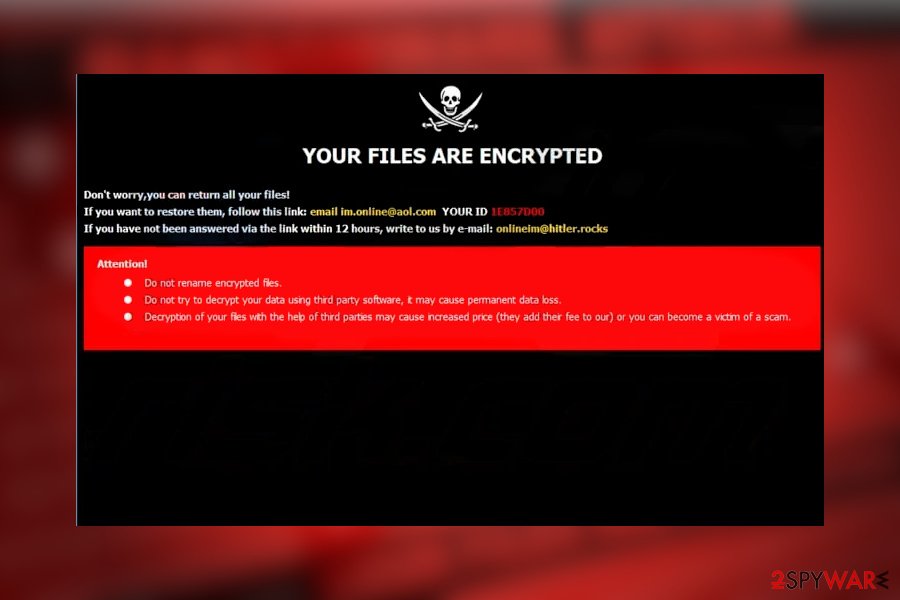
Love$ ransomware version drops a Dharma-typical ransomware note called FILED ENCRYPTED.txt which demands the victim to contact criminals via im.online@aol.com or onlineim@hitler.rocks emails and urge not to initiate manual or automatic changes on the files if permanent file loss is not required. The size of the ransom hasn't yet been specified.
YOUR FILES ARE ENCRYPTED
Don't worry, you can return all your files!
If you want to restore them, follow this link: email im.online@aol.com YOUR ID 1E857D00
If you have not been answered via the link within 12 hours, write to us by e-mail:onlineim@hitler.rocks
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
LOL ransomware
LOL ransomware has been first detected in 2017. It's a distinctive feature -.id-xxxxxxxx.[Helpsir@rape.lol].LOL file extension appended to encrypted files. Likewise earlier versions, this threat takes advantage of malspam campaigns to enter unprotected PCs and then launch the payload to lock personal files. Upon encryption, a victim is presented with a ransom note FILES ENCRYPTED.txt, which instructs the victim to send a reply with a unique ID number and one file to recover to helpsir@rape.lol or bitcoins12@tutanota.com emails.
Based on VirusTotal analysis, the main executable of the LOL (Dharma) ransomware is svchost.ex_[11]. The file mimics the legitimate Svchost.exe file to evade immediate detection and elimination. Nevertheless, 59 AV programs out of 69 are capable of detecting it.
BANG ransomware
BANG ransomware is one of the Dharma 2020 variant, which has been detected at the end of May by Jakub Kroustek. One of the malicious processes of this virus detected under the name payload.exe-retrieved-ca6b7dab175b447a0fb83fc71a09a8f3372def74.tmp have been uploaded to the VirusTotal[12]. 63 AV engines out of 72 are capable of detecting and contaminating it, so if you are one of the ransomware victims whose files have been encrypted by .BANG file extension virus, employ a security tool of your preference and run a thorough system scan with it.
This new variant is no less malicious than its ancestors. Its developers exploit spam emails to spread malicious executable files and employ an AES cipher to lock targeted file types. Upon successful uncover of the payload and cipher run, personal files on a host machine get a .bang extension. The suffix is typically preceded by a combination of ID-xxxxxxxx.[gangflsbang@protonmail.ch]. Such files can no longer be opened or modified.
Criminals behind the BANG ransomware virus are using identical ransom note as for earlier variants. It appears under the FILES ENCRYPTED.txt and contains the following information:
all your data has been locked us
You want to return?
write email gangflsbang@protonmail.ch or gangflsbang@cock.li
Besides, the BANG file-encrypting ransomware changes the desktop background. The image features black and red background with a skull applique and “YOUR FILES ARE ENCRYPTED” slogan. The same background image has been used by most of the Dharma 2020 versions, including .harma, .msplt, .8800, .pay, .news, and .roger. Both note and background provide a contact e-mail gangflsbang@protonmail.ch.
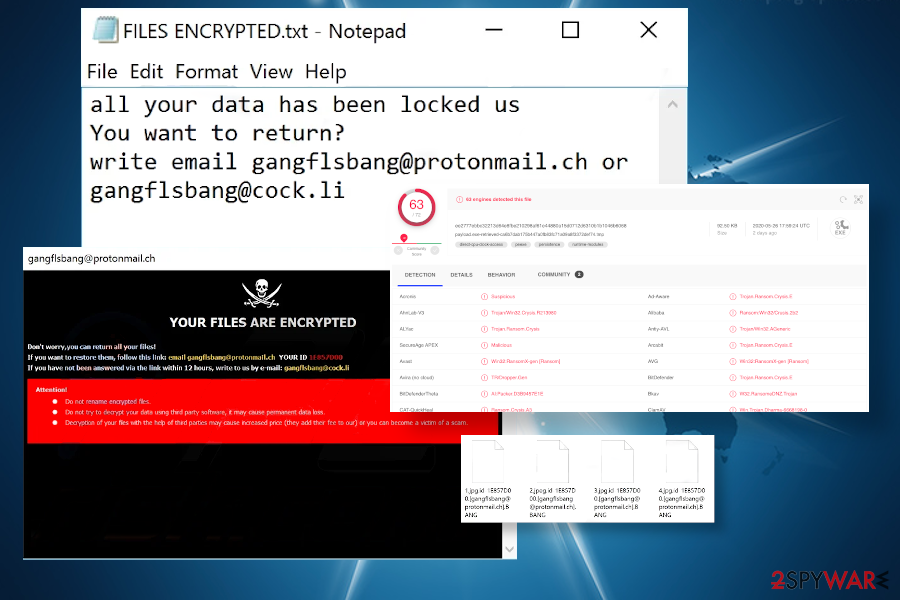
PayB ransomware
PayB ransomware or .payb file extension virus emerged right after the BANG variant at the end of spring 2020. It's a copycat version of the previous variant, except two differences, i.e. altered file extension and renewed contact e-mail, which is now paybit@aol.com. Other traits of this ransomware attack are the following:
- the payload is typically spread via obfuscated email attachments;
- upon infiltration, it alters Windows registry entries, runs malicious files within system directories, and changes boot sequence;
- when the virus roots into the OS, it launches the AES cipher and targets the most popular file types for locking;
- all encrypted files get the extension id-xxxxxxxx.[paybit@aol.com].payB file extension;
- the desktop background gets changed to the “YOUR FILES ARE ENCRYPTED” image;
- a Dharma-specific ransom note FILES ENCRYPTED.txt is created;
- victims are demanded to pay the ransom that varies from $480 to $980 in Bitcoins;
- criminals use paybit@aol.com email for communication.
Experts recommend people remove PayB ransomware without a delay if managed to infiltrate the system and lock files. It's a deadly dangerous virus that can cause severe Windows distortion and lead to crashes. Besides, do not get scared by criminals who share false claims that resisting to pay will lead to permanent file loss. Most of the variants can be decrypted using an official Crysis decryptor.
Before PayB removal, copy all encrypted files to the USB flash drive or alternative storage and run a scan with AV tool in Safe Mode to get rid of all malicious entries. After that, follow the guide at the end of this post explaining how to get the official decryptor and run the software to decrypt files encoded by .payB file extension.
Ransomware malspam campaigns infect hundreds of users daily
Just like many other ransomware-type viruses, this one takes advantage of naïve computer users and employs phishing[13] techniques to infect the targeted systems. One of the most popular ways is malspam campaigns which trick gullible people to open malicious attachments with the payload of the Dharma ransomware. Despite the information about precautionary measures that help inexperienced computer users protect their systems, many people continue to fall for the same tricks of the attackers.
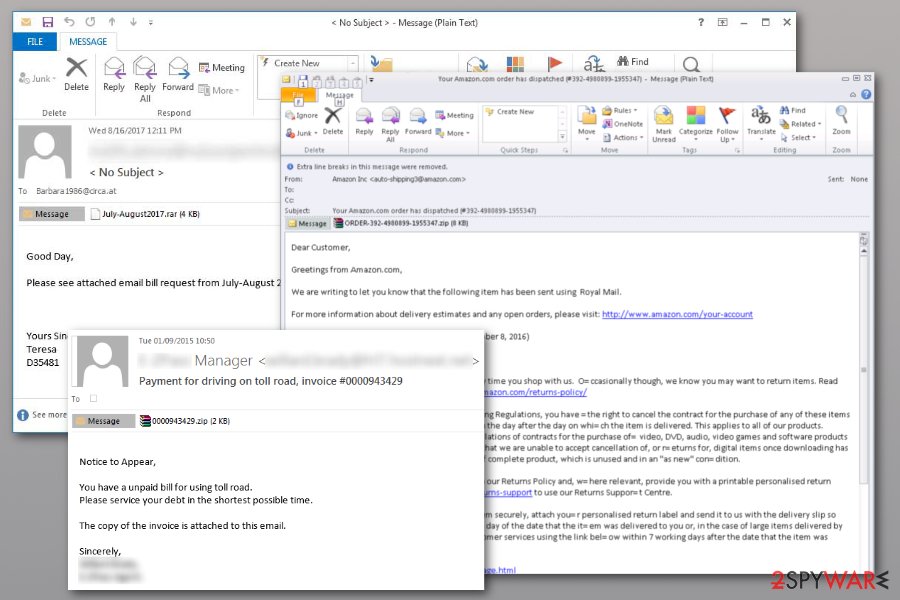
LesVirus.fr[14] team has prepared tips to avoid ransomware infiltration. We kindly ask you to do the following if you want to protect your computer:
- If you, yourself, receive an email from some unknown sender, company, or institution, carefully investigate it.
- Think about whether you expected such an email in the first place if you have no idea why it has reached your email – it might be that you are being targeted by extortionists.
- In such a case, you should stay away from any attachments that might be added to the email and delete them immediately. Otherwise, malware can sneak in its malicious payload with some fake plane ticket, speeding ticket, or any other documents that might look convincing enough to be taken for granted.
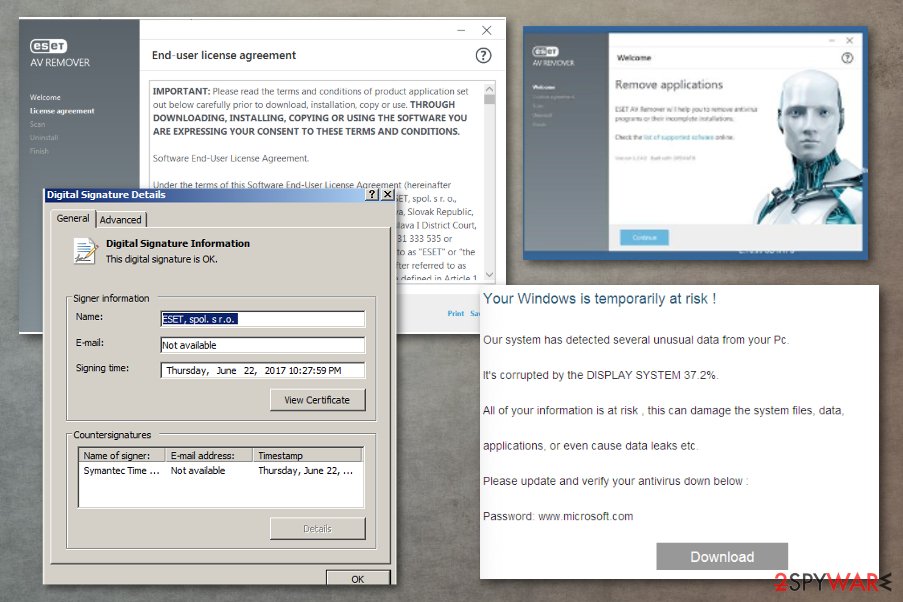
Fake ESET AV tool used to distribute ransomware versions
The more recent campaigns in 2019 revealed more information about the particular Dharma ransomware distribution method. It still involves spam emails and attached files, but it revolves around the installation of a specific AV tool. During this process, cryptovirus can hide its encryption and infiltration activities.
The email itself that delivers such a file states the needed malware elimination or risks on your machine. The system possibly can get damaged if you don't download the program provided in the notification. Of course, the sender poses as Microsoft and claims to be the legitimate support team member.
Unfortunately, when the button DOWNLOAD gets clicked, the password provided in the email is required. Once all those steps are done, the program gets loaded on the system via executable files Defender_nt32_enu.exe or Defender.exe. The old version of ESET AV Remover gets loaded, and during the installation process that needs users' involvement, the virus distracts the victim from its ransomware activities.
The installation of this security tool and Dharma encryption are not related, and the encryption still happens even when the installation is not executed. The security software installation is included to trick people into thinking that there is nothing malicious happening when the system slowdowns during the download.
Removal instructions for the ransomware
It is evident that ransomware-type threats are highly dangerous and tricky. Likewise, people can either get help from an IT specialist or employ professional virus removal software. Note that such cyber infections have numerous components and are able to hide them or disguise them as legitimate system processes.
That is why you cannot remove Dharma ransomware directly and need to complete a few extra steps first before you run the system scan. We have presented these steps down below. Feel free to use them and don’t forget to scan your system automatically afterward! We suggest using one of these tools: SpyHunter 5Combo Cleaner or Malwarebytes.
Bonus: video clip for help on the virus elimination process
Since Dharma ransomware has been a widely-distributed cyber threat, we decided to create more accurate removal instructions for this threat with graphical elements. Our goal is to help users to clean, optimize, and refresh their computer systems after the secret infiltration of dangerous malware. If you also are a victim of this notorious file-encrypting cyber threat, take a look at this below-provided video clip and receive a clearer view of the malware elimination process:
Victims of Dharma ransomware are lucky since security experts discovered a leak in its code and also found numerous decryption keys online. Likewise, Kaspersky Lab has already upgraded the decryptor which you can download here. Alternatively, try ESET Crysis Decryptor.
In case the decryptor fails to decrypt your files: Recently, our team received a message from a person who said one of his clients got infected with .[oron@india.com].dharma ransomware version. Surprisingly, our site visitor reported that he managed to restore encrypted data archives by extracting them with 7-Zip. We suggest you try this method if you haven't already. You can find the original comment from the visitor in the comments section below.
Getting rid of Dharma virus. Follow these steps
Isolate the infected computer
Some ransomware strains aim to infect not only one computer but hijack the entire network. As soon as one of the machines is infected, malware can spread via network and encrypt files everywhere else, including Network Attached Storage (NAS) devices. If your computer is connected to a network, it is important to isolate it to prevent re-infection after ransomware removal is complete.
The easiest way to disconnect a PC from everything is simply to plug out the ethernet cable. However, in the corporate environment, this might be extremely difficult to do (also would take a long time). The method below will disconnect from all the networks, including local and the internet, isolating each of the machines involved.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet

- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
If you are using some type of cloud storage you are connected to, you should disconnect from it immediately. It is also advisable to disconnect all the external devices, such as USB flash sticks, external HDDs, etc. Once the malware elimination process is finished, you can connect your computers to the network and internet, as explained above, but by pressing Enable instead.
Scan your system with anti-malware
If you are a victim of ransomware, you should employ anti-malware software for its removal. Some ransomware can self-destruct after the file encryption process is finished. Even in such cases, malware might leave various data-stealing modules or could operate in conjunction with other malicious programs on your device.
SpyHunter 5Combo Cleaner or Malwarebytes can detect and eliminate all ransomware-related files, additional modules, along with other viruses that could be hiding on your system. The security software is really easy to use and does not require any prior IT knowledge to succeed in the malware removal process.
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Find a working decryptor for your files
File encryption is a process that is similar to applying a password to a particular file or folder. However, from a technical point of view, encryption is fundamentally different due to its complexity. By using encryption, threat actors use a unique set of alphanumeric characters as a password that can not easily be deciphered if the process is performed correctly.
There are several algorithms that can be used to lock data (whether for good or bad reasons); for example, AES uses the symmetric method of encryption, meaning that the key used to lock and unlock files is the same. Unfortunately, it is only accessible to the attackers who hold it on a remote server – they ask for a payment in exchange for it. This simple principle is what allows ransomware authors to prosper in this illegal business.
While many high-profile ransomware strains such as Djvu or Dharma use immaculate encryption methods, there are plenty of failures that can be observed within the code of some novice malware developers. For example, the keys could be stored locally, which would allow users to regain access to their files without paying. In some cases, ransomware does not even encrypt files due to bugs, although victims might believe the opposite due to the ransom note that shows up right after the infection and data encryption is completed.
Therefore, regardless of which crypto-malware affects your files, you should try to find the relevant decryptor if such exists. Security researchers are in a constant battle against cybercriminals. In some cases, they manage to create a working decryption tool that would allow victims to recover files for free.
Once you have identified which ransomware you are affected by, you should check the following links for a decryptor:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

If you can't find a decryptor that works for you, you should try the alternative methods we list below. Additionally, it is worth mentioning that it sometimes takes years for a working decryption tool to be developed, so there are always hopes for the future.
Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Dharma and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ David Bisson. Ransomware hit garage used by Canadian internet registration authority. Tripwire. Cybersecurity solutions.
- ^ Charlie Osborne. Texas hospital becomes victim of Dharma ransomware. Zdnet. 24/7 news coverage and analysis on the trends.
- ^ R. Sachin. Dharma vs Karma. The official eScan blog.
- ^ Steve Ranger. Locky ransomware: How this malware menace evolved in just 12 months. ZDNet. Global and local news.
- ^ Santiago Pontiroli. Tweet by @spontiroli. Twitter. Social Network.
- ^ Sue Marquette Poremba. Expect an Evolution in Ransomware in 2017. ITBusinessEdge. Data Security blog.
- ^ Encryption. Wikipedia, the free encyclopedia.
- ^ Types of Ransomware: Crypto and Locker. VinRansomware. The exclusive online hub to know all and everything about Ransomware.
- ^ Michael Gillespie. ID Ransomware picked up on another new extension for #CrySiS/#Dharma Ransomware: ".java". Twitter. Online Source for Communication and News.
- ^ Jakub Kroustek. '.dec' - 'de_cryption@tuta.io'. Twitter. Social network.
- ^ svchost.ex_. Virus Total. Free URL and file scanner.
- ^ payload.exe-retrieved-ca6b7dab175b447a0fb83fc71a09a8f3372def74.tmp. Virus Total. Free URL and file scanner.
- ^ Phishing attacks at their highest in 2016. Avast security blog.
- ^ LesVirus. LesVirus. Malware Removal Tutorials.






































